Here is a interesting post from Billy Austin found on www.drchaos.com HERE
What 3rd party apps do remote workers have installed?
Remote workers are nothing new, but the challenge of hunting down employees on-the-go and assessing these devices can be a task in and of itself. With the increase of cyber incidents triggered by remote connectivity & insecure 3rd party apps, one would think these devices are in-scope for security and compliance quarterly checkup scans. After speaking with security and auditing colleagues, it proved to be quite the opposite.
Why you should care about 3rd party client software
When analyzing exploit development and attacks trends, one will find concentration is centered around popular client applications such as Browsers, Adobe and JAVA. Attack code that takes advantage of such 3rd party apps are known as client exploits. Poor configurations and un-patched laptops are still the norm, while unknown or forgotten installed vulnerable software is often overlooked, but not by the Bad Guys.
Hackers understand this and so should the rest of the industry tasked with protecting remote employee computing. Penetration testers find a high success rate when simulating a client exploitation attack against remote workers. A few takeaways here: Attacks targeted around the telecommuter are increasing as BYOD laptops trend to be juicy un-patched systems with an intent of gaining entry to the corporate fortress. The attack process is merely to entice an employee to click a link, connect to an insecure wifi access point or visit a website, whereby the exploit takes advantage of the non-patched 3rd party client software.
Why bang away at external network devices where border security is increasingly tightened, when what’s in your pocket or briefcase is where hacker fertility awaits.
When speaking with our Managed Service Provider partners here at iScan that understand the endpoint, Systems management and RMM footprints appear to be growing as teleworkers increase. Scanning, Patching and Configuring are equally important for internal devices, although the what’s in your pocket and briefcase tend to be neglected by most. If you don’t use a service provider or have a challenge answering “How vulnerable are my employees’ device”, let’s look at another option of discovering exactly what 3rd party software is on such endpoints.
How to discover what’s installed, simple and fast
A. Run the free sample script provided below
B. Try iScan Online’s free Inventory scan to enumerate all HW/SW details
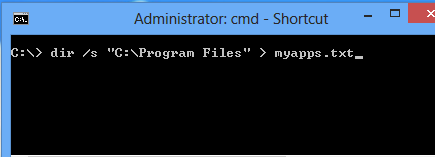
DOS Prompt + Script
Whether you’re a skilled consultant or a novice technological enthusiast, this script is simple but loaded with information and takes roughly a few seconds to perform. In Windows, navigate to your terminal window, aka a DOS or CLI prompt and enter:
C:\> dir /s “C:\Program Files” > myapps.txt
This will create a file called myapps.txt discovering your installed apps with the name of the application, last patch date, versions and more. Once you have performed this exercise, open the “myapps.txt” file to have a peek. If you assess or audit systems, this script should come in handy down the road.
iScan Inventory Scan or Script
For consultants and service providers with an iScan Online account, additional hardware and software details are uncovered. iScan’s Inventory scan type takes roughly 2-3 seconds and produces results in HTML, PDF or JSON. Sample iScan Inventory Report.
Removing the barriers of assessing the remote user, iScan includes several delivery options and sample usage:
- CLI executable – Utilize any systems management tool to initiate the script, create login scripts or add it to your batch file, scanning users upon VPN connectivity. Active Directory can also initiate and schedule tasks with the iScan binary.
- Browser Plugin – Send an email with a URL where the user initiates the inventory. Alternatively, an iScan HTML snippet can be embedded into any web app that can also auto-facilitate the scan discovery
- RMM Procedures – Remote Monitoring & Management tools are popular with MSP’s and iScan includes pre-configured procedures for Kaseya, Labtech and others for Inventory Discovery & many other Scan types.
- Executable plus a visual – This creative example illustrates a CLI Script that will trigger a browser to automatically open, scan and present the results to the user
Regardless of the method or script chosen, inventory assessments take 2 seconds and in most cases, provide a wealth of value to the assessor. This should not be a substitute for scanning and keeping remote laptops updated, but purely another method of discovering potentially vulnerable apps.
In short, ensure your consultant or service provider is assessing 100% of your devices and not a partial assessment for what is physically at the office. If you have challenges for assessing remote on-the-go employees or teleworkers, drop us a line to learn more about iScan Online’s compliance, vulnerability and data discovery scanning solutions.
To learn more visit: iScanOnline at http://www.iscanonline.com/