My buddy Aamir wrote a great post on Cryptolocker. The original can be found HERE.
Cryptolocker is malware that is categorized as ransomware. According to Wikipedia, “Ransomware comprises a class of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator of the malware in order for the restriction to be removed” (Wikpedia).
Cryptolocker is dangerous because if you are infected with the malware, you are in danger of losing all your files that are local to your machine, including attached storage (USB drives) and connected network drives. The network drives or any other mass storage media that shows up as a drive letter could be corrupted by the malware.
Cryptolocker is generally being spread by Phishing attacks. The malware will encrypt the victim’s file so they are inaccessible. The files are encrypted using asymmetric Public Key encryption. . The infection was originally spread sent to company email addresses that pretend to be customer support related issues from Fedex, UPS, DHS, etc. These emails would contain an attachment that when opened would infect the computer.
Cryptolocker can also be embedded in some types of video files (including online video), PDFs, and other types of applications.
Cryptolocker is not a self-replicating worm; some help needs spread it. This usually means a user clicking on a link, forwarding an email or other type of file that in infected. Mac users, you are lucky. Cryptolocker can infect almost all versions Windows, but as of right now it is limited to Windows.
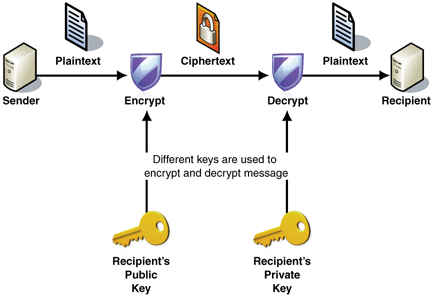
The picture from Microsoft depicts Public Key Encryption (PKI). PKI requires two separate keys, one of which is secret (or private) and one of which is public. Although different, the two parts of this key pair are mathematically linked. The public key is used to encrypt plaintext or to verify a digital signature; whereas the private key is used to decrypt ciphertext or to create a digital signature. The term “asymmetric” stems from the use of different keys to perform these opposite functions, each the inverse of the other – as contrasted with conventional (“symmetric”) cryptography, which relies on the same key to perform both.
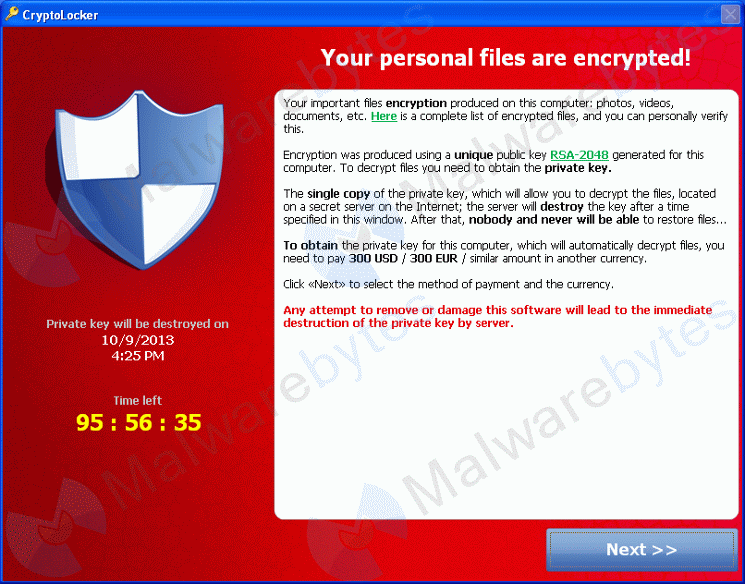
When Cryptolocker encrypts your files. It is impossible for you to read your files unless you have the private key. To decrypt your files you must pay the ransom. The ransom will buy you your private key that is needed to decrypt your files. It is paid in Bitcoin currency and ranges from $300 – $900 to get your files decrypted.
Your private key used to decrypt and access your files can only be obtained for a limited time (usually 72 hours). After that your data may be unrecoverable.
You can protect yourself against Cryptolocker, by maintaining backups of your files and systems. You can use these backups to restore your data. It is important that you do not backup and restore your files while connected to the Internet. Additionally if you use NAS systems, consider not mapping drive letters unless you need them.
Sandboxing your environment and web browser also is a good way of mitigating the attack. Sandboxi is an excellent tool to protect againt Cryptolocker and other malware, spyware, and unwanted software.Sandboxi is a $21.00 tool that runs your web browser in a sanbox protecting your system files. When you done working in Sandboxi, your Internet sandbox is emptied and the files are flushed.
For enterprises, using OpenDNS’s Umbrella product are currently protected against Cryptolocker. Businesses trust OpenDNS to protect them against the latest online threats, but sometimes infections sneak in as binary email attachments or on thumb drives. To address these botnet threats, OpenDNS blocks the malware’s ability to communicate with the command and control server and prevents it from getting encryption keys, updates, or attack instructions. This cripples the malware and prevents it from causing harm while giving IT valuable time to address the issue. See more at:http://blog.opendns.com/2013/11/06/umbrella-msps-protects-networks-cryptolocker/#sthash.t0dgrphH.dpuf
If you decide to pay the ransom (there are many who have), there is no guarantee you will be able to recover your files. It is also possible for you to get attacked by the malware again.
Kyrus Tech has developed a 3rd party decryption engine for Cryptolocker. http://www.kyrus-tech.com/cryptolocker-decryption-engine/ You will still need to pay the ransom to get your private key. However, now if the decryption does not work or is complete, you can use the technology developed by Kyrus Tech to decrypt your files.
Malware detection tools are getting better at detecting the malware, however, currently there is no way to decrypt the files without obtaining the private key and paying the ransom.
Sources:
Wikiepdia – http://en.wikipedia.org/wiki/Ransomware_%28malware%29
Malwarebytes – http://blog.malwarebytes.org/intelligence/2013/10/cryptolocker-ransomware-what-you-need-to-know/





It is truly an honor to read articles by Aamir Lakhani. He is one the web’s leading security professionals. Thank you. The anti-spam and multiple captcha on this site is nuts.