Many industries rely on revenue generated by sales and if credit is used, Payment Card Industry (PCI) compliance is mandated. This includes all industries that process, store or transmit credit card information. Like any compliancy standard, this is the minimal level of real security and should not be considered the goal to protect sensitive data. All compliance mandates that matter must go through various review and audit processes that take time and cause the results to be dated compared to the speed of new attacks you should expect against your network. This means meeting mandates such as PCI should just be part of your overall security strategy.
Example where credit card skimmers can be placed
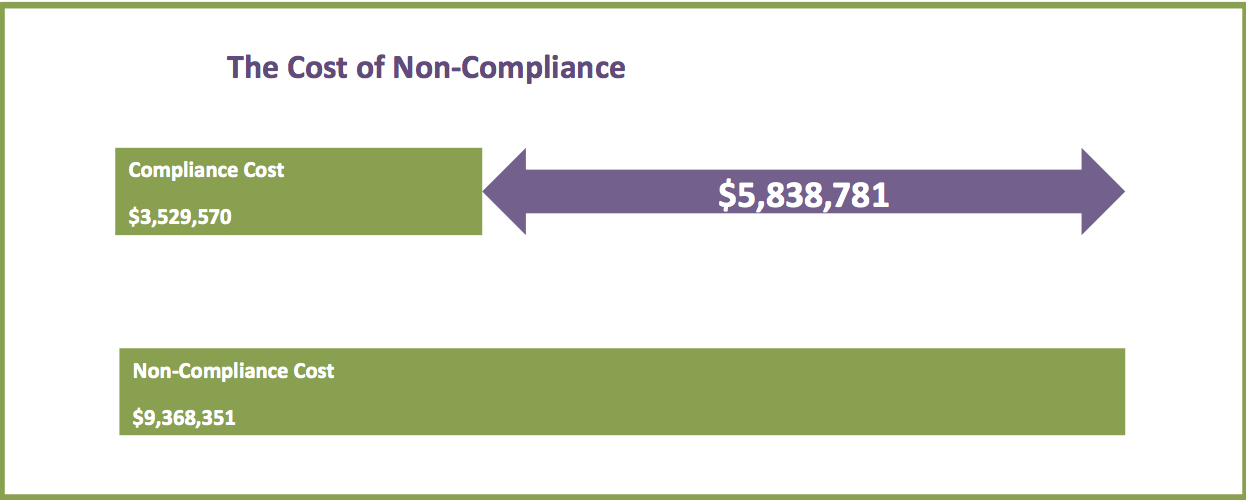
There are many forms of attacks against financial transaction systems that range from compromising the system storing credit data to memory scrapers used to capture sensitive information during the transaction process. Tools can focus on hardware such as Skimmers placed in credit card slit or identify and exploit vulnerabilities in servers holding sensitive content. Breaches are hitting the news more often than we would like to see and typically the losses to brand and cost of remediation are devastating to the business. Its crazy how many times I have received a notice “we have possibly been breached. We suggest you monitor your account and change your password.”. I’ve personally seen this for ebay, playstation and my credit card company the last 6 months. Verizon published a PCI report found HERE covering statics on PCI compliancy and reported breaches.
Comparing Meeting PCI To Losses From Breach
Best practices for PCI must extend beyond standard firewall, IPS and anti-virus solutions. These technologies focus on detecting threats however its pretty much impossible for a product to detect everything. Reason why is there isn’t a silver bullet product and if one ever exists, the attackers will eventually buy it to research how to bypass it (more on this concept HERE). This includes next generation firewalls based on the need to support HTTP traffic. White listing is also not a silver bullet since the list must be encrypted. Typically encryption found during these strategies is MD5 or SHA 256, which both have problems. MD5 is vulnerable to collisions while SHA 256 requires a lot of process overhead, which typically is too much for the average payment system.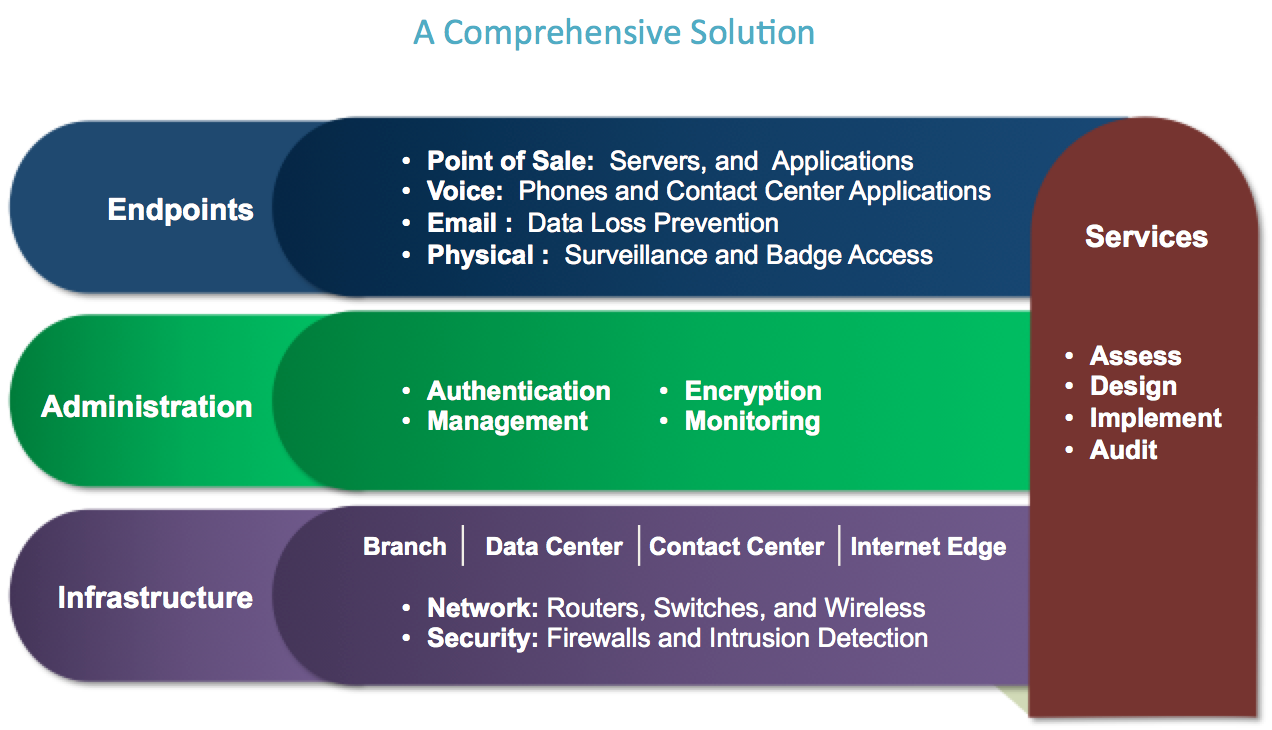
Areas to consider for PCI including services
The first recommendation for PCI best practices is using proper network segmentation and enforcing least privilege access control between segments. This means only specific users and devices should access sensitive areas of the network and system posture should continuously be monitored. Segmentation can be accomplished though a blend of firewall and access control technology with firewalls being harden beyond default settings to meet PCI Data Center Standards 1 and 2. Segmentation can be physical or logical using VLAN, ACLs or Secure Group Tags (STGs), which should compliment the authentication and authorization enforced by the access control system. Cisco published a PCI DSS document covering these concepts HERE.
As stated earlier, detection technology is important (IPS, Anti-Virus, etc) but isn’t enough so measures should be put into place to detect when these systems are bypassed before sensitive data is lost. This includes manpower used to monitor high level alerts to avoid what happened with Target (alarms detected a insider breach however nobody acted on it). Its also important to note that collecting data is not enough unless you have experts trolling the data 24/7.
One best practice is viewing trends from the entire network to detect anomalies rather than standard signature based technologies. This means alarming when a user or communication of interest is seen for the first time. For example, a sales person starts exporting data from a sensitive area outside the network, a unauthorized VPN is established, an administrator is accessing systems at odd hours and so on could all be a indication of a breach. This type of monitoring can be accomplished though NetFlow or other trending technology however intelligence must be included or the data captured is useless. Lancope and Plixor are known for offering this capability.
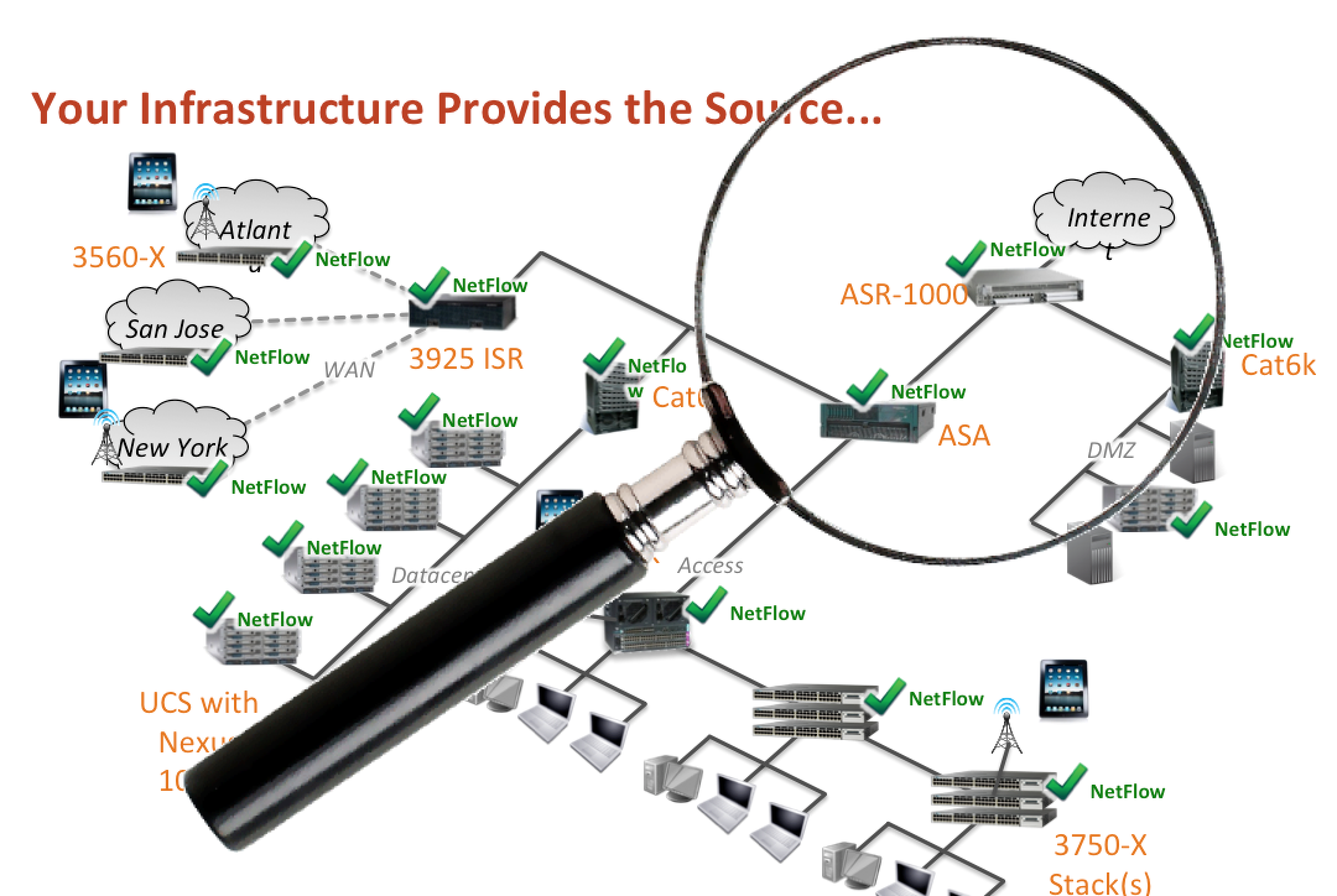 Turning the network into a IPS/IDS
Turning the network into a IPS/IDS
One major concern for this approach is if a network is already breached prior to installation, the malicious communication will be part of the baseline trend. This means a new installation of a network monitoring solution should include a network assessment or penetration test to make sure the environment isn’t already compromised. Some solutions such as Lancope offer canned attack rule sets (example alarming to network reconnaissance), monitor communication to known botnet sources and can offer “host-locking” capabilities aka stop communication against specific rules sets, which can all help with pre-installation breach problems. More on Lancope can be found HERE.
Another post compromise technology to consider is identifying and removing day zero threats. This extends beyond detection technologies such as Anti-Virus and IPS/IDS by looking for techniques used to bypass detection such as encoding, polymorphism, delay / targeted execution, etc. NSS Labs did a great report that defines and tests these types of solutions (more on this found HERE). A key feature that should also be included is retrospect visibility meaning the ability to not only detect a threat, but map out its entire presences since the initial breach. Without this, cleanup becomes a game of whack a mole meaning administrators cleaning one system while another is being compromised.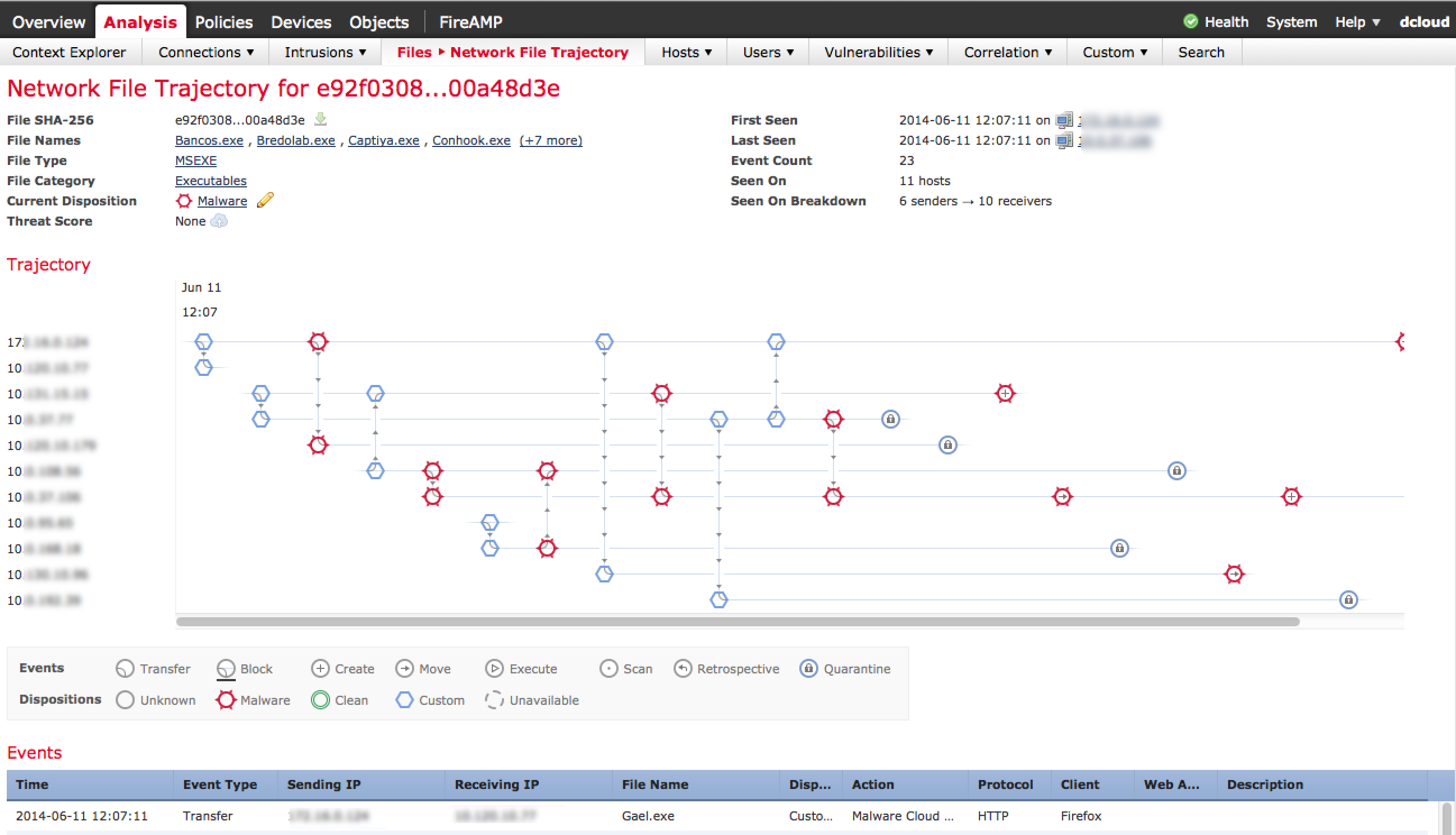
Example of retrospective mapping of malware
Lastly a complete data loss prevention solution can control how sensitive data is accessed and moved. Data loss solutions can be purchased in parts however a true end-to-end solution focuses on Network, Endpoint, Data Center and Email (more found HERE). The data must first be classified and encrypted with access control mechanisms to control who can access the data regardless of its location. For example, if somebody pulls sensitive files off the network, they won’t be able to unencrypt them without proper authorization. Typically this authorization requires an endpoint component to add things like single sign-on to open documents. The most common ways data leaves a network are through email and web, which is where data loss prevention can be implemented to control unclassified data that contains sensitive information (example a email containing SSN or credit card data).
These are just some recommendations beyond standard security defenses. Cisco published a PCI DSS 2.0 document as well as many others recommendations for security found HERE. All of Cisco’s compliance solutions can be found HERE including some simplifying PCI compliance white papers HERE and HERE. Most vendors that sell products to commercial customers should have similar PCI documentation so its recommended to verify what hardware and configurations are required to meet (and hopefully exceed) PCI compliancy requirements.