Every once in a while I get time to check out what new security technologies are popping up. Last week at Cisco Live I met the Centripetal Networks team and saw a impressive demo of their RuleGate solution. This post will provide a general overview of what I saw with some screenshots of their offering.
Centripetal Networks goal is to shorten the time a threat intelligence source produces data and that data is delivered to a security tool to take action against the threat. Typically the time to accomplish this takes a while as research has to be converted into a feed and a vendor has to important that feed as well as have it impact defenses in some manner. Also many security solutions are limited to how many checks can be enabled meaning a well tuned IPS may have 8-10 thousand checks and bundled with a application layer firewall may have 30-40 thousand checks.
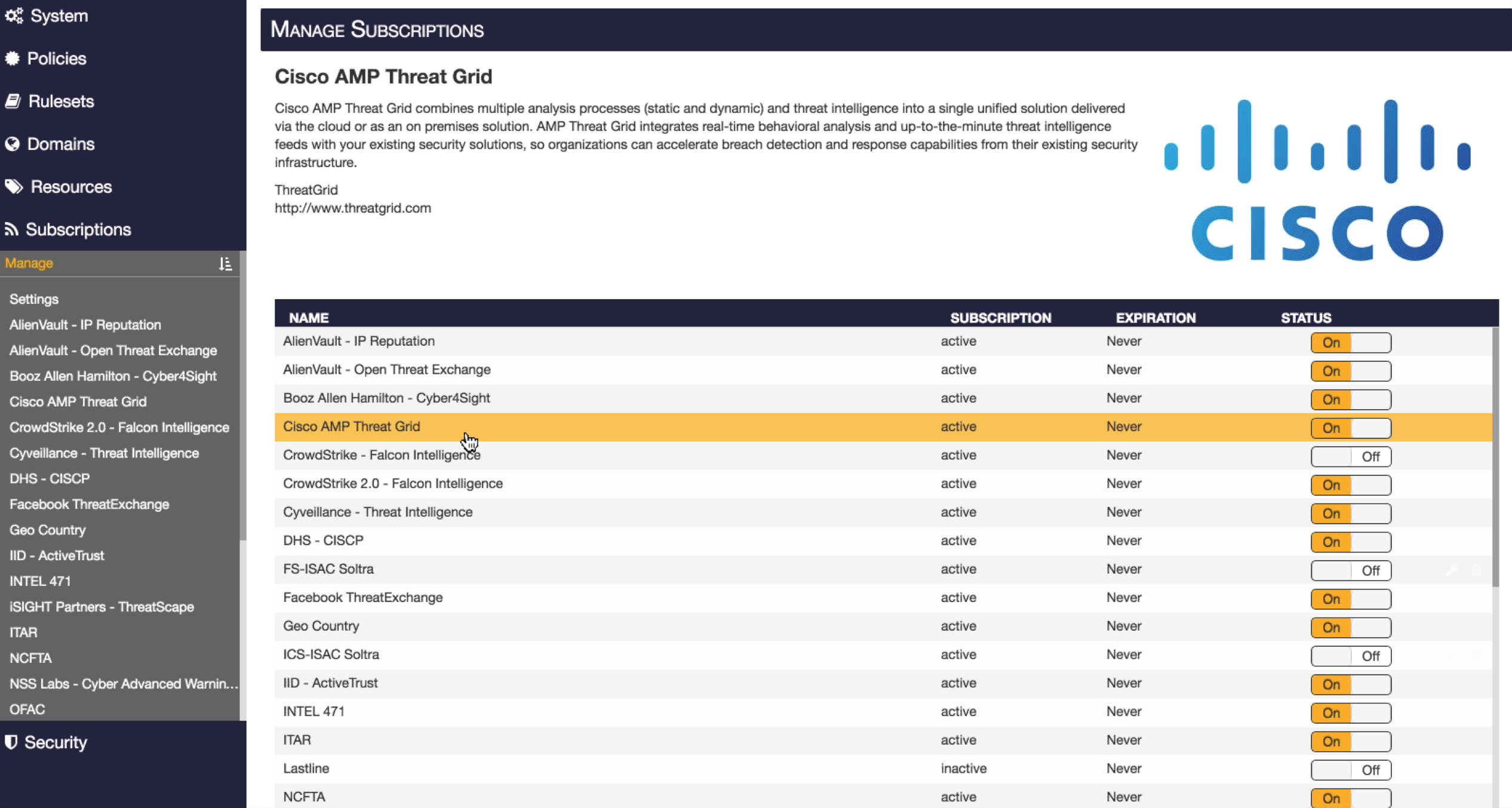
Centripetal showed me their approach to these issues by enabling multiple feeds that provide around 5 million checks when fully enabled. Threat feeds come from various open source and enterprise services and can be immediately transferred into action, which can be block the threat, trigger an alarm or generate a PCAP of the incident. The next screenshot shows the dash board presenting a ton of feeds including the highlighted Cisco AMP ThreatGrid feed. Note the enterprise feeds are not managed by Centripetal so they must be purchased by the feed provider.
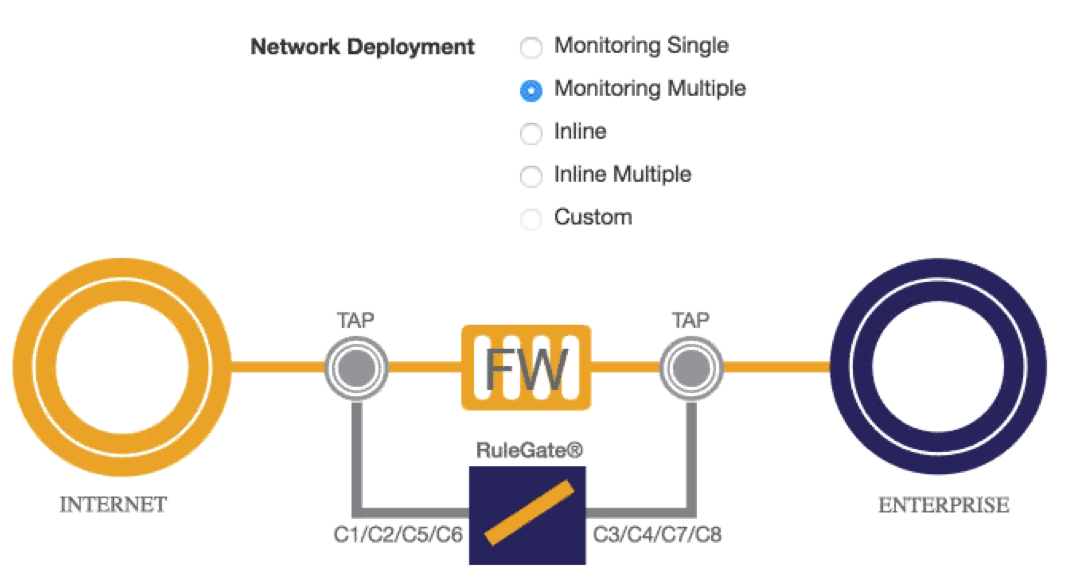
 Centripetal’s RuleGate solution can be deployed inline or as a tap providing assessment and blocking capabilities. If inline and in front of the firewall, it can filter a ton of the attacks that would normally hit the Firewall. The next two images show the RuleGate dashboard displaying deployment options.
Centripetal’s RuleGate solution can be deployed inline or as a tap providing assessment and blocking capabilities. If inline and in front of the firewall, it can filter a ton of the attacks that would normally hit the Firewall. The next two images show the RuleGate dashboard displaying deployment options.
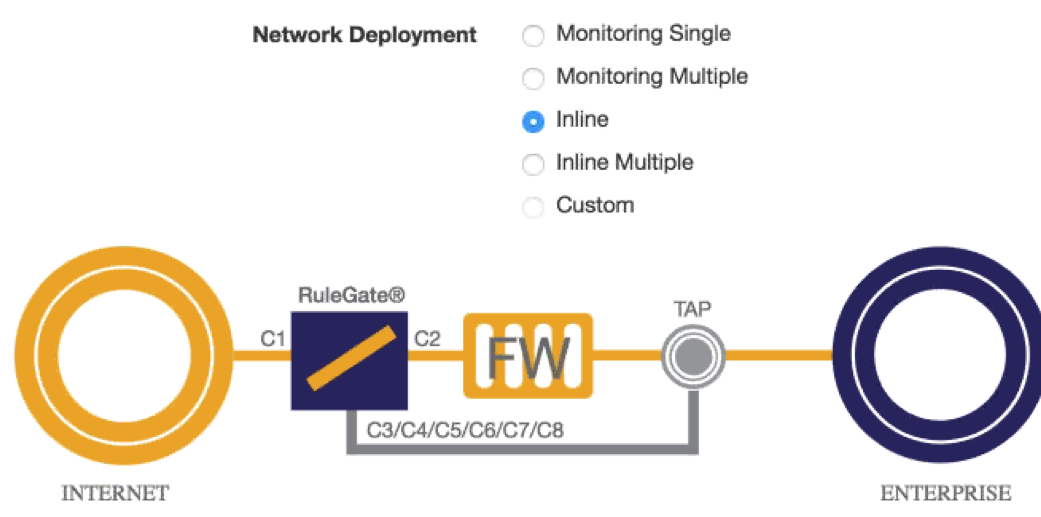 RuleGate Inline and In Front of the Firewall
RuleGate Inline and In Front of the Firewall
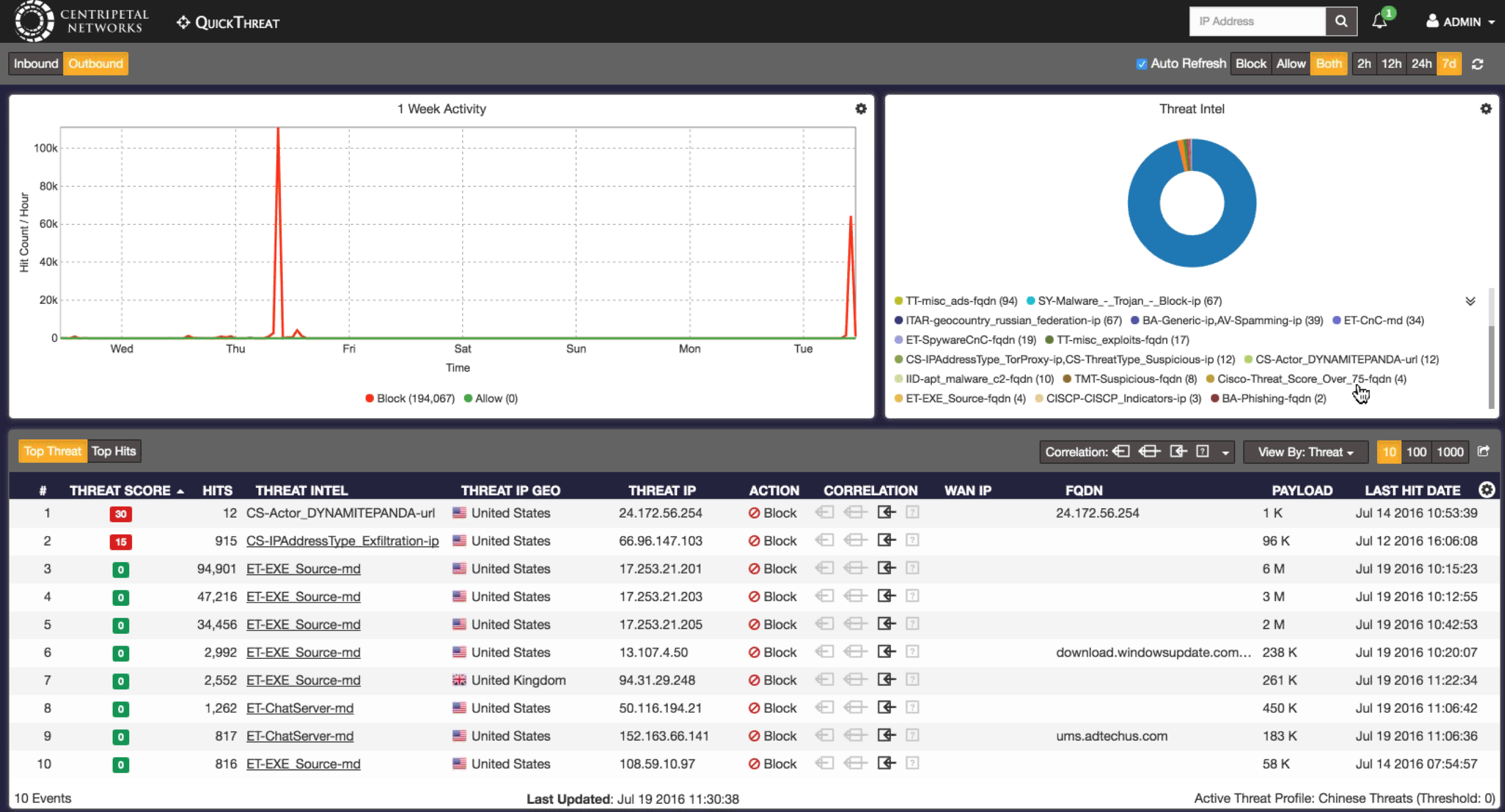
The idea is having various threat intelligence sources feeding indicators of compromise (IOC) data so RuleGate can quickly take action or correlate and inform administrators of breaches. The next image shows the RuleGate dashboard displaying the Threat Intel doughnut that represents IOCs that have triggered, their risk level and which threat feed the rule came from.
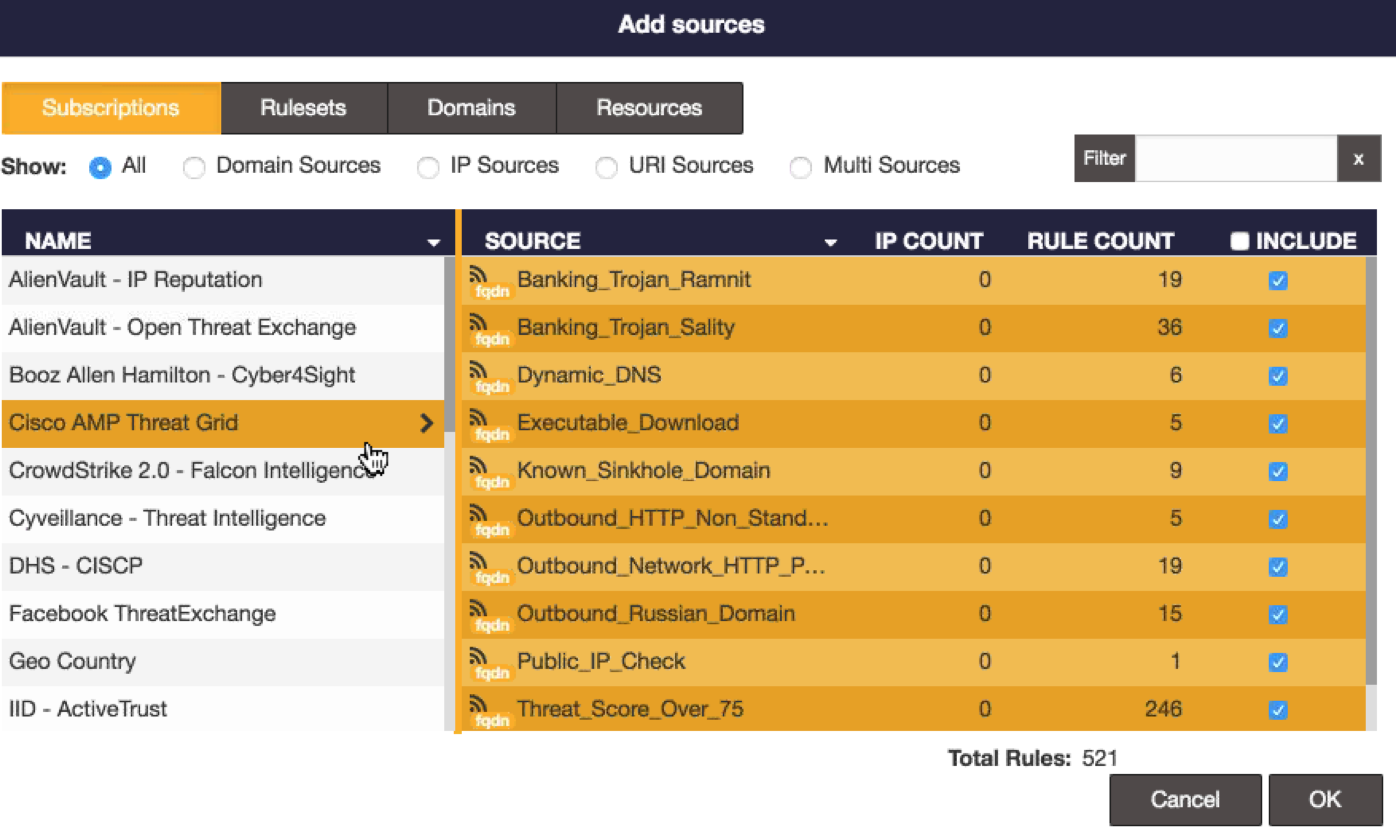
 Centripetal Networks likes to provide assessments with the RuleGate solution by placing it on a network with all feeds enabled and monitoring it for rules being triggered. They can come back and recommend which open source and enterprise feeds should be considered based on rules that were triggered. The next image shows how adding the Cisco AMP Threat Grid feed is increasing the count by 521 new IOCs to check for.
Centripetal Networks likes to provide assessments with the RuleGate solution by placing it on a network with all feeds enabled and monitoring it for rules being triggered. They can come back and recommend which open source and enterprise feeds should be considered based on rules that were triggered. The next image shows how adding the Cisco AMP Threat Grid feed is increasing the count by 521 new IOCs to check for.
 I found this tool to be a pretty cool new approach to leveraging threat data. They don’t do signature based data today outside of using partnerships but they mentioned that may be coming. I personally like the idea of not only having threat data centralized but also validating which vendor IOC rules are triggered to validate the value of paying for the feed. Learn more about these guys at http://www.centripetalnetworks.com.
I found this tool to be a pretty cool new approach to leveraging threat data. They don’t do signature based data today outside of using partnerships but they mentioned that may be coming. I personally like the idea of not only having threat data centralized but also validating which vendor IOC rules are triggered to validate the value of paying for the feed. Learn more about these guys at http://www.centripetalnetworks.com.