I speak often about how phishing campaigns are built around current themes. COVID continues to be a current theme and there are many phishing campaigns take advantage of the confusion associated with shots and other COVID related data. Inky.com posted an example of one of these attacks. Inky’s post can be found below. The original post can be found HERE.
Phishers are always shifting their tactics, adapting to the changing environment like chameleons in the forest. They have been surfing people’s anxieties over the evolving coronavirus news for more than a year now, moving from one phase to the next with their campaigns.
In early summer, INKY data analysts began seeing phishing campaigns that aimed to take advantage of people’s uncertainty about returning to the office. In June, things were looking positive. By August, the Delta variant cast its pall over everyone’s hopes for going back to normal. First, vaccinated workers felt nearly invulnerable. Then, breakthrough cases started making the news. This confusion was a perfect environment for black hats to introduce a new form of phish.
In one of the most recent phishing campaigns to hit INKY customers, bad actors sent emails that spoofed recipients’ human resources (HR) department, requiring them to submit fake Covid-19 vaccination forms.
Quick Takes: Attack Flow Overview
Type: Phishing
Vector: Hijacked email accounts
Payload: Malicious links to credential-harvesting sites
Techniques: Account Takeover, Internal Spoofing, Brand Impersonation
Platform: Microsoft 365
Target: Microsoft Outlook user
The Attack
Several INKY users received emails like the one below that supposedly originated in their own HR departments. While the pitches appeared to be local, in fact, they all originated from various legitimate — but hijacked — external accounts. This legitimacy enabled them to pass standard email authentication (i.e., SPF, DKIM, and DMARC).
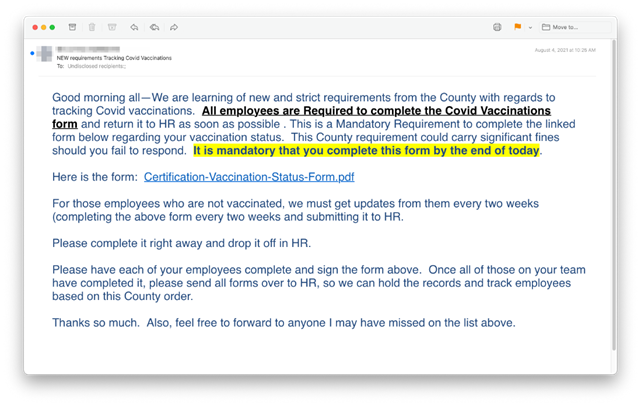
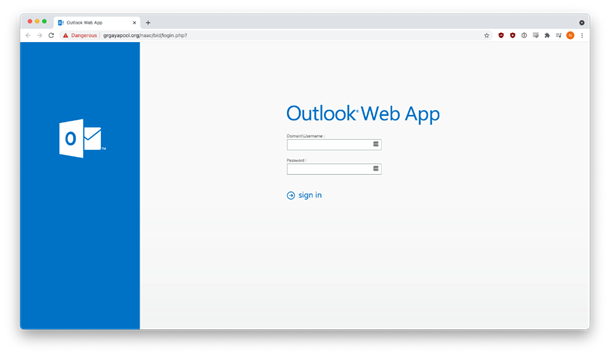
Clicking on the blue anchor text (“Certification-Vaccination-Status-Form.pdf”) took the recipient to a hijacked site that impersonated a good-looking Microsoft Outlook web app login page. In reality, it was hosting a credential-harvesting operation. If the victim logged in, their username and password were stolen.
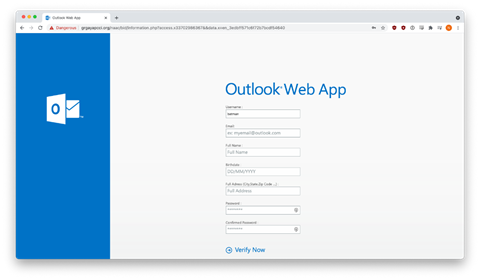
To add insult to injury, victims who entered their credentials were presented with another credential-harvesting form that asked for their full name, birth date, and mailing address.
And why not? Fool them once, and maybe you can fool them twice.
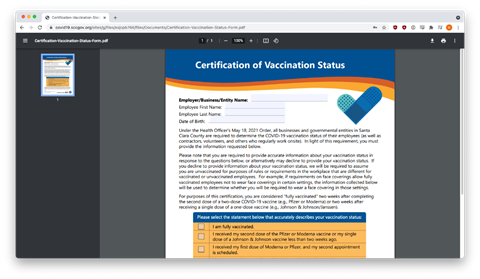
After sensitive data was harvested, phishers attempted to remain undetected by redirecting their victims to a real Covid-19 vaccination form on the website of the Santa Clara County government in California. With this final ruse, the baffled victim might not realize what they had just lost.
Techniques
This campaign was able to bypass existing email security in a number of ways. It sent the lures from legitimate but hijacked email accounts to evade standard security checks. If the recipient clicked through, they were taken to a hijacked web page that impersonated a trusted brand. Because the phishers used a hijacked site, their exploit had not yet appeared on any threat intelligence feed. The sally was effectively a zero-day attack. Now that it’s been discovered and reported, any email security products that reference such feeds can find it, but it’s a little late for the first victims targeted by the campaign.
Recap of Techniques:
- The exploitation of current events — capitalizes on the uncertainty, fear, and urgency related to Covid-19 vaccinations and plans to return to the office
- Brand impersonation — uses elements of a well-known brand to make an email look as if it came from that company
- Credential harvesting — occurs when a victim thinks they are logging in to one of their resource sites but is actually entering credentials into a dialogue box owned by the attackers
- Compromised email accounts — are used by phishers to pass most security software tests, allowing phishing emails to slip past corporate defences and into hapless recipients’ inboxes
Best Practices: Guidance and Recommendations
Recipients who are aware of these types of attacks may note that this email and sender deviate from their normal HR communications. The style may be different. The call-to-action is likely unusual. They should be suspicious that the vaccination form was not attached to the email. An employee shouldn’t have to log in to view a PDF.
If the recipient examined the URL of the phishing site, they might note that it is not a Microsoft domain.
The credential-harvesting form requests information (I.e., date of birth, mailing address) that HR already has. This request is at least highly unusual. A recipient should call the HR department directly to ascertain the request.
If the IT/infosec department doesn’t already have anti-phishing software layered on top of traditional security measures, managers should strongly consider acquiring a robust solution.
Look for the next edition of INKY’s Fresh Phish blog coming soon.
Fresh Phish examples were discovered and analyzed initially by Bukar Alibe, Data Analyst, INKY


