People continue to focus on what The Shadow Brokers are up to. Riskbasedsecurity provided a great overview of who they are. The original post can be found HERE.
This week a hacker group going by the name The Shadow Brokers has surfaced and appears to be auctioning off computer exploits it claims are stolen from the Equation Group. The Equation Group, a group of hackers believed to be operated by the National Security Agency, was named by Kaspersky after their analysis of “APT” activity leading up to 2015. According to Wikipedia:
“The Equation Group is a highly sophisticated threat actor described by its discoverers at Kaspersky Labs as one of the most sophisticated cyber attack groups in the world and “the most advanced … we have seen”, operating alongside but always from a position of superiority with the creators of Stuxnet and Flame”
The group that leaked the new exploit files goes by the name The Shadow Brokers and operates the Twitter account @theshadowbrokerss. Based on their Tweets, it appears that they have been preparing for this release since at least the start of August. It started with the creation of a Reddit account on the 1st of August and then over the next 13 days it appears they created accounts at GitHub, Twitter, and Imgur.
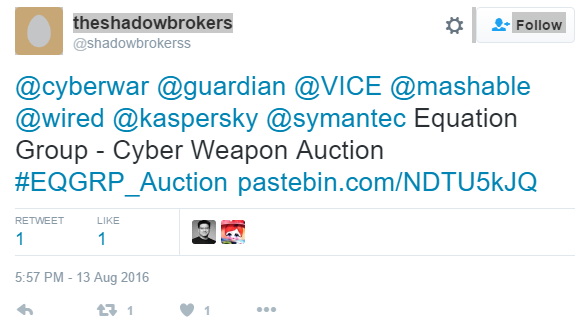 On the 13th of August they they announced the leak of this data, which stands out from other leaks because it appears to be a teaser and advertisement to promote the online auction of a larger portion of the data they got a hold of. The leak and auction announcement has been posted to various sites, including Twitter, GitHub, Tumblr, Reddit, Imgur, and Pastebin:
On the 13th of August they they announced the leak of this data, which stands out from other leaks because it appears to be a teaser and advertisement to promote the online auction of a larger portion of the data they got a hold of. The leak and auction announcement has been posted to various sites, including Twitter, GitHub, Tumblr, Reddit, Imgur, and Pastebin:
How much you pay for enemies cyber weapons? Not malware you find in networks. Both sides, RAT + LP, full state sponsor tool set? We find cyber weapons made by creators of stuxnet, duqu, flame. Kaspersky calls Equation Group. We follow Equation Group traffic. We find Equation Group source range. We hack Equation Group. We find many many Equation Group cyber weapons. You see pictures. We give you some Equation Group files free, you see. This is good proof no? You enjoy!!! You break many things. You find many intrusions. You write many words. But not all, we are auction the best files.
The data was uploaded to several sites including MEGA, which shows that it was last modified on their system on the 1st of August further suggesting they have had it for some time.
The Auction
While we have increasingly seen the data from hacked companies be put up for auction, it is rare to see this big of a teaser posted publicly. Many breaches only end up publicly disclosing a very small sample of data to show their authenticity, but the Equation Group teaser data includes a significant trove of exploits designed to compromise firewalls. This data alone has incredible value to a wide variety of companies, both offensive and defensive. The hacked data release came with a FAQ and a set of instructions for the auction:
We auction best files to highest bidder. Auction files better than stuxnet. Auction files better than free files we already give you. The party which sends most bitcoins to address: 19BY2XCgbDe6WtTVbTyzM9eR3LYr6VitWK before bidding stops is winner, we tell how to decrypt. Very important!!! When you send bitcoin you add additional output to transaction. You add OP_Return output. In Op_Return output you put your (bidder) contact info. We suggest use bitmessage or I2P-bote email address. No other information will be disclosed by us publicly. Do not believe unsigned messages. We will contact winner with decryption instructions. Winner can do with files as they please, we not release files to public.
The FAQ has several interesting points:
Q: Why I want auction files, why send bitcoin? A: If you like free files (proof), you send bitcoin. If you want know your networks hacked, you send bitcoin. If you want hack networks as like equation group, you send bitcoin. If you want reverse, write many words, make big name for self, get many customers, you send bitcoin. If want to know what we take, you send bitcoin.
Q: What is in auction files? A: Is secret. Equation Group not know what lost. We want Equation Group to bid so we keep secret. You bid against Equation Group, win and find out or bid pump price up, piss them off, everyone wins.
Q: What if bid and no win, get bitcoins back? A: Sorry lose bidding war lose bitcoin and files. Lose Lose. Bid to win! But maybe not total loss. Instead to losers we give consolation prize. If our auction raises 1,000,000 (million) btc total, then we dump more Equation Group files, same quality, unencrypted, for free, to everyone.
Q: When does auction end? A: Unknown. When we feel is time to end. Keep bidding until we announce winner.
Q: Why I trust you? A: No trust, risk. You like reward, you take risk, maybe win, maybe not, no guarantees. There could be hack, steal, jail, dead, or war tomorrow. You worry more, protect self from other bidders, trolls, and haters.
The Exploits
The compressed data is a little over 256MB and contains both the teaser data (eqgrp-free-file.tar.xz.gpg) as well as the data being auctioned (eqgrp-auction-file.tar.xz.gpg). While both are encrypted, the Shadow Brokers only provided the password for the teaser data, and only the auction winners presumably receive the password for the rest. Highlights:
- Free data file extracts to a folder named “Firewall”
- The date stamps on the encrypted files are July 25, 2016.
- The decrypted “free file” has file dated as far back as 2013.
- Directories are dated back to 2010.
- The data structure is same as shown in Imgur preview.
 While many companies and analysts rush to figure out what exploits were released, with some already publishing their initial analysis, a few of the highlights based on our cursory examination are below. The directory structure uses four letter code names for specific exploits. Some of the codes, exploit names, and relevant details:
While many companies and analysts rush to figure out what exploits were released, with some already publishing their initial analysis, a few of the highlights based on our cursory examination are below. The directory structure uses four letter code names for specific exploits. Some of the codes, exploit names, and relevant details:
EGBL: EGREGIOUSBLUNDER version 3.0.0.1 – A web-based exploit that targets Fortigate firewalls (various builds of firmware FGT_60-v300) including models 60, 60M, 80C, 200A, 300A, 400A, 500A, 620B, 800, 5000, 1000A, 3600, and 3600A. One researcher notes that Avast calls it CVE-2006-6493, which is a vulnerability in OpenLDAP.
ELBA: ELIGIBLEBACHELOR – An exploit against an unspecified vendor, affecting versions 3.2.100.010, 3.3.001.050, 3.3.002.021 and 3.3.002.030. This exploit uses the third-party library from Keld Simonsen called ISO/IEC 14652 i18n FDCC-set.
ELBO: ELIGIBLEBOMBSHELL version 1.2.0.1 – A web-based exploit reported to be against the Chinese madeTOPSEC firewall and affects versions 3.3.005.057.1 to 3.3.010.024.1. Some payloads are noted as having been added as far back as 2009 and have their own code name designations, including WOBBLYLLAMA, FLOCKFORWARD, HIDDENTEMPLE, CONTAINMENTGRID, and GOTHAMKNIGHT. Notes in the exploit include information “FOR DEVELOPERS ONLY”.
ELCA: ELIGIBLECANDIDATE version 1.1.0.1 – A line in the exploit describes itself as “What is the sound of a single thread blocking?” This web-based exploit targets the /cgi/maincgi.cgi script of Chinese made TOPSEC firewalls version 3.3.005.057.1 to 3.3.010.024.1.
ELCO: ELIGIBLECONTESTANT version 1.1.0.1 – A line in the exploit describes itself as “A packet drops in a router. Does anyone hear it?” This web-based exploit targets the /cgi/maincgi.cgi script of Chinese made TOPSEC firewalls before version 3.3. The exploit also has warnings for the user that the “User may be logged in. PLEASE REVIEW SYSTEM INFO“.
EPBA: EPICBANANA version 2.1.0.1 – This exploit targets several models of Cisco PIX Firewalls and Cisco Adaptive Security Appliance (ASA) devices. It uses the pexpect.py Python module written by Noah Spurrier and includes an extensive list of credits for helping develop the module. The affected ASA device images include 711, 712, 721, 722, 723, 724, 80432, 804, 805, 822, 823, 824, 825, 831, and 832. The affected PIX device images include 711, 712, 721, 722, 723, 724, and 804.
ESPL: ESCALATEPLOWMAN version 1.1.0.1 – A local exploit against an unknown vendor, with one very interesting line in the params.py file. One of the configurable parameters is “callback” and the example in the header of the file says “callback (“30.40.50.60:9342”) parse to: callback_ip, callback_port”. That IP address is registered to the DoD Network Information Center located in Columbus, Ohio that is part of the Defense Logistics Agency. This may be a telling piece of information, or an unfortunate sample IP address as we see it used in at least one book on administering data centers. One researcher notes that it appears to be unroutable and potentially just a placeholder.
EXBA: EXTRABACON version 1.1.0.1 – An exploit against the SNMP service of Cisco Adaptive Security Appliance (ASA) devices that affects version 8.0(2) to 8.4(4).
The exploit dump contains many other tools and scripts, along with other wonderful codenames such as BANANAGLEE (impacting Juniper devices), BARGLEE, BLATSTING, BUZZDIRECTION, SCREAMPLOW, and BANANADAIQUIRI.
Bidding and Bitcoin
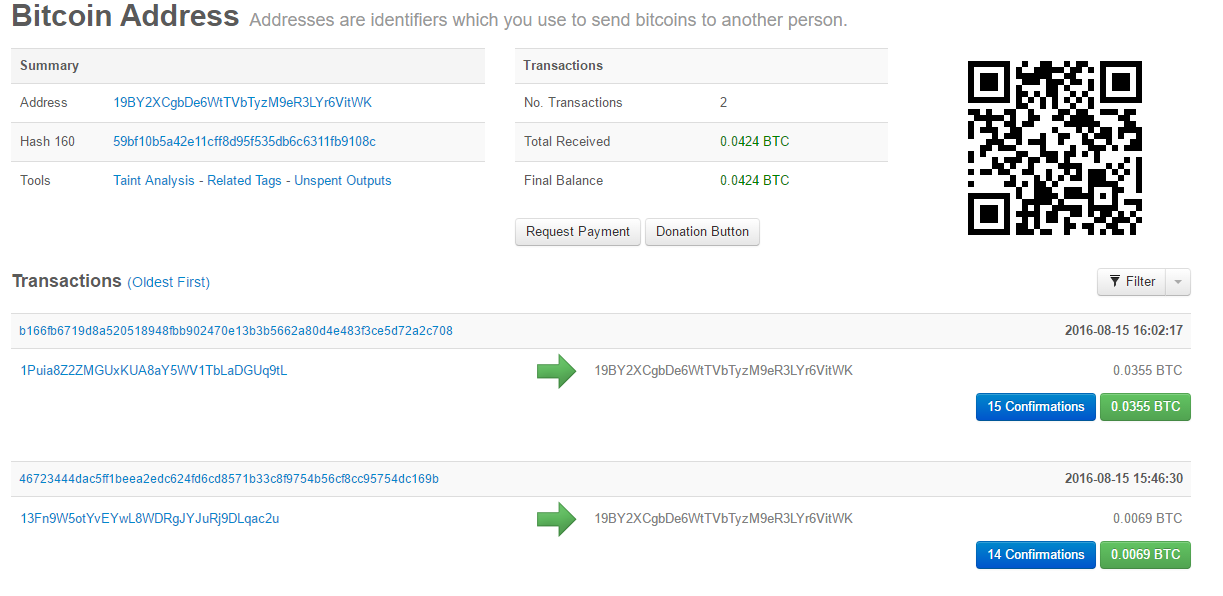
Several researchers have taken to monitoring the BTC (bitcoin) transactions associated with the auction of the leaked data, and have pointed out it can be monitored on the blockchain. At the time of publishing, the auction currently has two transactions worth a total 0.0424 BTC ($23.56US). The first transaction bid was 0.0355 BTC and the second one was 0.0069 BTC. The current high bid comes from Mike Damm, who has announced it on twitter.
As we wrap up this initial blog post, the amount of attention and analysis this leak is receiving is considerable. The ShadowBrokers GitHub page has been suspended already, but copies of the leaked data are already spread far and wide. In the coming days and weeks, we expect to see a variety of blogs further analyzing the exploits as well as the affected vendors scrambling to evaluate the information to provide patches.
While this leak seems extremely damaging to the NSA on the surface, we caution readers to remember that false flag operations are a critical part of high-level hacking activity. As one analyst notes, this leaked information likely comes from a compromised system hosting the exploits rather than the NSA getting hacked directly.