Management of security devices is a critical function for maintaining the best performance and being aware of security related events. Cisco has released their second generation of ASA, which includes new management options. This post will cover the new management interface and compare it to the previous options.
Cisco next generation ASA
Here is the quick and dirty on Cisco’s next generation adaptive security appliances (2nd generation ASA). Cisco first entered the firewall market with the Pix firewall appliance. Later, Cisco combined their VPN 3000 concentrator and Pix firewall to form the Adaptive Security Appliance also known as the ASA. The ASA offered modules for adding additional security features such as IPS/IDS and malware / content filtering however you would have to purchase the hardware module along with associated licenses.
1st Gen ASA with IPS module
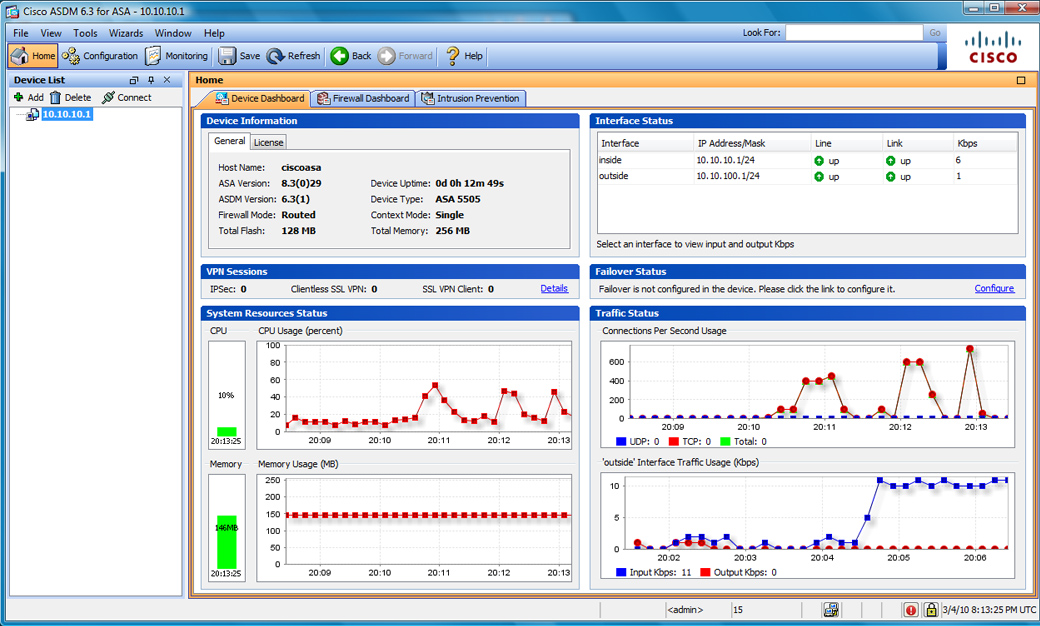
To manage the original ASA, you could use command line, local management with ASDM or manage multiple security appliances using Cisco Security Manger (CSM). ASDM is free and local to each appliance while CSM has a cost and an external management system. Both management options run on Java. To manage module additions, you could see basic information in ASDM however they would have their own management interfaces such as the IPS having IPS manager express … which is also java based.
ASDM Dashboard for 1st Gen ASA
Today people expect more from their traditional firewalls hence the call for “next generation firewall”. What this typically means is a few things
1) Ability to see all layers of the protocol stack aka applications. I can tell you that Joey’s windows laptop using firefox is accessing the Facebook game Farmsville.
2) Consolidating hardware meaning providing IPS, Application visibility, Stateful firewall, VPN and Reputation / cloud based security in one appliance.
3) Leveraging the cloud aka security research mixed with customer data. Basically, being able to learn about attacks happening on your or other networkers so the security product is aware of more than its silo part of the network.
The 2nd Generation ASA offers all of this aka Stateful firewall, various flavors of VPN, IPS, Application visibility and Reputation using the ASA with CX offering. You can can learn more about the next generation ASA CX HERE.
Management
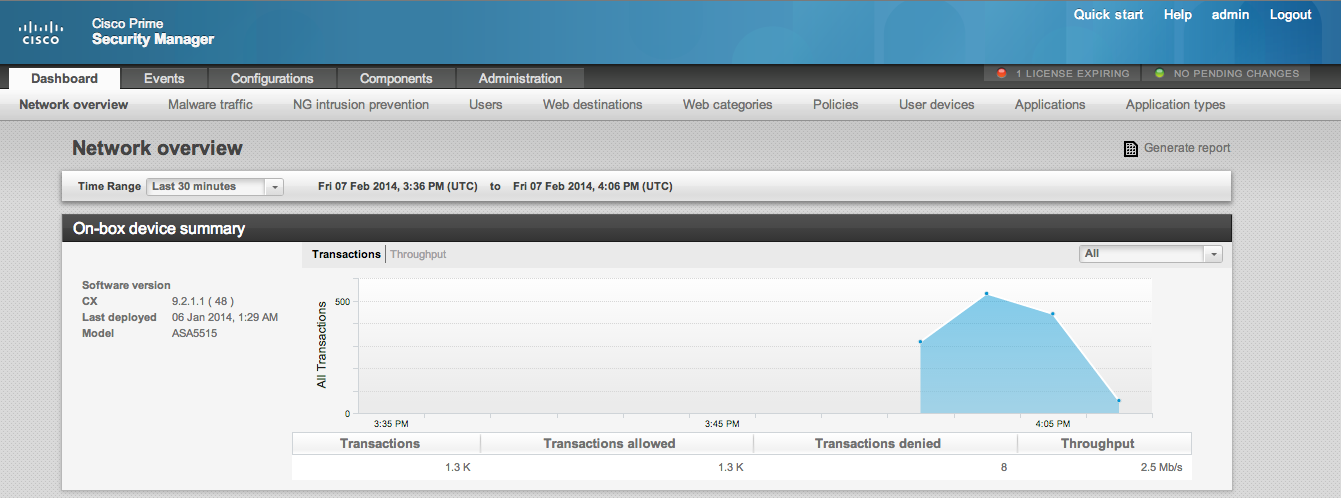
The 2nd generation ASA has two options for managing the next generation features. Option 1 is similar to ASDM meaning you access an IP address local to the ASA and open Local Prime Security Manager. This gives you the ability to configure the single ASA CX module. The ASA CX has a separate IP address from the core ASA appliance meaning if you have the ASA as 10.1.1.10 and ASA CX is 10.1.1.20, going to .10 would offer ASDM to manage the core ASA while .20 will bring up Local PRSM to manage the next generation features. Both are free as beer (well beer has a cost so not sure why people say that).
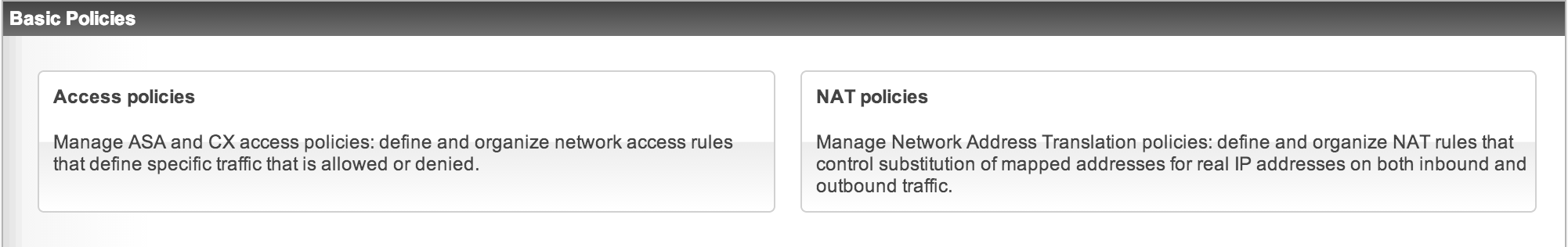
For those that want to centralize managing all security features for both 1st and 2nd generation ASAs, Cisco offers External Prime security manger. For example, you can push out one Access List or Policy to enforce something to all security solutions on your network (ASA 5520s, ASA5545s and any CX modules as an example). External Prime can be an appliance or VM and has a cost. Compare it to a next generation Cisco Security Manager (CSM) however some features have not yet become available in External Prime that are available in CSM as of this post.
Comparing Dashboards Between Local and External Management
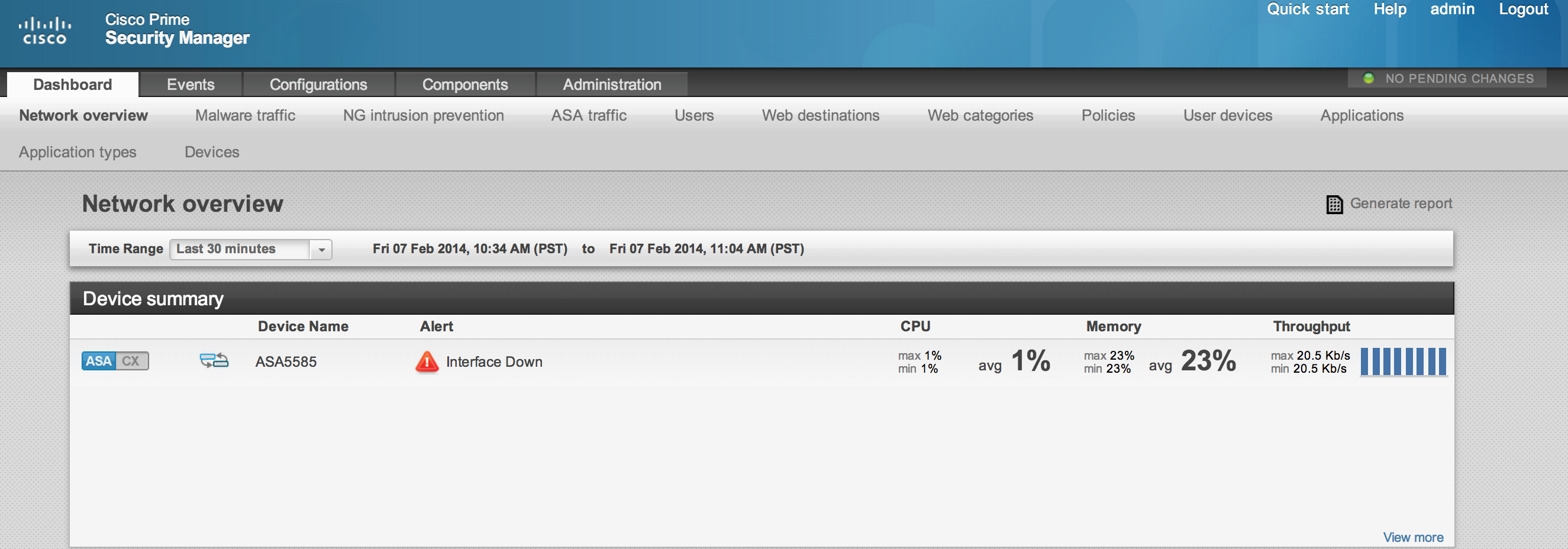 External Manager Showing Options and ASA8858 with CX
External Manager Showing Options and ASA8858 with CX
Local ASA Management Show Dashboard options
As you can see from the above images, all of the next generation features such as IPS, Application Layer Traffic and so on in both Internal and External Prime. The major difference is the External PRSM can manage multiple ASAs and give configuration options for all versions of ASA appliances as well as ASA CX modules. For example, you can click the CX tab on the external prime in the image above to see how that module is operating within the ASA 5585 appliance as well as the core ASA’s current operation status. If you add more Firewalls, you would see them listed in the status widget.
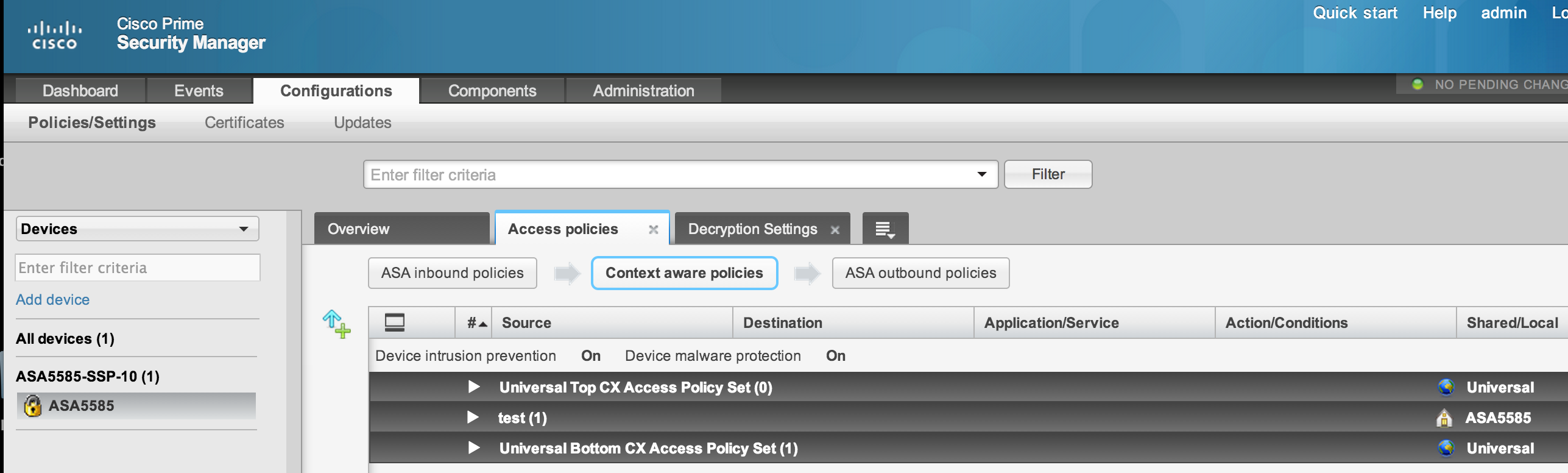
The Next Image shows creating policies that can impact an ASA along with Context / Application traffic. An admin can search the entire network for any user on a iPad accessing NetFlix or deny something such as Skype network wide from one GUI. Another example is selecting the NAT policy tab shown below to develop how you want IP addresses to translate as traffic travels across your network. Setting up and monitoring high availability is another great use case for centralized management.
PRSM Policy Tab
PRSM Access and NAT policy tabs
To summarize, the first generation ASAs have ASDM as a free GUI management and alternative to command line for managing a single ASA. If you were looking to manage multiple ASAs as well as other security features such as IPS, you would purchase Cisco Security Manager as a external management platform to centralize management to one interface.
The next generation ASAs can be managed in a similar manner using ASDM, Local PRSM or CLI to manage the system (PRSM being the new web GUI). If you are looking to centralize management of multiple 1st or 2nd generation ASAs with all next generation features from CX (IPS, Application and Policy Enforcement, and so on), you should consider External PRSM as your single management interface. All CSM features such as VPN are not available in Prime yet but are planed for a release this year. Check out www.cisco.com/go/asacx to see the current release status regarding available features for both ASA CX and Prime Security Manager.
Here is a short list comparing local vs external Prime Security Manager
Off-Box Prime Security Manager has:
- More capacity to store real-time and historical events (depending on VM or Appliance)
- Built-in RBAC
- Reports to PDF
- Policy Sharing across devices
- Configuration sharing across devices
- ASA and NGFW Management
On-Box Prime Security Manager has:
- Full NGFW Management Only
- Real-time events
NOTE: Prime Security Manager does not manage the older Cisco IPS/IDS appliances or modules. You will need to use IPS Manager Express or CSM for that.