Mobile device security is a hot topic for 2012 and some current industry leaders are Mobile Iron, Airwatch, Good Technologies and Zenprise. There are two approaches to addressing mobile device security, which are a “sandbox” or “application management” approach (more info can be found HERE). My team found the majority of our customers prefer the application management approach offered by Mobile Iron and Airwatch. For those interested in evaluating Mobile Iron, below are some steps to setup a basic lab for testing functions such as remote wipe, policy enforcement, flagging jailbroken devices and other features.
Mobile Iron has two parts to their solution. There is a Mobile Iron VSP (management system) and Sentry (policy enforcement) server that can be a physical appliance or virtual server. The Sentry piece isn’t required but used 95% of the time since it enforces policies built by the VSP. A basic Mobile Iron lab will need ESX4.0 or greater, around 4GB of memory and 40GB of disk space. You can download a Mobile Iron ISO from https://info.mobileiron.com/free-smart-start-trial.html. Mobile Iron will need some ports opened for communicating to devices and data synchronization. Plan to open outside ports 8080 or 8443, 9997, 9998, 443, 2195 / 2196 and inside ports 25, 389 / 636, 9090, 443, 22 and 8443 depending on what services you will be testing. Ports can be changed on the main dashboard if needed.
After booting the Mobile Iron VSP for the first time, you will be prompted to enter basic network information (subnet, gateway, etc.). Fill out the requested information and wait for the VSP to boot up. Access your Mobile Iron system via the domain name you provided plus /admin (IE. mydomain/admin) and you will see a login. Login with the username and password specified during the initial build and you will see the following dashboard.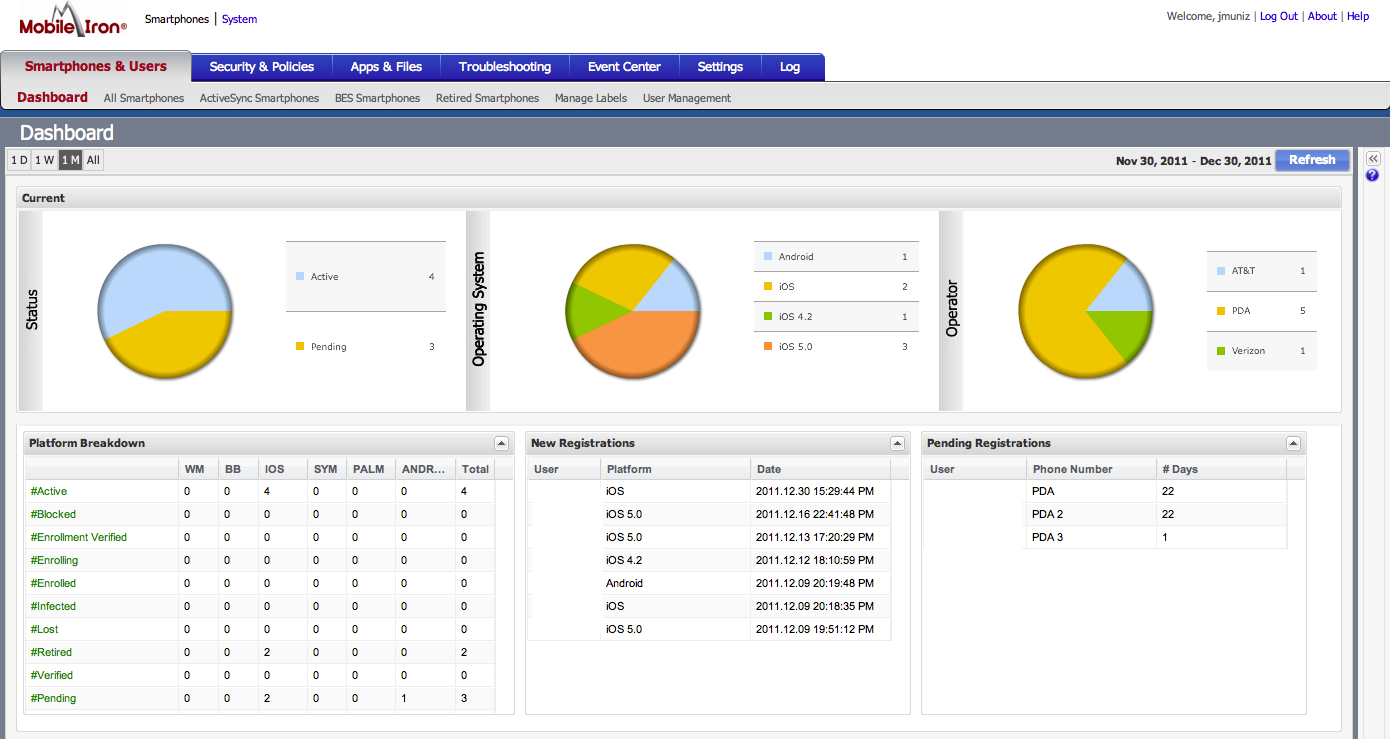
You can add local users by clicking “Smartphone and users” or a LDAP (under LDAP) for user database integration. At the very top, there is a system link to configure management settings. Make sure to configure SMTP under email settings so you can test alerting. Verify and update basic network info that configured during the initial setup. You can also check for software updates under the maintenance tab.
For those testing Apple products, Mobile Iron recently added an enhanced certificate option that doesn’t require a Apple development license to generate a cert (we learned this the hard way and paid the $299 weeks before the update). For users looking to test custom built applications, a developer license is required however labs testing basic functions such as managing existing apps via the app store, mobile security, etc. won’t need this. Create a certificate and upload it under Smartphones, Settings and Local Certificate Authorities. To read more on generating IOS certificates, go HERE.
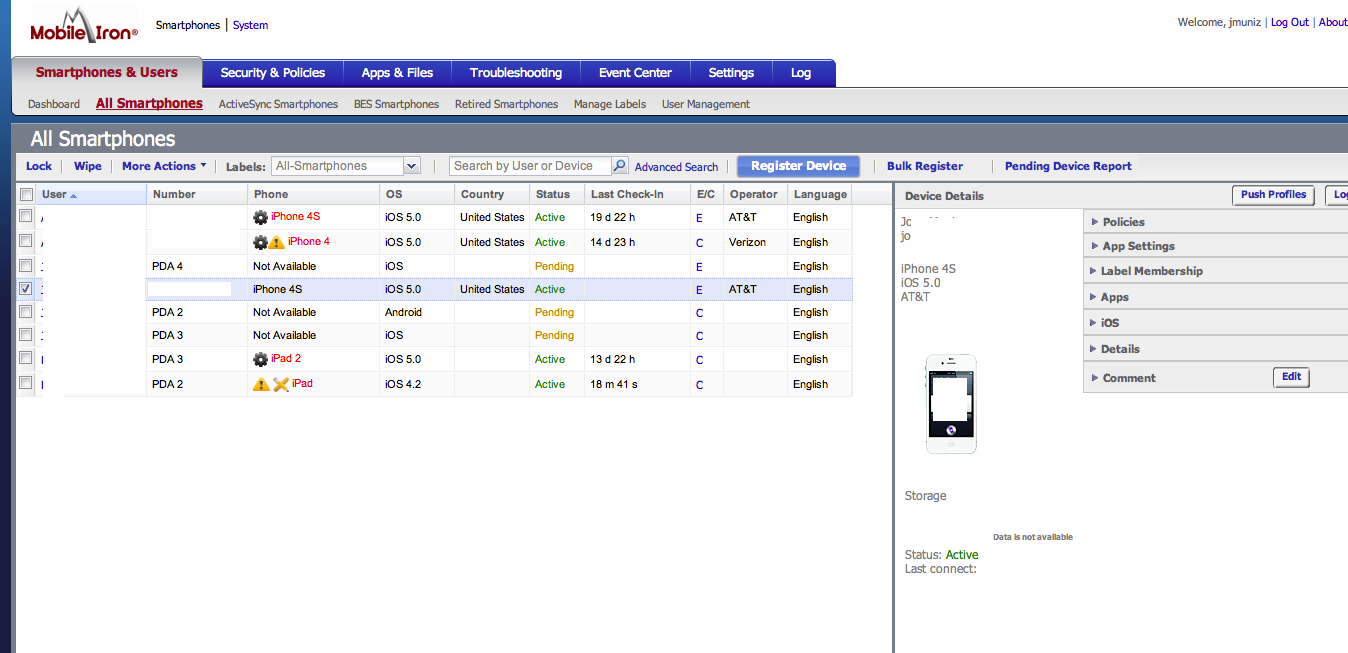
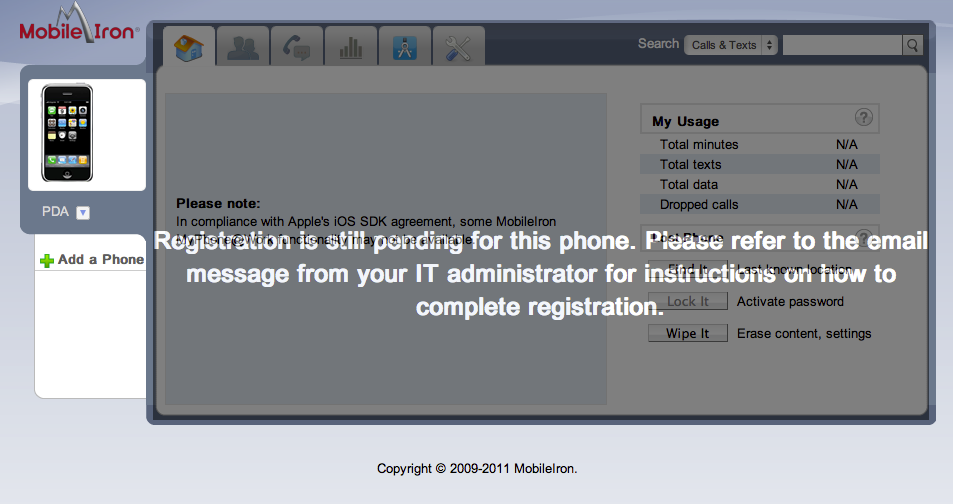
At this point, you have a working Mobile Iron VSP and can register a test device a few different ways. One way is to click the Register button in the VSP and fill in the request page. An email will be send to the user you created explaining how to download the Mobile Iron application, server name, user name and password. A second way is to go the user GUI, which is your domain without /admin at the end. Users can log in and register their devices based on accounts created in the Mobile Iron VSP. A third way is having users find the Mobie Iron app using their mobile devices and filling out the server information that is sent via email requests from the VSP. Below are some pictures me registering devices
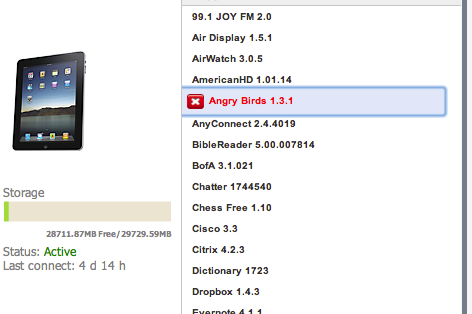
Labels are used to group device types and policies together. The default labels and new ones can be built under Smartphones & Users, Managed Labels. Policies are checks that can be performed on devices part of Labels. Policies can be found at Security & Policies, All Polices. Compliance Actions are what can be done if a Policy is violated (IE blocking or sending a alert if somebody violates the policy “Downloading Angry Birds”. Test out building a label and apply some policies to that label. Create a few Compliance Actions for each policy such as sending out alerts. Place some users under your test label and register a device. Below is a screenshot of testing a policy against Angry Birds on IOS devices.
This is a very brief crash course on Mobile Iron. Check out http://www.mobileiron.com/ for more information on their solution. I’ll probably do a simliar post for those looking to test AirWatch in the near future. Happy New Year!


Excellent article..Thanks for sharing!
MobileIron is the worst MDM solution i tested and saw in the market today.
Unsecure in DMZ deployment, wich is not flexible, internal DMZ firewall is made a swiss cheese with al the ports that need to be open. and even get more swiss cheesed when you add monitoring, backup, notifications and more mngttask. VSP intercepts EAS traffic , never intercept EAS traffic from the EMAIL flow only with a mail relay or antivirus/intrusion if necessary. CAS/EDGE is leading, if you want to manage the authorization let CAS/EDGE handle it by for example powershell commands. Also HA functionality is very poor with Mobileiron so when VSP gets in front of CAS/EDGE you make you email infrastructure weak and unreliable. I can go on and on, but i think my point is made. Look for much better solutions, like Citrix Xenmobile, BlackBerry Enterprise Service 10 or VMWare Airwatch. Leaf Mobileiron out of scope.
??
EAS proxy is a viable option