For those that follow my blog, you will find that I tend to post a few articles after DEF CON on the cool tools I end up purchasing every year from various vendors. One fun little gadget that I’m going to cover is the Wi-Fi enabled Keylogger called KeyGrbberer Wi-Fi Premium. You can learn more about this tool HERE as well.
To summarize a Keylogger, it is a tool designed to capture keystrokes. This may be for auditing purposes, recording for scripting reasons or something more malicious like spying on somebody. There are many variations of keyloggers on the market and some are useful for specific situations. For example, there are keyloggers that you can implant into most common model keyboards meaning they are connected to the actual internal chipboard and only can be detected by opening the keyboard. Another option is using keylogger software that is installed on a host system. The more common approach is placing a small device at the end of the keyboard connection so it can perform a man-in-the-middle connection between what keys are entered into the keyboard and transferred into the computer.
One other Keylogger like tool I saw for sale was a device placed between a desktop monitor and computer to log all video, compress the files and email them out. I didn’t get a live demo to see it in action but it sounded very cool.
The Keylogger Grabber Wi-Fi Premium is a USB option designed to connect to USB keyboard. There is a lower grade model that has less space and doesn’t include Wi-Fi with a cost of around $50 dollars. The Premium version offers 4 gigs of storage and Wi-Fi that is setup through updating a text file either edited directly or using the GUI software. The image at the top of this article is the model I picked up for $150 dollars.
The first step to use it is to configure it.
Option 1: Connect it to a keyboard and press the default keys to turn it into a USB hard drive, which are K, B and S simultaneously by default. Once it becomes a hard drive, I can create a new file called WIFI.txt with the wireless network information it should look to connect to (SSID, encryption, Password) and what email it should send reports to. Here is an example configuration.
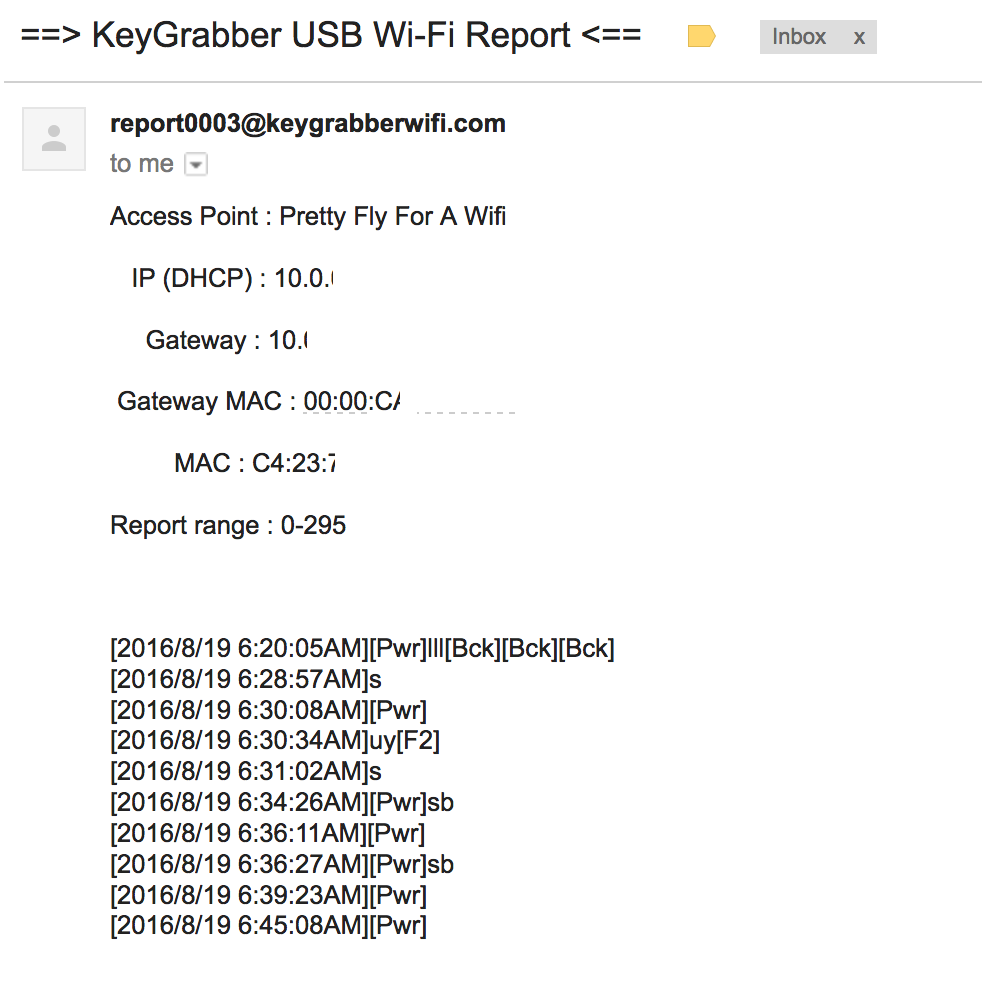
Once the USB is unplugged and plugged back in to reboot, it will take a minute or so before it auto connects to the wifi network specified in wifi.txt. I found once it successfully connects to the wifi network, it will send a report to the specified email. Here is an example of what the email looks like. I didn’t capture many key strokes in this so think about future reports showing every keystroke entered.
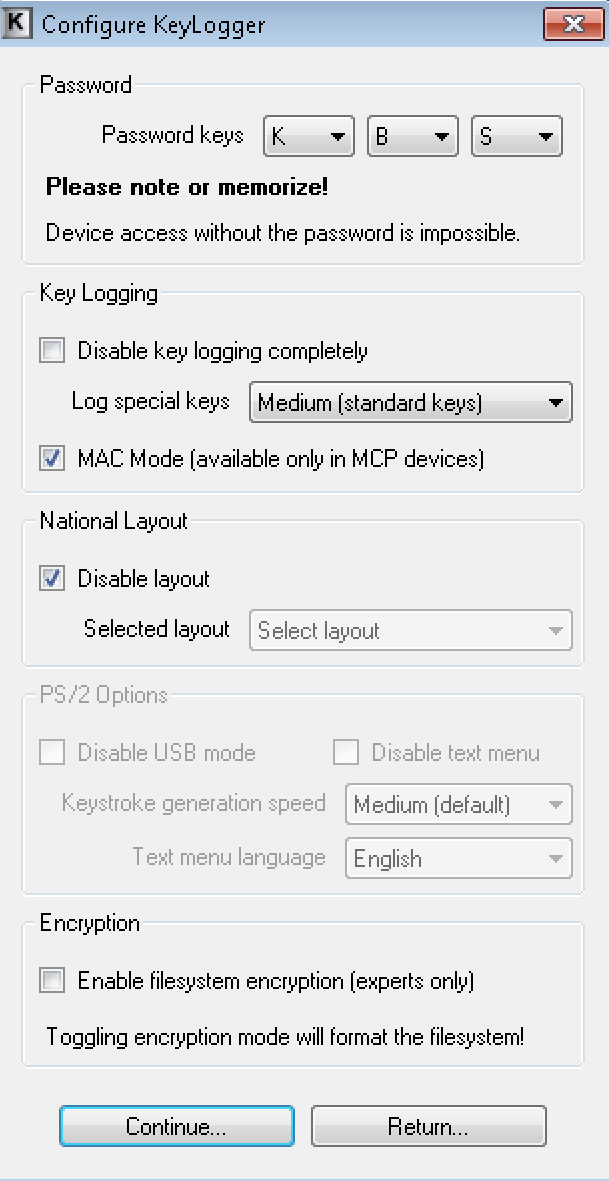
 Option 2: Do everything I just explained is to download the GUI from the Keylogger as a hard drive or find it online searching google for KL Tools.. Once installed, you can manage multiple keyloggers as long as they are on the same LAN. Here is a screenshot of all the options you can manage from this software.
Option 2: Do everything I just explained is to download the GUI from the Keylogger as a hard drive or find it online searching google for KL Tools.. Once installed, you can manage multiple keyloggers as long as they are on the same LAN. Here is a screenshot of all the options you can manage from this software.
 You can access what was logged or push out configuration as shown. Notice I can change the default password to turn the Keylogger to a USB drive, do the basic settings and next page asks about the Wifi network and where to send emails.
You can access what was logged or push out configuration as shown. Notice I can change the default password to turn the Keylogger to a USB drive, do the basic settings and next page asks about the Wifi network and where to send emails.
 I found the software has a few limitation during my initial testing. The scanning seems to be able to identify other keyloggers however sometimes it is unable to connect to the USB over Wi-Fi to pull down what was logged or sending the configuraiton. I was more successful plugging a keyboard directly into to the computer and access the keylogger directly to set it up and later connect to it over Wi-Fi. It also would be better if there was a manual method to confirm that the Wi-Fi is working verses waiting for the confirmation email. Sometimes I had to unplug and plug it back in to get it to work so that could be a concern if you are planting it in a very tight timeline (example while somebody is away from their desk to use the restroom). Worst case the Wi-Fi may not work but you still would have the 4 gigs of space to locally store what was logged.
I found the software has a few limitation during my initial testing. The scanning seems to be able to identify other keyloggers however sometimes it is unable to connect to the USB over Wi-Fi to pull down what was logged or sending the configuraiton. I was more successful plugging a keyboard directly into to the computer and access the keylogger directly to set it up and later connect to it over Wi-Fi. It also would be better if there was a manual method to confirm that the Wi-Fi is working verses waiting for the confirmation email. Sometimes I had to unplug and plug it back in to get it to work so that could be a concern if you are planting it in a very tight timeline (example while somebody is away from their desk to use the restroom). Worst case the Wi-Fi may not work but you still would have the 4 gigs of space to locally store what was logged.
Ideal Attack Goal: I set up my Keylogger to connect to a Wi-Fi SSID I broadcast from my cell phone. The goal is to plant the Keylogger at a target location and later access it from outside the building while sitting in my car. This way I can drive up at night and pull down what was logged without having to re-enter the building. I could later send new configuration to wipe it to hide my tracks. I tested it and it worked at my house (Keylogger does connect to my phone and I can access it from my laptop from another room). I can’t wait to use it in the near future.