I have been preaching the value of reputation security for years. For those that don’t know what it is, it is a way to validate the credit score so to speak of a resource before allowing a connection. If a user attempts to access a “banking” website, reputation security would first validate if the source could or could not be a bank. If the website has been online for a few hours, hosted from go daddy, associated with a domain owner of malicious websites, then its obviously not a bank and should be blocked. I have posted details about reputation security HERE. For those in the education space, this isn’t a violation of freedom of speech since its only blocking malicious websites and providing referenceable information why the source was blocked. I suggest all businesses use this capability whenever possible.
The HackerNews posted about a new malvertising campaign that targets Google ads. The goal is to trick the victim to click an ad so they are redirected to a malicious website that links to various malware files hosted from Dropbox or Onedrive. The details of how this campaign works can be found on the post HERE.
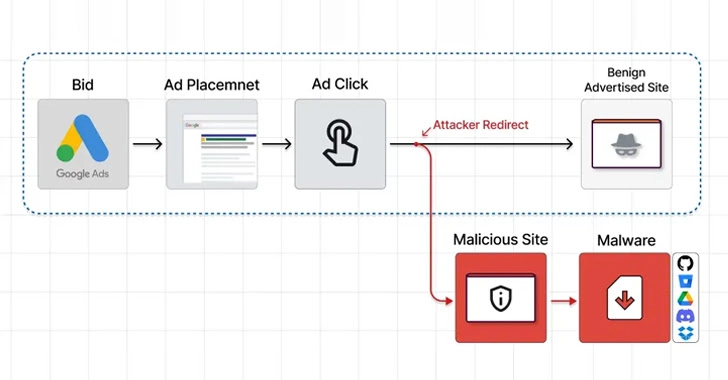
What is the best defense? Defense in depth is always the best option meaning a combination of endpoint detection and response, web filtering, system hardening, etc. etc. however reputation security should be the FIRST line of defense. The Attacker redirection should be identified as a risk based on factors surrounding how long it has been up, where its located, who the domain owner is and other identifiers.
Most modern security vendors offer reputation security as a filtering or blocking feature (Proofpoint email, microsoft email, cisco email, cisco NGFW, Fortinet Firewalls, Palo Alto Firewalls, etc. etc). I highly suggestion you test to see if your organization is using it by going to ihaveabadreputation.com. If you see a block page, that is a good thing. If you see a ghost saying you would have been owned, you lack reputation security and should look to enable it. If your block page is coming from a gateway security tool such as a next gen firewall, that is good, but a better option would also look to enable it at the host level. This way when a host is not behind the NGFW, they are still protected. The following image is an example of Microsoft Defender SmartScreen blocking this test website.


