Its shocking how organizations are compromised due to administration carelessness such as using default passwords or advertising sensitive information on public sources. Many companies purchase top dollar security solutions however fail at addressing the most common security weakness; enforcing thorough security policies. One popular reconnaissance technic known as Google Hacking (however can use other search engines) can expose confidential information, vulnerabilities and login credentials using Internet search engines. Here are some tips to avoid being abused by Google Hacking or other reconnaissance techniques.
Strong Passwords:
 Anything facing the Internet should have very strict security policies implemented to defend against hackers. For starters, all default passwords should be changed using a strong policy. Strong password formats do not contain words found in spoken languages including changing letters to other characters (IE: Ex@mp1e would be considered weak). An example of a good password format is using the first or last letter of a sentence plus numbers and special characters (IE: This Blog Talks About Many Crazy Things CONVERTED WITH FIRST LETTER OF EACH WORD = tbtamct135@!). Also length, expiration time and number of factors impact password security strength. More on passwords can be found HERE
Anything facing the Internet should have very strict security policies implemented to defend against hackers. For starters, all default passwords should be changed using a strong policy. Strong password formats do not contain words found in spoken languages including changing letters to other characters (IE: Ex@mp1e would be considered weak). An example of a good password format is using the first or last letter of a sentence plus numbers and special characters (IE: This Blog Talks About Many Crazy Things CONVERTED WITH FIRST LETTER OF EACH WORD = tbtamct135@!). Also length, expiration time and number of factors impact password security strength. More on passwords can be found HERE
HERE is an example list of default passwords for popular network devices. It’s common to uncover default logins on small neighborhood wireless networks however my team finds default information on large corporate systems as well using targeted Google Hacking queries. Some examples are searching #-Frontpage- inurl:administrator.pwd or inurl:odbc.ini ext:ini –csv for Microsoft and ODBC passwords. Some automated hacker tools use Google Hacking queries to gather system information prior to launching exploits and password cracking efforts. Don’t be a victim to weak passwords!
Know What Is Public Facing:
It is key to protect sensitive information such as vulnerability reports, employee information and confidential records. There are great tools available to audit for sensitive information such as data loss prevention products and compliance tools (more on DLP HERE). Crazy enough, sometimes administrators unknowingly let audit results for confidential information leak to public search engines. One example is searching for audit report headers (IE “This Report Was Generated By Nessus”) to identify vulnerable targets without setting off alarms using penetration testing techniques. Another example is searching for phases such as Classified via intext:classified COMPANY to find sensitive corporate information. Its shocking what is out there.
Some fun search terms are looking for cameras using queries such as Linksys inurl:main.cgi or ViewerFrame?Mode= . Be careful, some people don’t know they are in front of a live camera. Seriously, try it! You can move around cameras and see different parts of the world 🙂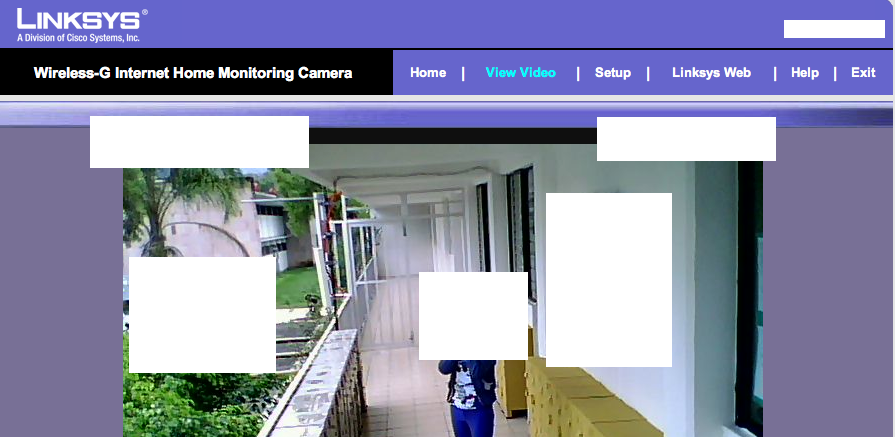
A really good source for finding Google Hacking search terms is Hackers For Charity GHDB (Google Hacking Database) found HERE or at johhny.ihackstuff.com
Harden Web Servers and Applications:
There are vulnerabilities in web applications that automated malicious applications can identify though Google Hacking. Best practice is using strong security procedures for developing web applications as well as hardening all hosting systems. There are companies such as Cenzic, McAfee and Radware that offer solutions to protect against web based attacks such as cross site scripting. It is also important to verify what is included in source code as well as search engine exclusion lists such as a Robots.txt file typically used to hide information from search engines. Best practice is hiring professionals to simulate hacker activity through a full penetration test. Vulnerability tools are good however only penetration testing will confirm how vulnerable you really are to Google Hacking as well as other attacks. Best practice is also to secure any audit findings from tools and contractors.
Example of www.cnn.com ‘s robots.txt file
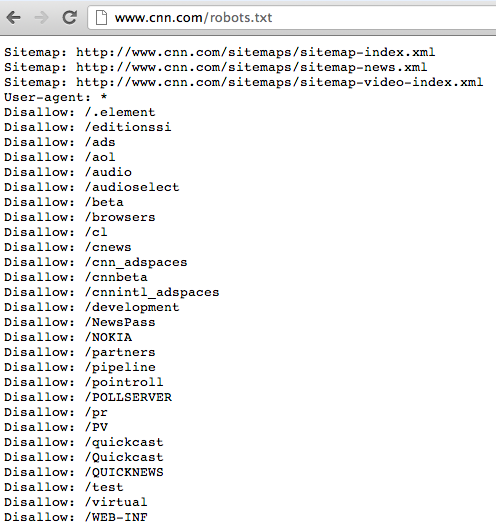
Its very important to understand that removing things from the Internet doesn’t guarantee people can’t find them. There are sources such as archive.org and searching a website/robots.txt to identify what content is being hidden or has once been exposed. You may secure things now however an older version may be available displaying sensitive information.
Go ahead and try Google Hacking your organization. What do you see when you google YOURCOMPANY intext:confidential copyright or YOURCOMPANY intitle:index.of inbox dbx to find outlook inboxes. Go to johhny.ihackstuff.com and run some queries against your organization. You can also find more on Google Hacking online and in Google Hacking for Penetration Testers Volume 2 book by Johnny Long.



