This week’s product overview is Cisco Security Manager also known as CSM. For some people, hearing CSM makes them cringe as older versions from 4+ years ago had some issues. Personally, I consider the recent CSM release a completely different solution and I’m sure just by the screenshots, people familiar with the old version will not recognize anything as its been completely rebuilt.
Cisco Security Manager is used to manage multiple Cisco security products. Management includes centralizing configuration, quickly troubleshooting security events, unifying software versions, backing up configuration, enforcing policies for best practice, and reporting. Products that can be managed by CSM include ASAs, IPS modules / Appliances, Firewall Service Modules, ISR routers, Switches and VPN. Its installed as a software package but can also be purchased as a bundle with a UCS server for those looking for a appliance feel.

Once installed, CSM is accessed by using a client (the launch screen is shown as the top of this post). There is a separate interface for managing the actual CSM server and a client to access the management interface. The image above shows each desktop icon for launching access to the server and management center. When you launch the client and select Dashboard, you will get the next screenshot.
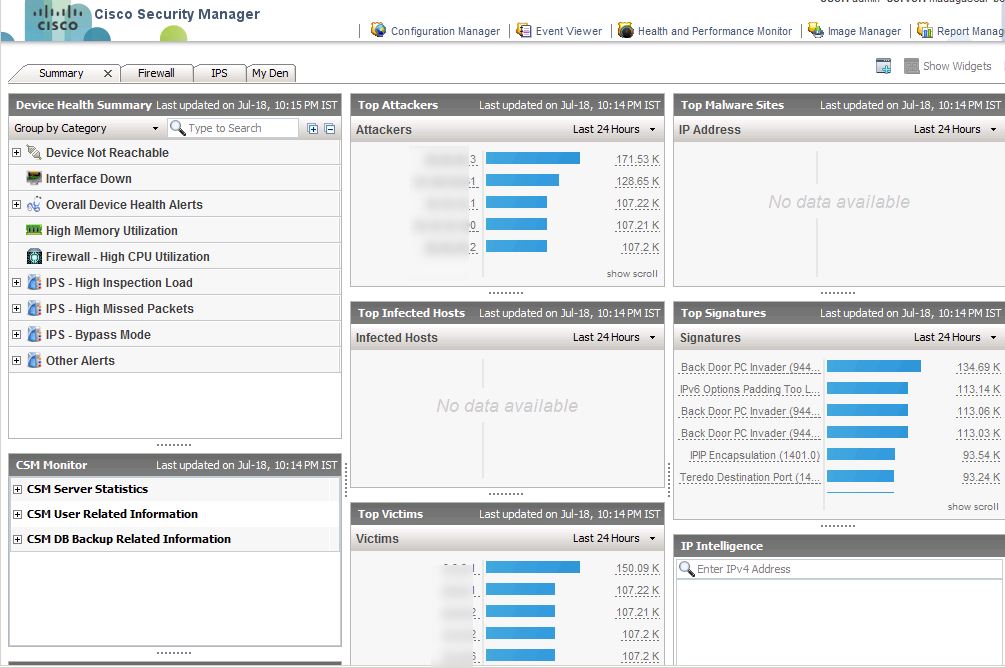
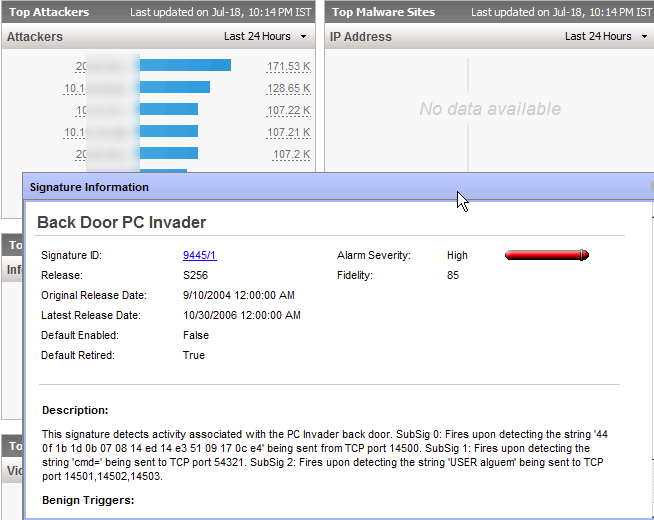
CSM has different modules that focus on specific tasks. The data in each module is the same however it may be displayed differently depending on what is being accomplished. The first module is the dashboard shown above. This provides a summery of all systems regarding what is reachable, top alerts, attacks, throughput loads, etc. The top left has tabs that focus on all Firewalls, IPSs and customized dashboards. The “my den” is an example of grouping together various device types to focus on that segment such as calling a group of devices “the Florida office”. The data windows are Widgets that can be customized to display various types of data the administration would want to see on a summery page. Everything is clickable. For example, I clicked a IPS alarm and the next screen shows the explanation page.
At the top are the other modules that can be launched as shown below. I’ll click the Configuration Manager to check out that module.
The configuration module is where administrators configure gear as well as enforce those configurations as policies. For example, you could say AAA must be installed on all devices and push that out as a policy. If any device comes on the network without AAA, it will set off alarms as being out of compliance, which in turn could have remediation steps in place.
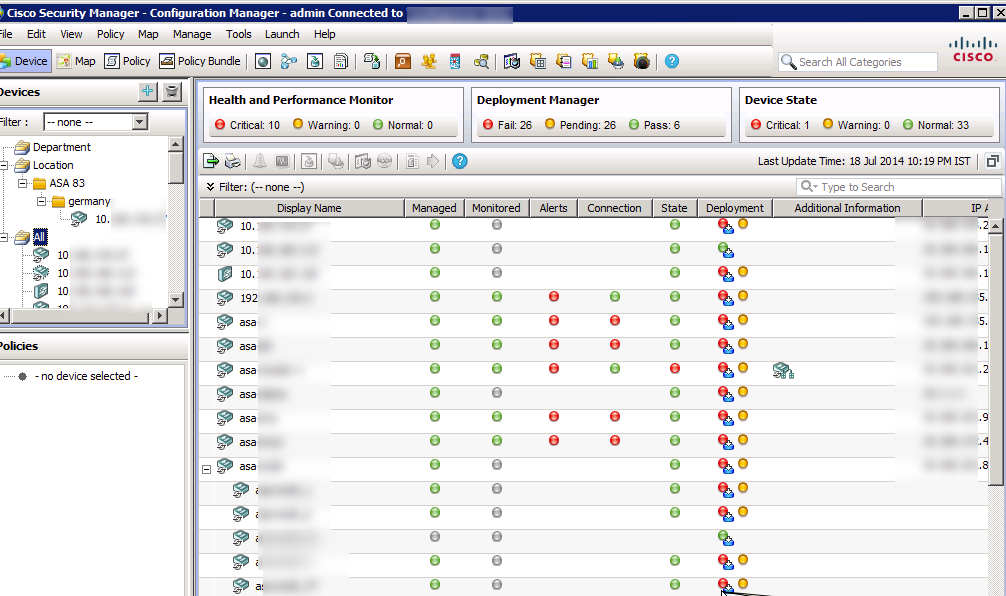
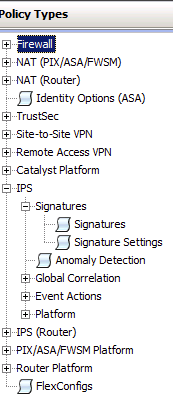
The image above shows a summery of devices and image below shows some example policy categories that can be pushed out to the managed devices. NOTE: You still can access devices via command line and their individual GUIs however CSM provides a way to unify configurations across multiple devices as well as prevent random admins from taking down a device due to “fat fingering” a command.
You can create a network map that lights up based on various alerts being triggered (for those that have large monitors in their datacenter and like a visual representation of the network). There are various focused managers within the configuration manager module such as VPN, or IPS with wizards simplifying deployment of tasks across multiple devices.
The next module shown is the Event Viewer main dashboard.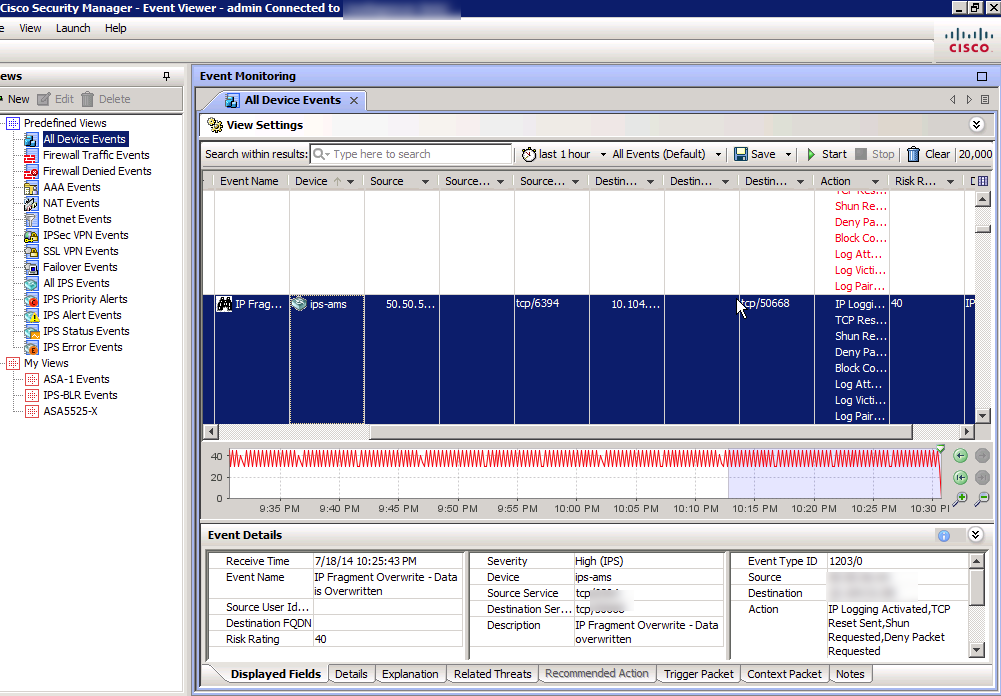
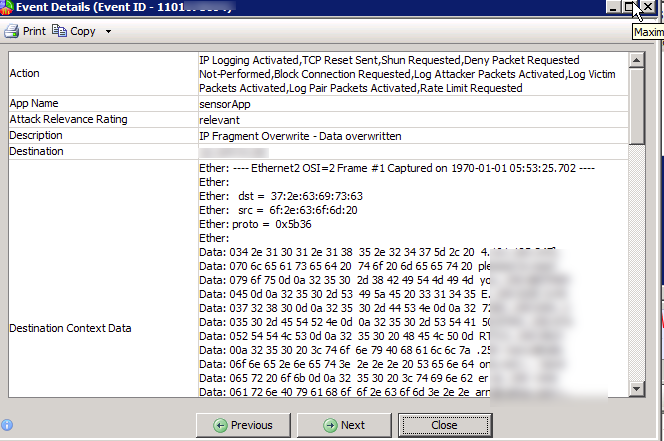
This is like a SIEM for those looking to shuffle through logs, events and identify the top things to focus on. On the left shows the different categories of devices to quickly locate your desired data. You can dive into any log and pull up the dirty details as shown.
There is a separate module for Health and Performance that I’ll open next.
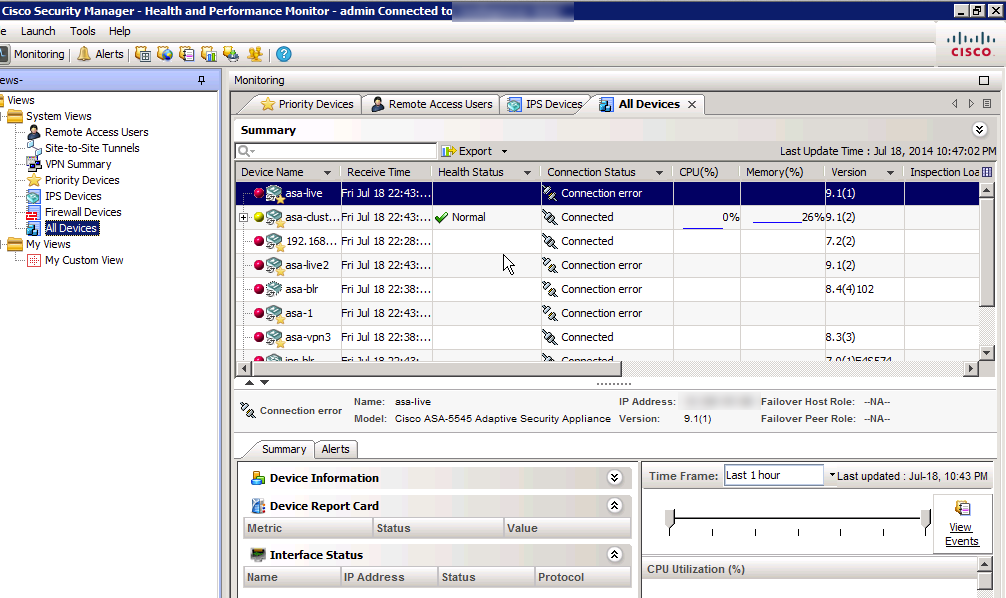 This is where admins can quickly identify if any system is over unitized or has interfaces down. Its like what WhatsUpGold use to provide for me as a administrator aka set off alarms if any device goes down. I can also check the state of VPN tunnels, who is remotely connected to my network, glance at versions installed, etc to give me a overall update on the health of my network.
This is where admins can quickly identify if any system is over unitized or has interfaces down. Its like what WhatsUpGold use to provide for me as a administrator aka set off alarms if any device goes down. I can also check the state of VPN tunnels, who is remotely connected to my network, glance at versions installed, etc to give me a overall update on the health of my network.
If you are looking to manage the software installed on devices, there is a module designed for this called the Image Manager shown next.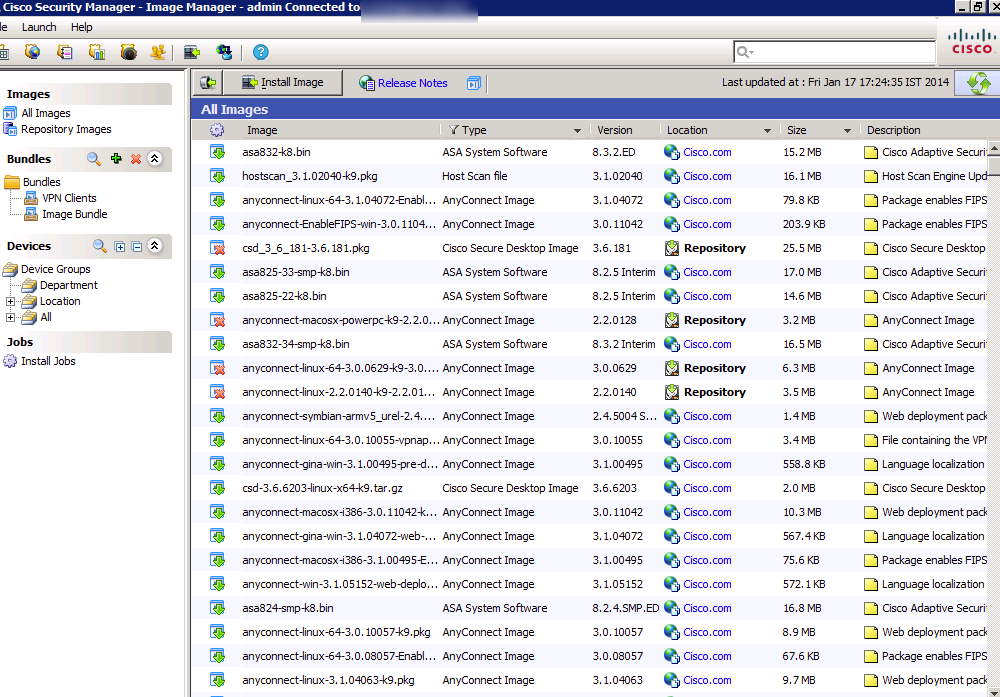
This will display all images installed and running on everything on your network. You can click a device and it will show all possible updates available with a smartnet contract, any software install not being used and details about what is currently running. This is a great tool for establishing a baseline for what should run on what type of hardware as well as removing software not being used that is wasting flash. Updates can be scheduled to be installed at future times when users are not on the network.
The last module to focus on is the Reporting Manager.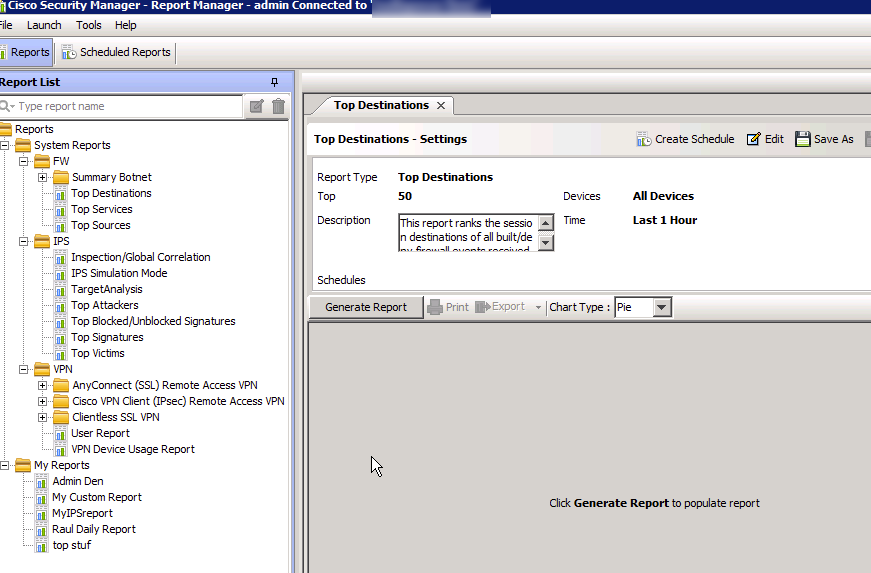
This is where you can generate reports live or scheduled on a reoccurring basis. Reports can be customized and delivered through a few methods such as emailing a PDF to [email protected] every monday at 2pm. The left shows tons of out of the box reports however you can create customized ones focusing on particular devices or data.
And that is a basic overview of Cisco Security Manager. You can more information on the latest version of Cisco Security Manager solution HERE. This includes videos on how to configure and manage CSM. My demo was showcasing 4.5 however as of this posting, 4.6 is the latest release.
Cisco also just released a service pack a few days ago that includes bug fixes and other updates. The complete list of bugs being fixed can be found HERE via the 4.6 SP1 release notes README doc.




Very interesting post,
Thanks a lot =)