 Free file sharing services such as LimeWire, FrostWire and UTorrent in most forms is illegal (note: there are legal sources however this post is focusing on file-sharing of pirated content). The cost of music, software and other applications are becoming more expensive to accommodate lost revenue caused by piracy spread through file sharing. As the price goes up to make up lost revenue, more people join file sharing networks. It’s a vicious cycle. There is however a more important reason besides ethics, law and cost to not be involved with file sharing services. Like my mother use to say … “nothing is free in this world”. Most of the pirated goods from file sharing you believe are free actually come at a very high price to your system and privacy.
Free file sharing services such as LimeWire, FrostWire and UTorrent in most forms is illegal (note: there are legal sources however this post is focusing on file-sharing of pirated content). The cost of music, software and other applications are becoming more expensive to accommodate lost revenue caused by piracy spread through file sharing. As the price goes up to make up lost revenue, more people join file sharing networks. It’s a vicious cycle. There is however a more important reason besides ethics, law and cost to not be involved with file sharing services. Like my mother use to say … “nothing is free in this world”. Most of the pirated goods from file sharing you believe are free actually come at a very high price to your system and privacy.
Nuclear RAT rootkit
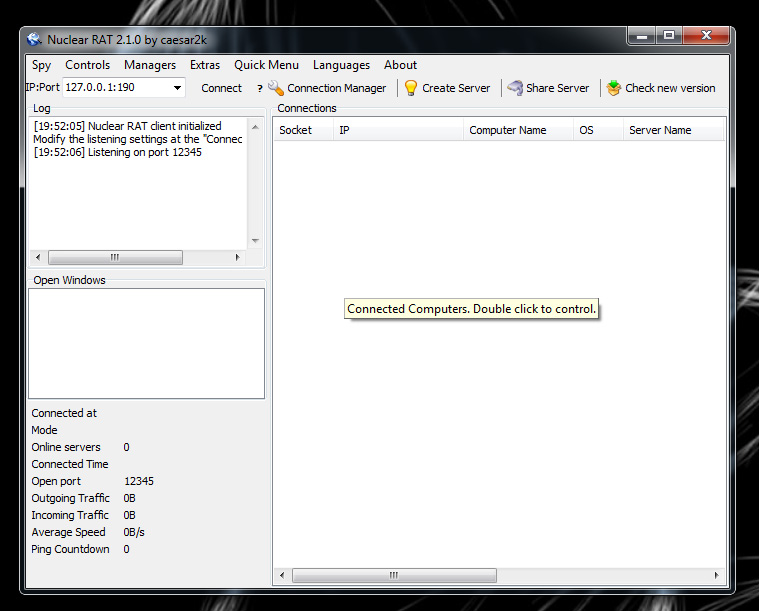 There are many malicious applications used by hackers to gain access to a system. The worst form is a Rootkit. Rootkits gain full control of a system without the victim’s knowledge and typically are very hard to detect and remove. Many popular rootkits include covert channel communication tools to hide phone home attempts from modern security tools. The rootkit example above is called Nuclear RAT (Remote Access Tool found at nuclearwintercrew.com). The image is the RAT server GUI that manages connections from Rootkits placed on systems. Some spy options include seeing the victim’s screen, logging keystrokes, controlling the mouse, opening a remote shell and so on (see images). There are options to hide RAT such as Melt Server (deletes executable) and using Stealth Shell Folders so you won’t see it running. Once installed, an attacker owns your system.
There are many malicious applications used by hackers to gain access to a system. The worst form is a Rootkit. Rootkits gain full control of a system without the victim’s knowledge and typically are very hard to detect and remove. Many popular rootkits include covert channel communication tools to hide phone home attempts from modern security tools. The rootkit example above is called Nuclear RAT (Remote Access Tool found at nuclearwintercrew.com). The image is the RAT server GUI that manages connections from Rootkits placed on systems. Some spy options include seeing the victim’s screen, logging keystrokes, controlling the mouse, opening a remote shell and so on (see images). There are options to hide RAT such as Melt Server (deletes executable) and using Stealth Shell Folders so you won’t see it running. Once installed, an attacker owns your system.
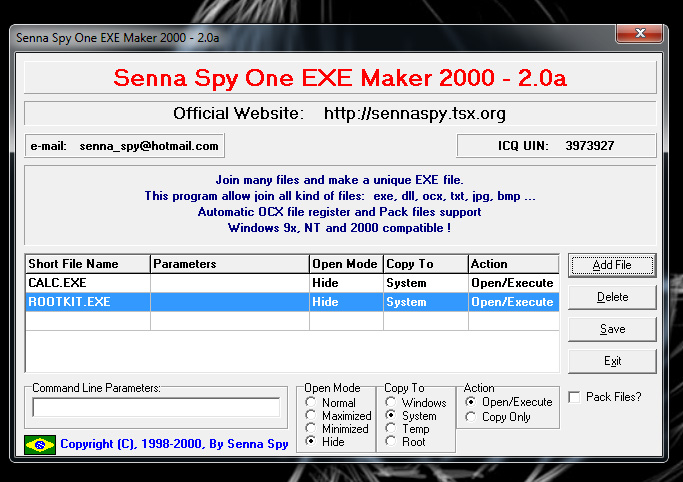
Rootkits like RAT can be wrapped inside normal programs. A hacker can take a common program like Photoshop and wrap it with RAT. When a user executes Photoshop, they actually install both Photoshop and RAT. Wrapping can be done with almost any file type so don’t think avoiding .exe on a file share will keep you safe! Senna is a popular wrapping software. The picture below shows wrapping the default windows calculator program with RAT. To do this, I choose the safe file (calc.exe) and rootkit. Once it’s wrapped, anytime somebody runs the calculator, the calculator will functional normally however my rootkit will be installed in the background and all evidence of its existence will be hidden. Only a very skilled forensic investigation would be able to detect its presence. Imagine normal applications such as outlook or explorer wrapped with a rootkit and spread across your network. This is how compromising one system could lead to compromising the entire network!
Senna GUI
Developing Trojan software for file sharing is that easy. Any script kitty can Google “Rootkit”, “Application Wrapper”, pick a common desired software and build malware in a matter of minutes. So, do you still NEED that Snoop Dog remix of My Shorona? How about that pirated movie recorded with a hidden camera? Are you not willing to fork over a few hundred dollars for the latest Photoshop? Well go start file sharing and trade over control of your computer and privacy. Is your computer worth the trade? How about all the information you access such as bank accounts, company records and other sensitive data. If you look at the options for RAT above, you will see Webcam. Imagine what that means (hint, don’t undress in front of your computer). 




Very informative post. I’m reminded of my days in college when people were using Napster to download hundreds of songs. My classmates often downloaded free design software like Photoshop. I’m sure this downloading is still very common, but with torrents. Is there a software out there that can detect when an application or file has been wrapped with RAT? Seems like software like that would be very popular.
Hi Devin,
Unfortunately the only way is using checksums of the software against the developer’s website to see if its been modified. Usually a easy way to do this is download directly from the solution provider’s website or a trusted partner (example get photoshop from adobe or a adobe reseller). File sharing means you don’t know where the software originated from.
Some host based applications can detect the presence of rootkits. Also some large security companies such as Symantec, McAfee and Sophos also include limited scanning of files executed. This by far doesn’t cover the vast amount of “day zero” aka unknown rootkits that security vendors haven’t developed a signature for. I always like malwarebits, spybot and some other freeware detection software. I noticed in the past when a friend calls me in to help out with a painful rootkit compromise, there is typically a specific removal software available on google. The problem is most people never know they are owned since they only rely on commercial anti-virus and host based firewalls for security. Hope this helps
Joey,
Great post! Root kits are very common and very difficult to detect, even with modern anti-virus. Enterprise white listing software such as Bit9 is one of the best endpoint security tools that I have seen that guard against root kits. Another good tool is Lancope’s stealthwatch product which can defend against insider threats. These tools are for large corporations, and right now there is nothing that really comes close on the consumer side that provides this sort of protection.
Please stop spreading bad information. File sharing software is as legal as web browsing or email client software.
People breaking speeding limits, blowing stop signs and red lights don’t make cars or driving ilegal.
Same thing applies to file sharing software, internet browsers and email clients, all technologies that can be misused, also copyright laws vary from country to country and it’s best to know your local laws to not get in any trouble.
Thanks.
Well said Gubatron. I agree. I do however want to make a few points clear about this post. First off, law is behind technology so relying only on that for your judgement is not wise. People can perform recon on DOD networks and be legal as long as they don’t accept the ACK HOWEVER I assure you its a bad idea regardless. Second, the point of this article is to expose the threats associated with illegal file shares. There are many creditable file sharing sources and methods that are safe and legal (example dropbox is awesome). Regardless there are tons of illegal sharing and people should know the truth behind the intent of trojan software being advertised. Hopefully this post will give people a better reason than ethics or law to avoid pirated software. If a handful of people avoid being owned by trojan software due to awareness of risk associated with illegal file sharing, then the post has done its job.
Thanks for your input. I have added a note to clarify this in the post