Detecting threats on endpoints like laptops and mobile devices is important but not enough to defend against the threats we see against our users. Reason why is Anti-Virus and host IPS/IDS can only scan for so many signatures and leverage so many behavior checks before they must let the traffic go through or it will impact the user experience. This is why many users get compromised by clicking the wrong email, accessing the wrong website, share the wrong USB drive and so on. Detection needs to extend beyond the doorway and look at files that have breached a host’s defense to determine if that system has been compromised as well as offer a method to remediate the entire outbreak.
NSS Labs defined this type of security as “breach detection” and graded the top players on their capabilities to stop real world threats (more on this report found HERE). Sourcefire led the pack with Advanced Malware Protection AMP for network and endpoint. Typically, customers can add this protection as a license to a Firepower solution however there is also an endpoint only version of this offering. I recently downloaded it to a few laptops and and will cover my experience using AMP.
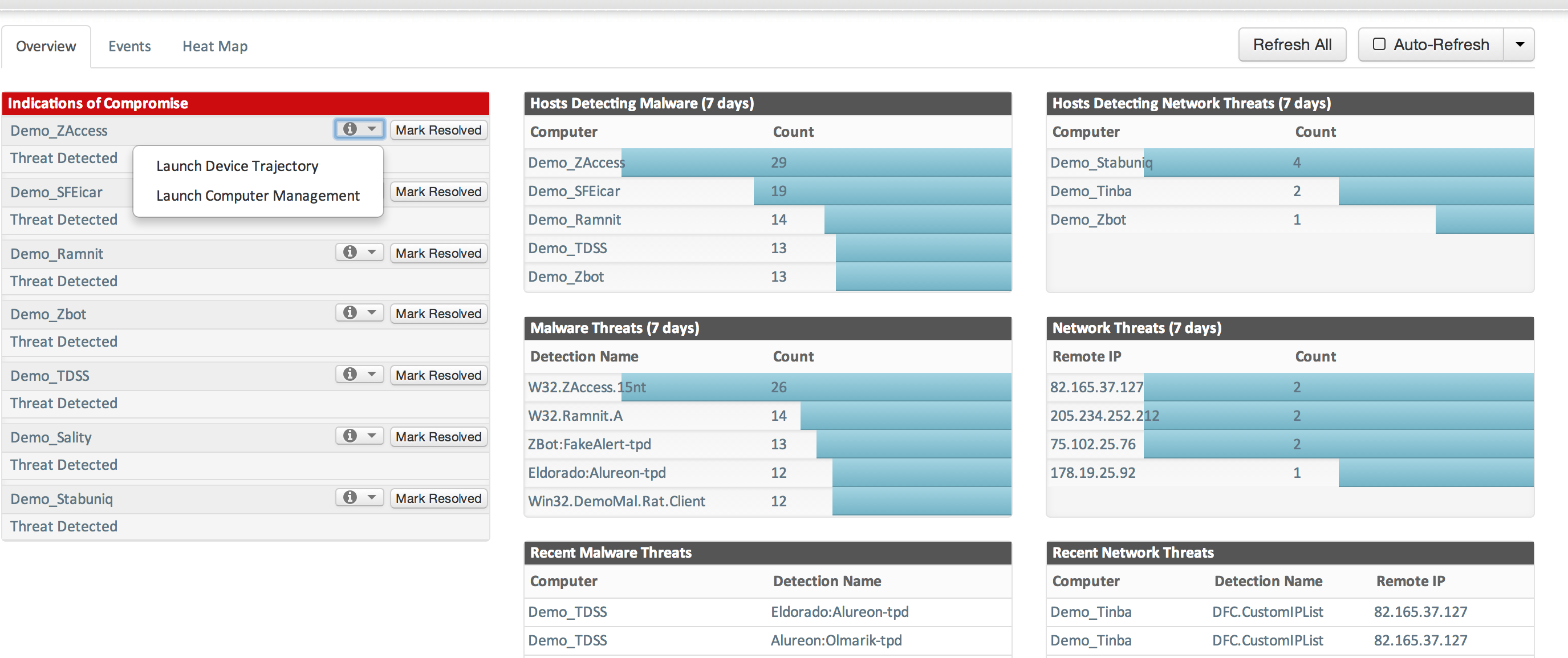
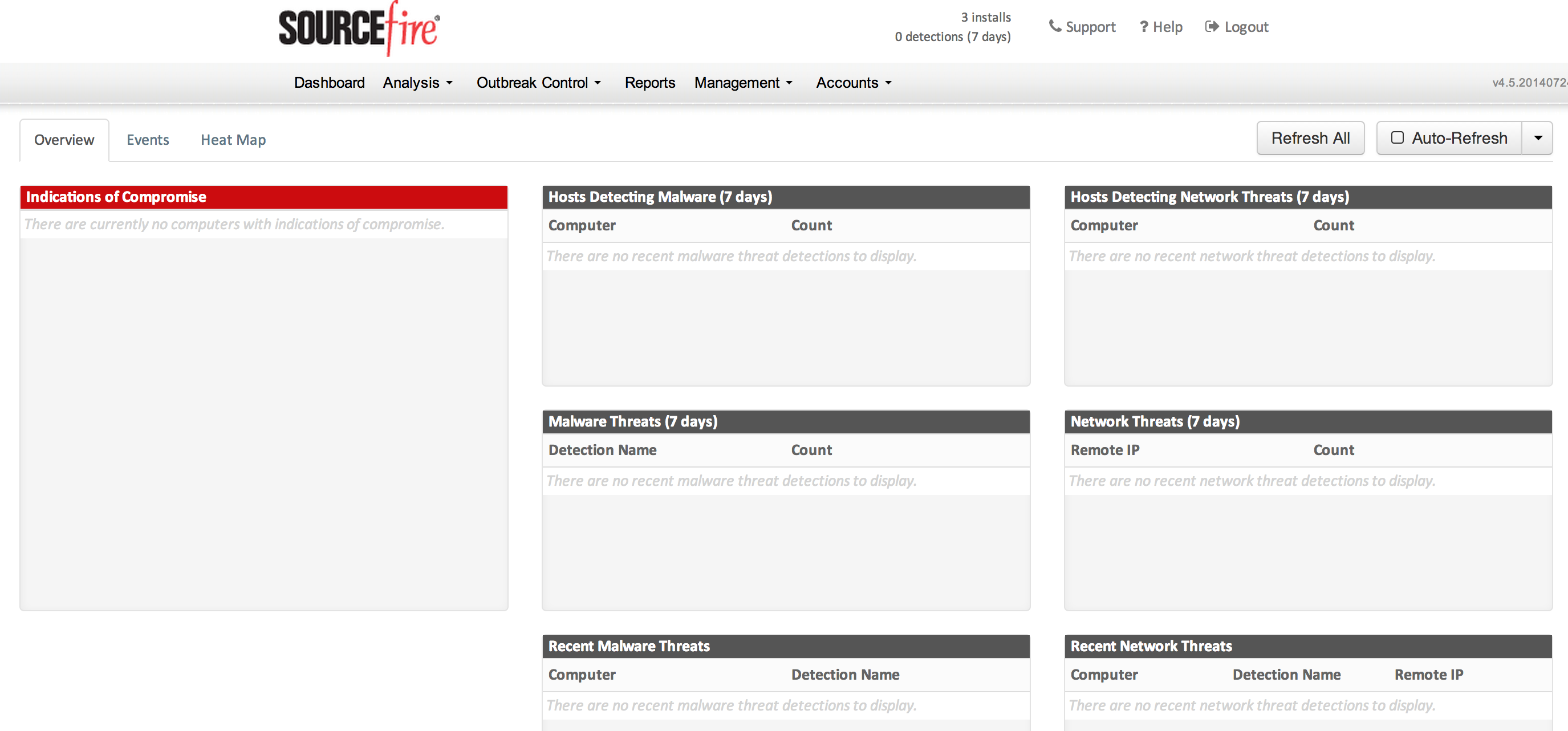
AMP For Endpoint Main Dashboard with Demo Data
The first step to install amp for endpoint is registering with the Cisco/ Sourcefire via a activation link that will be emailed to the administrator upon purchasing it. Once activated, you can log into the main dashboard via https://console.amp.sourcefire.com/dashboard#/. You can select demo data to get a feel of a compromised network as shown above or just move forward with your own data.
Once you register, you need to download some agents to endpoints. You can find the download link via Management -> Download Connector. There are different types of connector settings such as a monitor only for just looking for events, different levels of protection profiles and the most extreme triage profile used for systems expected to be infected. I went with basic “protected” setting for my 4 endpoints. After selecting the endpoint type of mode, a client will be downloaded to that system to install. Once installed, the client will launch and scan the endpoint. I put two on my MACs, one on a PC vmware image and had my mom download one for her PC.
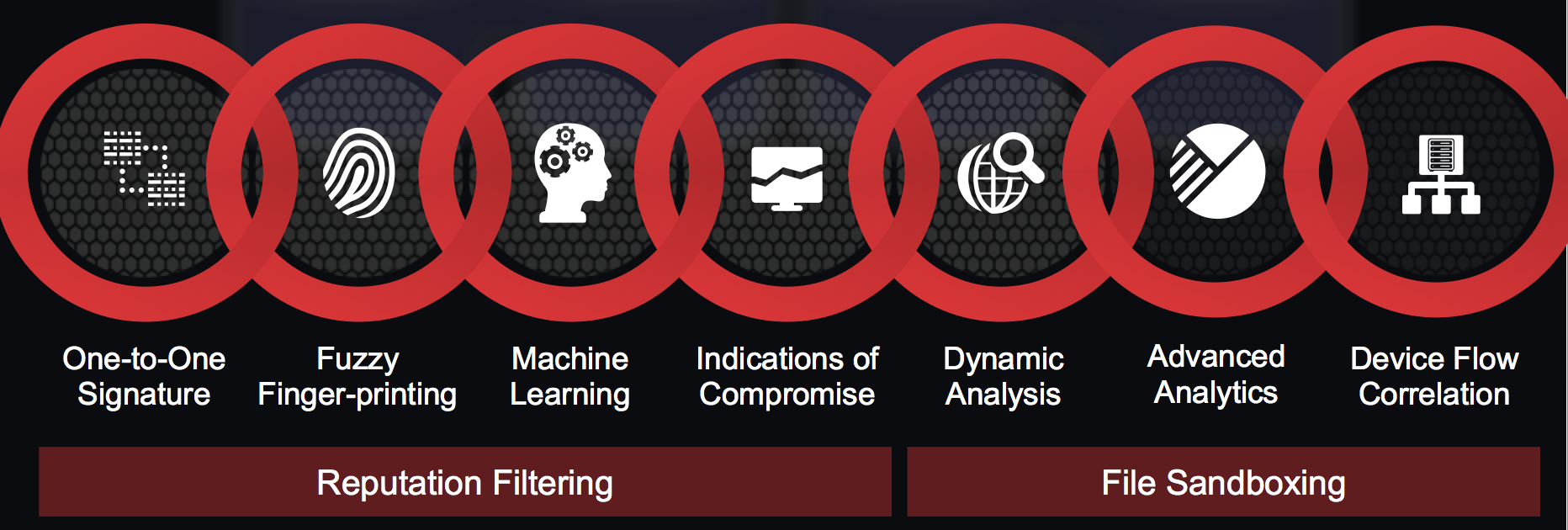
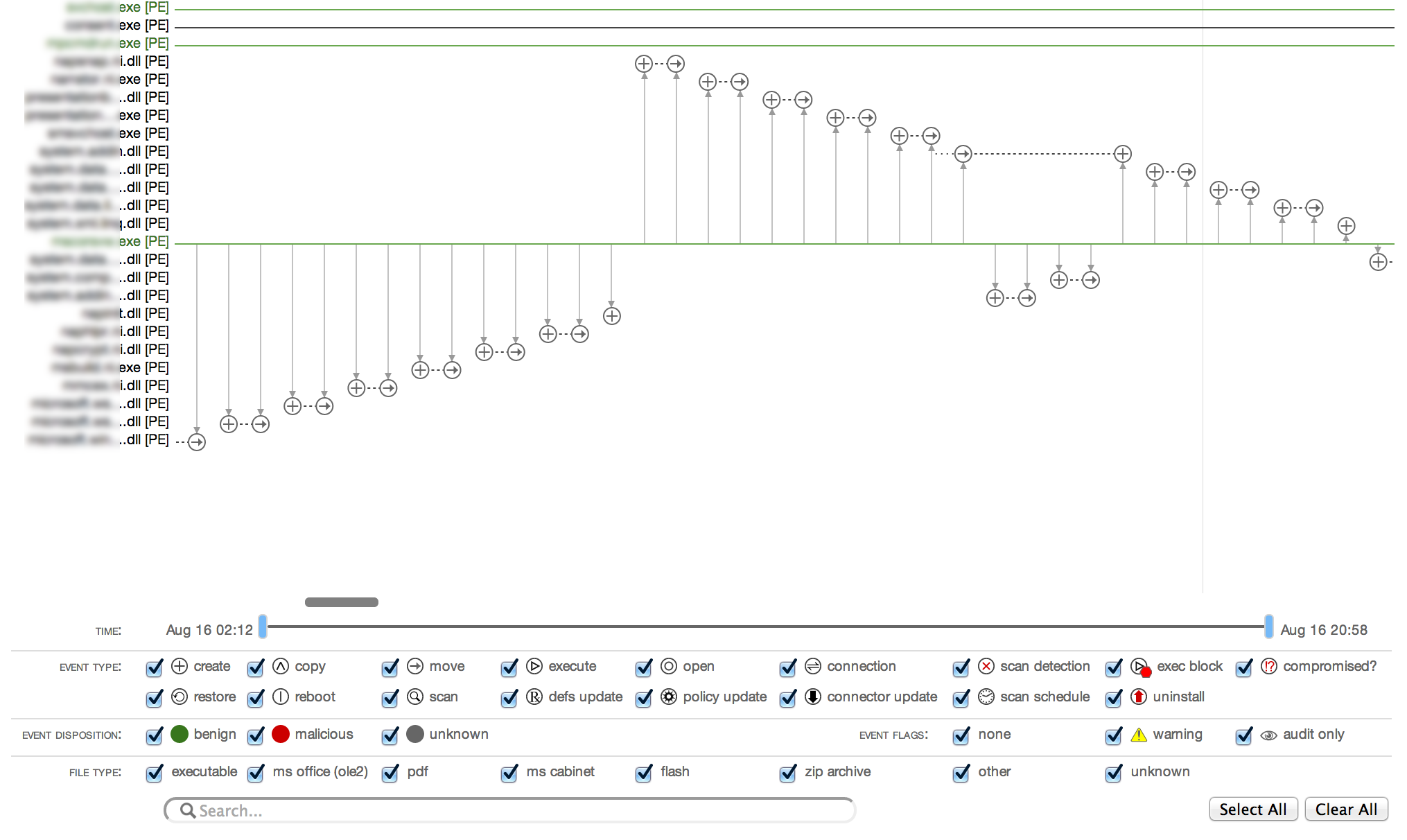
AMP works by using multiple detection capabilities combined with big data analytics and continuous analysis to determine if advanced, unknown malware is on your network (see the above diagram). Sophisticated machine learning techniques evaluate more than 400 characteristics associated with each file to analyze and block advanced malware. This combination provides detection capabilities that go beyond traditional point-in-time detection, allowing amp for Endpoints to also retrospectively detect files that become malicious after the initial point of entry aka identify the user that first brought the infection on the network as well as everybody associated.
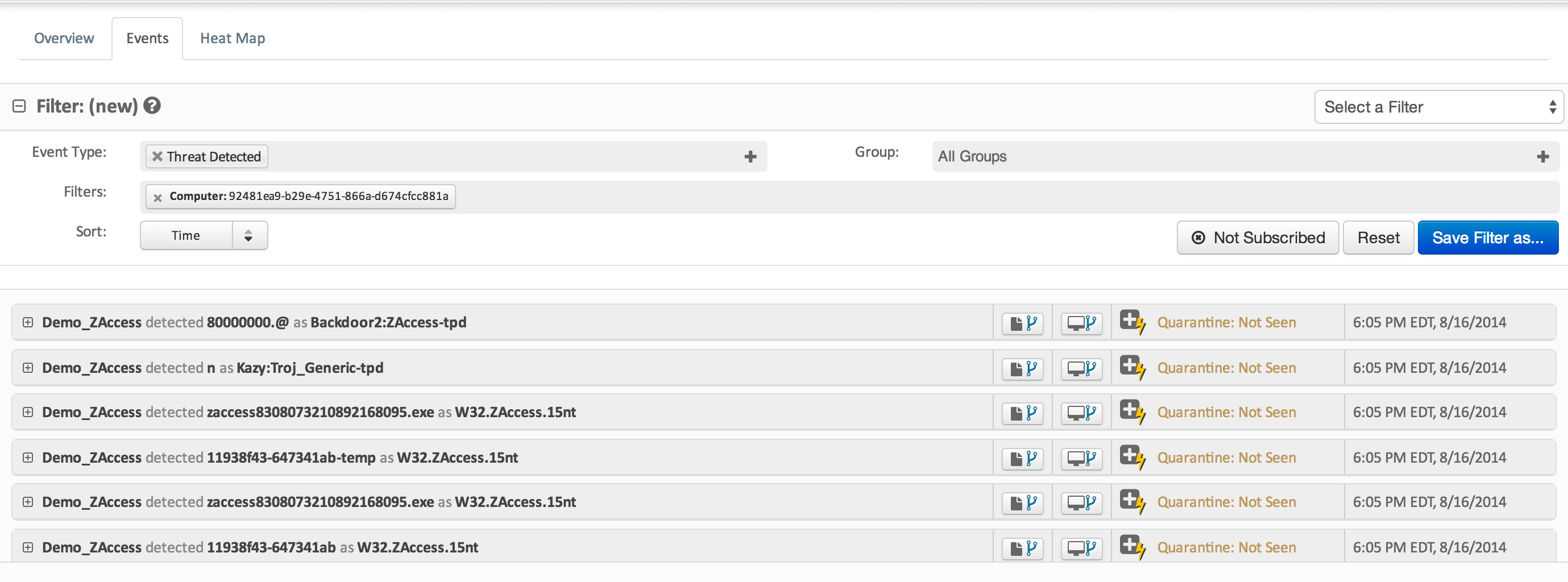
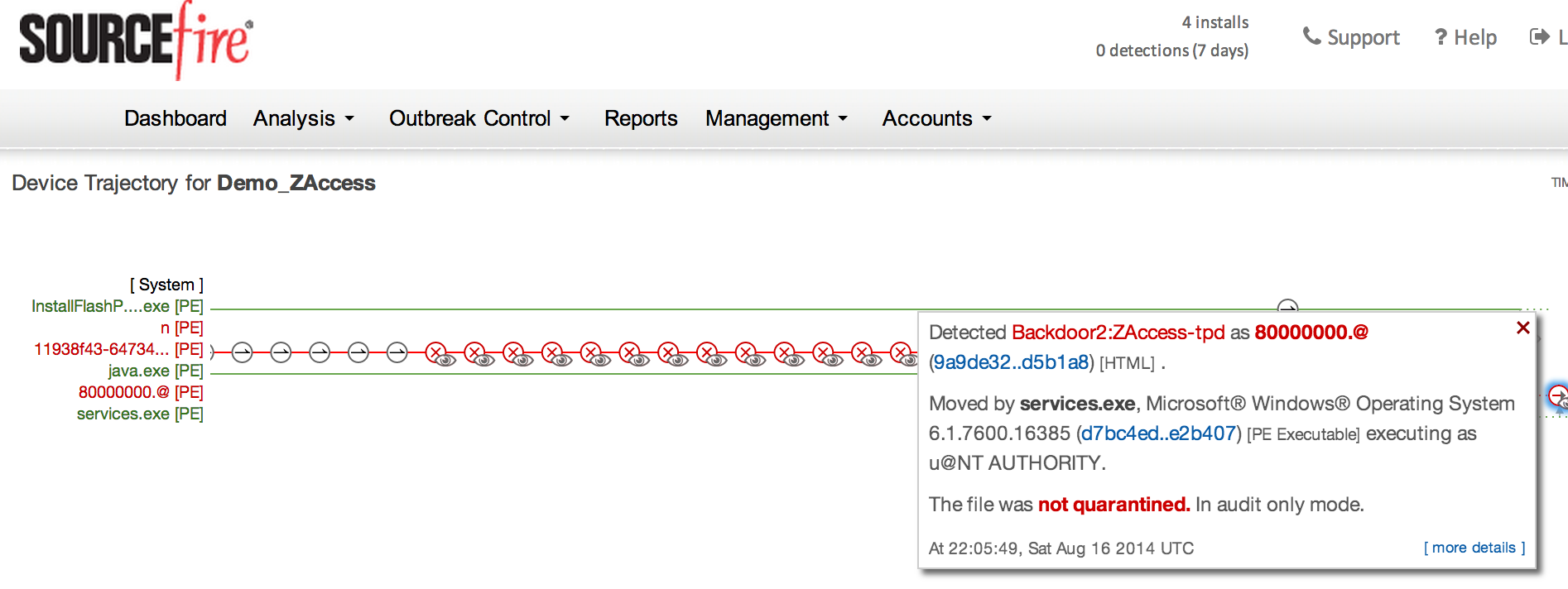
The image above shows infections from using demo data in AMP. You can click the computer image to bring up the entire history of the file including who downloaded it, where it has gone at what time and its current statues.
Demo Data in AMP showing the history of a infected file
I turned off the demo data and ran scans on my systems. Luckily I didn’t find any infections, which was a surprised since my mom’s computer was included. Below shows my clean dashboard..
I clicked one of my endpoints and found a list of all files installed including the history of those files. There is a search option and categories to help quickly narrow down desired file types to investigate.
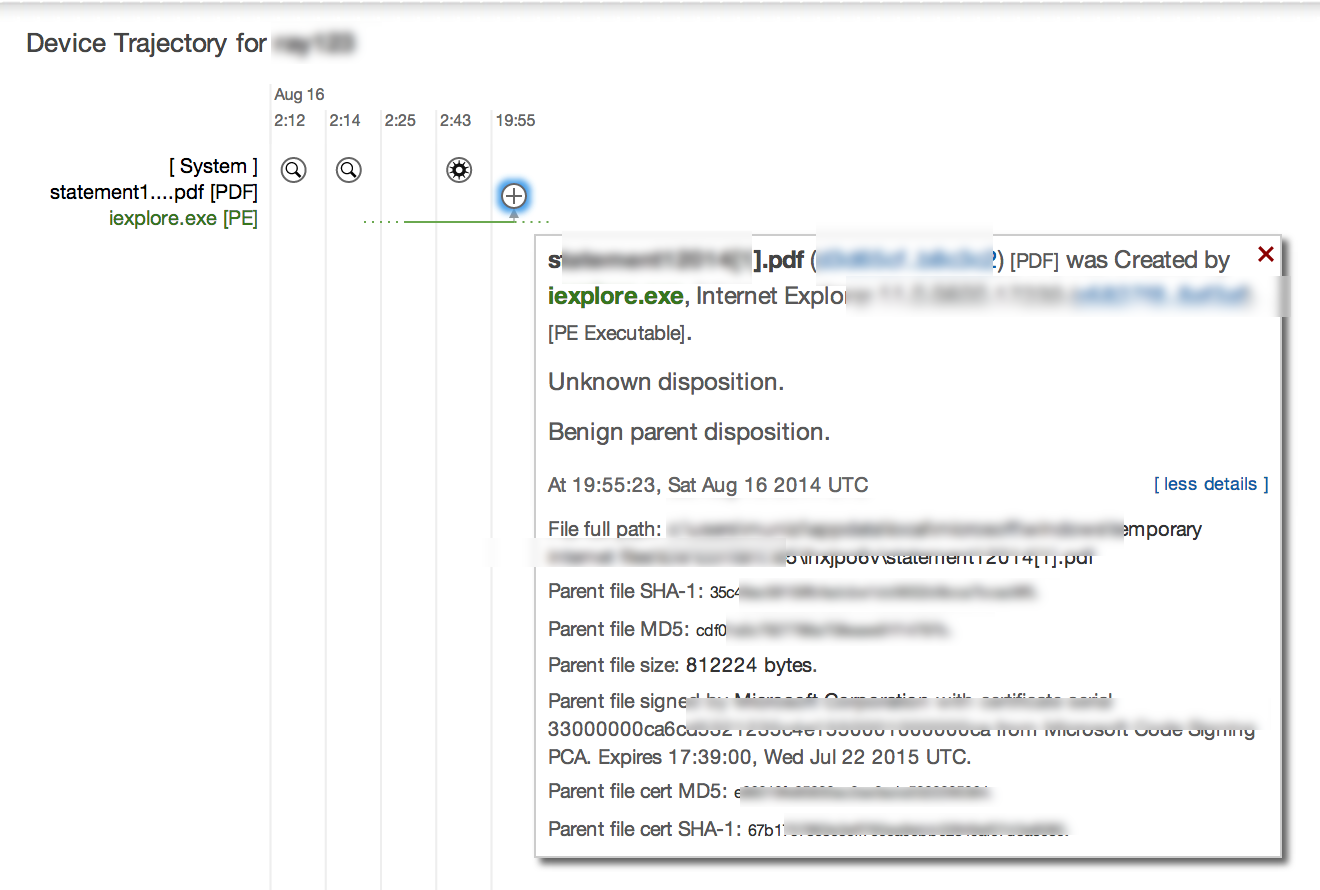
 I searched for PDF files and clicked one to see the type of details AMP would display. This example shows a safe file tagged by AMP and monitored.
I searched for PDF files and clicked one to see the type of details AMP would display. This example shows a safe file tagged by AMP and monitored.
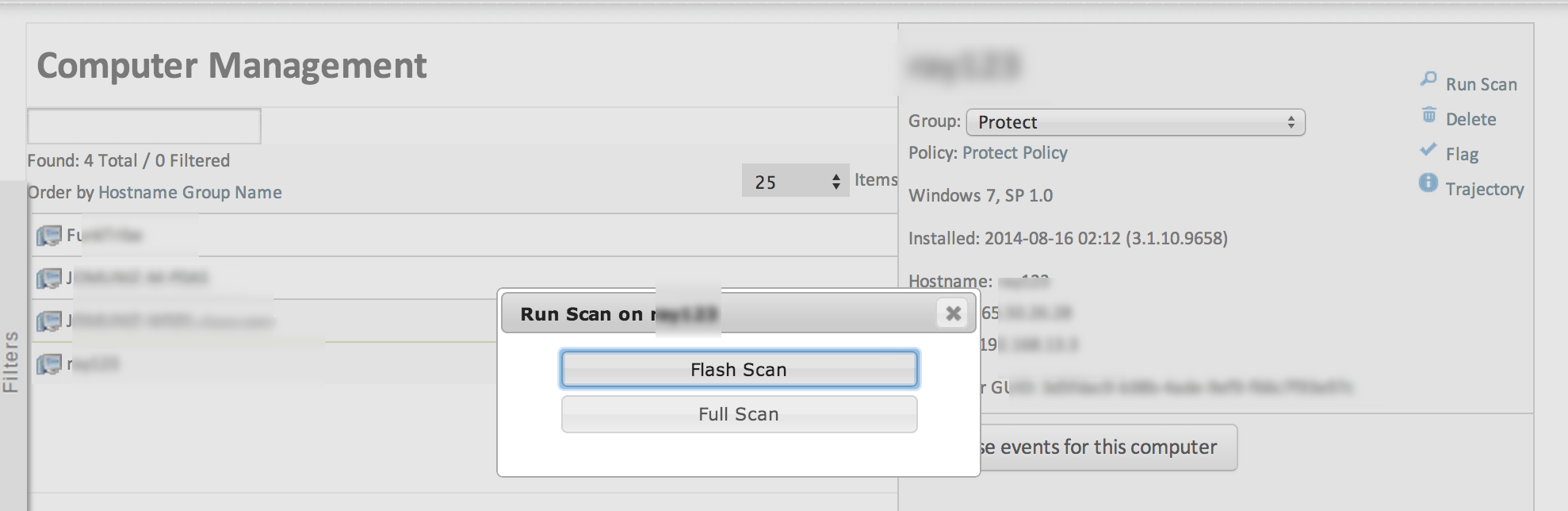
 I can select my mom’s computer and issue a scan as shown. As yon can see, I put her profile as the “protect” category.
I can select my mom’s computer and issue a scan as shown. As yon can see, I put her profile as the “protect” category.
So all in all, AMP is pretty cool and a very good complimentary to most host base security strategies. To be clear, AMP for endpoint shouldn’t replace the need for anti-virus or host based IPS as those serve as a good method to block the volumes of common attacks seen daily. AMP should be there when common detection solutions are breached and malicious software has entered your network. More on AMP for endpoint can be found at www.sourchfire.com.