 Today’s Internet is a dangerous place. Imagine a small village with law and order surrounded by a wall keeping out miles of ungoverned ruthless territory. Most known websites surfed daily by your users make up a small percentage of the total Internet. The remaining 80% or more of uncategorized websites are contaminated with Botnets, malware and short-lived websites targeting your users. Many of these malicious websites are embedded in trusted sites such as social networks by hiding in advertisements or silly links posted by your friends. The best protection for this threat vector is limiting Internet usage to trusted websites and monitoring those websites for malicious applications.
Today’s Internet is a dangerous place. Imagine a small village with law and order surrounded by a wall keeping out miles of ungoverned ruthless territory. Most known websites surfed daily by your users make up a small percentage of the total Internet. The remaining 80% or more of uncategorized websites are contaminated with Botnets, malware and short-lived websites targeting your users. Many of these malicious websites are embedded in trusted sites such as social networks by hiding in advertisements or silly links posted by your friends. The best protection for this threat vector is limiting Internet usage to trusted websites and monitoring those websites for malicious applications.
The most common method to protect users while surfing the Internet is leveraging a web security solution. I wrote a post about this HERE. Cisco has two web security flavors, which are a dedicated proxy and application firewall add-on. The dedicated proxy, known as the Web Security Appliance (WSA) came from the acquisition of IronPort. Cisco replaced its content filter module for their ASA firewalls based on McAfee technology with an application aware addition known as CX Context-Aware. There are many overlapping features between the two approaches however there is a clear distinction when to choose one over the other.
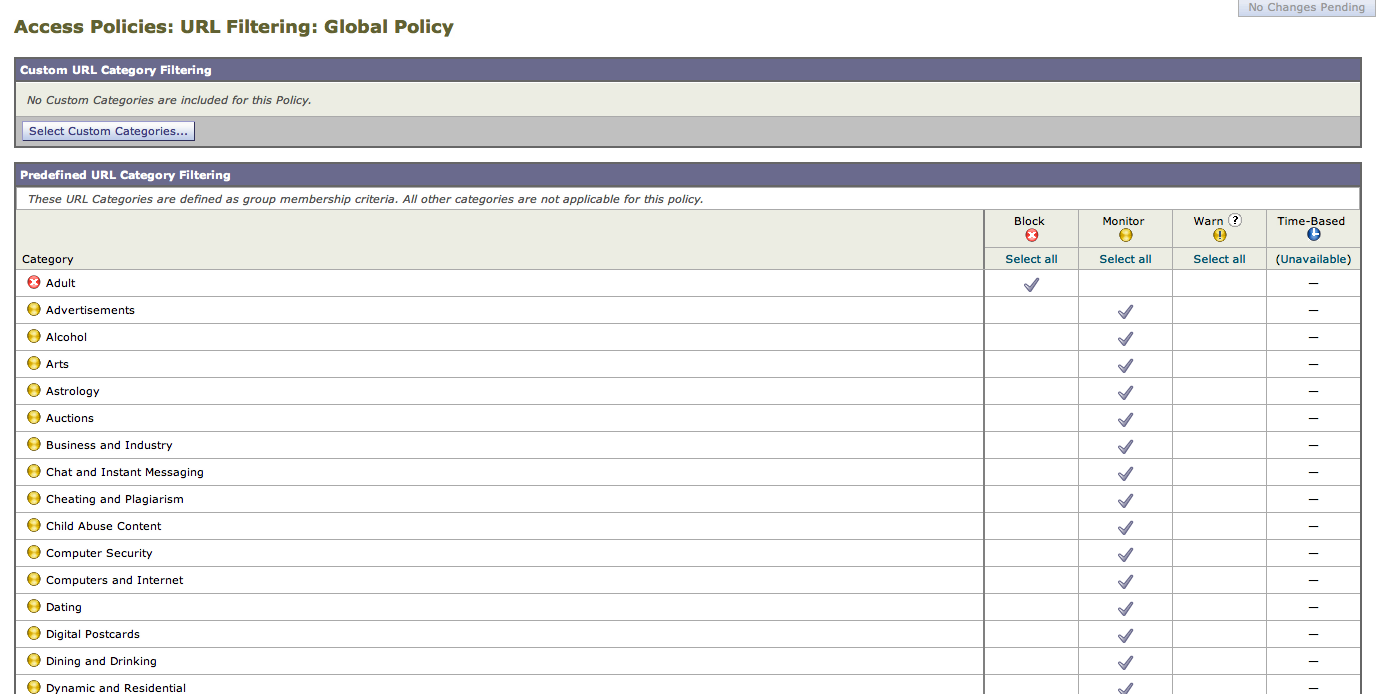
Both CX and WSA provide features expected from a web security solution. Both CX and WSA offer the ability to monitor and control what type of websites are available for users based on categories (examples Adult, Hate, Gambling, etc.). Both CX and WSA include reputation controls meaning ability to blacklist known malicious websites (more on reputation HERE). Both CX and WSA can limit or deny traffic types based on user groups such as denying Skype, throttle download speeds and target specific applications (example permitting Facebook while denying Farmsville for employees 9am-5pm). Both solutions can scale beyond the internal network using VPNs to route traffic from remote users.
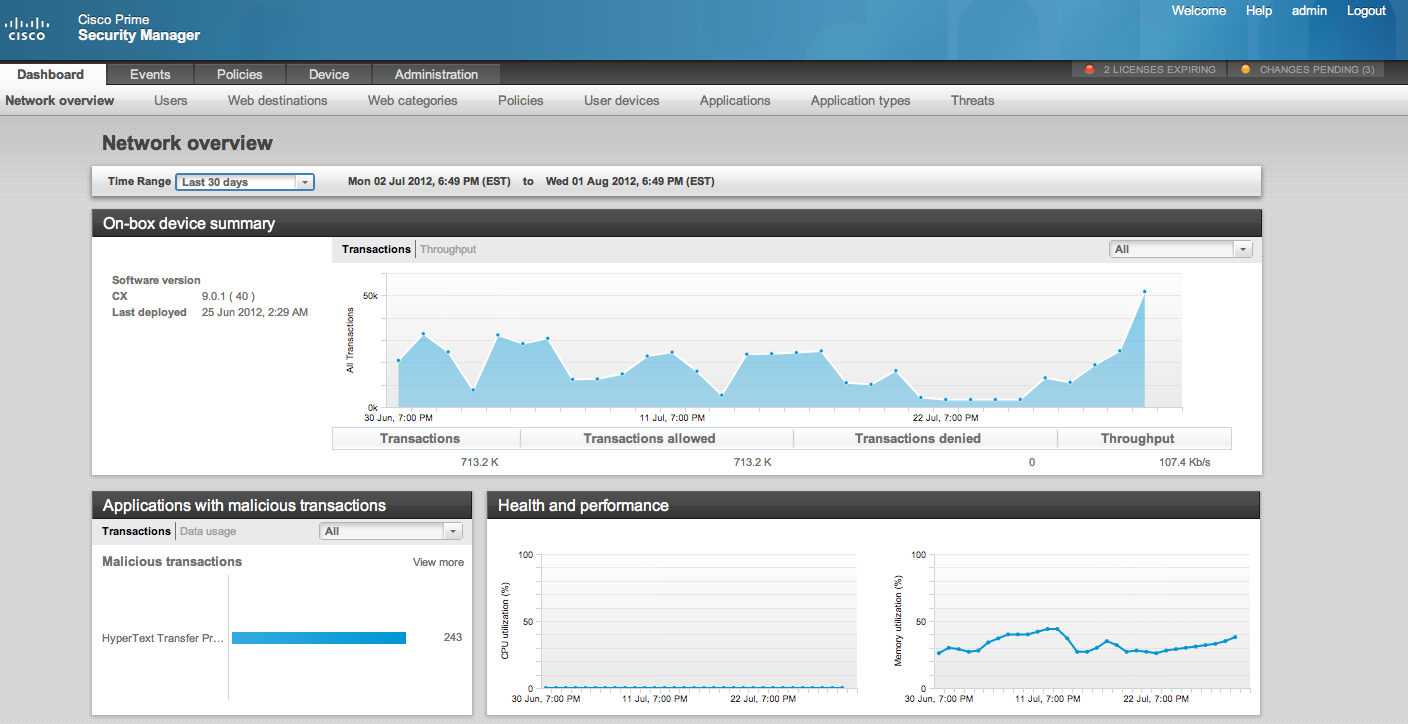
CX DASHBOARD (click to see larger)
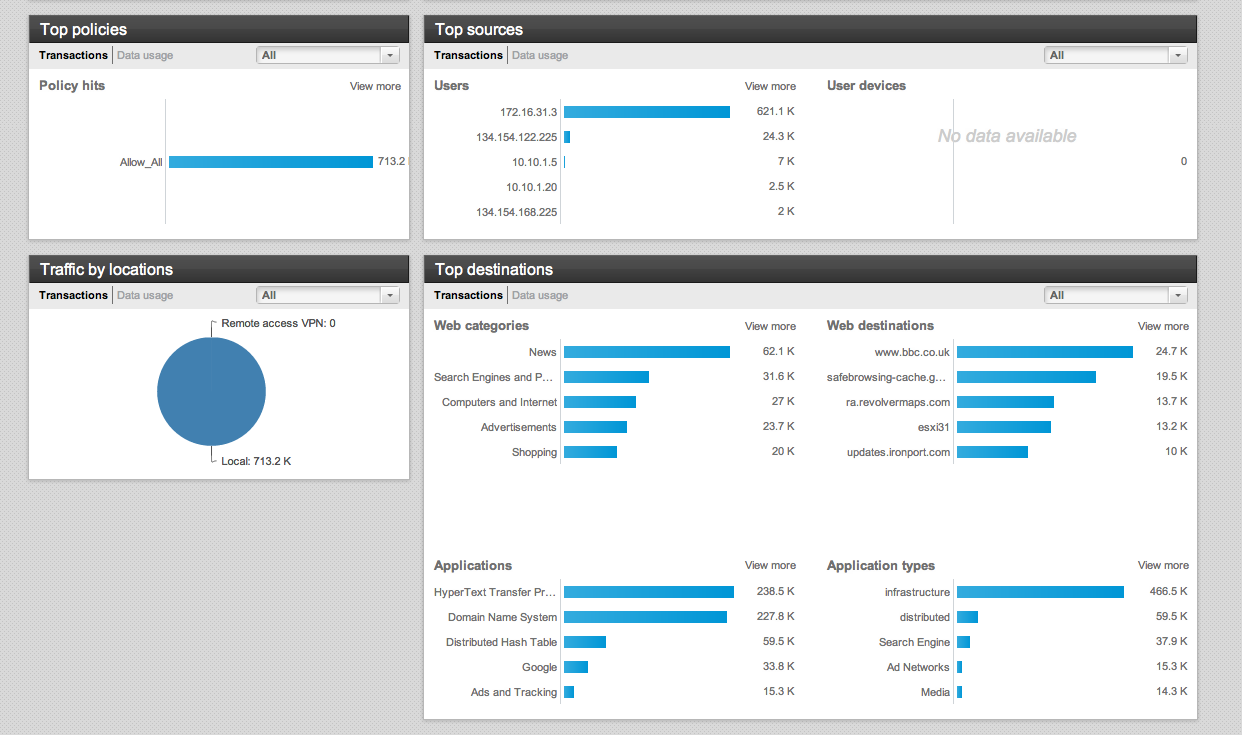
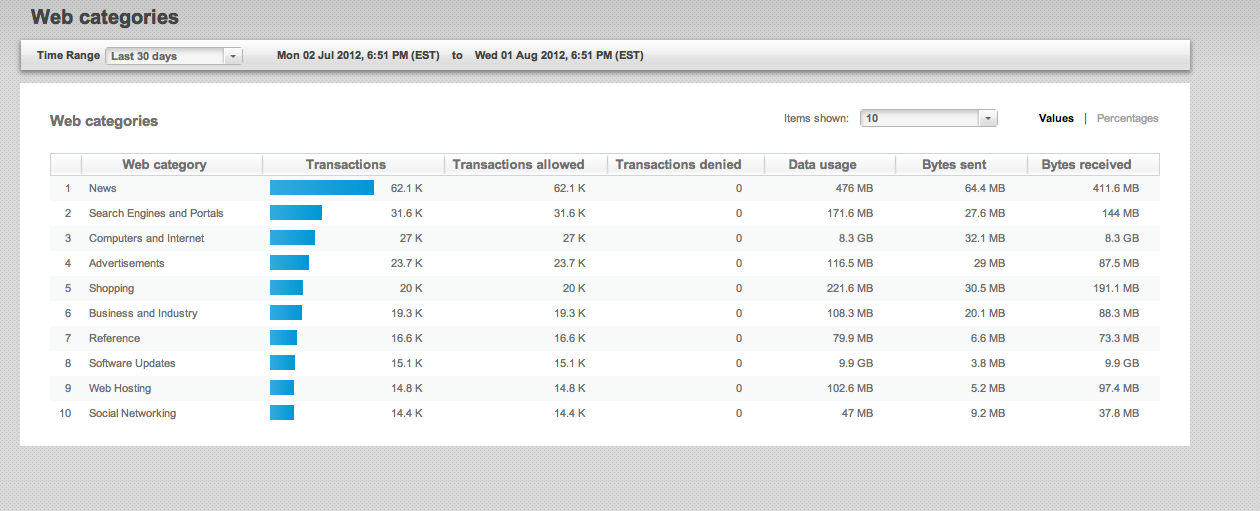
CX Web Categories
IronPort WSA Categories
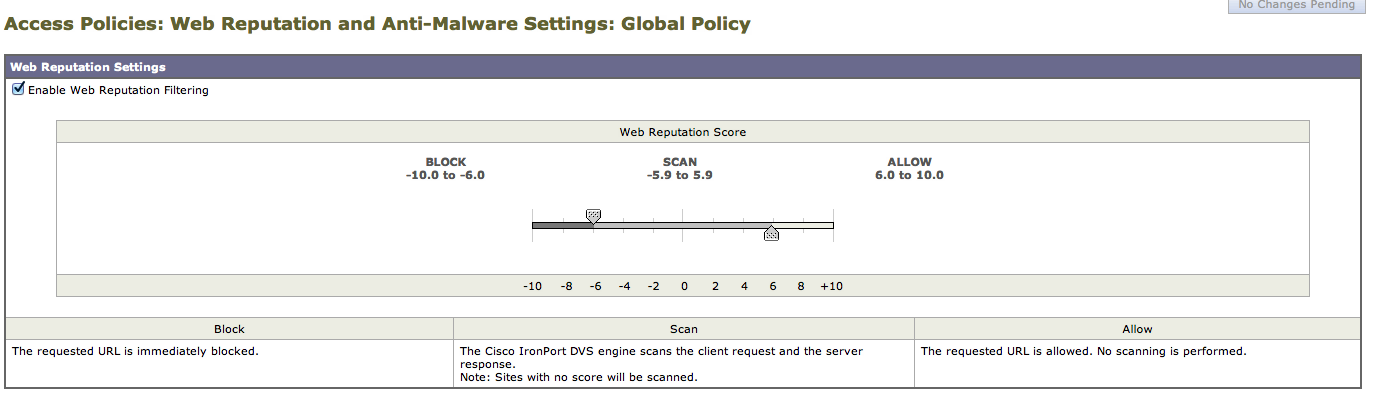
WSA Reputation Score Settings
Features offered by IronPort not included with CX are focused on what happens after traffic passes reputation and content policies. WSA offers anti-malware scanning licenses for McAfee, Sophos and Webroot for any traffic tagged as “grey” meaning traffic that passes the reputation blacklist but not considered completely trusted or “white-listed”. These signature-based verdict engines are licensed separately and can be stacked to provide a wide range of scanning capability. WSA also offers a dedicated layer 4 Botnet scanner targeting phone home communication from infected machines. These additional features provide more layers of defense beyond common application firewall technologies including Cisco CX.
Some other differences are based on the design and implantation of WSA and CX. The WSA is a dedicated proxy, which can be deployed using host inline proxy settings or directing network traffic to the WSA using WCCP. The CX uses policy maps routing traffic seen by an ASA through the CX addition. WSA includes caching to improve network performance. WSA can direct traffic through a DLP solution adding network based DLP scanning (A possible roadmap is including DLP in the appliance as a add-on license similar to the IronPort Email Security Appliance). Cisco roadmaps show IronPort offerings will include a virtualized option in the near future. Probably the most important CX design consideration is today Cisco ASA 5500X can either leverage CX or IPS however not both simultaneously. CX is also not available on some ASA 5500X models such as 5585-40s and 5585-60s. Expanding CX to other ASA models and dual IPS CX support are roadmap items at this time.
 To summarize, its best to consider Cisco CX for essential web security meaning content filtering and reputation based protection. The CX is also a viable option if you don’t require IPS from your ASA 5500X. WSA is suited for Comprehensive web security meaning content filtering, reputation protection, malware scanning and layer 4 botnet awareness. WSA is also a dedicated proxy providing performance benefits as well as design options such as including Data Loss Prevention. If you desire your ASA to include IPS functionality, today you will need to consider a WSA to handle web security. Hopefully this post helps with distinguishing when to choose CX or IronPort WSA.
To summarize, its best to consider Cisco CX for essential web security meaning content filtering and reputation based protection. The CX is also a viable option if you don’t require IPS from your ASA 5500X. WSA is suited for Comprehensive web security meaning content filtering, reputation protection, malware scanning and layer 4 botnet awareness. WSA is also a dedicated proxy providing performance benefits as well as design options such as including Data Loss Prevention. If you desire your ASA to include IPS functionality, today you will need to consider a WSA to handle web security. Hopefully this post helps with distinguishing when to choose CX or IronPort WSA.





Excelent post!!!!
Hi!
Can you please update this post, or post a new comparison?
Cisco ASA CX already can support both services (IPS and CX)
Also, what about the adquisition of Sourcefire by Cisco?
Very good point. Sure I’ll write another post featuring ASA CX 9.2 vs the latest Ironport Web Security Appliance (WSA). We also have some new WSA features being announced at RSA in a few weeks as well (hint … they are coming from SourceFire). I’ll include that when considering one over the other. Look out for this post next week. Thanks for the feedback.
Sourcefire brings a handful of stuff. First off, it brings open source security to Cisco. For example, the SourceFire security team out of Maryland is now part of security feeds in all products. Second, it brings the FirePower appliance series. Some of those features are soon to be offered in multiple products. Both Cisco ASA and FirePower are NOT being ended anytime soon. I’ll include this in the next post but the focuses are slightly different market wise.