Researchers have found a simple trick they can use to once again decrypt the notorious Jigsaw ransomware. The Check Point Threat Intelligence Research team explain they made their discovery on Friday while investigating the ransomware’s user interface. Here is the info from this post.
The Jigsaw ransomware was first spotted in April 2016, and has since received a bit of traction. It became infamous thanks to an image of the Jigsaw killer from the movie ‘Saw’ displayed on the ransom note (hence its name), and its unique way of persuading victims to comply – if payments aren’t made within an hour, Jigsaw starts deleting files from the infected machine.
While investigating the latest Jigsaw Ransomware variant (SHA256: 61AA800584B170FFE9959ACD057CCAF784BF3088E1D3AAB39D07C0793F6C03DF) and its false claims to steal users’ credentials and Skype history, we came across the mechanism the ransomware uses to check whether payments have been made.
Jigsaw provides the user with a convenient GUI:
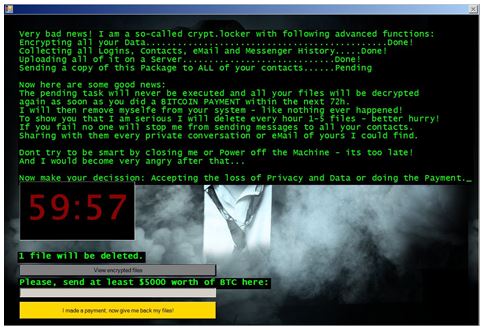 “When the user presses the ‘I made a payment, now give me back my files!’ button, the program makes an HTTP GET request to:
“When the user presses the ‘I made a payment, now give me back my files!’ button, the program makes an HTTP GET request to:
btc.blockr[.]io/api/v1/address/balance/
and as a response, gets the following
json: {“status”:”success”,”data”:{“address”:””,”balance”:0,”balance_multisig”:0},”code”:200,”message”:””}
This got us thinking – what if we change the request, so it queries a different account? Perhaps one that holds the necessary amount of Bitcoins to decrypt our files? Or even better – what if we change the response to say we have the necessary amount?”
Curious, the researchers changed the “balance” variable from 0 to 10. To their delight, Jigsaw interpreted this change as receipt of payment and began decrypting the files!
But it gets better. The decryption trick appears to work on older variants of Jigsaw. Once complete, the process also leaves no trace of the ransomware on an infected machine.
 Researchers have successfully decrypted every version of this file-deleting ransomware since its discovery back in April, including its “CryptoHitman” alter-ego. Jigsaw has made several updates in that time span, including the addition of a live chat feature. But none of those features have put a stop to the work of several knowledgeable security researchers.
Researchers have successfully decrypted every version of this file-deleting ransomware since its discovery back in April, including its “CryptoHitman” alter-ego. Jigsaw has made several updates in that time span, including the addition of a live chat feature. But none of those features have put a stop to the work of several knowledgeable security researchers.
Check Point has built a decryption tool that incorporates this latest trick. It is freely available for download here.
But even though he’s happy about his team’s discovery, Lotem Finkelsteen, who leads Threat Intelligence Operations at Check Point, believes we haven’t seen the last of Jigsaw:
“The fact that security companies and independent researchers have published decryption tools for it and this did not prevent Jigsaw’s developers from creating and issuing new versions of this ransomware is telling.”
With that in mind, users should continue to avoid clicking on suspicious links and email attachments, make sure their anti-virus solution is up-to-date, implement all software updates when they become available, and regularly back up their critical data.