
What is reputation? By definition “Reputation is the opinion (more technically, a social evaluation) of the group of entities toward a person, a group of people, or an organization on a certain criterion. It is an important factor in many fields, such as education, business, online communities or social status”. Older security technologies use signatures of known bad elements however those remain static and can’t detect changes without regular updates. Many leading vendors are realizing it’s easier to watch the change of Reputation of information rather than trying to capture signatures of attacks and updating their technology.
Cisco looks at this from the web viewpoint. They acquired Iron Port a few years ago, which relies on their “sender base” research of web and email Reputation (www.senderbase.com). Sender Base looks at things like how long a website has been up, what type of content is present, has the sender been flagged for spamming, etc. to develop a credit score of the traffic. An example of this is how I launched my hip-hop group’s website and it was flagged with a mid range credit score based on it being up for a few days and the hosting agent being a group hosting firm. It took a few weeks before my group moved into a safe music site category.
Another area Cisco uses this is for email security. Spammers have cleaver ways to bypass standard security scanning technology. Some common methods are using spotting to slightly change the message (IE d.o some.th ing like th is) or including links to phishing websites that pull down the bots post email.
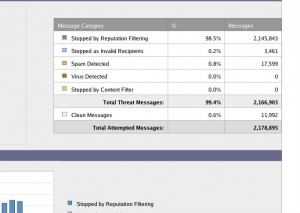
We use Iron Port at WWT, which below shows I’ve received 2,145,843 emails this month that were blocked based on bad reputation. Only a few got through and had older scanning technology catch them, which is crazy that 98.5% of my email is crap.
Symantec is starting to use reputation from a different viewpoint by looking at the reputation of application use. They are looking at things like how many people are using an application, where did it come from, etc. to determine if it can be installed. Think about it, who wants to be the first person in the world to install a software application? I think it’s pretty awesome to create a check that says “ only install application form these vendors that at least a thousand people have installed as a security checkpoint prior to scanning it for viruses. (http://www.symantec.com/business/theme.jsp?themeid=insight)
Word from both Cisco and Symantec is that reputation will appear in more of their security products. Reputation seems like the future of real-time defense and a lot faster to leverage since there isn’t a time wasted on scanning.




