Everything is going on line. Regardless if you want it to or not … it’s happening. If you look back 20 – 25 years ago, people had fax machines and every home had a landline. Today, most offices use e-mail verse faxing and many homes only have a landline for alarm systems or because it comes with a internet and TV bundled plan. 15 -20 years from now, it will be weird to physically turn on lights, your TV or anything else that is not online today. It’s happening …. the Alexa concept will be everywhere. This also means there will not be 20 thousand individual products and apps. It will be one larger system that you interact with. In the morning, you will say “Lights …. and make me Coffee”.
With this great value comes huge security risks (Spiderman would say “with great power comes great responsibility”). IoT has become one of the top targets for attacks due to many reasons. The industry is claiming as high as fifty percent of company compromises are being caused by vulnerabilities in IoT. Here is a breakdown of some of the top ones.
- You can’t install firewalls, IPS or other security products on most IoT devices
- The available security capabilities are typically limited
- Many IoT developers are small companies that focus on features vs security
- Many vulnerabilities take much longer to be disclosed and patched by the IoT vender vs other technologies
- IoT products typically leverage an application, which can have its own security vulnerabilities.
- Many IoT developers are not trained in secure programming lifecycle concepts.
So how can you compromise a IoT device IE how do you do IoT penetration testing? There are many methods. First, you can try pulling the micro drive IE mini hard drive if one exists. Some devices also have micro USB drives essentially letting you turn the device into an external hard drive. You can use any dump tool found in Kali Linux to essentially investigate what’s installed. I have a digital forensics book coming out in a month that covers many tools in Kali Linux you can use to recover data off any type of hard drive. Foremost is an example of one really cool data recovery tool.
Another tactic is looking at the firmware. Most IoT devices have their firmware posted on websites or it’s something you can ask the manufacture for. You can modify the firmware and the device won’t validate if its authentic. Most of the time, the IoT device only checks the size of the file and format. Sometimes you may need to gain root to the system and identify this but if you can get the firmware, you can modify and own the device.
You can also look at the radio or Bluetooth signal coming from the device. There are tools like the HackRF that can easily modify and replay signals. You may also attack the application with the goal of owning the device without having to connect to the actual device. Application security is a whole other topic to be concern about and can lead to having your IoT devices being owned.
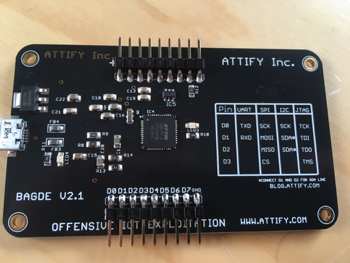
 One awesome method to abuse IoT is hardware hacking. There are testing protocols like JTAG that you can tap directly into and gain root to a IoT device. In summary, chipboard manufactures need a standard to test hardware. So what they sometimes do is place connections on the chipboard used for testing purposes. Attackers can connect to those and immediatly obtain a root shell to the system!. Attify makes a small tool that you can use to tap into an existing JTAG connection if one exists on the target device. Senrio posted a really good blog post on abusing JTAG HERE.
One awesome method to abuse IoT is hardware hacking. There are testing protocols like JTAG that you can tap directly into and gain root to a IoT device. In summary, chipboard manufactures need a standard to test hardware. So what they sometimes do is place connections on the chipboard used for testing purposes. Attackers can connect to those and immediatly obtain a root shell to the system!. Attify makes a small tool that you can use to tap into an existing JTAG connection if one exists on the target device. Senrio posted a really good blog post on abusing JTAG HERE.
 If you are responsible for defending a network from cyber threats, you should consider testing your IoT network for vulnerabilities and validating those vulnerabilities with a penetration test. You should also isolate any IoT device to a separate network to avoid the risk of those devices becoming pivot points for attackers to the rest of your network. Lastly, you should have breach detection monitoring how those IoT devices behavior including some type of network baseline so you can quickly identify if a HVAC tool starts performing network reconnaissance as an example. You can’t depend on IoT devices to be sure. You need to secure around them!
If you are responsible for defending a network from cyber threats, you should consider testing your IoT network for vulnerabilities and validating those vulnerabilities with a penetration test. You should also isolate any IoT device to a separate network to avoid the risk of those devices becoming pivot points for attackers to the rest of your network. Lastly, you should have breach detection monitoring how those IoT devices behavior including some type of network baseline so you can quickly identify if a HVAC tool starts performing network reconnaissance as an example. You can’t depend on IoT devices to be sure. You need to secure around them!
In summary … adapt or die. If you don’t think about securing IoT, it will be how you get owned.