Nicole Perlroth wrote a interesting post on the NewYorkTimes blog about a new type of Ransomware and Cisco’s view as it spreads in the wild. The original post can be found HERE.
It has been mere days since federal agents seized control of computer networks used by hackers to infect victims with CryptoLocker, a piece of malware known as “ransomware,” which encrypts the contents of computing devices so hackers can demand a ransom to decrypt it. More on Ransomware such as CryptoLocker can be found HERE.
Now security researchers are seeing an influx of another form of ransomware, called Cryptowall.
In April, criminals began advertising RIG, a so-called exploit kit, which automates the exploitation of software vulnerabilities. For $60 a day or $300 a week, criminals could use it to infect victims’ machines with 8 to 12 percent success rates, according to advertisements. Almost immediately, security researchers began noticing the kits being used across the Internet, in many cases to distribute Cryptowall.
Security researchers at Cisco said the exploit kit has been gaining steam this month. Since Cisco began blocking the attacks on April 24, its researchers said they had blocked requests to over 90 infected web domains for more than 17 percent of its cloud-security customer base.
In many cases, criminals were infecting victims by distributing malicious advertising — known as “malvertising” — on legitimate, popular websites, then using the exploit kit to burrow into customers’ machines and encrypt their contents with Cryptowall.
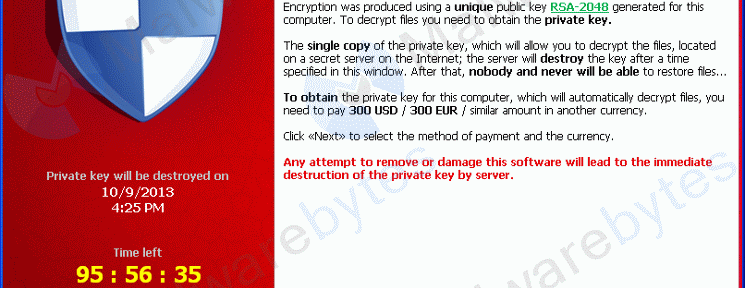
In several cases, victims would find a message informing them that their data had been encrypted by criminals and would remain unreadable until they paid a $200 fee.
“If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist,” was one message. When victims do not pay the specified ransom by the deadline, they may receive a second message — as Cisco’s researchers did — tripling the ransom demand to $600.
The largest share of infections, some 42 percent, are in the United States, followed by England and Australia, according to Cisco.
Ransomware dates to 2009 in Eastern Europe. Earlier this week, the Justice Department estimated that criminals had infected as many as one million computers and cost people more than $100 million in direct and indirect losses.
Cisco researchers said the best defense was to be cautious about clicking on malicious sites, back up the contents of your devices and regularly run software updates to ward off attacks like RIG.