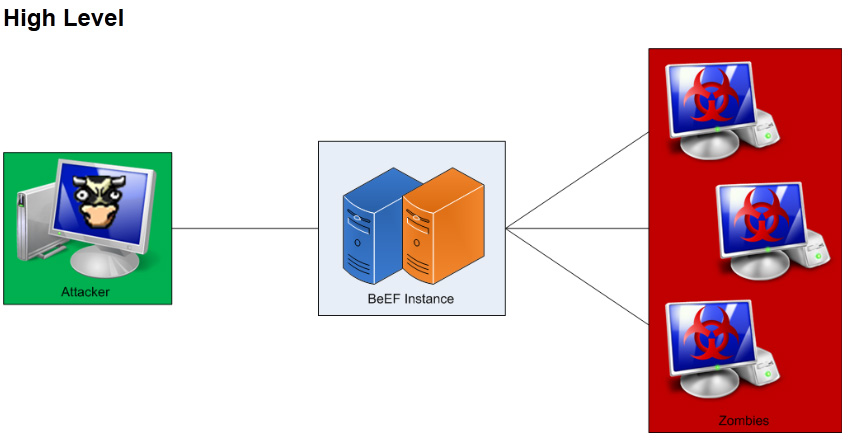
There are many cool penetration applications that should be included in your hacking arsenal such as one of our favorites known as BeEF. BeEF (short for The Browser Exploitation Framework) is a browser based exploit package that “hooks” one or more browsers as beachheads for launching attacks. A user can be hooked by accessing a url and continue to see typical web usage while the attacker has access to the user’s session. BeEF bypasses network security appliances and host based anti-virus applications by targeting vulnerabilities found in common browsers such as Internet Explorer and Firefox. BeEF is included with the latest BackTrack 5 r3 and can be found at beefproject.com
Backtrack Prep
Before you setup BeEF, we need to do a few house keeping items on Backtrack. First you may want to disable the firewall to prevent blocking the BeEF services. We are doing this for our lab however this step is optional.
Open up a terminal window and type the following commands:
IPTABLES -F
IPTABLES -X
IPTABLES -t nat -F
IPTABLES -t nat -X
IPTABLES -t mangle -F
IPTABLES -t mangle -X
IPTABLES -P INPUT ACCEPT
IPTABLES -P FORWARD ACCEPT
IPTABLES -P OUTPUT ACCEPT
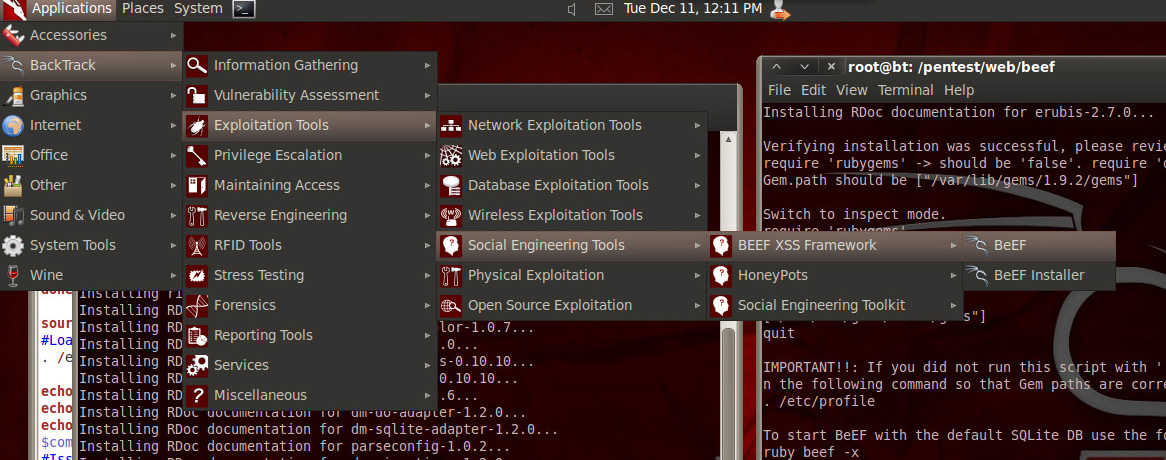
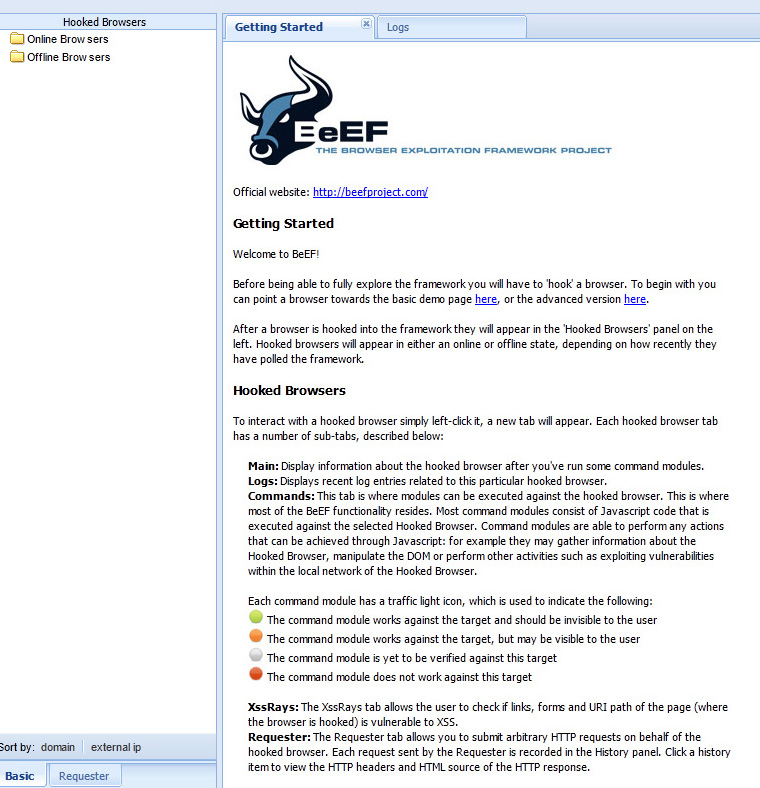
To setup BeEF in BackTrack 5, you can run a script found HERE. One you run the script and updates, run BeEF from the backtrack 5 application list to see the management GUI IP and hook URL. When you access the management interface via a web browser, you log in with the default “beef” credentials to see the main dashboard.
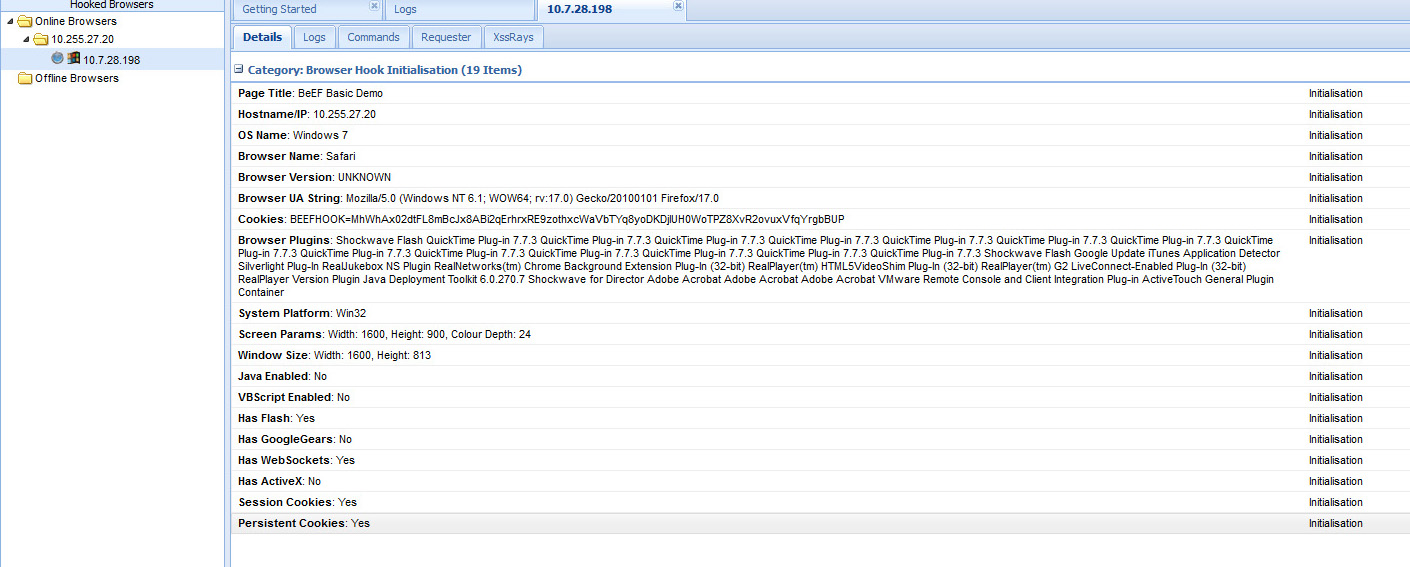
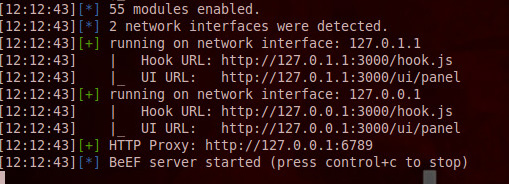 Dashboard and Hook IP Addresses. Shows BeEF server is running
Dashboard and Hook IP Addresses. Shows BeEF server is running
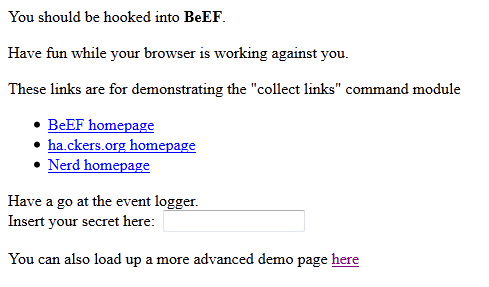
You can change the hook URL and hide it many ways such as through phishing emails, posting on message boards, social media websites, etc. BeEF includes two demo websites to test the hooking function (see below). All you need is a victim to click the hook link and you own the browser even if the victim disconnects and reconnects later.
Websites to test Hooking victims
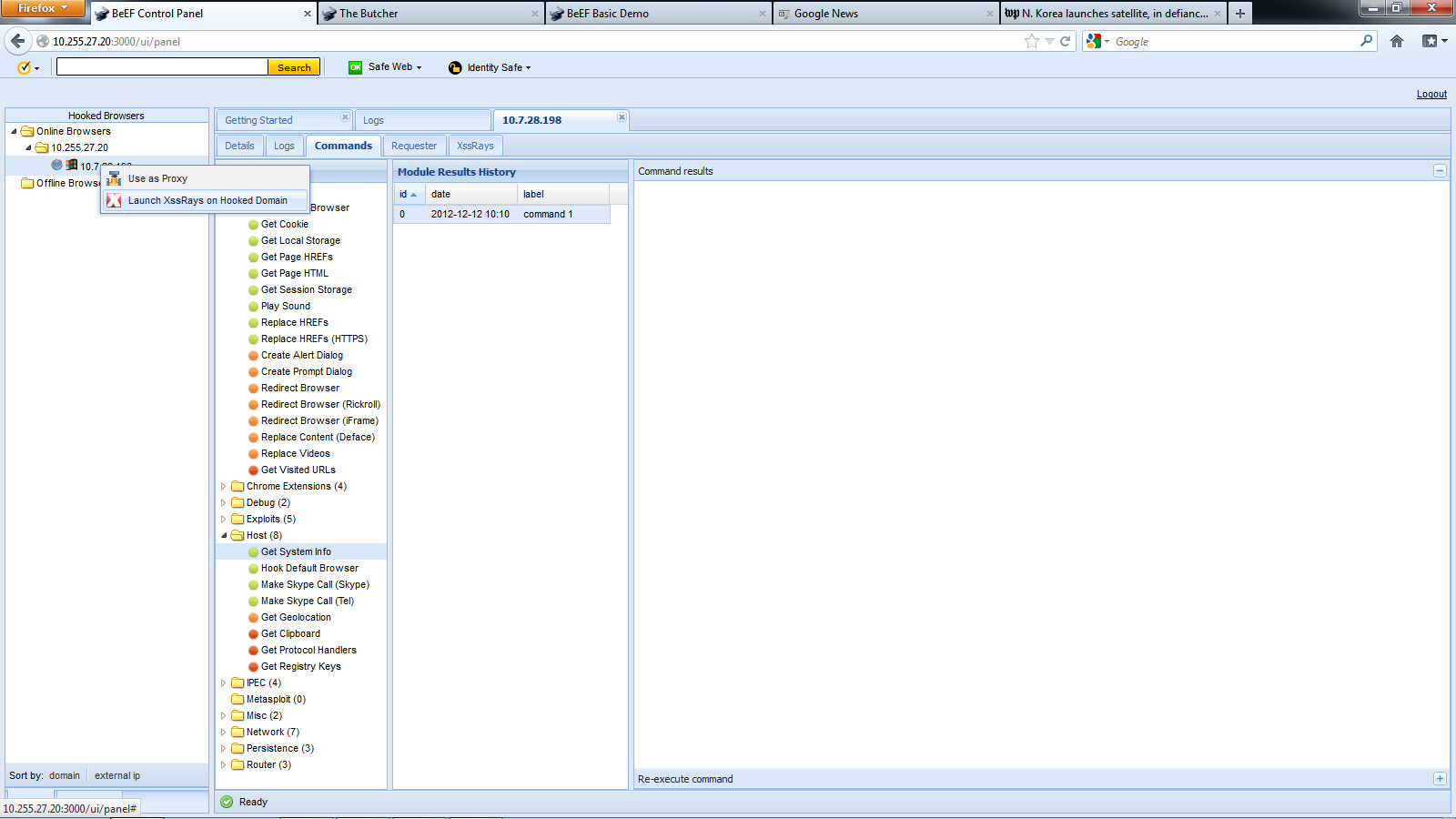
The main dashboard shows active and offline hooked browsers. You can click an active browser and choose java based command modules that are available based on how vulnerable the victim’s browser is to various exploits. BeEF provides a range of attack options with explanation of what will happen as well as risk of being exposed.
Module Command Options
Hooked Windows PC
The pictures above show me hooking my windows laptop. You can see I’m using Firefox, windows 32, my browser plugins, if scripts or java is enabled and other useful information. I can execute commands on hooked machines such as make a sound chime, grab session cookies and even use the hooked browser as a proxy to attack other systems. A test example is having the hooked system log into Facebook and using BeEF to capture the session cookie. An attacker can reply the authenticated session and have full access to the victim’s Facebook account. The possibilities for evil and destruction are endless.
Defending against browser based penetration tools is difficult. Best practice is keeping all host applications including browsers up to date with patches, disabling the use of Java and Flash without manual acceptance per use, content security solutions to identify known malicious sources and most important … end user training on popular social networking attacks. The majority of victims to penetration tools such as BeEF are users clicking links included in emails or social media guests sharing things while claiming to be someone they are not. As always, end users are the weakest link for these types of attacks so make sure to invest in cyber security training!
Authors: Joseph Muniz and Aamir Lakhani
Joseph Muniz – www.thesecurityblogger.com