Bleepingcomputer.com wrote an article on a new ransomware variant being called CryptON that targeted Remote Desktop Services. The original post can be found HERE.
A new and active campaign for the CryptON Ransomware is currently underway where attackers are hacking into computers with Internet accessible Remote Desktop Services. Once the attackers gain access to the computer they manually execute the ransomware and encrypt your files.
This new campaign was first discovered by Malwarebytes security researcher S!Ri who posted about it on Twitter.
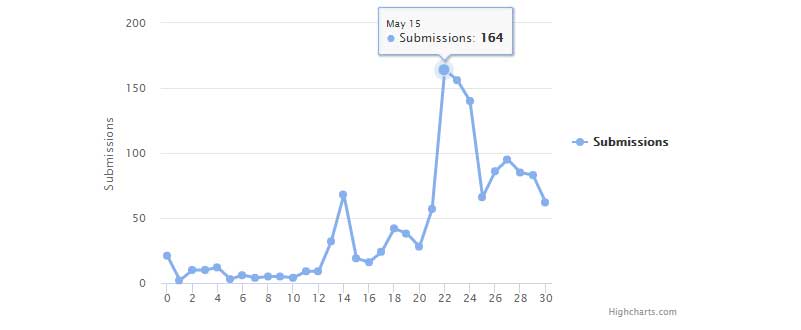
In addition to seeing larger than normal CryptON support requests in our forums, ID-Ransomware also shows a huge uptick in reported infections on their site for May.
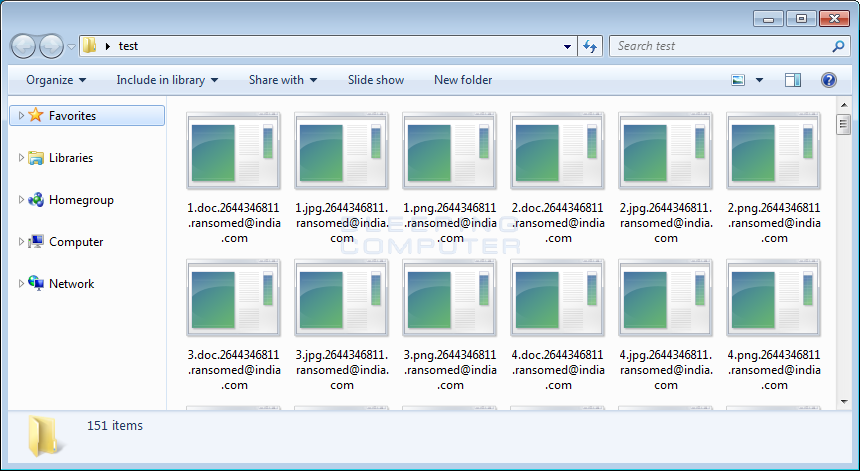
 When installed, CryptON will encrypt a victim’s files and append the [email protected] extension to the encrypted file’s name. This means that a file named 1.jpg would be encrypted and renamed to [email protected] as shown below.
When installed, CryptON will encrypt a victim’s files and append the [email protected] extension to the encrypted file’s name. This means that a file named 1.jpg would be encrypted and renamed to [email protected] as shown below.
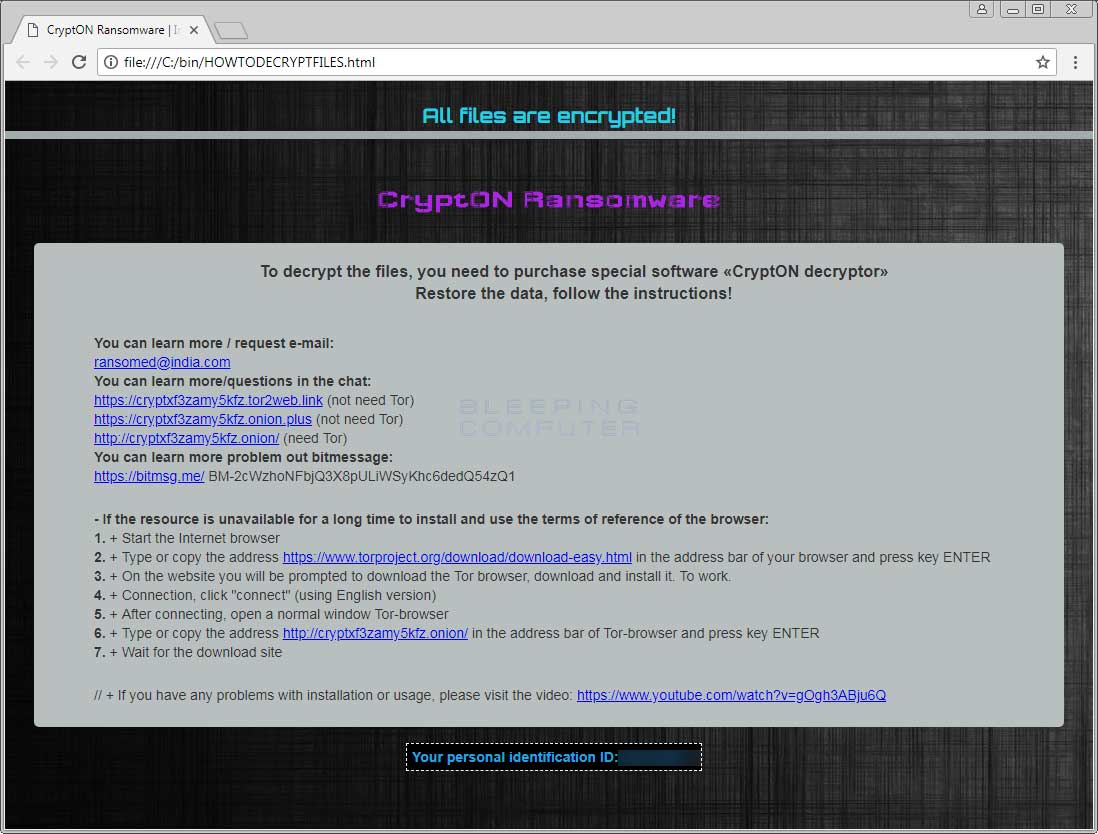
In each folder that files are encrypted, a ransom note named HOWTODECRYPTFILES.html will also be created that contains instructions on what has happened and how to connect to a TOR support site to receive instructions.
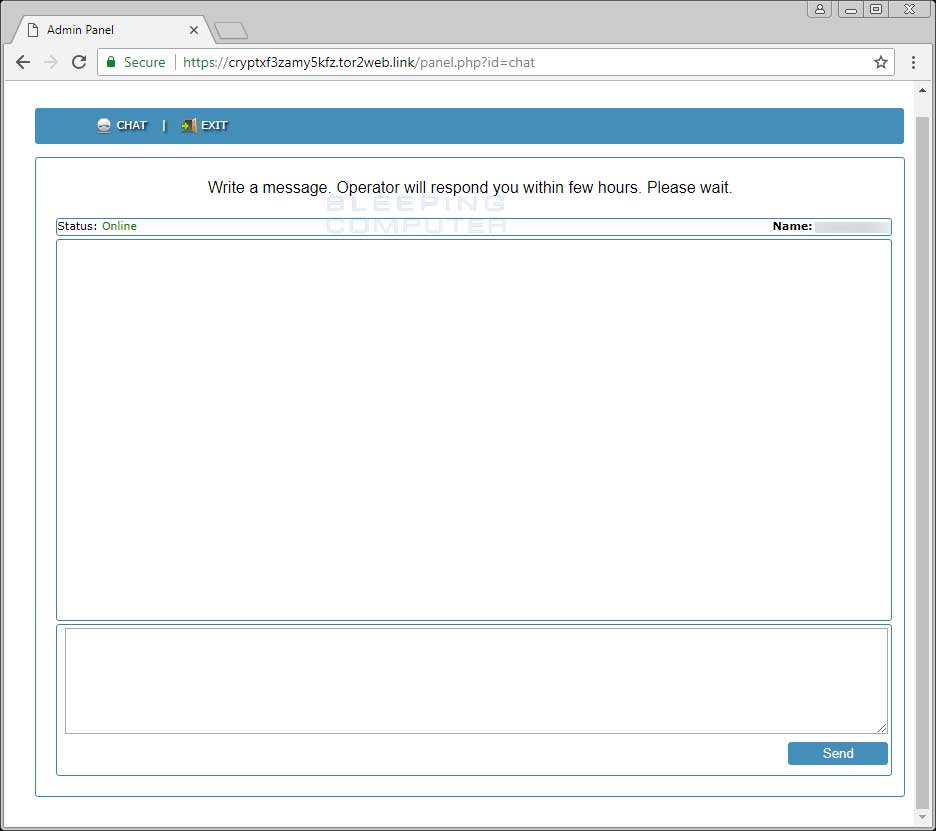
The CryptON support site is nothing fancy. It just has a chat form that you can use to communicate with the attackers in order to receive payment instructions.
It is not possible to decrypt the CryptON Ransomware Variant
Unfortunately, at this time there is no way to decrypt files encrypted by the CryptON Ransomware variant for free. Emsisoft does have a decryptor for older variants, but it does not work with the current version and it is unknown if a solution will be found.
The only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though CryptON does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.
For those who wish to discuss this ransomware or need support, you can use our dedicated CryptON Ransomware Support & Help Topic.
How to protect yourself from the CryptON Ransomware
In order to protect yourself from CryptON, or from any ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
As the CryptON Ransomware is commonly installed via hacked Remote Desktop services, it is very important to make sure its locked down correctly. This includes making sure that no computers running remote desktop services are connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
It is also important to setup proper account lockout policies so that it makes it difficult for accounts to be brute forced over Remote Desktop Services.
You should also have security software that incorporates behavioral detections to combat ransomware and not just signature detections or heuristics. For example, Emsisoft Anti-Malware and Malwarebytes Anti-Malware both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
Last, but not least, make sure you practice the following good online security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed.
- Use hard passwords and never reuse the same password at multiple sites.
- If you are using Remote Desktop Services, do not connect it directly to the Internet. Instead make it accessibly only via a VPN.
For a complete guide on ransomware protection, you visit our How to Protect and Harden a Computer against Ransomware article.
IOCs
Hashes:
8D47C2AC3987FC7BD18303E7376BB05E
7C3DC9AD79B800F0A31BA3BDAC79F7E4
Associated Files:
HOWTODECRYPTFILES.htmlCryptON Associated Emails:
[email protected]CryptON HOWTODECRYPTFILES.html Ransom Note:
All files are encrypted!
CryptON Ransomware
To decrypt the files, you need to purchase special software «CryptON decryptor»
Restore the data, follow the instructions!
You can learn more / request e-mail:
[email protected]
You can learn more/questions in the chat:
https://cryptxf3zamy5kfz.tor2web.link (not need Tor)
https://cryptxf3zamy5kfz.onion.plus (not need Tor)
http://cryptxf3zamy5kfz.onion/ (need Tor)
You can learn more problem out bitmessage:
https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1
- If the resource is unavailable for a long time to install and use the terms of reference of the browser:
1. + Start the Internet browser
2. + Type or copy the address https://www.torproject.org/download/download-easy.html in the address bar of your browser and press key ENTER
3. + On the website you will be prompted to download the Tor browser, download and install it. To work.
4. + Connection, click "connect" (using English version)
5. + After connecting, open a normal window Tor-browser
6. + Type or copy the address http://cryptxf3zamy5kfz.onion/ in the address bar of Tor-browser and press key ENTER
7. + Wait for the download site
// + If you have any problems with installation or usage, please visit the video: https://www.youtube.com/watch?v=gOgh3ABju6Q
Your personal identification ID: