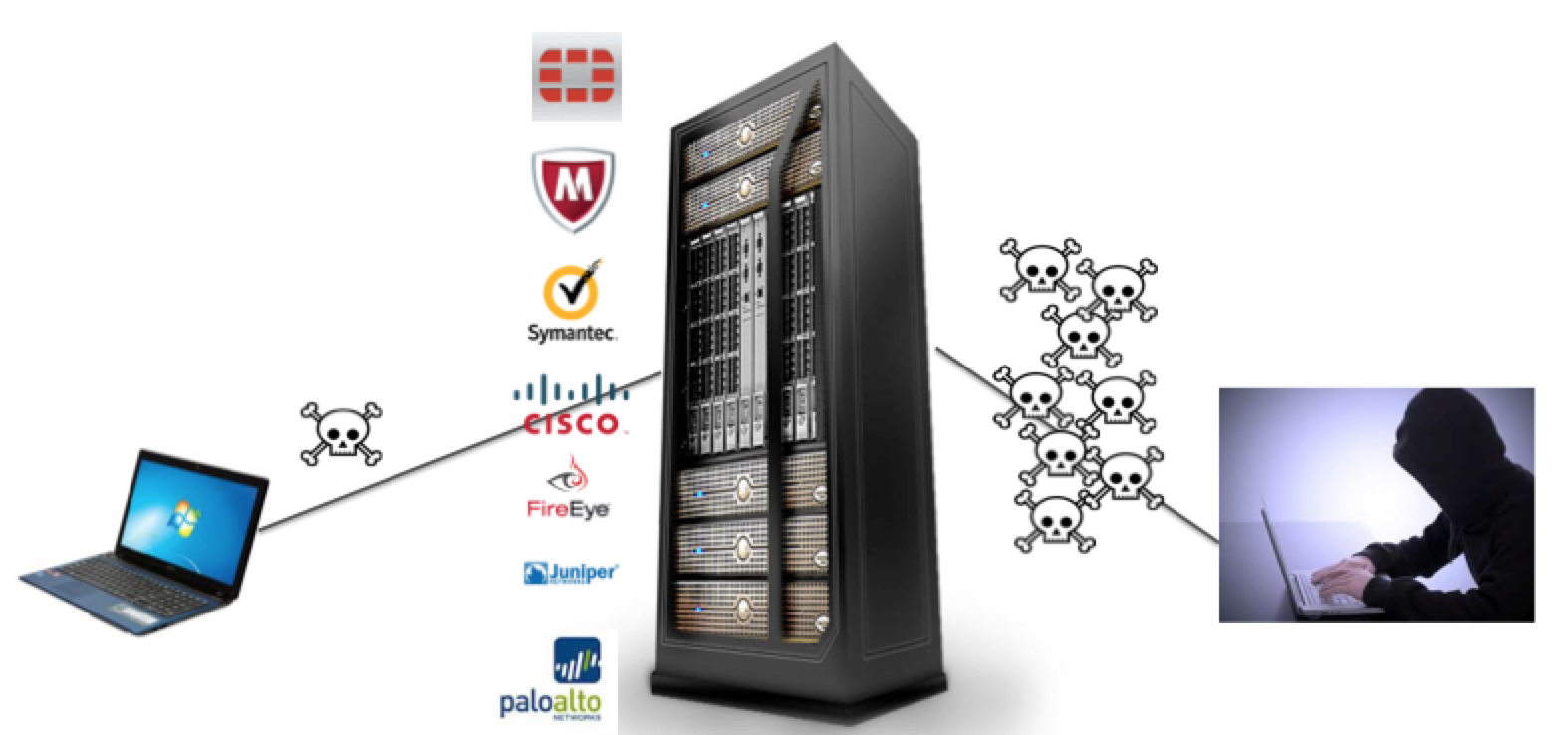
Many security professionals will make the claim “there is no silver bullet security solution”, which is completely true … but why? Why can’t large security vendors spending millions on research develop a way to ensure we are protected? We landed on the moon many years ago. Why not solve this? Well it comes down to a few concepts.
Concept 1: Anybody can buy the silver bullet product
Hackers Have Vendors In The Lab
Both good and bad engineers do research and development. Large security vendors spend millions capturing samples of live malware, creating new methods to detect attacks and other testing to stop the bad guys. So reverse this and you have the strategy for hacker research and development. If your entire business depends on breaching systems, where do you think crime organizations raking in millions spend their money? They buy the latest security technologies and develop labs to test the effectiveness of attacks. If a vendor announces a new tool to detect threats, that tool will most likely end up in an attacker’s lab.
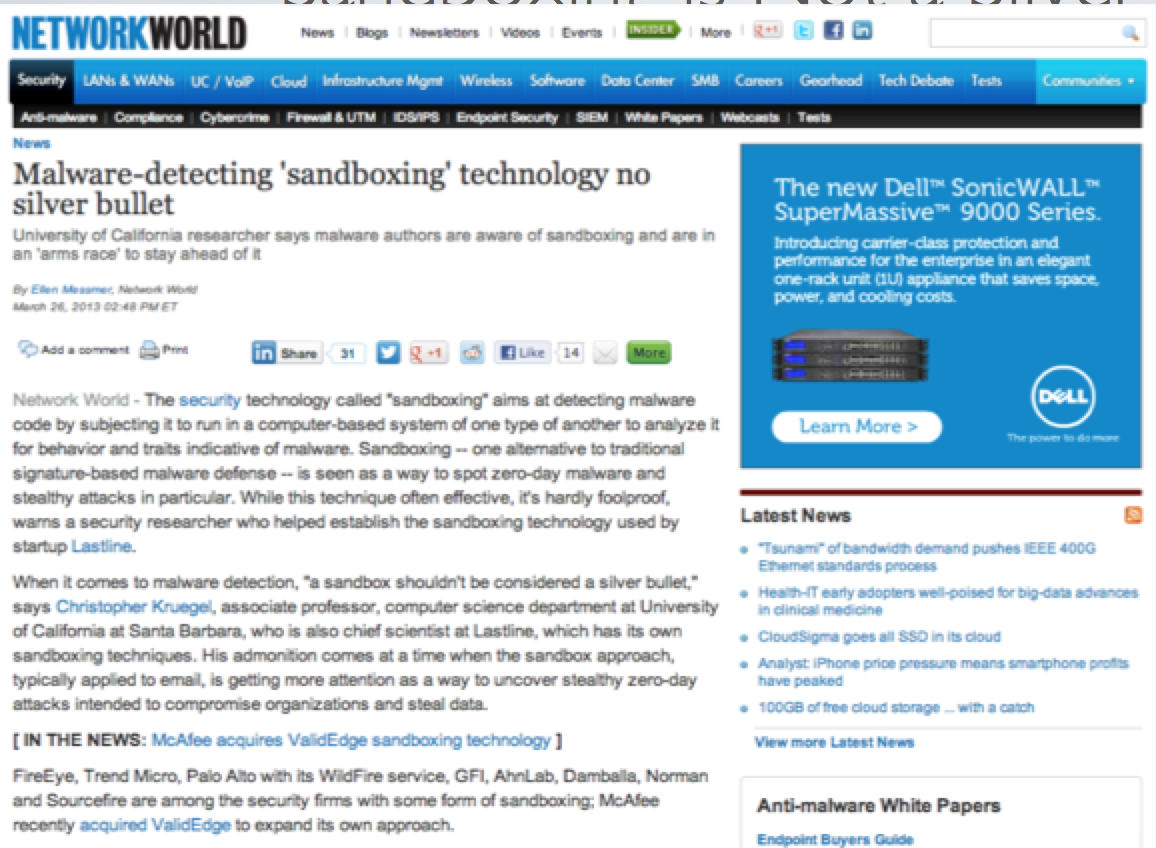
A prime example is when Sandboxing was introduced as a means to test unknown files for malicious behavior. At first, this strategy worked well as malware would reveal itself in the secured environment stopping the threat from hitting the real network. However hackers have developed methods to bypass sandbox technology as shown in the next image. Why … because they have those products in their lab.
Article About Sandbox Now Not The Silver bullet
Concept 2: Good guys have to make money
Organized crime has more advantages over vendors providing security defenses. One example of this is how security vendors have to be profitable. This means decisions are made such as what is released, who can buy it and so on with the goal of making money. Shareholders may cause products to be released prematurely and profits may shift development maps. Customers expect documentation and support typically causing delays and resources to be consumed. Criminals don’t have these problems as they are not promoting a brand like a company.
Concept 3: Good guys follow the law
Security vendors must comply with legal requirements. This typically means additional costs and delays to meet compliancy requirements. The attackers can do whatever it takes to achieve a goal.
Concept 4: The target space is growing
Everything is becoming Internet capable and many vendors are jumping on the bandwagon regarding Internet capable products. This means security administrators need to accommodate more devices as well as different types of devices (IE a person may have a laptop, tablet, phone and even IP enabled wrist watch). Developing and maintaining security policies that meet the vast number and various device types continues to be a challenge. Hackers just need one gap to compromise a network. For example, its common to find a company is breached by an unknown network aware device such as IP camera or gaming system they did not include in their security policy.
Concept 5: Not all networks are managed correctly
I’ve seen great products fail because they were not configured correctly, sized properly and so on. Also, I’ve seen very secure concepts sold to meet a specific compliancy requirement however deployed in a way that violates the intended security. For example, somebody may purchased a product that is FIPS compliant but not deploy it in FIPS mode. Another example is deploying a access control technology in a way that untrusted access can touch the internal network. There may be a great security product invented that can stop most attacks but there will also be users that don’t deploy it correctly causing a false sense of security. Vendors may try to enforce programs to limit who can deploy a technology however concept 2 states … money comes first so if somebody wants it and will pay, they will get it.
Reverse Concept: Hackers may get arrested and that has a cost
Yes there are many cons to the criminal approach such as having to spend additional dollars to stay anonymous and avoid the authorities however on average, the criminals continue to have the upper regarding developing attacks vs vendors developing defenses.
What can you do about it? Well its not about looking for a silver bullet product. The best way to protect yourself is following best practice of layering security for all aspects of your network. This means regardless if its your data center, wireless, or remote access users, you should consider how you defend that entry point both from a who is attacking to how you see the attack. You should also have a post compromise solution in place since most likely you will be breached. It’s important that when that does happen, you identify and remediate it before it causes harm to your business. Following best practices for all areas of your network is the only way to improve security, which is not achieved through a single silver bullet product. Sorry but it will never be that easy.