Cisco recently announces the intent to acquire CloudLock as explained HERE. I had the opportunity two weeks ago at Cisco live to meet the CloudLock team and get a demo of the solution. This blog post will provide an overview of CloudLock with screenshots of their demo.
CloudLock is a Cloud Access Security Broker (CASB) and Cloud Cyber Security solution. What does that do for you and your organization? Think about all the people with smart phones containing tons of applications connected to everything under the sun. Many times users don’t even know what they are sharing on the cloud or unaware of potential risks and policies they are breaking. My talk at DEF CON in two weeks will show an example of this when users enable the FLICKR app to share any photographs from their phone including when they scan in pictures of checks for other mobile banking applications or sext their girlfriend a picture they probably didn’t intend to post on the public cloud.
Even applications like Pokemon GO are ultra intrusive asking for access to things it really doesn’t need. Check out this post HERE by adam reeve showing the first version of Pokemon could read your email, send email as you, access your google drive data, look at search history and a ton more!
 Bringing the conversation to the office, lets consider the sales person that has games and Salesforce installed on his or her phone. In many cases, applications will ask the user if they want to authenticate accessing one cloud system using another such as using a Facebook account to access a game in the cloud. This is called Open Authorization (OAuth) (more on this HERE ) and can potentially give users the permission to connect a cloud resource containing sensitive information to an untrusted cloud source. Think about FLICKR auto sharing the checks used by the banking application as an example or the game app having access to Salesforce data. The challenge is this happens all the time and IT can’t do anything about it since the users are making this happen with these applications. . The next example shows the app Podio requesting access to other cloud resources essentially connecting two clouds.
Bringing the conversation to the office, lets consider the sales person that has games and Salesforce installed on his or her phone. In many cases, applications will ask the user if they want to authenticate accessing one cloud system using another such as using a Facebook account to access a game in the cloud. This is called Open Authorization (OAuth) (more on this HERE ) and can potentially give users the permission to connect a cloud resource containing sensitive information to an untrusted cloud source. Think about FLICKR auto sharing the checks used by the banking application as an example or the game app having access to Salesforce data. The challenge is this happens all the time and IT can’t do anything about it since the users are making this happen with these applications. . The next example shows the app Podio requesting access to other cloud resources essentially connecting two clouds.
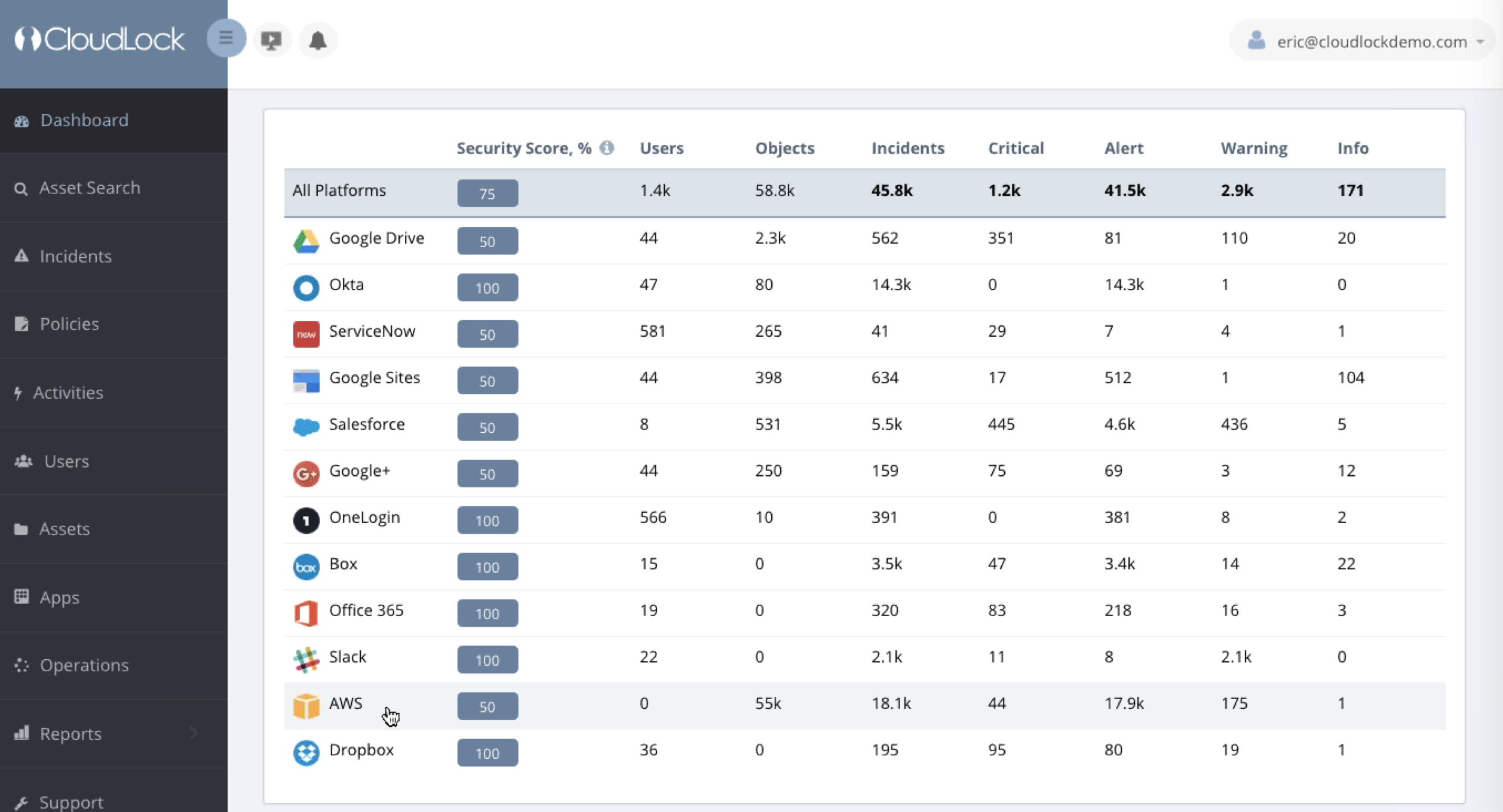
 CloudLock’s goal is to protect data, access to data and control what applications have access to via the cloud. Here is the main CloudLock dashboard giving a view of cloud sources they can protect.
CloudLock’s goal is to protect data, access to data and control what applications have access to via the cloud. Here is the main CloudLock dashboard giving a view of cloud sources they can protect.
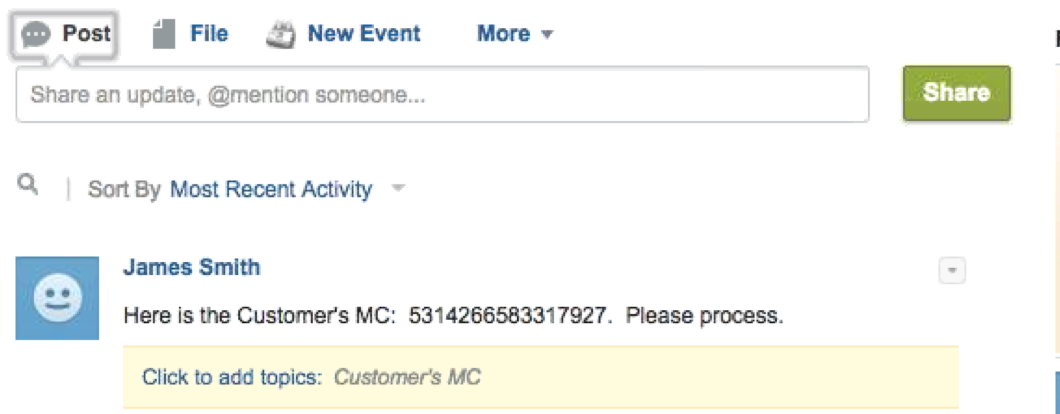
 The idea is now you can take control of securing cloud applications. What does that mean? Well let’s consider an employee posts a credit card number on Salesforce such as this screenshot.
The idea is now you can take control of securing cloud applications. What does that mean? Well let’s consider an employee posts a credit card number on Salesforce such as this screenshot.
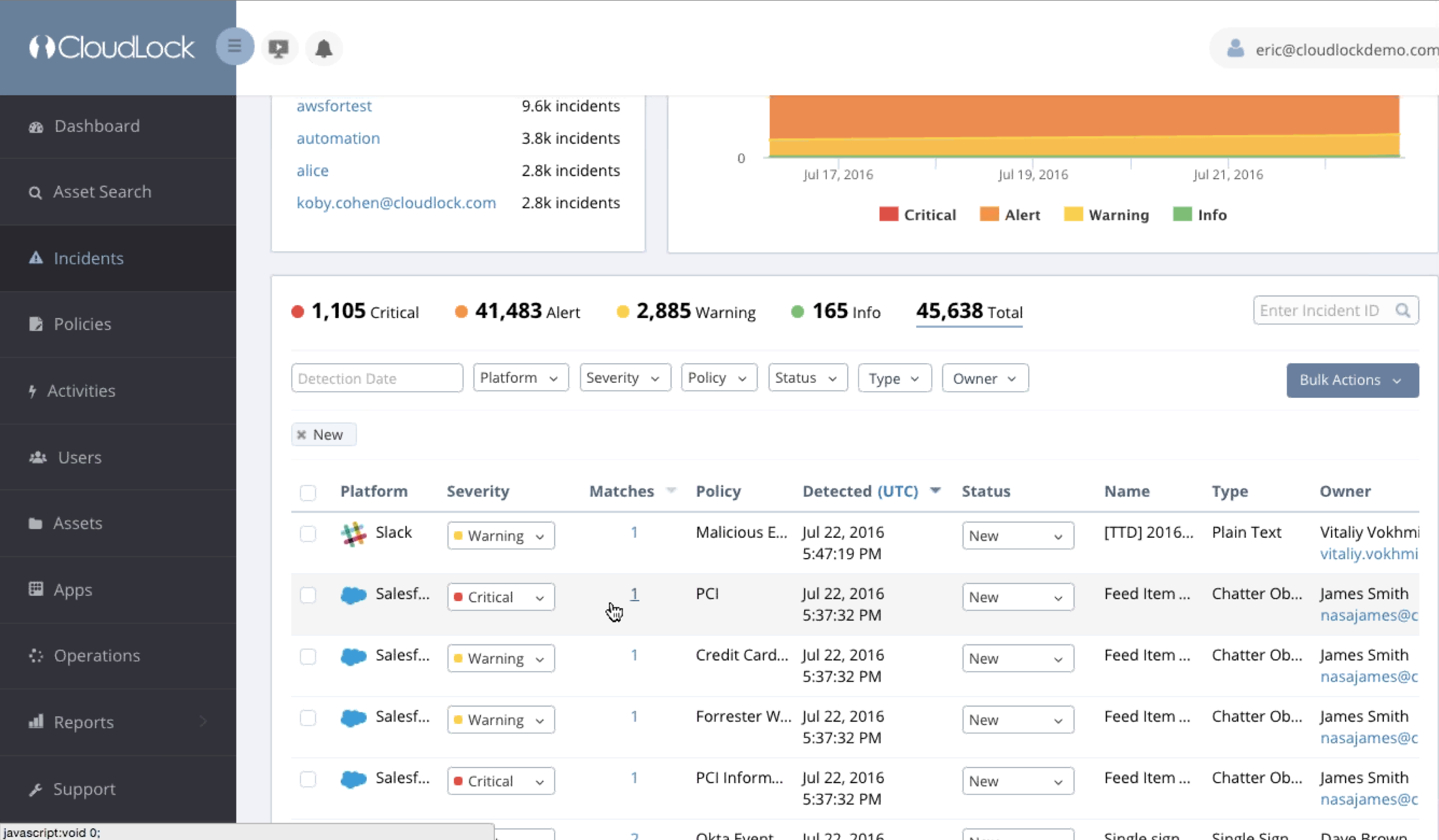
 This is a PCI violation that could lead to bad things or violate compliance regulations within your organization. CloudLock can have security policies enabled so an administrator can be alerted via CloudLock’s security dashboard shown next or through a SIEM pulling in this data. Notice the critical PCI alarm.
This is a PCI violation that could lead to bad things or violate compliance regulations within your organization. CloudLock can have security policies enabled so an administrator can be alerted via CloudLock’s security dashboard shown next or through a SIEM pulling in this data. Notice the critical PCI alarm.
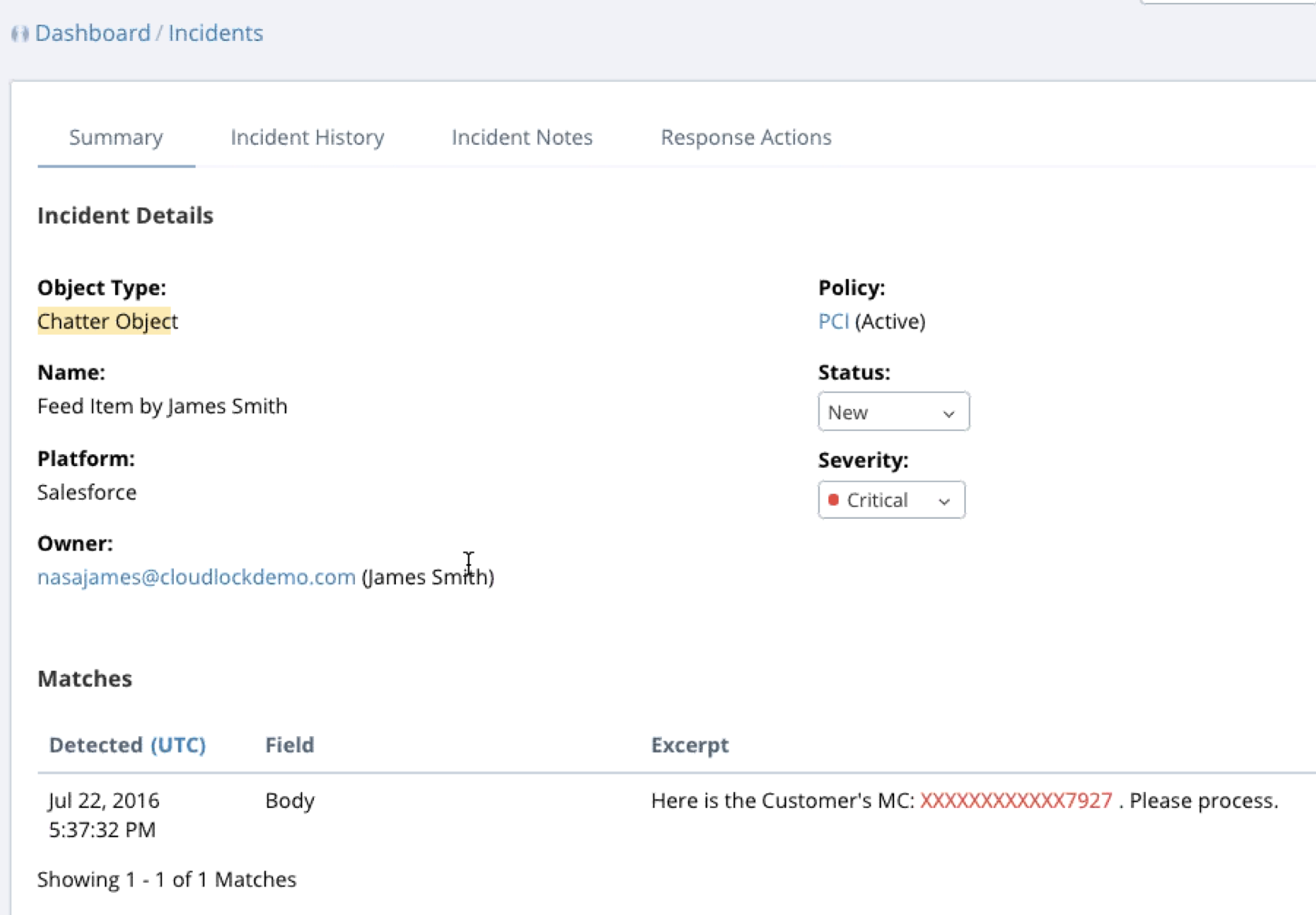
 The administrator may not have rights to see the actual sensitive data so CloudLock can provide enough to show a violation has occurred while masking part of the data as shown with the credit card violation.
The administrator may not have rights to see the actual sensitive data so CloudLock can provide enough to show a violation has occurred while masking part of the data as shown with the credit card violation.
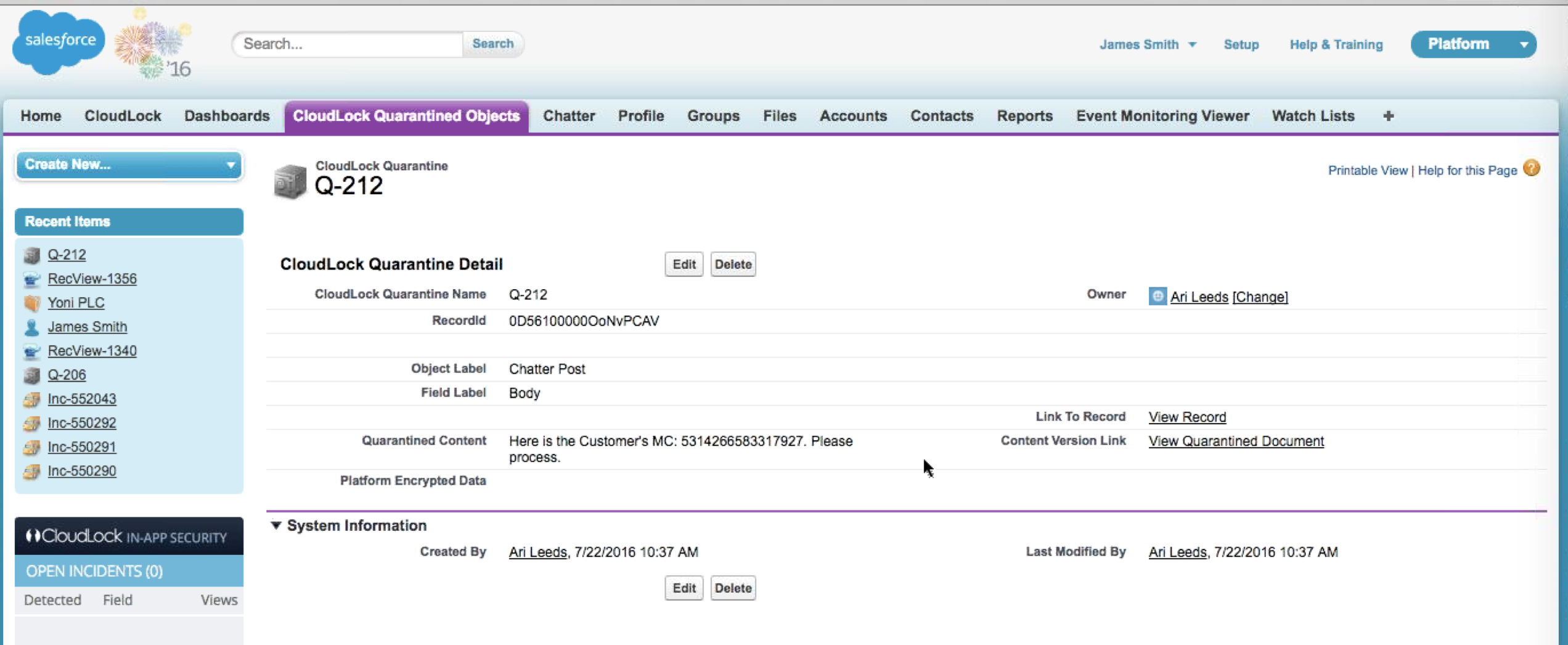
 CloudLock can also take action such encrypting, revoking access to or quarantining the data and only permitting it to authorized people. The next two images show CloudLock quarantining the data, which an authorized person can click and still access while everybody else is blocked essentially permitting business to operate while following PCI policies.
CloudLock can also take action such encrypting, revoking access to or quarantining the data and only permitting it to authorized people. The next two images show CloudLock quarantining the data, which an authorized person can click and still access while everybody else is blocked essentially permitting business to operate while following PCI policies.
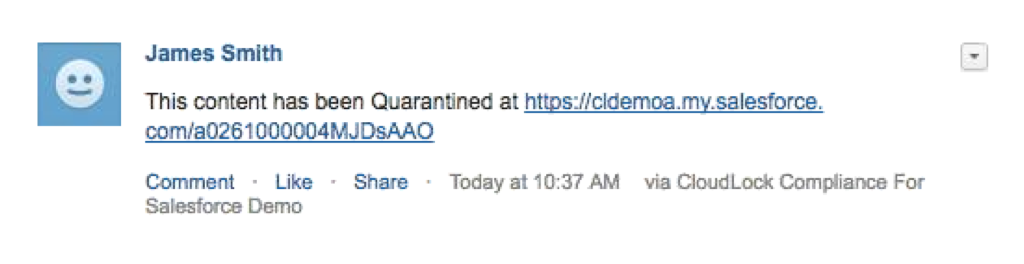 And if you click the link and authorized, you can see the data in Salesforce
And if you click the link and authorized, you can see the data in Salesforce
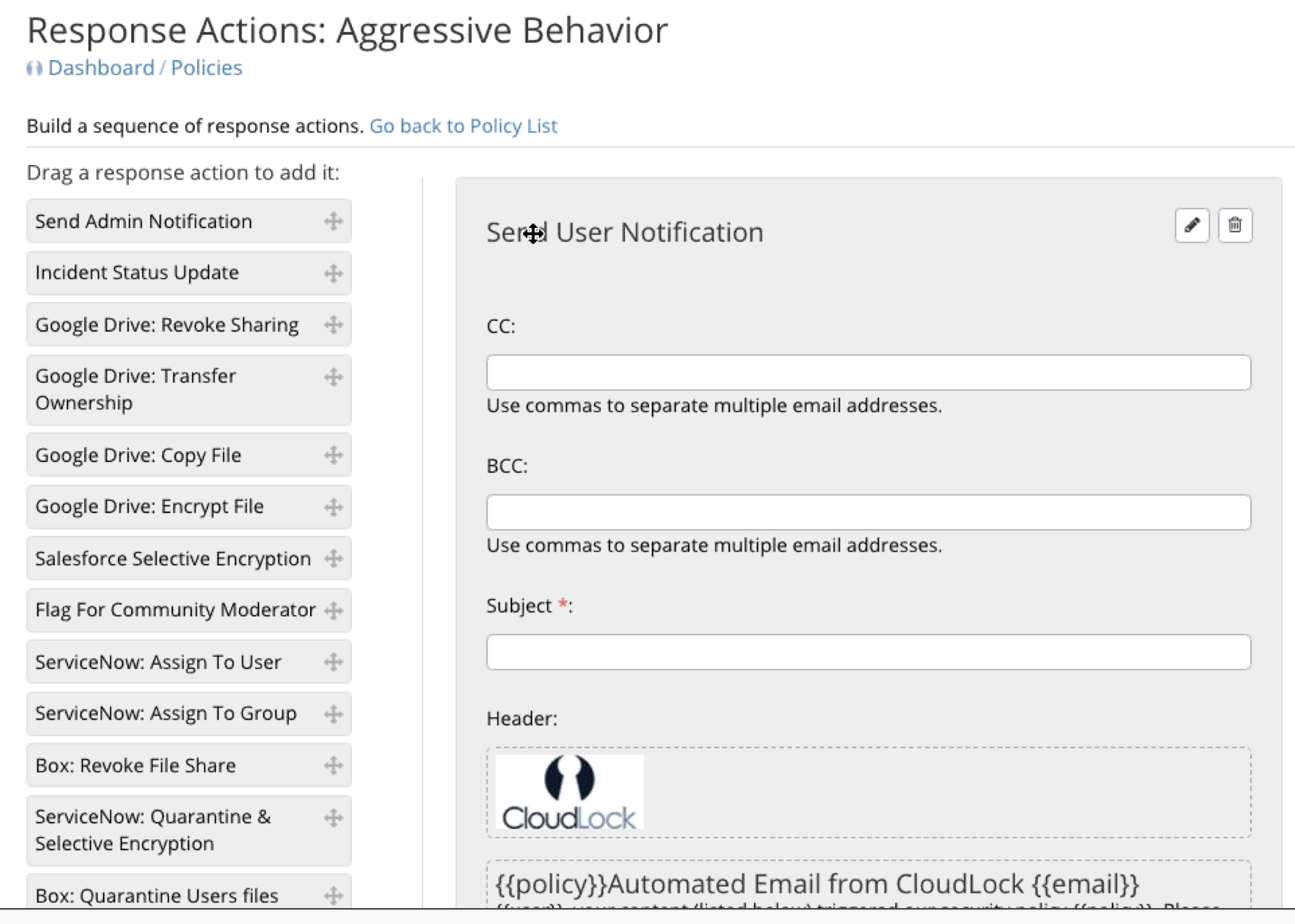
 Half of the battle is user education so they don’t continue to violate policies. The next image shows how CloudLock can provide various responses to violations such as emails, restricting access, warnings and so on including time based responses meaning after a few hours, increase the warning messages if the user is not seeing the violation alerts.
Half of the battle is user education so they don’t continue to violate policies. The next image shows how CloudLock can provide various responses to violations such as emails, restricting access, warnings and so on including time based responses meaning after a few hours, increase the warning messages if the user is not seeing the violation alerts.
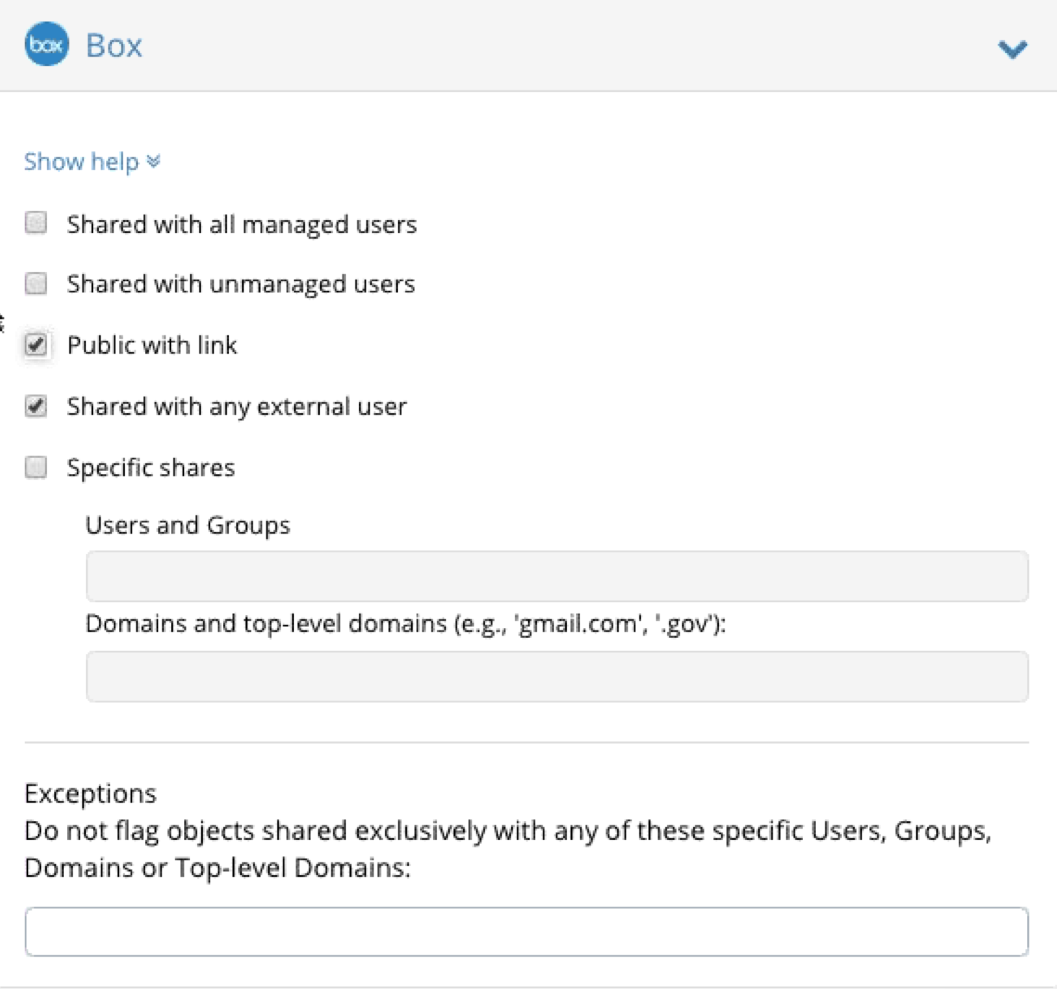
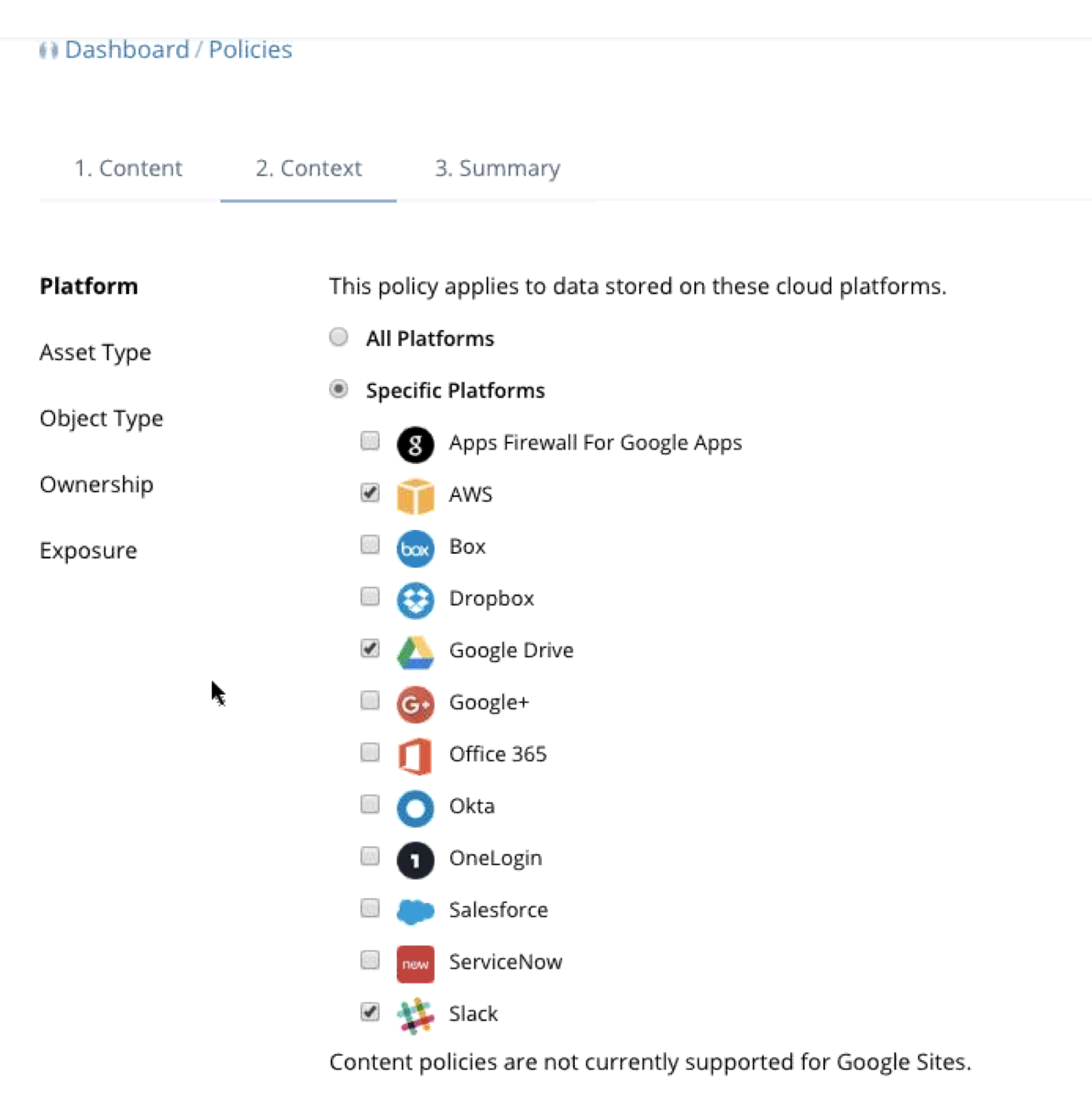
 One common issue with Data loss is false positives. CloudLock has many granular settings to help with this issue such as narrowing down alarms to specific uses of data like credit card data before a flag is issued or having the intelligence to validate a string is indeed a credit card number based on how companies issue card numbers. Exposure can also be considered such as the data can be in Box however if the link to access it is externally facing, then that is a violation due to containing PCI data as shown.
One common issue with Data loss is false positives. CloudLock has many granular settings to help with this issue such as narrowing down alarms to specific uses of data like credit card data before a flag is issued or having the intelligence to validate a string is indeed a credit card number based on how companies issue card numbers. Exposure can also be considered such as the data can be in Box however if the link to access it is externally facing, then that is a violation due to containing PCI data as shown.
 There are many other features such as identifying that I logged into my Box account at 9pm from Washington DC and two hours later logged in from China. This obviously is impossible for me to do so it would trigger a velocity alarm. CloudLock can link policies together such as it is ok to show Joey Muniz and talk about asthma however any document stating Joey and asthma could trigger a HIPAA alarm based on leaking information about me (however I really don’t have asthma … its just an example).
There are many other features such as identifying that I logged into my Box account at 9pm from Washington DC and two hours later logged in from China. This obviously is impossible for me to do so it would trigger a velocity alarm. CloudLock can link policies together such as it is ok to show Joey Muniz and talk about asthma however any document stating Joey and asthma could trigger a HIPAA alarm based on leaking information about me (however I really don’t have asthma … its just an example).
Check out www.cloudlock.com to learn more about what they can do for it. Also expect great things from integrating this technology with Cisco security.




