Microsoft, Palo Alto and others teamed up to disrupt the ZLoader botnet. There are a few interesting things to learn from this event. First, it’s great to see collaboration between technology provider research teams all aiming to make the Internet a safer place. Major take downs like this require organizations and governments to team up and share information.
Second, it is helpful to review how the Zloader botnet is leveraged by cybercriminals. Traditional botnets were primary used for coordinated denial of service attacks or distractions for other attacks. Modern botnets are leveraged in many more ways. One-way modern botnets are leveraged is for their ability to compromise hosts aka access to their victim list. Zloader was very effective at exploiting systems through exploited Adds or phishing campaigns leading to a huge victim list across all vertices.
It is important to remember that in order for a system to be turned into a botnet, it must first be exploited. The botnet effect is one of the many results that can happen when exploitation is successful. Modern botnets such as Zloader have very sophisticated options for exploiting victims along with anti-detection functions. Zloader administrators can sell access to systems they have infected with botnets to other criminals, which those criminals could leverage that access to plant their own malware. This leads to an exploited system having various malicious artifacts implanted potentially owned by multiple threat actors. The following chart comes from the Microsoft Digital Defense Report showing the average cost for a compromised system.
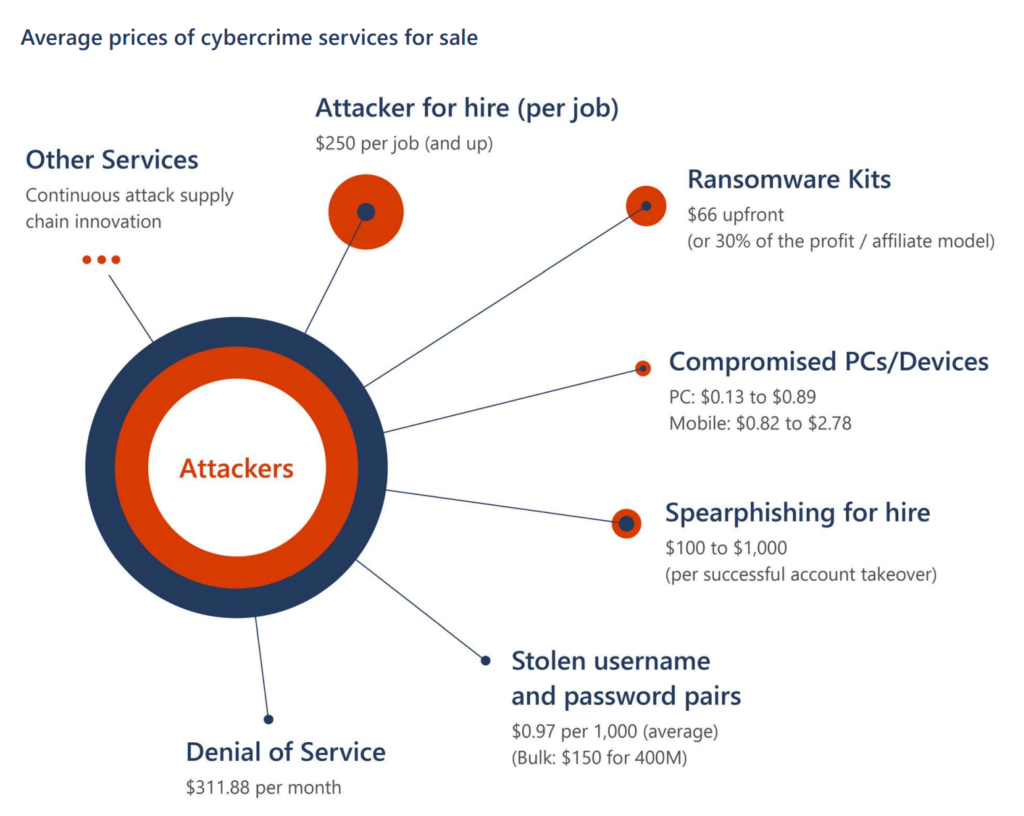
Another lesson from ZLoader botnet is how profitable it can be. Selling access to compromised systems is one profit stream, however the Zloader threat actors could use the botnet resources for a denial-of-service ransom. This works by taking down an organization for a short period to show the threat and asking for ransom to avoid further denial of service attacks to occur. I’ve spoken with Radware on webinars about this threat as its tough for many organizations to defend against volume-based DDoS. Zloader can also load ransomware for traditional extortion. Exploited systems could also be harvested for data. The list goes on, which these profits continued to fuel innovation of the Zloader capabilities. If this activity is profitable, it will continue to grow and become more sophisticated as its funded.
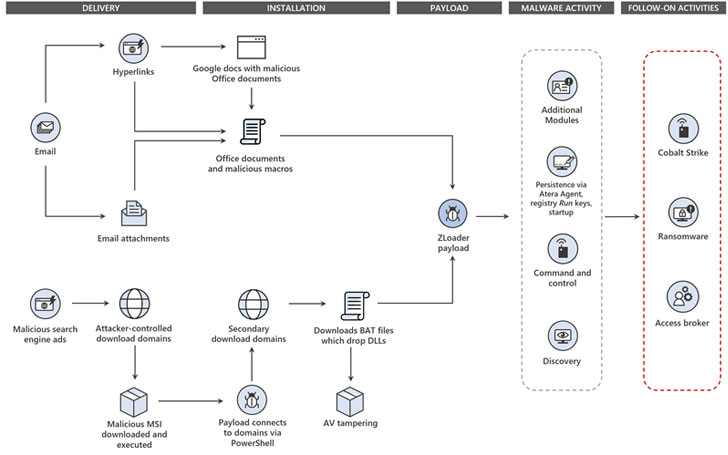
You can learn more about the ZLoader botnet takedown from a post from the HackerNews found HERE. The following diagram comes from that post showcasing a threat model of Zloader. It’s worth the time to perform a tabletop exercise against this threat model to test how your organization would respond in the event you find you have been compromised by something like Zloader.