Is There More To This Image?
How we communicate has become extremely easy in today’s digital society. Most mobile devices offer software that integrates with social networks, business applications and e-mail. People share anything from where they are eating to what they are about to eat in near real-time (personally I find it annoying). This convenience makes securing communication more difficult since most digital messages leave a digital fingerprint as well as usually transmitted over nonsecure sources. My team has demonstrated how hackers can steal data in transit using man-in-the-middle attacks with tools like the Pine Apple (more HERE), BeEF (more HERE), and compromising mobile devices to pull up old text messages and e-mails.
How can you protect your communication? Best practice is investing in multifactor authentication to trusted systems, VPN technology for communication outside of a secure network, data loss prevention monitoring what data is permitted to leave a secure network, internal network security products and host based security to stop key loggers and other threats. Communication solutions should offer a mix of confidentiality (protecting the information), integrity (can’t modify the message), availability, authenticity (message is genuine) and non-repudiation (guarantee sent and received).
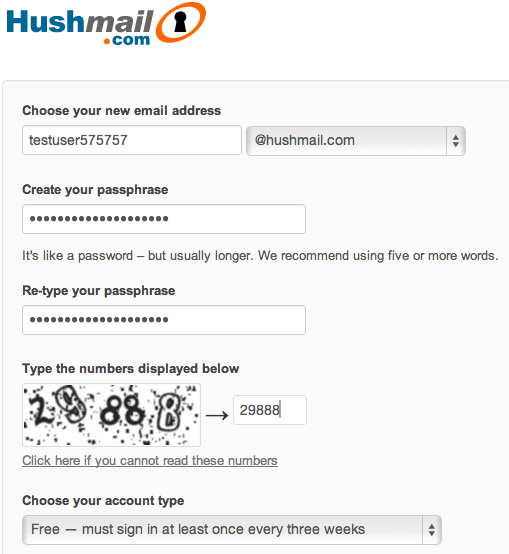
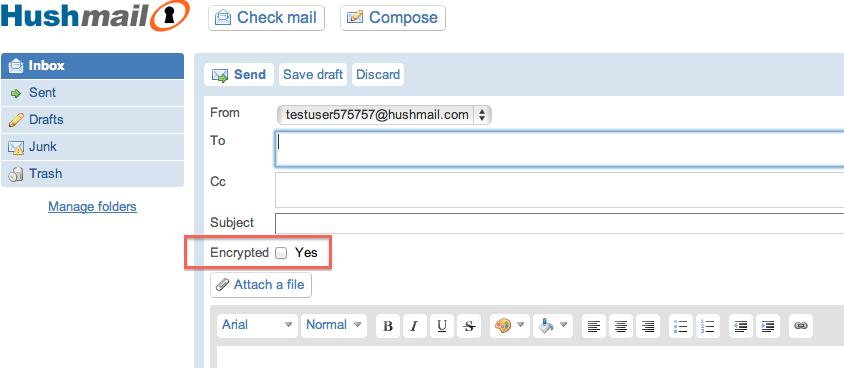
Meeting best practice typically requires investments in multiple technologies however what about the average user looking to send a sensitive message? There are methods to send messages securely using free tools. One option is using a secure e-mail solution. Hushmail offers free PGP-encrypted e-mail and file storage. If you look at the image below, you will see the checkbox for encrypting the outgoing message as well as how Hushmail enforces a strong passphrase promoting secure e-mail standards. The downside of Hushmail is it doesn’t offer some of the flashy features other e-mail services include such as chat or customizable backgrounds.
Setting up a Hushmail account
Sending Encrypted E-mails
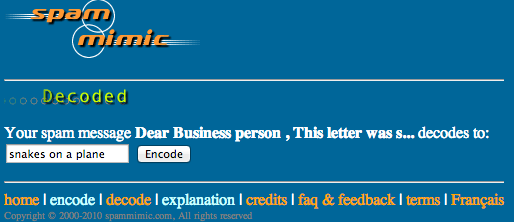
Another way to protect you message is hiding it in the clear using Steganography techniques. One cool tool is Spammicmic, which jumbles a short message in a large spam e-mail. The average user will assume the message is spam and overlook your hidden message. To use spammicmic, go to spammimic.com and click encode. Enter your short message and spammicmic will convert it to a long spam message. Have your receiver take the spam message and decode it on spammimic’s decoder section to see the real message.
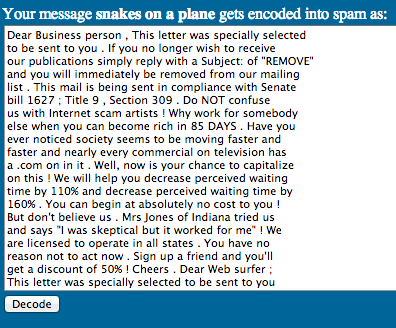
Example of Spammimic Generated Spam
Decoded Spam Message
Some advanced Steganography options can hide messages in images, videos and audio files. Mobilefish offers both image and message steganography. Below I’m adding a hidden message in the image at the beginning of this post (guy and girl with the cups and string). To decrypt, go to Mobilefish.com, upload the image and use the password “snakes”. You can also find many steganography software options that include layering encryption, passphrase and multiple file types into a single image. For example, I can post an image of a cat on facebook and inform my intended receiver to download the image and use a passphrase to unlock three hidden word documents. I can set a timer to disable unlocking the files after X days making it extremely difficult for my secrets to be compromised. You can google for free Stegranography software or check out one I like called Invisible Secrets (however this one has a small fee to use).
Using Mobilefish to hide message in a image


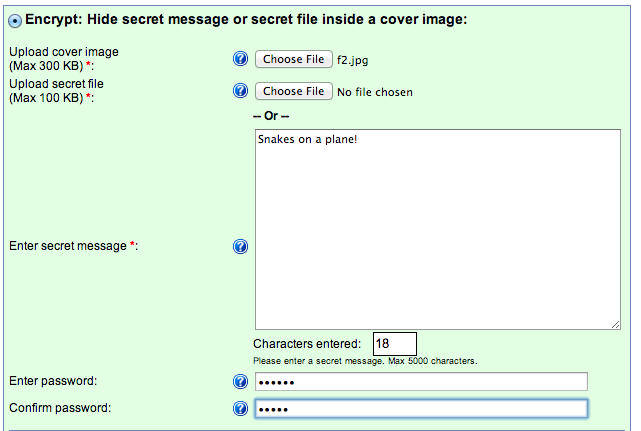



These tools may be fine for consumer use but are in no way enterprise ready. Tools need to be recordless and create no electronically stored information.
As we found with tools that encrypt and spoof they can be hacked and recreated!
Hi Patrick,
Absolutely agree. There are many enterprise solutions available that offer many more features. The purpose of this post is for the home user not able to invest in a enterprise grade tool.
Steganography and cryptography both are used to providing secure communication between sender and receiver.for securing communication we used digital signature and encryption technology also .
___________
Printer spooler error
Agreed …. the more layers the better. Unfortunately many users leverage strong security methods for work communication however drop all best practices for personal internet use. You may find employees at the pentagon or within large banks with social network accounts and personal cloud based email secured with weak passwords. There are also small business owners who can’t afford to invest in enterprise grade cyber security. Hopefully these or other free tools could help when secrets need to be exchanged.
I seriously love your website.. Pleasant colors & theme. Did you develop this web site yourself? Please reply back as I