Nice post by Aamir Lakahni aka Dr. Chaos. The original post can be found HERE
The U.S. Department of Homeland Security awarded their continuous monitoring and diagnostics contract. The vendors will provide the tools, hardware, software, and professional services to implement solutions and provide continuous-monitoring-as-a-service.
The awardees listed include:
- Booz Allen Hamilton
- CGI
- CSC
- DMI
- DRC
- General Dynamics-IT
- HP
- IBM
- KCG
- Kratos
- Lockheed Martin
- ManTech
- MicroTech
- Northrop Grumman
- SAIC
- SRA
- Technica
Each awardee proposed several tools and partnered with OEMs they would be pitching to DHS. The majority of the tools are around access control and endpoint security (achieved thru various McAfee solutions) and 802.1x and NAC security (achieved thru Forescout). There are a few other complimentary tools such as mobile device management, logging, help desk, and configuration management tools as well.
According to Federal News Radio, “Under the contract, DHS will work with agencies to implement continuous diagnostics and mitigation (CDM) tools at the network level using more than $183 million, which Congress provided as part of the fiscal 2013 budget.”
Federal News Radio continued to state:
Agencies will use their own funding to implement the software and services for specific applications or systems, said John Streufert, director of Federal Network Resilience at DHS.
“The way the government has structured its information systems is we share networks with multiple custom applications,” he said during a press briefing after speaking at the SANS Institute’s Critical Security Controls Summit in Washington Tuesday. “We track more than 6,000 applications which are categorized at a moderate level of risk, and more than 1,200 applications that are categorized at a high level for risk. Because they all share common networks across both military and civilian government, it was the judgment of DHS that protecting the networks first would be an important foundation and then we would overlay additional software security protections, database protections and website protections on top, and feed to the same dashboards that will be funded in the initial increment under the continuous diagnostics and mitigation program.”
One of the biggest problems I have with this approach is that it seems that DHS has essentially locked in civilian agencies to specific products and vendors, rather than taking a holistic security approach. Continuous monitoring is a concept, but in many ways it is abstract, similar to cloud computing, it is abstract and some definition needs to be added to it.
The security industry has struggled with how to accurately represent security threat information consistently and make it relevant and meaningful. Anyone who has managed a security or logging solution understands they provide big picture graphics on the health of a network, but reveal nothing in terms of data breaches and data loss.
According to Andrew Benhase from Cisco Systems, in his article What is Continuous Monitoring,“security event information has traditionally taken the form of ASCII log data aggregate into a centralized database where a process often takes a considerable amount of time to create static views of very stale, albeit correlated threat data.”
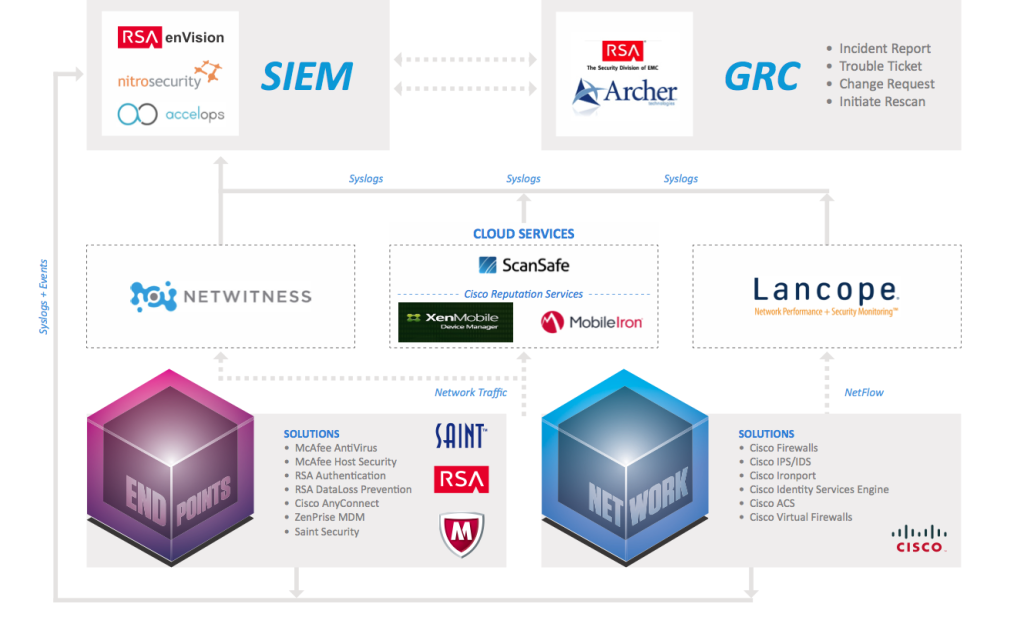
I believe that is why big data and security analytics is going to important. I would have preferred that DHS built a framework of reference architecture that could be achieved using any product instead of a set of particular OEMs. Agencies could still use their prefer vendor of choice in the reference architecture without compromising the integrity of the solution.
DrChaos.com Continuous Monitoring Reference Architecture
(originally developed by Joseph Muniz and Dan Catalano)
We still have some work before terms like continuous monitoring and big data security analytics become more than buzzwords, but one thing that is obvious protecting data on the edge is an outdated solution. Most organizations have no idea how accurately determine if an active breach has occurred inside their organization, and simply putting in point products and calling them a continuous monitoring solution won’t solve that problem.