Controlling who and what access your network is a critical element to keep your resources safe from malicious threats. Network Admission Control (NAC) solutions like the Cisco Identity Services Engine (ISE) can police who and what is permitted network access as well as enforce policy for those devices. Examples would be permitting an administrator with a government furnished Windows 7 laptop access to VLAN 10, which holds internal servers, while provisioning a marketing professional’s iPad with VLAN 20 access, which is limited to Internet and email through the use of ACLs.
But what happens once a device is granted network access? Access control solutions are pretty much out of the picture, aside from limited profile monitoring for identifying changes in device types. (Examples of this limited functionality include figuring out that an “Apple Device” is really an “iPad” based on DHCP and other traffic seen while the user is browsing the network, or blocking a user who attempts to spoof a printer’s MAC address to gain network access.)
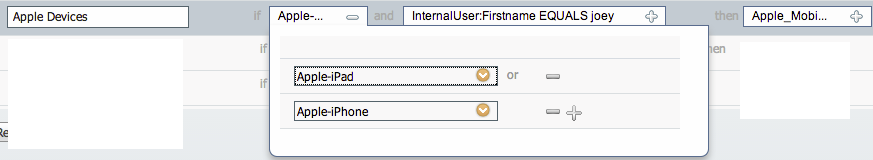
Example ISE policy for profiled Apple iPad or iPhone and User “Joey” to get Apple_Mobile Access
Beyond this is where the handoff to an internal monitoring solution such as Lancope’s StealthWatch System should come into play. An internal monitoring solution can handle security where the access control solution leaves off. These solutions monitor all devices on the network for performance and suspicious behavior, regardless of whether or not they were approved by NAC. Examples of devices that NAC solutions may miss are virtual systems inside the data center, network sharing such as turning an iPhone into a wireless hub, Linksys routers using NATing to hide unauthorized access, or devices accessing a part of the network without access control.
An important function of a post access control solution is identifying devices compromised while on the network, since most access control solutions only verify policy for patch updates and other installed security applications (e.g. antivirus). Being compromised while on the network can happen when users surf the Internet, plug in a USB drive hosting malware, open an infected email, etc. In most cases, the threats that compromise internal users are not common viruses, meaning there isn’t a known signature that can be used by antivirus or firewall technologies to flag the attack. A post access control technology that leverages behavior as the means to identify threats can catch not only insider threats posed by authorized users, but also stealthy, externally-launched threats that bypass the security measures typically enforced by a NAC policy.
The integration of Cisco ISE for access control and Lancope’s StealthWatch for internal network monitoring saves customers money by leveraging NetFlow data already inherent in routers, switches and other network infrastructure devices to essentially turn the entire network into a giant sensor grid for detecting anomalous activity. Both Cisco and Lancope use industry standards leveraged by most vendor equipment (Cisco ISE using 802.1x and Lancope using NetFlow). Both companies also offer physical and virtual versions of all solution components, and both can be architected in a centralized or distributed design.
Here are the beneficial actions that can be taken by combining access control and internal monitoring:
- Enforce policy on devices accessing the network.
- Identify unauthorized devices not seen by NAC.
- Monitor devices for threats and performance during their entire lifecycle on network.
- Know who and what is on the network as well as what they are doing.
- Automatically provision network access for trusted users and guests.
- Identify threats on the internal network including malware, botnets and data loss.
- Limit access for remediation of an identified threat.
- Document a threat’s entire presence on the network for information assurance.
And here are the steps for setting up Cisco ISE and StealthWatch within a network:
Click here for more information on how Cisco and Lancope work together to defend governments and enterprises against advanced threats.