Many network administrators do not have a method to know what is on their network. Devices may be very basic yet use IP for updates or heartbeat purposes (examples are printers, card readers, even some refrigerators). Other issues could be users not having administrator privileges to their systems or recently the demand to bring personal mobile devices onto the network. For these and other reasons, the visibility on what is on the network is becoming blurred.
Many network administrators do not have a method to know what is on their network. Devices may be very basic yet use IP for updates or heartbeat purposes (examples are printers, card readers, even some refrigerators). Other issues could be users not having administrator privileges to their systems or recently the demand to bring personal mobile devices onto the network. For these and other reasons, the visibility on what is on the network is becoming blurred.
Cisco released its flagship access control solution Cisco Identity Services Engine ISE last year with the goal of using identity as a means to provision network access. Many people evaluating Network Admission Control solutions get caught up with the concept of denying rather than understanding a core purpose of these solutions is identification. Cisco ISE is able to profile devices using a number of network probes that analyze the behavior of devices on the network to determine what they are. Probes are optional yet best practice is to enable as much as possible to gain the best network visibility. Some options for probes are Netflow, DHCP, DHCP SPAN, HTTP, Radius, NMAP, DNS, SNMP Query and SNMP Traps. Ports used are configurable as well as device profiles. For example, if a Avaya phone requires DHCP as a requirement for identification, that requirement can be adjusted if DHCP is not available.
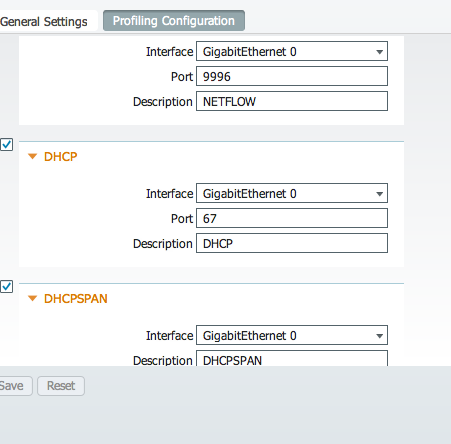
To prove the ISE network monitoring concept, I stood up a ISE system on a small server, enabled all profiling probes and let it sit on my network overnight. ISE did not have AAA setup, user information, 802.1x or device management enabled. Consider this ISE system a server / laptop plugging into a DHCP port and sniffing the wire using profiling probes.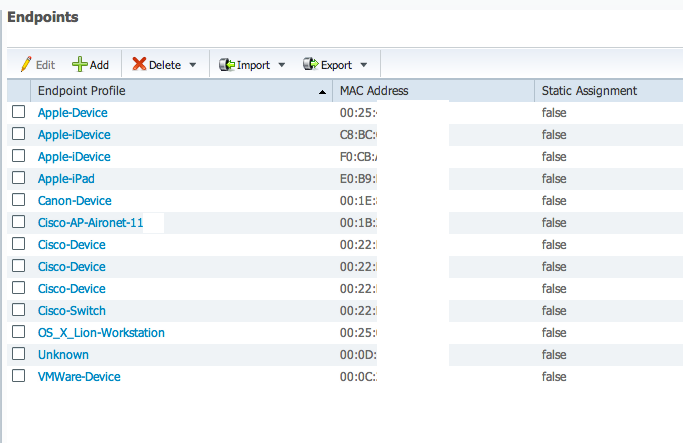
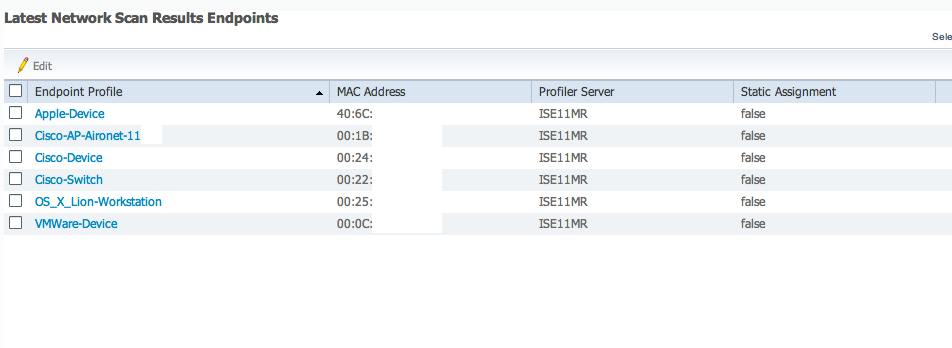
My network is very basic. I have a small Cisco Firewall providing LAN access with a ROKU Netflixs player, Blue Ray device (off during test) and Cisco Access Point powered from the firewall. ISE was able to identify my laptop as a Apple Workstation running Lion, my printer as a Canon device (I turned it on for 5 minutes to scan a document and powered it down), MACMINI as a apple device hosting VMWare, Apple iPad connecting to the Access Point and iPhone connected but not surfing the internet (seen as Apple iDevice since it generated little network traffic). This was done without using the new NMAP feature.
I verified findings by launching a NMAP scan and found a consolidated list of active devices. (Note this is the MR1.1 release however 1.1 includes NMAP as well)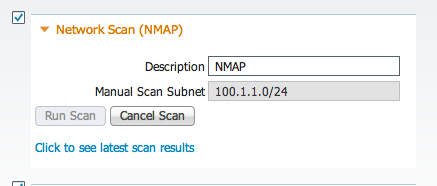
Cisco Identity Services Engine ISE is a very powerful access control tool yet many forget the simple things in life. Consider ISE for identifying what is on your network using profiling as a network monitoring tool. Its a great first step to establish your network policy.