Want to protect your privacy when using the Internet? Well unfortunately that is tough to do these days. Many agencies and governments are investing in network surveillance programs to monitor Internet traffic. Firewalls can offer application visibility packages capable of identifying device and browser type, where people are surfing the Internet and what applications are being accessed. Most websites include tracking cookies that gather data about users accessing their resources. Data obtained about you is used for various things you probably are not aware of and may not approve. This includes selling that data to large marking firms that eventually turns into SPAM and other unwanted contact. A more extreme example of unauthorized surveillance is covered by Jacob Appelbaum’s talk on the US governments Internet spy tools (found HERE). Its eye opening!
The good news is there are measures you can take to protect your privacy. The most popular way to access the Internet while preserving your privacy and anonymity is using the Tor network (info on Tor found HERE). Tor is a network of virtual tunnels also known as “onion routing” aimed at improving privacy and security on the Internet. By randomizing your traffic through a network of encrypted tunnels, it becomes close to impossible to analyze traffic between two parties.
There are various ways you can leverage Tor. One method I recommend is Tails. Tails is a live CD or USB operating system preconfigured to use Tor as well as hardened against common methods to probe systems. Below are the steps to download and run Tails. Basically, you can take a Tails CD anywhere and boot up a secure system from any standard computer. An example use case would be a journalist speaking with a whistle blower online without giving away who they were speaking with or what was covered during the conversation. Once the sensitive conversation is concluded, both parties could shut down the Tails CD and power up their normal computers. If you got sensitive things to talk about online, you may want to have a Tails CD in you desk to fire up.
Using Tails
Tails download page
Booting Tails
Tails can be downloaded as an ISO image from https://tails.boum.org/. The website includes a cryptographic signature for those that are paranoid of counterfeit versions. The Tails ISO can be burned to a DVD or installed on either a USB drive or SD card. Best practice is using a method that can’t be altered meaning read only DVD or USB drive to avoid having the Tails operating system tampered with by unwanted parties. Once installed, you can also create copies of Tails. This is the easiest method to get Tails onto a USB drive meaning start with a DVD and create USB versions from that running system.
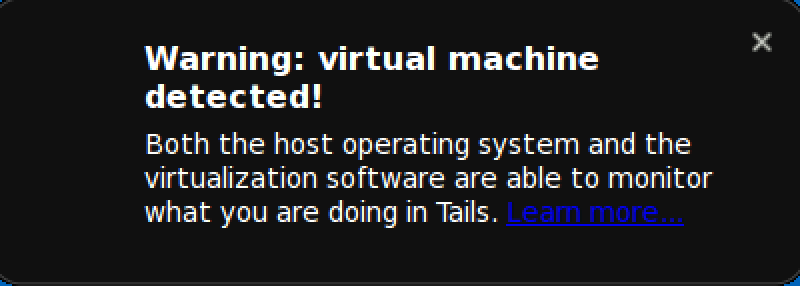
Tails comes preinstalled with several applications pre-configured with security in mind (web browser, IM client, email, etc). Below are a few screenshots of using Tails with VMware (not recommended as a secure use case). I was surprised to not only find tails resisted various forms of probing, but it also would auto reboot if I attempted to power down and later retrieve a previous session. The default settings are designed to circumvent censorship, keep your identity private and not leave a trace of the session unless you explicitly choose to do so. For more info, check out Tails as well as the other Tor related projects. God bless those guys for their contributions to Internet privacy.
Tails environment
Tails warning when used with VMware