Talos did a really good job summarizing some of the top threats seen this year. The original post can be found HERE.
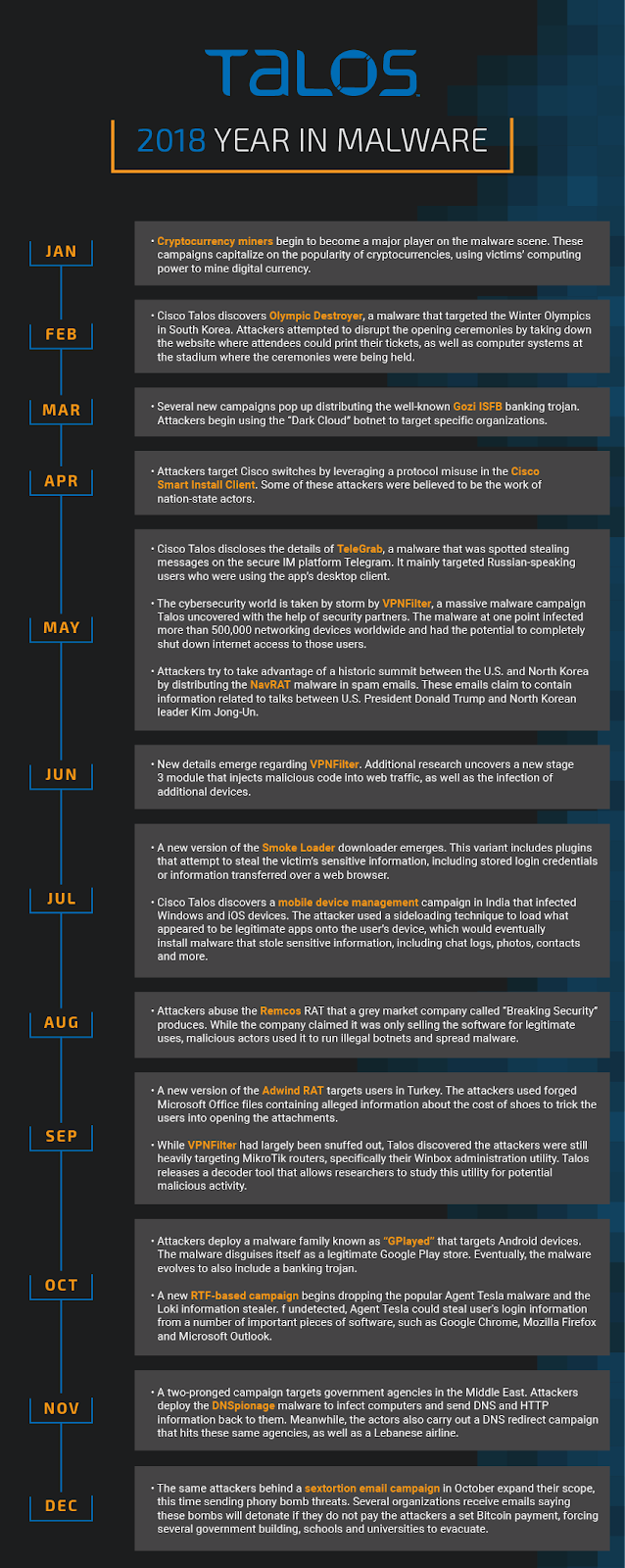
It was easy to see a wild year coming in cybersecurity. It started with a bang, with Olympic Destroyer targeting the Winter Olympics in February in an attempt to disrupt the opening ceremonies. Things only got crazier from there, with cryptocurrency miners popping up everywhere, and VPNFilter taking the world by storm over the summer. There was never a shortage of cybersecurity news this year, and Talos was there to dissect all of it. As the year wraps up, here’s a look back on the most prominent malware we discovered and the major trends we saw — some of which we expect to continue into 2019. Take a look below for our malware Year in Review, as well as a timeline of the major attacks Talos discovered this year.
Olympic Destroyer
The aforementioned Olympic Destroyer malware started the year out with a bang. This attack first emerged the night of the Opening Ceremony in South Korea, temporarily taking down the Olympics’ ticketing website and infecting systems at the stadium where the ceremonies were being held. Talos identified several malware samples that indicated a malicious actor hoped to disrupt the ceremonies, as the malware only contained destructive capabilities. In the following weeks, researchers attempted to identify who was behind the attack. However, the malware included several false flags that made attribution incredibly tricky. Olympic Destroyer would eventually return with a variant later in the year that makes it tougher to detect.
 A few months later, VPNFilter took the world by storm. Talos first disclosed the details of this attack
A few months later, VPNFilter took the world by storm. Talos first disclosed the details of this attack
Cryptocurrency miners
The value of cryptocurrencies spiked across the board in late 2017 into early 2018. Attackers who traditionally relied on payments from ransomware campaigns to make their money suddenly saw a new source of income. Over time, we saw more cryptocurrency miners emerge, replacing the usually popular ransomware. Talos first wrote about these miners — which siphon off computers’ power to secretly mine cryptocurrency — in January when we saw a series of pool-based miners emerge. Rather than attackers hoping they would get one large lump-sum payment, they could instead harvest money every day in the form of cryptocurrencies. For the user, this meant sometimes higher energy bills if their systems were working overtime, and decreased computing power for everything that didn’t involve mining. Any organizations hit with these miners were at even more considerable risk of these effects. Eventually, we discovered “Rocke,” a Chinese-speaking actor who became one of the largest users of cryptocurrency miners. Rocke spent the entire year distributing and executing cryptomining malware using a varied toolkit, including Git repositories, HttpFileServers, dropping miners via shell scripts and JavaScript backdoors. At the time, we predicted that Rocke would explore social engineering as another way of tricking users into downloading cryptocurrency miners. Throughout the year, the value of cryptocurrencies has fallen fairly substantially. This has made miners less profitable than they once were. However, we don’t expect cryptocurrency miners to go anywhere any time soon.
Mobile malware
More consumers are turning to mobile devices for their every day needs rather than desktops. And as more every-day consumers use their smartphones for shopping, email and more, attackers can take advantage of those people who may not be as aware of online threats as they should be. This has opened the door to mobile malware that relies on tricking users into enabling malicious apps to access content they shouldn’t be able to otherwise. In some cases, attackers have gained the ability to completely take over a mobile device, as in a small campaign we discovered in India in July. In a small campaign, Talos discovered 13 devices infected with mobile device management (MDM) software that could allow attackers to tack on malicious features to legitimate apps, giving them the ability to exfiltrate information such as contacts, photos, messages and location. Later on in the year, we discovered this campaign targeted more devices than we initially thought and even connected the attack to another actor who had a history of targeting Android devices. Another trick attackers liked to use this year on mobile devices in disguise. In the case of GPlayed, an attack we discovered in October, one actor was able to trick users into downloading a malicious app that disguised itself as a legitimate Google Play app store. Once installed, the malicious app can load plugins and inject scripts. Eventually, GPlayed evolved to the point that it included a banking trojan that attempted to steal users’ login credentials to financial services websites.