Interesting release from Malwarebytes regarding a new type of ransomware that targets Mac systems. This goes to show that Macs can be infected with malware and most likely will continue to be a focus for malicious attacks as Apple wins marketshare. Yes, Windows based systems have more known malware in the wild however, Macs are not necessarily more secure as many people believe. The original article can be found HERE. Credit due to Jerome Segura (@jeromesegura), senior security researcher at Malwarebytes and the rest of his team.
For years, Windows users have been plagued by ransomware demanding several hundred dollars to unlock their computers.
The bad guys know there is a growing market of Apple consumers who, for the most part, feel pretty safe about browsing the Internet on a Mac without the need for any security product.
Cyber-criminals, well known for not re-inventing the wheel, have ‘ported’ the latest ransomware to OS X, not by using some complicated exploit but rather leveraging the browser and its ‘restore from crash’ feature.
(Scroll all the way to the end of the post for a video on how to remove this Apple ransomware.)
he ransomware page is being pushed onto unsuspecting users browsing regular sites but in particular when searching for popular keywords.
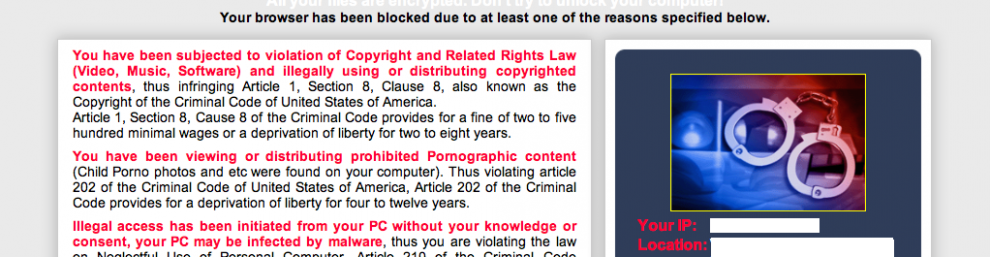
Warnings appearing to be from the FBI tell the victim: “you have been viewing or distributing prohibited Pornographic content.. To unlock your computer and to avoid other legal consequences, you are obligated to pay a release fee of $300.”
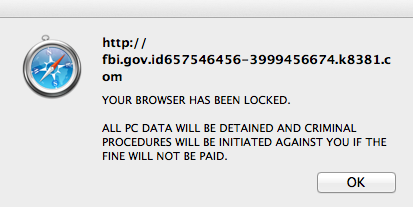
A quick look at the address bar shows an interesting URL: fbi.gov.id657546456-3999456674.k8381 . com, the bad guys are clearly trying to fool users.
If you choose to ignore the message (which you should), you cannot get rid of the page:
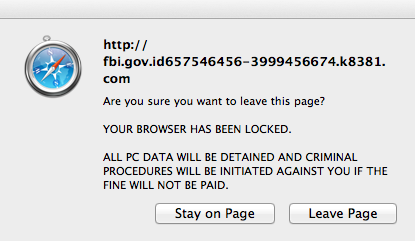
Repeated attempts to close the page will only lead to frustration as even the “Leave Page” browser trick does not work:
If you “force quit” the application, the same ransomware page will come back the next time to restart Safari because of the “restore from crash” feature which loads backs the last URL visited before the browser was quit unexpectedly. Talk about a vicious circle.
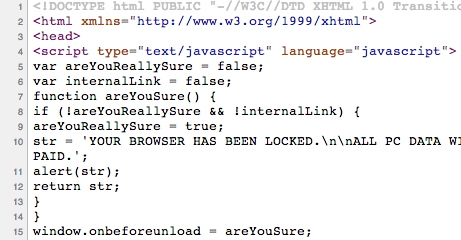
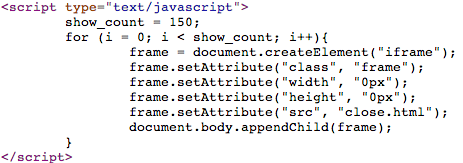
This is how it is done, by using some JavaScript code:
The “infinite loop” (which really isn’t) is made possible by 150 iframes created dynamically by this JavaScript snippet:
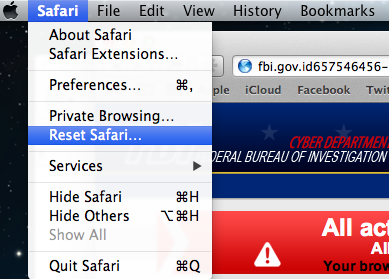
There is a way to get rid of it (without clicking on the prompt 150 times) and more importantly without paying the $300 ransom. Click on the Safari menu and then choose “Reset Safari”:
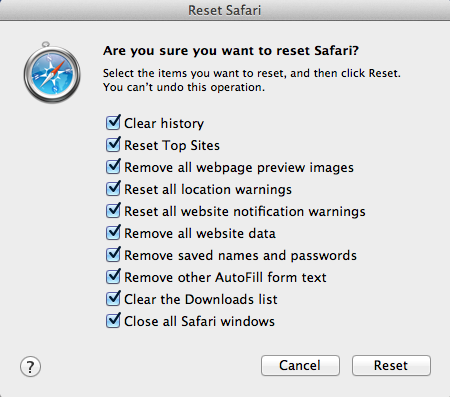
Make sure all items are marked and hit the Reset button:
You can bet many people are going to fall for this scam and pay the ransom money, filling the bad guys’ pockets.
Whenever alarming messages are displayed, it is important to take the time to review them, call a friend or talk to someone about it.
The bad guys know how to use social engineering to entice victims as, for example, I was lead to this locked page by doing a search for Taylor Swift on Bing images. The victim will feel they may have actually being doing something wrong and got caught and ashamed, will pay the “fine.”
This scam is unfortunately all too efficient and is not going away anytime soon.
Watch this tutorial on how to get rid of the FBI ransomware for OS X.