One really cool tool that I’ve had a lot of fun playing with is the Raspberry Pi. My buddy Aamir Lakhani and I recently went under contract for our second book covering how to run Kali Linux on a Raspberry Pi to perform various penetration testing scenarios. Here is a basic overview of the Raspberry Pi used as a security tool. The book should be out early next year.
For those that haven’t heard of a Raspberry Pi, it’s a small computer that is dirt cheap and can be imaged for just about anything. For example, there are many penetration testing arsenals that have customized versions also known as “ARM” images that function nicely on the Raspberry Pi. The Raspberry Pi ARM images tend to not include as many tools as a full installation based on the need to meet the limited storage and processing capabilities offered by a Raspberry Pi.
Purchasing a Raspberry Pi is pretty straight forward. You can find the basic B+ model for around 40 dollars on Amazon, however you only get the core system.
A Raspberry Pi B+ default system
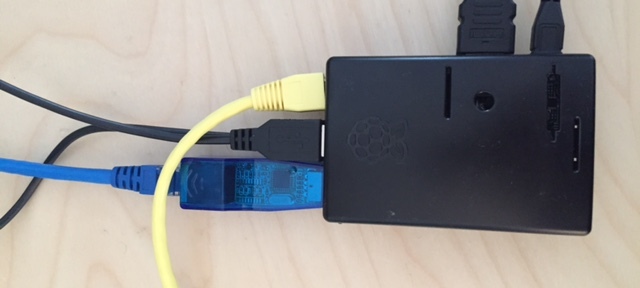
You will need a micro SD card to run an operating system as well as a power adapter for core requirements. There are four USB ports that are used for things like keyboards, mice, wireless adapters and so forth. The B+ module has one Ethernet port so you may want to pick up a USB to Ethernet or USB to Wireless adapter for things like man-in-the-middle attacks (the first screenshot in this post shows the Raspberry Pi as a man-in-the-middle tap). I found both of these adapters on amazon for around 10 dollars.
USB to Ethernet adaptor
There are bundles that include these items as well as various flavors of cases to protect your mini computer for around 80 bucks. One bundle I purchased included a ton of other additional wires, lights and cables I probably won’t use but I guess are nice to have.
Raspberry Pi Bundle Purchased on Amazon
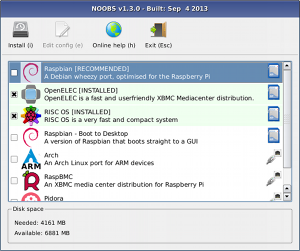
You will need a way to put the SD card into your computer. My MAC has a SD port so I had to pick up a SD to microSD card to be able put it in my computer. This adapter was around 7 bucks on amazon. There are many free open source software packages that can be used to format the microSD prior to loading the software. My Raspberry Pi’s microSD came with the NOOBS image preinstalled. This software offers a few operating system options you can select to be installed on the Pi. Its important to backup the software prior to running it as it wipes the main NOOBS stuff once an operating system is selected. If you happen to forget to do this, the NOOBS image is available to download. For my focus, I wiped that image when installing Kali Linux since it is not one of the NOOBS options.
NOOBS software options example
Installing Raspbian
The Kali Linux ARM image is pretty straight forward to install and run. I found some issues while going the process but in many cases, updating things and doing a little research helped me get through it (see the upcoming book for details on the installation process). A lot of the tools I liked were not installed so I had to apt-get install many things prior to using the Pi for my desired exercises. I highly recommend testing the tools you use in a lab prior to going live as many crashed my Pi or rendered it useless due to overloading the processors. I found it was typically a best practice to avoid GUI based tools and apply filtering whenever possible. For example, if you capture packets and try to store them, you will quickly run out of hard drive space. A better approach is only storing key data such as POST requests containing user logins.
Overall the Raspberry Pi offers a ton of value beyond its cool factor. One could easily hide it at a target’s location using things like placing it in a book, wall clock or empty power adapter. There are USB based power sources that work for the Pi however for long term breaches, you probably want to hide it in a way that gives it power such as hiding it in a printer power supply. The dollar value appeal is also great for buying these and using them for remote penetration testing units that can help reduce the need to travel to multiple locations. Customers will happily pay 80 dollars for a Pi over the thousands it would cost in travel for a security specialist to come on site. If you use it as a rouge attack device and it gets found, the dollar lost is a lot lower than hire priced tools such as the PWNIE Express. Speaking of that, there is a PWNIE Express ARM image available for the Raspberry Pi as well.
We are having a lot of fun putting this second book together and look forward to its release.




This is quite cool.. share with us your experiences regarding issues with pentesting on raspberry pi.
I can post a few things however that would take away from the upcoming book 🙂 . In summary, the book will talk about how the Raspberry Pi has limited resources so many tools found in Kali Linux are not available in the ARM image. There are many suggestions around how to tune things to run properly as well as establishing back doors to a remote C&C server that will carry loads requiring heavy processing. Look out for a few teaser posts prior to the books release Early next year.
new Pi came out double the power it could do more now!
How about this: http://pwnpi.sourceforge.net/