Cisco recently announced a partnership with Lancope to address Advanced Persistent Threat or APT type attacks. The reason Lancope / StealthWatch was added is most security solutions are based on signatures or behavior to identify threats. Some newer technologies are leveraging reputation (see my post HERE) or honey pots (example FireEye) however advanced attacks aka APTs are bypassing these traditional security solutions.
Cisco recently announced a partnership with Lancope to address Advanced Persistent Threat or APT type attacks. The reason Lancope / StealthWatch was added is most security solutions are based on signatures or behavior to identify threats. Some newer technologies are leveraging reputation (see my post HERE) or honey pots (example FireEye) however advanced attacks aka APTs are bypassing these traditional security solutions.
APTs are typically customized for a specific target and designed to stay under the radar using technics such as throttling network usage, communicating through standard ports, encryption and other means that bypass common security solutions. Examples of common security devices are Firewalls, IPS/IDS, Content filters, Anti-Virus / Anti-Malware, and other technologies that operate on a “probe” type design meaning they can only see traffic in a specific network segment. The APT problem becomes difficult to address with traditional tools due to lack of ability to detect the methods APTs operate on the network as well as difficultly to places detection technology in all network areas monitoring all layers of the network stack.
Some recent offerings to combat the APT threat are packet level and flow based monitoring solutions (Lancope being flow based). Both approaches look at all network traffic and flag anomalies that would bypass other security technology. Both views have pros and cons however one clear advantage of using NetFlow is many network devices are capable of generating flows which makes it more cost effective than capturing and storing packet level data. I’m not saying packet level monitoring is a bad however storage requirements tend to quickly raise the price tag of this approach.
Lancope StealthWatch works by viewing any host with an IP address that creates TCP/IP traffic on the network. Lancope collects metadata on hosts and builds a profile of behavior. Network hosts connected to devices such as switches, routers and firewalls generate flows of information which typically are NetFlow or sFlow. As flows are collected, Lancope aggregates, normalizes and analyzes NetFlow telemetry data to detect threats and suspicious behavior. Lancope can also integrate with Cisco Identity Services Engine aka ISE by taking in contextual information such as User Identity, Endpoint Device Profiling and Posture information. Lancope essentially enables security monitoring on network devices. This dramatically improves the time to identify and react to threats. We had one customer identify some malware that apparently had been active for months throttling its communication phone home patterns to bypass their IPS and SIEM solution.
MY Lancope LAB
When logging into the management interface of Lancope StealthWatch, you first have to launch a Java session.

Once launched, the management interface of Lancope looks like this.
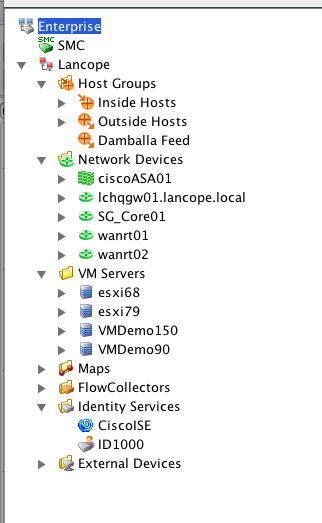
I have specific dashboards that come up which are customizable. Lancope offers TONs of reports that can pop up upon login. NOTE: My Lancope lab is using dummy data. Below is a breakdown of some of that data via the fake hosts, network devices and ISE system.
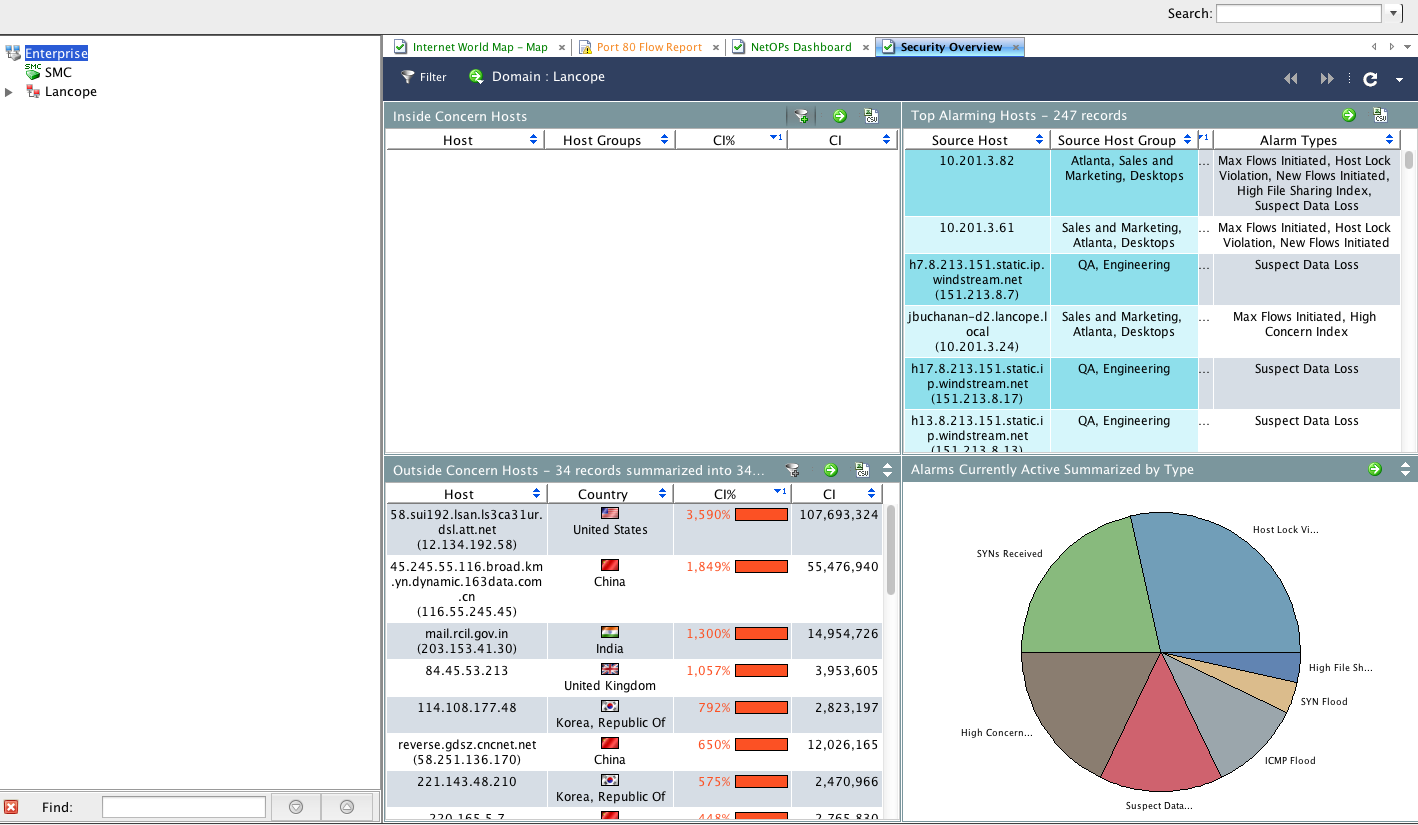
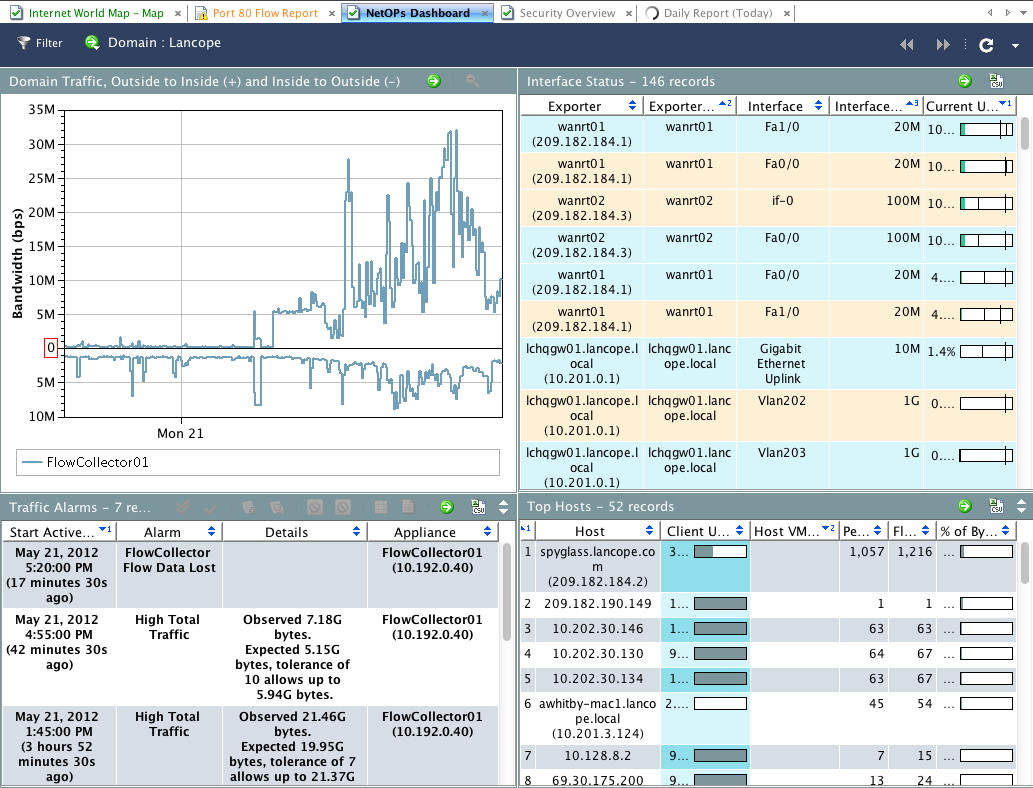
This Lancope dashboard shows traffic by hosts and bandwidth usage.
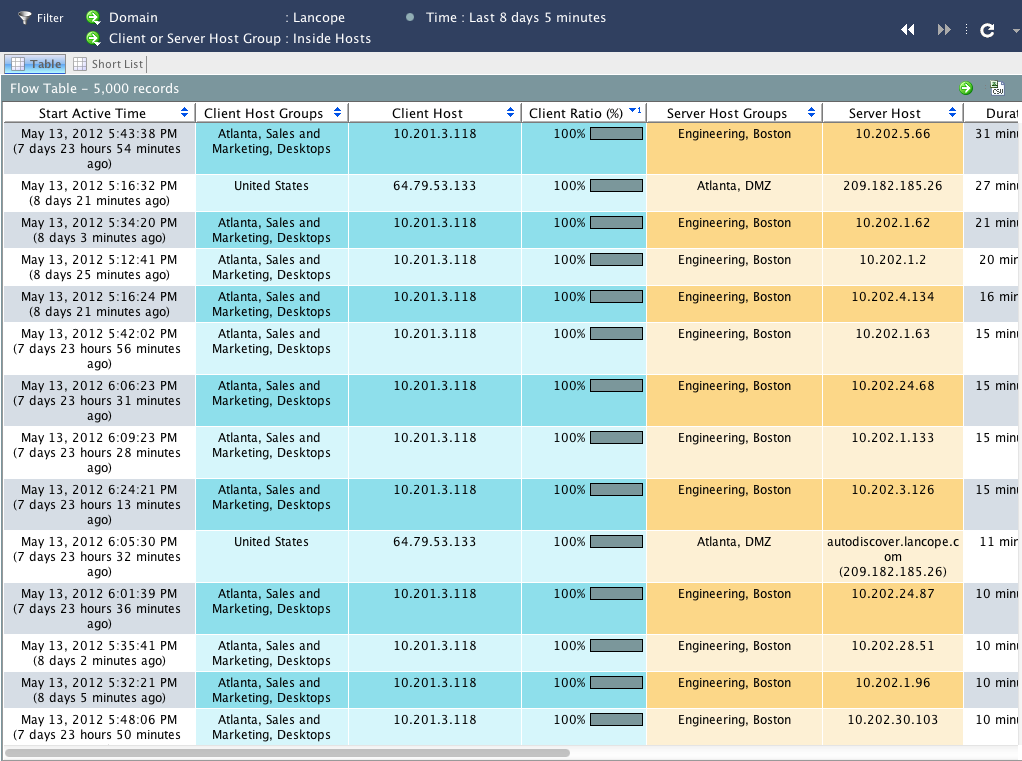
This shows a flow table in my Lancope lab. Flows are typically one way communications (Cisco ASAs are the only exception). Lancope stitches flows together so admins can easily see the full communication chain between hosts.
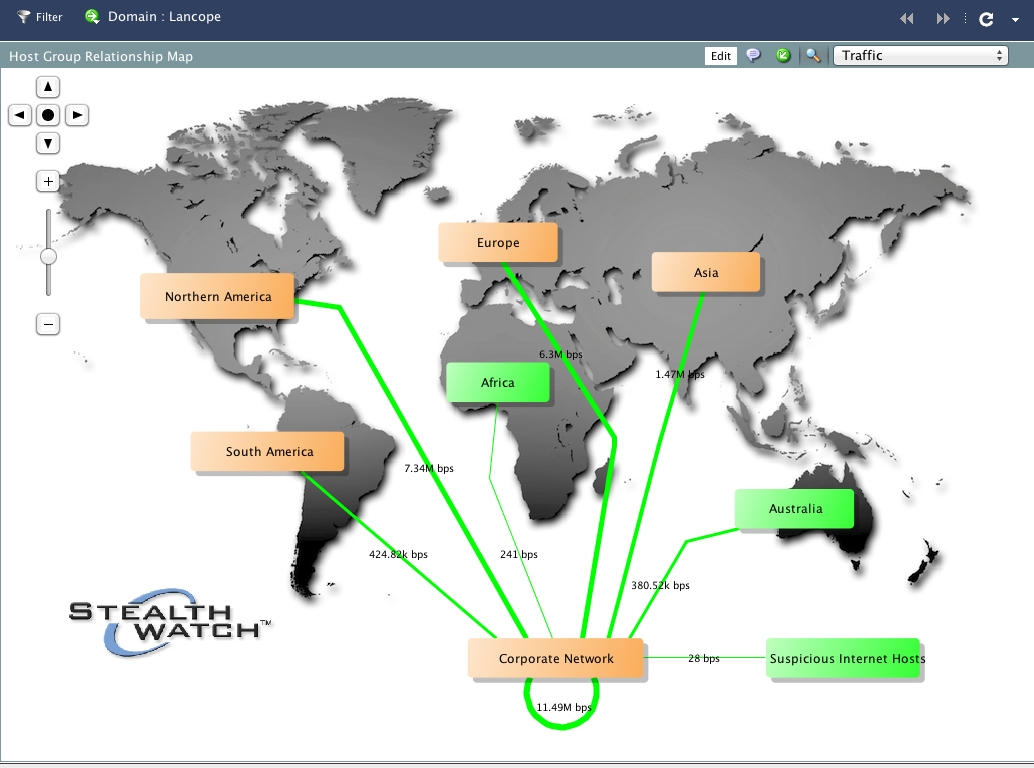
This Lancope diagram shows a global map of host relationship usage.
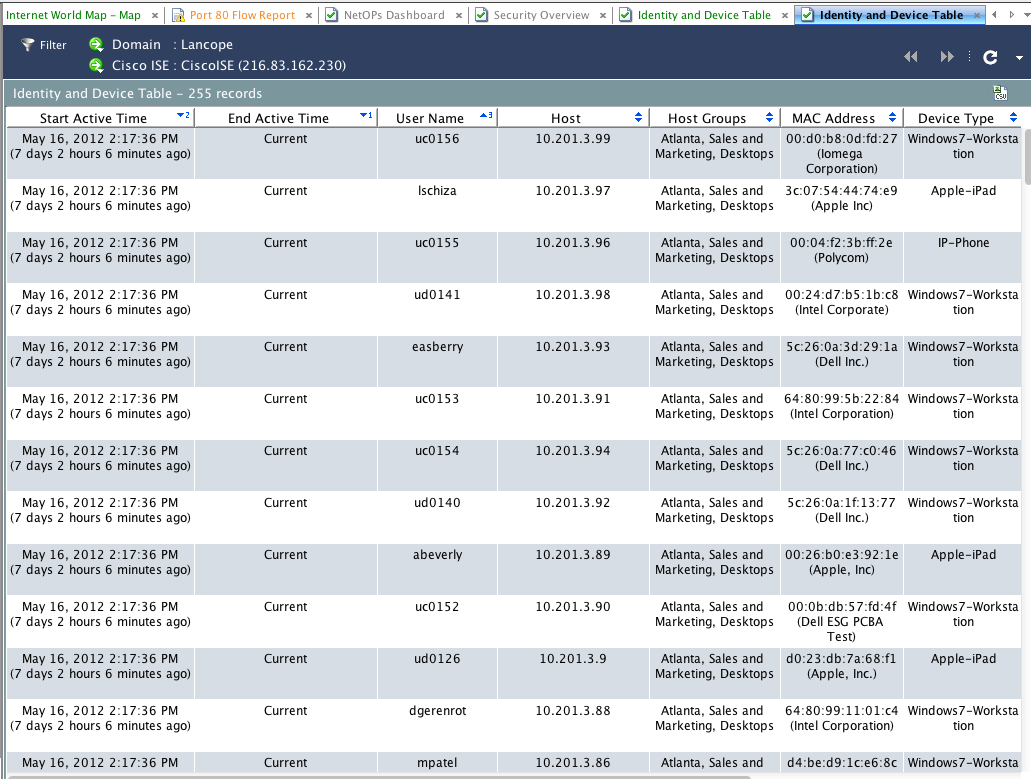
Here is a Lancope report showcasing user integration with Cisco Identity Services Engine aka ISE. Notice how inside Lancope, you can see who the users are , where they are located and what type of devices they have on the network utilizing the authorization and profiling capabilities of Cisco ISE.
The Lancope StealthWatch solution, Cisco NAM and Cisco Identity Services Engine or ISE integration is Cisco’s new flagship story to address advanced cyber threats aka APTs. I believe its critical to monitor flow or packet level data since in many cases, its the only way to identify and defend against advanced threats designed to bypass traditional security products. The scary thing about technology such as Lancope is what you will find when you first set it up in your environment. In many cases, customers find they are already owned and have been for a long time.