Most Security solutions leverage a combination of signature and behavior based technology (more HERE). This worked in the past however today these solutions are not good enough regardless if you layer multiple products that are built upon similar scanning methods. There are many ways to bypass point Security products such as throttling behavior and masking the known fingerprint of the attack code. A example of a technique used to hide malware from popular Anti-Virus packages is leveraging Dynamic Obfuscation software. 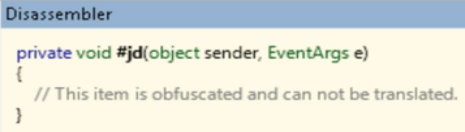
Obfuscation software was designed to protect source code from piracy by making the original code more complicated to read while retaining functionality. There are commercial obfuscation software packages available for programmers looking to hide their source code which is also obtainable for malware developers. This is bad for anti-virus vendors responsible for developing methods to fingerprint malicious code.
Malware producers can make things even more difficult for Anti-Virus vendors by adding dynamic elements that randomizes malicious code and encryption keys on the fly. For example, a victim accessing a malicious website could see a different variation of the same exploit each session. Dynamic obfuscation provides an endless number of variants making it almost impossible for signature based Security to identify the threat.
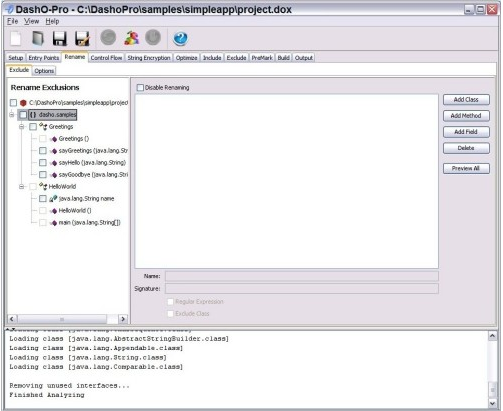
There are dozens of examples for commercial Java obfuscator packages. Some common packages are Zelix KlassMaster, Dash-O, ProGuard, Smokescreen, Thicket and Allitori. Popular penetration toolsets such as Metasploit also include malware obfuscating modules such as the VoMM module. Research on VoMM from a few years ago can be found HERE .
Examples of Java Obfuscation Software
The best way to combat dynamic obfuscated malware and other advanced threats is using tools that view all internal traffic and hardening security around web usage. Two popular methods to gain visibility around the security aspects of network traffic are packet capture and NetFlow based products such as NetWitness and Lancope (more HERE). The network communication footprint between obfuscated malware and host will identify the threat as well as monitor if it attempts to spread to other systems. SIEM solutions are also helpful as long as they are properly tuned and obtain feeds from multiple sources.
Most of the dynamic elements used by malware are server driven and require a connection back to a web based malicious source. Its important to invest in a web security solution that can go beyond content filtering and signature based security. One key feature that can identify malicious sources attempting to host dynamic obfuscated software is reputation based technology (more found HERE). Reputation eliminates any blacklisted website as a threat vector limiting the chances of users unknowing accessing a malicious website. Other features such as honeypots could be used to play out questionable sessions to verify if the code is really obfuscated malware (example FireEye).
The industry is seeing a growth in advanced threats emerge. The people behind these threats have unlimited funds and access to the same products we use for network defense. Dynamic Obfuscation malware is just one example of how to bypass traditional security defenses. Be aware of the threat landscape and consider looking beyond signature based security as your only defense.