Wow, what a crazy week! I’ve been slammed with questions about the heartbleed pandemic and thought I would provide a post answering “so what should I do?”.
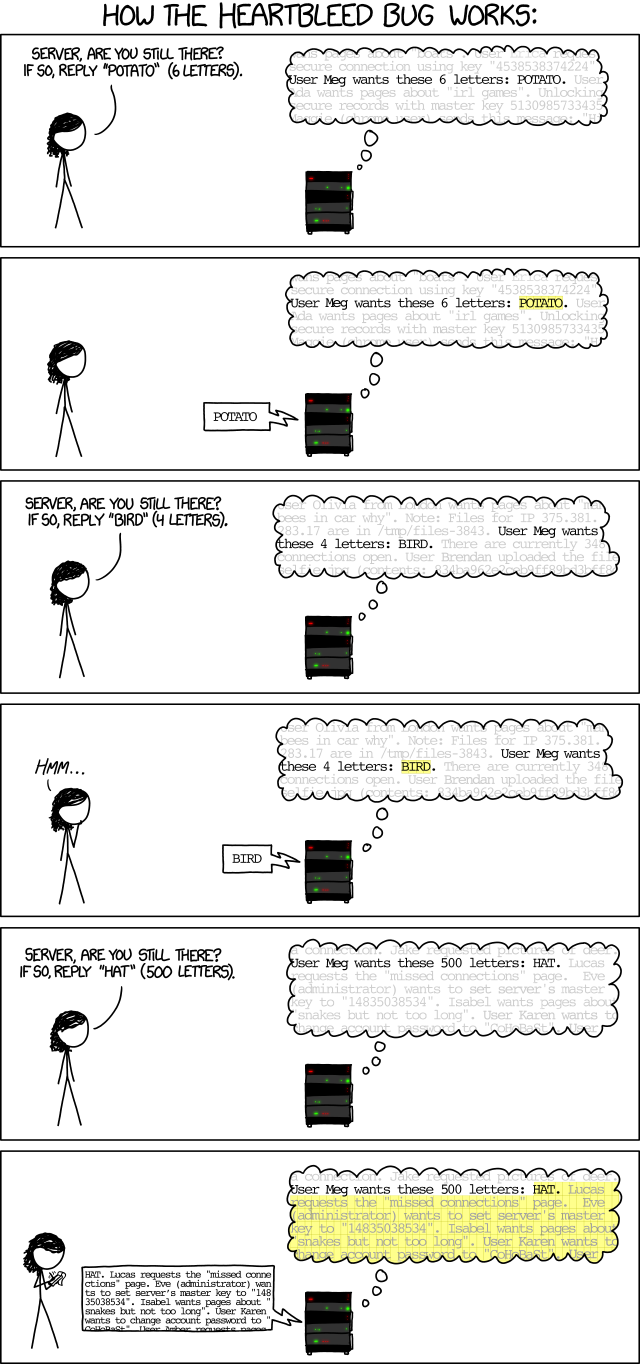
For those that don’t know about heartbleed, read this post HERE. I found this cartoon a entertaining way of explaining heartbleed in non-technical terms. The original cartoon can be found HERE via xkcd.com
What should you do?
The first thing to consider is anything Internet facing meaning systems insider your network that don’t interact with external users should not be your primary concern. Reason why is an attacker can’t potentially access them (assuming you are not breached by other means or the attacker isn’t a insider).
Next you should be focused on systems that could be vulnerable. So if you are using any modern type of Unix or Linux system, them you are very likely vulnerable to the bug. Microsoft systems use Microsoft Windows crypto so they are not vulnerable. I’ve been asking about routers, switches, xboxes, etc. The best advise I have is to go to the vendor’s website and search for a heartbleed advisory (using google searches on “heartbleed VENDOR NAME” or “heartbleed PRODUCT”. Most security vendors are listing what is being evaluated and what is and not vulnerable. For example, Cisco listed the ASA firewalls as not vulnerable as stated HERE along with other products.
Any systems found vulnerable should be upgraded via the suggested patch, upgraded OpenSSL to a newer version than 1.0.1f and all associated certificates should be revoked. There isn’t a forensics method to see if you have been breached so time shouldn’t be wasted on that type of investigation.
There are detection signatures being released by all major security vendors. If you have a IPS/IDS protecting your internal systems, make sure you update your signatures. Detection includes looking for the heartbeat request multiple times, requesting the wrong data size, etc. See the CVE-2014-0160 for more info. An example is Snort did a update yesterday found HERE. SourceFire customers should make sure Signature IDs 30510 through 30517 are enabled.
Products with reputation based security would help by limiting communication with only trusted sources. For example, most attackers wouldn’t launch an exploit from their home network. This means blocking communication from high risk web sources limits how an attacker to communicate with a potentially vulnerable server. More on this concept can be found HERE.
Behavior based technology can detect anomalies such using NetFlow to detect a remote user making repeated attempts to access data. Lancope talks about this HERE using StealthWatch.
As a user, you can use a few tools available online to evaluate a website for the heartbleed vulnerability. One problem with the test is many security products are enabling prevention capabilities which also stops remote evaluation tools from working properly possibly providing a false positive or negative. Some examples of tools are
- https://lastpass.com/heartbleed/
- https://www.ssllabs.com/ssltest/
- http://filippo.io/Heartbleed/
The best user advise is to change all your passwords. ABC news posted HERE about sites that may or may not be impacted meaning which sites you should change passwords on. My advise is also not only change your passwords, but enable multi-factor security if available. For example, on social media sites such as Facebook, you can have Facebook send you a text message anytime a new system logs in under your account. This additional step ensures somebody hasn’t breached your account unless they have stolen your personal device to access the system.
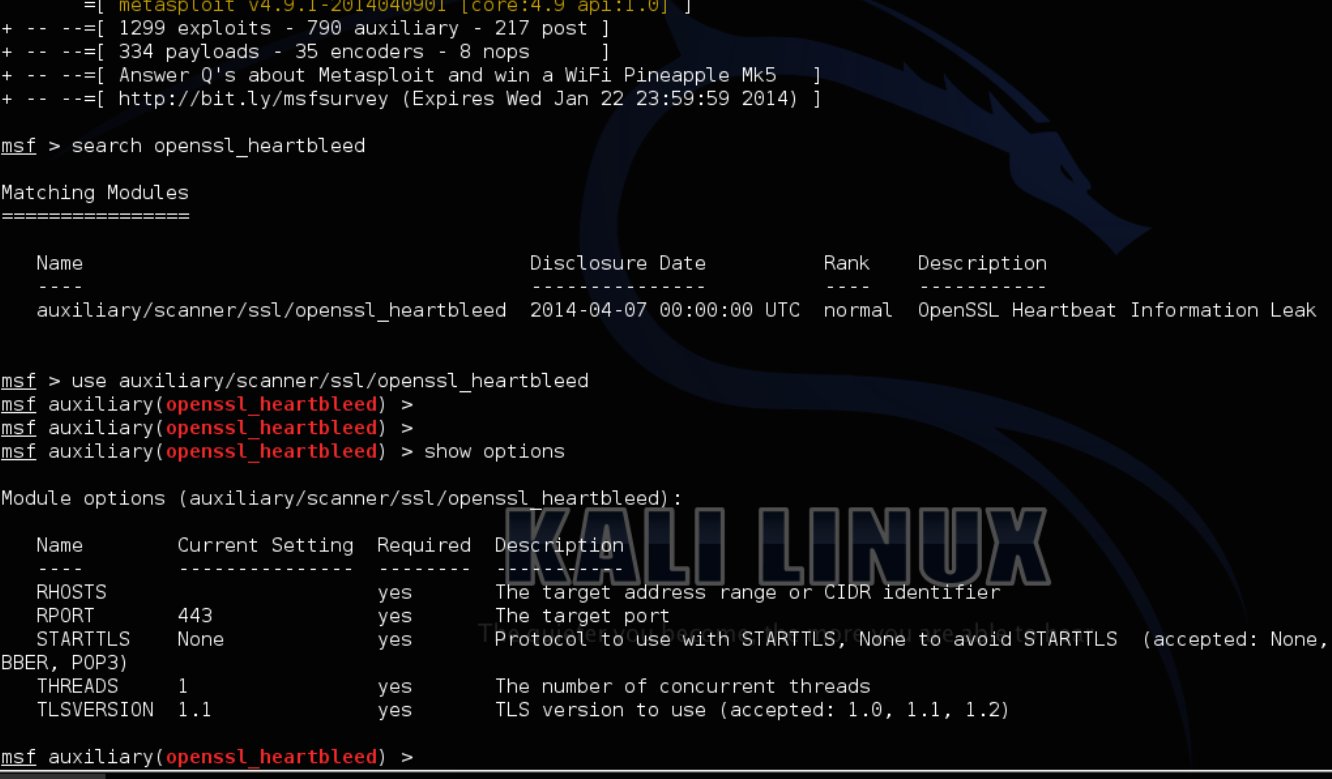
If you want to penetration test your own systems, the metasploit framework now has an exploit available. The next screenshot shows me pulling up the heartbleed exploit and doing a show options to see how its executed. More on using metasploit can be found HERE.
Hopefully this helps answer the burning question “what should I do about heartbleed”?