A few weeks ago, Cisco published a major new update to Identity Services Engine (ISE) via the 3.0 update. This post will do a quick overview of what is new and provide some images and experience I had upgrading from 2.6 and comparing the 2.x vs 3.x experience. First, lets start with the upgrade.
Note: You can find everything ISE.30 related in the official release notes found at https://www.cisco.com/c/en/us/support/security/identity-services-engine/products-release-notes-list.html
Upgrading to 3.0
The upgrade process details can be found HERE. What I did was first validate I could go from my current version to 3.0. I can confirm this by clicking the “server information” at the top right hand corner.
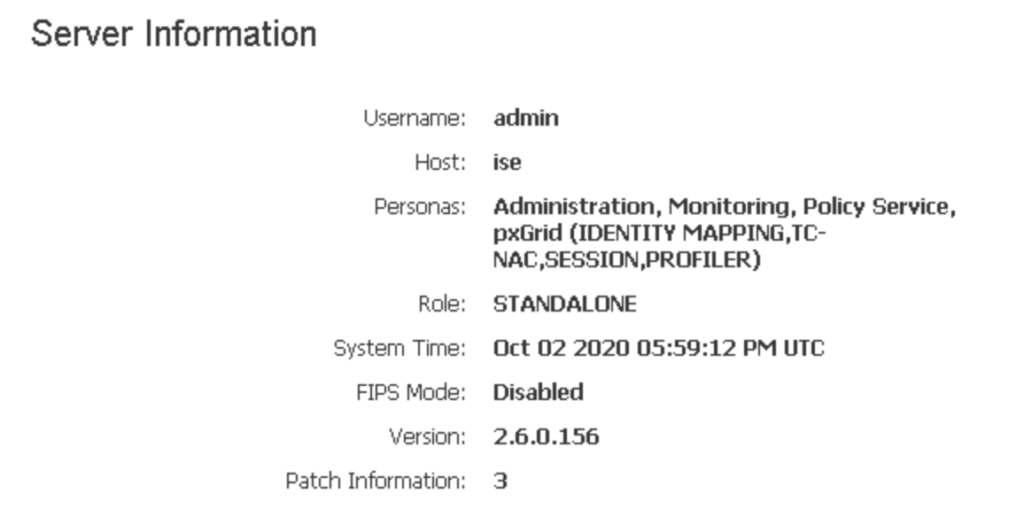
Since I’m running a lab that can be rebooted and broken, I skipped a lot of the checks and validation and went right into the upgrade. I downloaded the 11 gig file from cisco.com and placed it on a windows system. I installed filezilla server, created a user within filezilla, pointed the reference folder to where the image was sitting and tested that FTP works. This is done via on the same windows system opening a CLI promprt, type FTP <ip address> then type “user” to see if you have the login correct. Once you confirm that, go into ISE and create a repository as shown. I put X’s for part of the IP address of my windows system but everything else is as is.
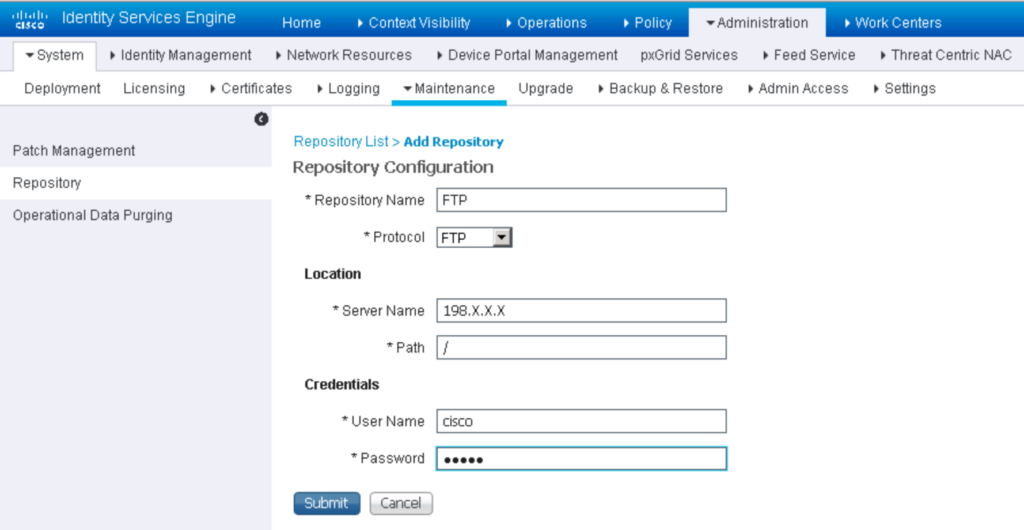
I used putty to connect into ISE and tested the repository by typing “show repository ftp”. At that point, I knew I was ready for the update. I clicked update, clicked through the accept and two hours later I had ISE 3.0.
ISE 3.0
First thing to notice is the GUI is different.
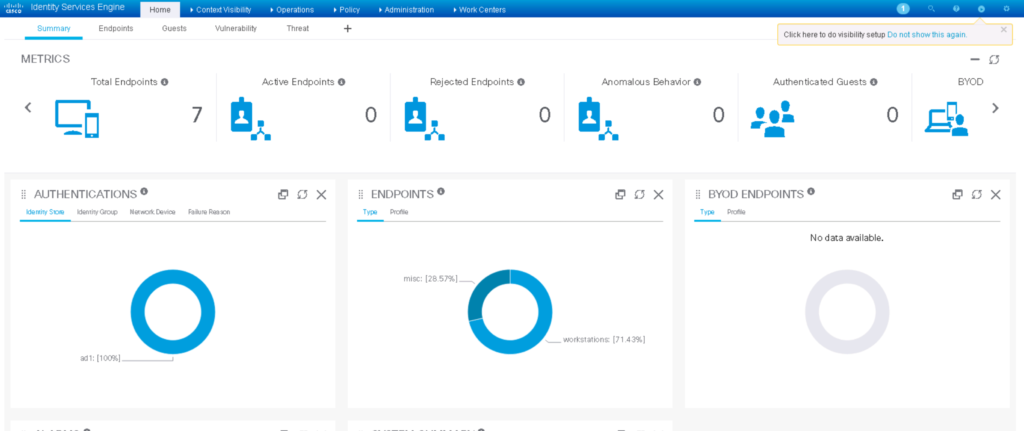
Compared to ISE 3.0
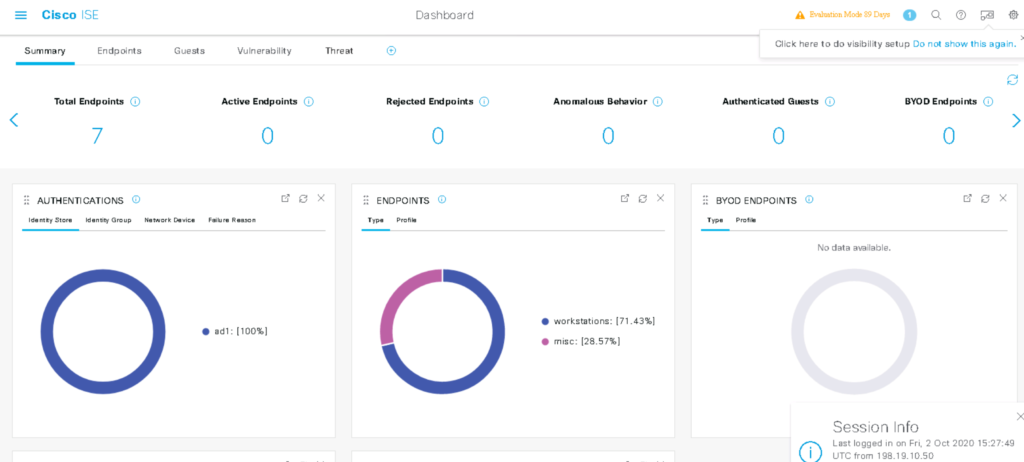
There are a ton of new things are new with 3.0. Here is a highlight of some of those updates.
- SAML SSO with Azure AD
- 802.1X with Azure AD
- ODBC Multiple Attributes Lookup
- Debug Wizard by Function
- TCP Dump Improvements
- Certificate Pinning for Multiple CAs
- Open TAC Cases from ISE
- Health Checks
- Make a Wish
- PassiveID with Windows Eventing APIs
- Device Identifier Changes for Windows Devices
- Baselines Policies with Microsoft SCCM
- Posture AV/AM Minimum Version
- Posture Session Status Sharing
- Windows & macOS Agentless Posture
- Endpoint Visibility with Custom Scripts
One dashboard add is the three line cheese burger representing administration seen in most modern GUIs was added to the top left.

When you click that, a huge swoop flies over putting you in the drivers seat to access various configuration options.

Within this page, you find the usual configuration options but it is just must cleaner. Also notice in the bottom left they took the idea of “make a wish” from Meraki meaning, you can make a wish for a new feature. This allows for super easy access to providing feedback directly to the developers.
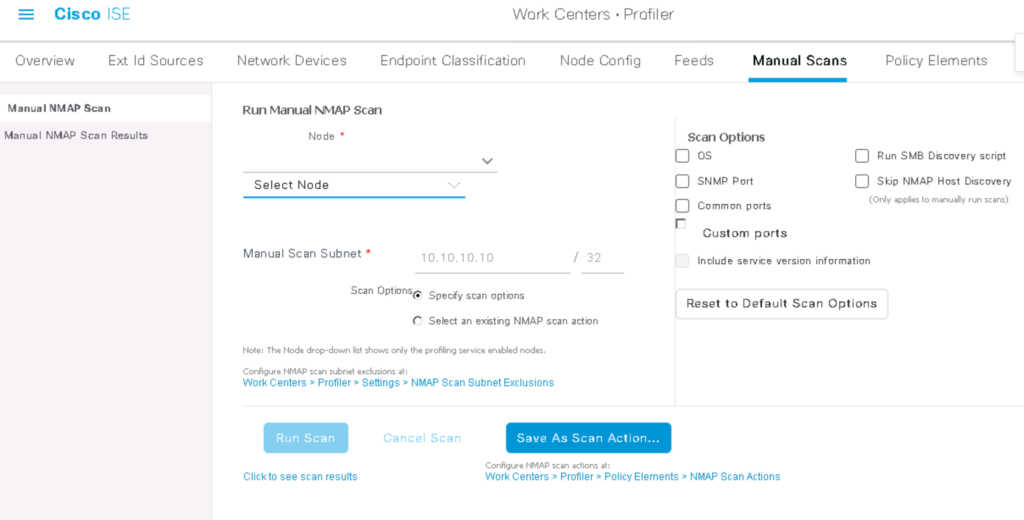
I found the manual scans option in ISE 3.0 is a simple way to get a collection of what is on your network now. Lets say an auditor needs a report of what installed on systems or what is connected to a subnet. This is a quick way to provide that information.
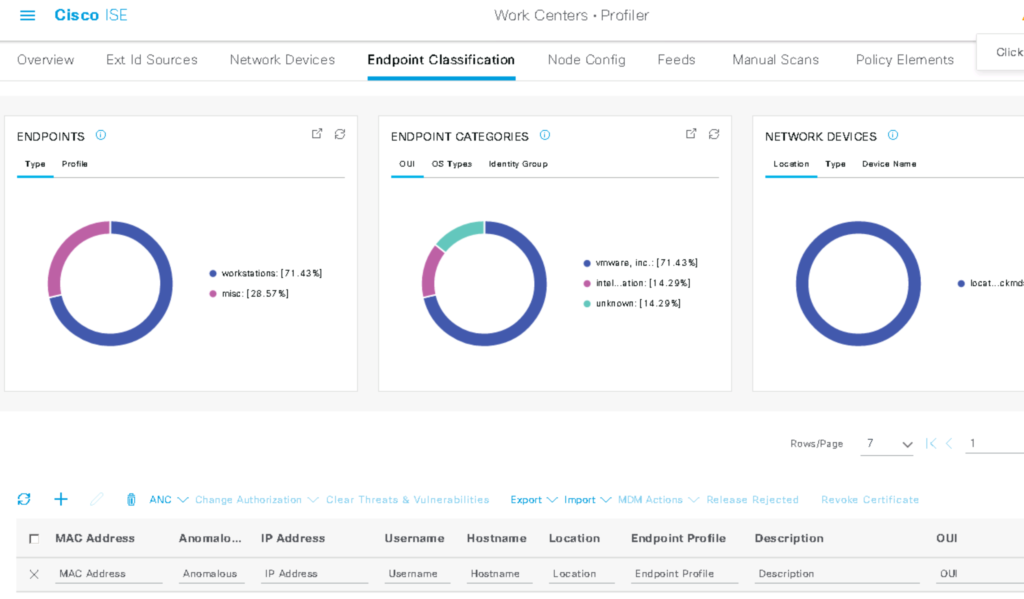
Same for gathering information on endpoints or the endpoint vulnerability page. The next image is the end point summary screen.
There is so much more but I’ve literally had 3.0 for less than an hour. More to come but at first look, the update looks really cool and seems much easier to navigate. I plan to try out some of the wizards, which are suppose to make troubleshooting super easy. Check back for a more deeper dive or reach out to me at [email protected] if you want access to a lab with ISE 3.0.


