For those following Cisco security, you probably know Cisco acquired Sourcefire last year (more found HERE). The most anticipated release has been adding Sourcefire’s flagship Firepower offering inside Cisco’s most popular firewall offering the Adaptive Security Appliance (ASA). As of September 16th, this offering is officially available. You can find data sheets, configuration guides and more on the new release HERE. This post will cover steps I used to build my ASA with Soucefire lab.
You will need a version of the 2nd generation ASA with a SSD drive (NOTE: Sourcefire is not available in 1st generation ASAs). See HERE for the model numbers. NOTE The ASA 5505 is a first gen ASA but there are new models coming out shortly for small business). There are versions of Sourcefire that don’t require an ASA such as a dedicated appliance and virtual Sourcefire appliance however this post will cover running sourcefire within a ASAX or in this case, a ASA5515X. You will also need a management appliance to manage the firepower services. My lab uses a virtualized version of this called FireSIGHT ran via ESXI 5.1. Your ASA must be running at least 9.2 or later as specified on the release page.
NOTE: You can only run one additional feature package on the ASA. Options today are an older dedicated IPS, ASA CX or Sourcefire. If you have one version already installed, you will have to stop that service and uninstall before moving forward. For example, if you have the dedicated IPS installed on the ASA, you would have to issue the following commands to kill it
hostname# sw-module module ips shutdown
hostname# sw-module module ips uninstall
hostname# reload
Many of the initial steps are similar to how ASA CX is installed on an ASA (see my post HERE). The first step is getting the software image. Download the boot image from Cisco. I suggest using ASDM and installing it under file management like explained in my ASA CX post found HERE. An example boot image file is asasfr-5500x-boot-5.3.1-58.img. Next you will need to get the Firepower system software from cisco.com and FTP that to the ASA once the image is running. Again, the steps are similar to the ASA CX post aka I suggest using dropbox to host it. In summary, you set the boot image using
hostname# sw-module module sfr recover configure image disk0:file_path
hostname# sw-module module sfr recover configure image
disk0:asasfr-5500x-boot-5.3.1-58.img
Load the image using
hostname# sw-module module sfr recover boot
Session to the image to get the Sourcefire command line (login in with user admin and password Admin123)
hostname# session sfr console
Type setup and configure the basic settings.
Install the system package using
system install http://asasfr-sys-5.3.1-44.pkg (I suggest using dropbox instead of this example. So your link would be a dropbox share link. Make sure to put the file in your public folder or it won’t be able to be seen by the ASA. Also make sure to delete it off dropbox after you are done!)
Session to the Sourcefire within ASA console using session sfr in the ASA command line (similar to ASA CX). Login with user admin and password Sourcefire. Complete the system configuration.
Specify the FireSIGHT management IP address (installation process below) using the following command. Note you need the IP address and make up any key. It can by whatever you want such as happy123 or for my example, thesecurityblogger. You will need this later when you add this to the FireSIGHT management.
configure manager add 10.89.133.202 thesecurityblogger (NOTE the ip is 10.89.133.202 and made up key is thesecurityblogger in this example)
At this point, all future steps are done within the FireSIGHT management.
Now you need to build the FireSIGHT management. You will need to download Virtual FireSIGHT / Defense center for VMWare, which will be a .tar.gz files. I used 7-zip for my windows VM to uncompressed the file since I need windows to access my ESX system (VMware needs to developed a MAC agent!). Have to unzip the .gz followed by untaring it. You should end up with a .vmdk file. Deploy the .OVF file in ESXI and set basic network configuration. Once complete, you should be able to access your FireSIGHT management GUI using the IP addressed you specified during the basic network setup. Open FireSIGHT in a standard browser and use admin for the user name and Sourcefire for the password. From the GUI, you will be asked to change the password. You can modify the network, time and other basics from the GUI if they weren’t done during the initial setup found under System->Local-> Configuration.
Basic System Setup Options in FireSIGHT
Its recommended to enable rule updates, check for software updates and enable geolocation updates. You do this by going to System-> Updates then select Download Updates. Update will appear and state if they require a reboot. Select the present picture to install. NOTE: A reboot will not reboot the core ASA. Sourcefire has its own processing, CPU, etc and runs inside the ASA similar to a separate virtual machine inside a server. 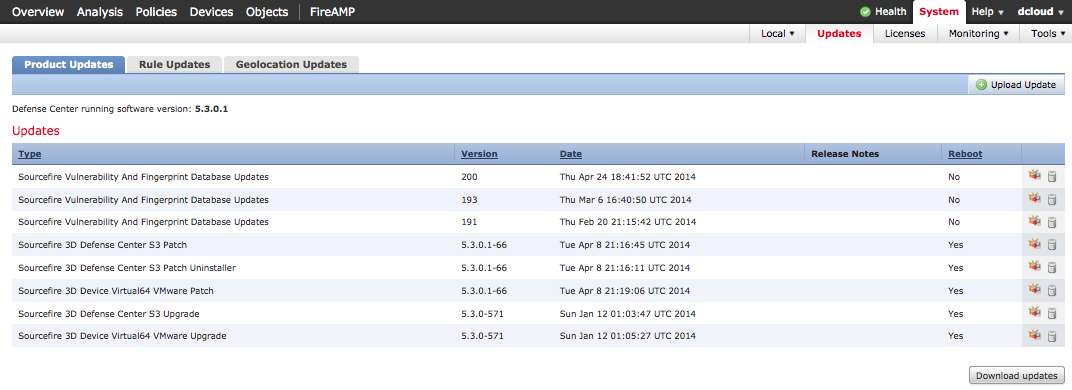
Updating software in FireSIGHT
The ASA with Sourcefire has three license offerings installed under System->Licenses. The default system gives you Application Visibility and Controls (identifying a iPad, windows system running firefox, etc.) however there is a separate URL license. The URL license gives you all categories such as the need to block adult websites, micro apps in Facebook and reputation security meaning blocking bad websites. For example, most attackers wouldn’t launch attacks from their home network. They would attack you from a new / rouge IP address that based on negative reputation would be blocked by this feature (aka pre attack blocking the traffic before it can hit your network). This typically stops 80% or more daily attacks since malicious attacks must come from a established trusted source. The second license option is IPS/IDS for blocking attacks. The last license is enabling Advance Malware Prevention (AMP) used to identify infected files on the network and endpoints (more on this HERE for only endpoint. The ASA with Sourcefire version is network and endpoint if you include the optional agents). Add a license by clicking add feature license, pasting your license key and submitting the license.
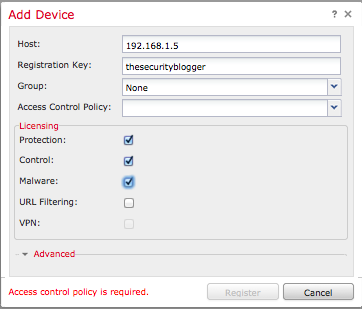
At this point, you should be able to add the Firepower services from the ASA. Go in the management GUI to Devices->Device Management, click the Add button and select Add Device. You will be asked to give the IP address of the Sourcefire IP inside the ASA and the key you made up (example shows thesecurityblogger) for the Registration Key spot. You can check which licenses you want to apply assuming you loaded some in prior to this and click add.
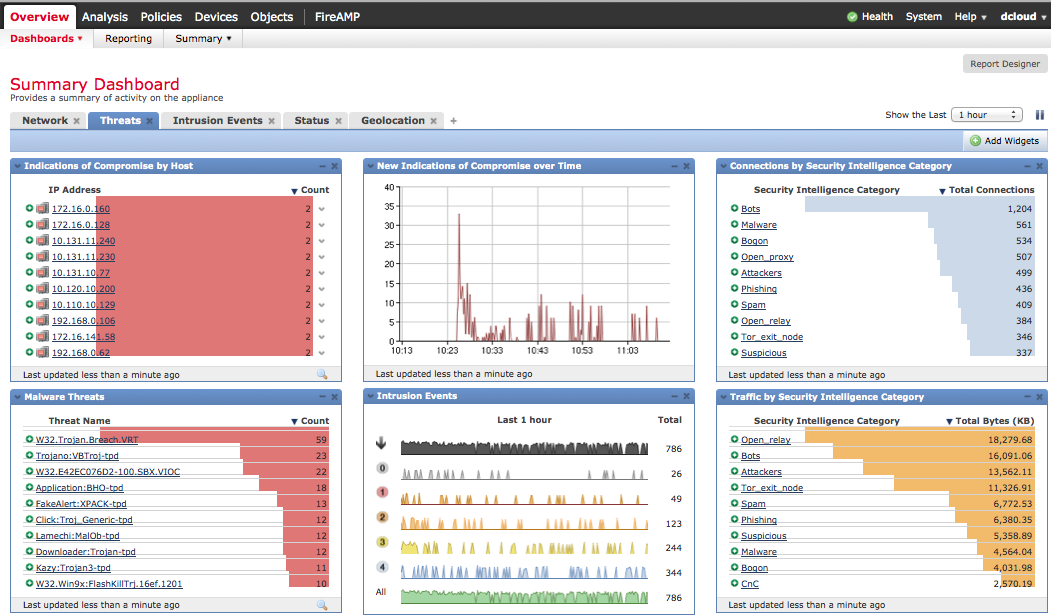
There are other steps to setting up FireSIGHT such as building access control policies, enabling network discovery to see whats on the network and so on (discovery found under Policies-> Network Discovery then adding a rule to specify the entire network). Before doing that, you should go back to your ASA and configure traffic to redirect through the firepower component of the ASA. NOTE: Without redirecting traffic through Sourcefire, the ASA will just act as a firewall meaning traffic will not be seen by the Sourcefire software inside.
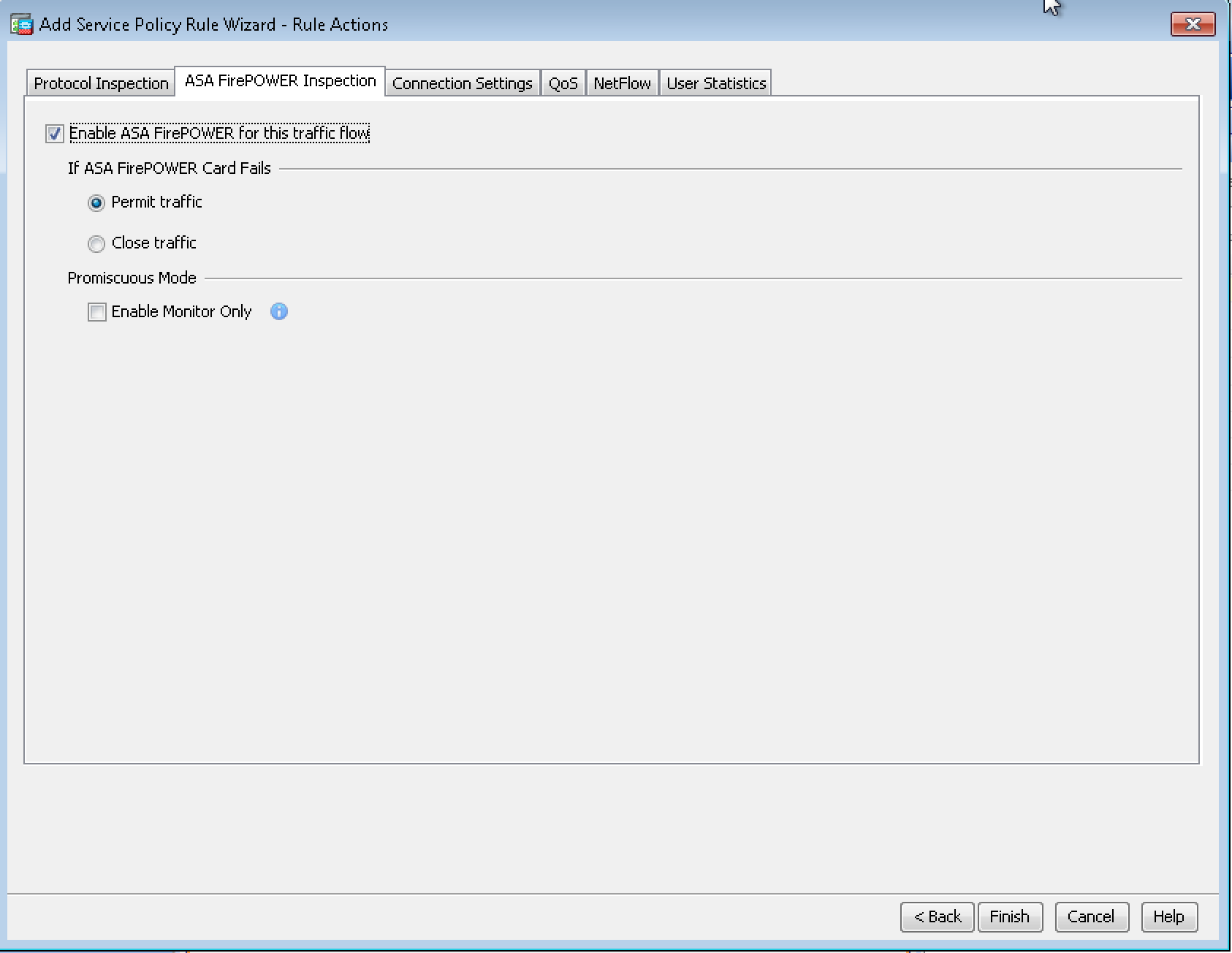
Access ASDM and select Configuration > Firewall > Service Policy Rules. Next select Add > Add Service Policy Rule. Click Next. The Add Service Policy Rule Wizard – Traffic Classification Criteria dialog box appears. Provide the basic info and on the next page select the ASA FirePOWER Inspection tab. Check the Enable ASA FirePOWER for this traffic flow check box. Select if you want to permit traffic if Sourcefire fails. Click finish.
FirePower service inspection policy tab
At this point, you should see basic data in the FireSIGHT management GUI. Check out the FireSIGHT management overview post HERE to get an idea of things to configure. At this point, you have a basic lab. Enjoy
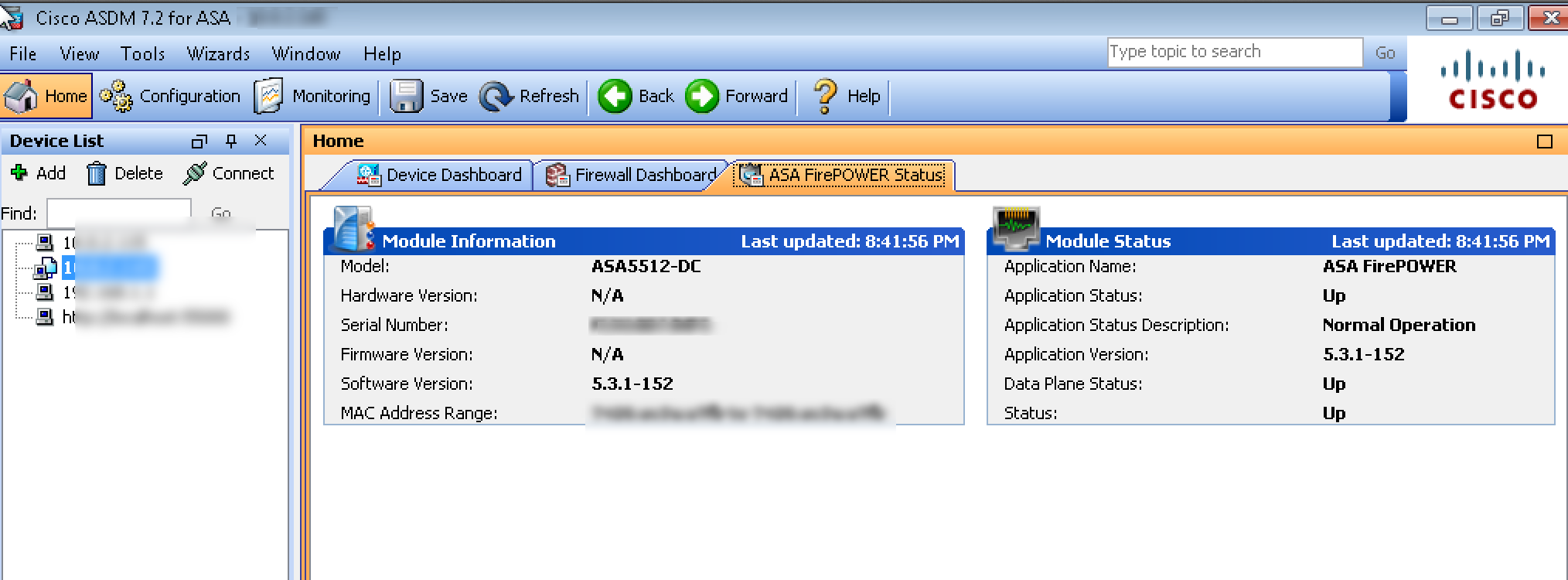
SourceFire tab in ASA ASDM




Very informative. Can you tell me what the maximum throughput is that you are seeing on the ASA 5515x after configuring the sourcefire module?
Hi Michael. The new data sheet found HERE says with IPS and the other features for a 5515x is 250 Mbps. They call it “media-rich” traffic which means real traffic (music, video and data) rather than ping 100 times to fud the numbers. Hope this helps. The next level up (5525X) is 650 Mbps
Great article. Any idea how the logging and log retention works?
For example, the legacy Cisco IPS’ use a bit of syslog, but mainly SDEE. And it needs a logging appliance to grab the SDEE. IME was used for this was as well, but the logging retention wasn’t very flexible
Great article, i ve got a demo of the software Cisco FirePower module up and running on my ASA 5525-X and i am ready to deploy the licenses.
Regarding the troughtput, having experience on ASA CX software module do not redirect every form of traffic into the SFR module(try http/https at first). I faced lots of problems with ASA CX at the beginning of the first release(memory leaks,oversubscription(lots of packets pending on virtual rings,high CPU.
The 650 Mbps throughput is theoritical and under ideal conditions. For example ASA-CX is not capable to achieve throughput up to 200-250 Mbps (with AVC+WSE).
On the other hand FirePower/FireSight is a different product produced by Sourcefire one of the best IDS/IPS vendors worldwide(in my opinion) so i am expecting a much better functionality.
Hi Theodore. I agree that I also experienced some large performance hits with CX. Many of us have tested the Sourcefire stuff and it does run a ton faster going this route. Now keep in mind SSL decryption is off box for the next few months but once that is included with the ASA Sourcefire platform, we still expect better performance. Thanks for the feedback.
This article has detail instruction: http://www.cisco.com/c/en/us/support/docs/security/asa-firepower-services/118644-configure-firepower-00.html
This article provides detail instruction on installation: http://www.cisco.com/c/en/us/support/docs/security/asa-firepower-services/118644-configure-firepower-00.html
What accesses do I need to download the FireSight VM Appliance. I have two difference CCO accounts, one with tons of contracts included and on both accounts it says “Additional Entitlement Required” Do I need the CON-SAU-VMWSW10 just do download the Appliance. I’ve already purchased FS-VMW-10-SW-K9.
Thanks!
If you purchased the lisence file and have the PAK number call Cisco 1-800-553-2447 ask for lisencing and they will take care of you.
Thor bless you, im going out from collague but never worked with cisco firewall not mention fire power module, but your tutorial is just perfect for the knowledge i’ve been getting from the official pdfs, thank you very much.
Hi, are there any evaluation licenses for the FireSIGHT? If so where can I get them? There doesn’t seem to be any out-of-box evaluation license like it was for the CX.
Any here would be great. Thanks!
Hi Michael. You will need to reach out to your Cisco support rep to get keys cut. They will ask for your firesight management key as explained in this post and the model number. It should take them a few minutes to issues demo licenses.
I don’t see the option to enable Sourcefire in ASDM. What version supports this? Also what commands will allow me route traffic to the SFR module through the command line?
The Firepower tab appears in ASDM once you install the firepower software. You don’t have to do anything in ASDM to get that to appear as long as you setup the firepower software correctly.
Guys i used to have Prime security on ASA CX .. does firepower has an on box version like how ASA CX does with prime security or do i have to use the vmware central manager
Please i really need a clear answer for this cause its not clear at all on cisco website
Guys? Its just me running this blog. To answer your question, today (April 17th 2015) you need the external manager known as FireSIGHT for all ASA models running firepower outside of the recent 5506 and 5508 appliances. Those come with a version of ASDM that has some Firepower management features meaning you can get by without the external manager on those but they don’t have the same level of features as having the external manager. It is expected that a later release of ASDM will provide similar functionality for all models of ASA running FP.
Hope this helps
Thx man your blog has been more than helpfull when i first installed ASACX with PRSM and now .. keep up the good work
Hi Guys.
I need help.
System image file is “disk0:/asa932-200-smp-k8.bin”
failover mode / context mode run.
ssd install
Name: “Storage Device 1”, DESCR: “Model Number: Micron_M550_MTFDDAK128MAY”
debug module−boot:
Mod-sfr 61> *** EVENT: Creating the Disk Image…
Mod-sfr 62> *** TIME: 01:11:34 UTC May 6 2015
Mod-sfr 65> *** EVENT: The module is being recovered.
Mod-sfr 69> *** EVENT: Error creating the Disk Image.
How do I fix this error?
Guys? It is just me
So your SSD drive is not be recognized by the ASA? Do you have a open TAC case? Have you tried reseating the drive? Do you have the old IPS software, CX or FirePOWER installed?
Hi.
Im see ssd sh inventory and led hd green.
I don’t understand how to see the working ssd.
TAC case not open 🙁
reseating and reboot has not helped.
I’m not have the old IPS software, CX or FirePOWER installed
sorry for my bad english 🙂
Hmmm. What happens when you attempt to run these commands (assuming you have uploaded ASA sourcefire software). Note you can do this via ASDM via the disk manager. Does it say something about the hard drive not found, another version of software is installed or other error? If you can place it in recovery mode, you should be good to reinstall stuff and get it working.
ciscoasa# sw-module module sfr recover configure image disk0:/asasfr-5500x-boot-5.3.1-152.img
ciscoasa# sw-module module sfr recover boot
hi.
upload files ftp
verify /md5 files – ok
TAC case open. yet the recommendations do not help to correct the error. %)
ciscoasa# sw-module module sfr recover configure image disk0:/asasfr-5500x-boo$
ciscoasa# sw-module module sfr recover boot
There was an error when trying to validate the sfr image but the recovery process will attempt to load the image and continue.
Module sfr will be recovered. This may erase all configuration and all data
on that device and attempt to download/install a new image for it. This may take
several minutes.
Recover module sfr? [confirm]
Recover issued for module sfr.
ciscoasa# Mod-sfr 108> ***
Mod-sfr 109> *** EVENT: Creating the Disk Image…
Mod-sfr 110> *** TIME: 01:18:21 UTC May 8 2015
Mod-sfr 111> ***
Mod-sfr 112> ***
Mod-sfr 113> *** EVENT: The module is being recovered.
Mod-sfr 114> *** TIME: 01:18:21 UTC May 8 2015
Mod-sfr 115> ***
Mod-sfr 116> ***
Mod-sfr 117> *** EVENT: Error creating the Disk Image.
Mod-sfr 118> *** TIME: 01:18:22 UTC May 8 2015
Mod-sfr 119> ***
you may not have enough free space in Flash:
check out this bug:
https://tools.cisco.com/bugsearch/bug/CSCun90707/?referring_site=bugquickviewredir
Howdy, love your blog! Thanks for sharing your experience wit da freaking cisco stuff 🙂
Greetings from Germany,
Dave
Hi ,
How can i do traffic managment , for example if i want to ensure certain bandwidth for certain IP, certain users , is it possible
Thanks
Hi All, i have having problems, i need to install the firepower software back on the asa 5506 but each time i try and use either http or Ftp i get either an error 103 or failed to connect to host, is there any other way to get this software back on ?
this is what i receive
asasfr-boot>system install http://192.168.1.19:1024/62A03/asasfr-sys-5.4.1-2112.pkg
Verifying
[Errno 113] No route to host
Upgrade aborted.
asasfr-boot>
I.o
Hello guys
I cannot change the default password, keeps on kicking me out…ant thoughts…this is in the initial setup stage
session sfr console
First off, note that you first need to install the default Firepower image on the ASA to get into the Firepower CLI. At that point, you need to install the permanent image. If you just have the default system image, it doesn’t save meaning if you reboot it, it will be lost. Are you installing the permanent image at this point and getting kicked out?
BTW this blog is just me
it is the module that came with the asa
if I do a show module it clearly shows the sfr in a up up state….
it is the image that is on the asa , it shows me that the sfr module is up up.
so I type : session sfr console
asa: enter password
me: Sourcefire
asa: change password
me: abcdefg
asa: disconnect from module
i just install the sfr and i was wondering if i can use the fire-sight to assign bandwidth to users..and if yes how can i go about it
Bandwidth Throttling is available in pretty much all Cisco content filtering products except Firepower right now. That’s coming with FirePOWER 6.1 released this spring (march 2016 time frame). There are some work around ways of doing it but for now, the official bandwidth throttle feature we all want is 6.1.
NOTE: The login for all default firepower sessions is admin Admin123. They stopped using the sourcefire password
For newer dropbox accounts, make sure your dl=1 (the default for me is 0, which required a web redirection).
https://www.dropbox.com/s/XXXXXXXXXXXXXX/asasfr-sys-6.0.0-1005.pkg?dl=1
Hello,
I have ASA 5506-X and Virtual Firepower management center (FMC), both 6.0.0. The ASA Firepower is running with Protect license, and it is shown in ASDM.
But FMC shows that the device is unlicensed. This is really confusing. And I can not find any place in FMC to add license for the device.
What should I do to make the ASA5506-X Firepower work with FMC?
Thanks,
P/S: I don’t know why, but posting a comment to your website is incredibly hard. I did everything right, but after pressing Post Comment, it shows “Error: Time limit is exhausted. Please enter CAPTCHA value again. Click the BACK button on your browser, and try again.”
Hi,
I’m going to write a post on how to configure a testing lab with a 5506 running 6.0 over the weekend, which will include licensing. In summary, there is a license page in ASDM once firepower is functioning properly on the 5506. If you are using the FirePOWER manager, log into the manager, click devices to see if your device is already added, click the device via edit. This will bring up the device details. Click the first tab and you should see which licenses are applied. Click edit and you should be able to check the boxes for which ever licenses you want to apply to that device and click apply. That will apply available licenses in your manager to that 5506. Hope this helps
Thanks. But in my case I can not tick any of the boxes.
This is what shown in ASDM http://i65.tinypic.com/25grl9x.png
And this is what in FirePOWER manager http://i64.tinypic.com/otzqzm.png. I couldn’t check any boxes in edit menu 🙁
(I took the screenshot yesterday. I cannot take a screenshot of check boxes now, but I tried yesterday)
This is screenshot with the checkboxes http://i.imgur.com/ZczZoW1.png. They are faded, I cant tick any of them. I tried with both Firepower and management center v5.4 and v6.0. I guess it is a Cisco’s bug?
(Though I cant use ASDM to control the device, I need Firepower management center in order to generate reports and delete old logs)
It looks like you haven’t uploaded any licenses to your firepower manager including the ASA connector license. You will need to do that or you won’t be able to apply licenses. I just posted about doing the same thing using ASDM so if you do have licenses, you could try that approach and see if they upload there. ASDM doesn’t make you apply them meaning you just upload and they stick. My guess is you are missing the controller license for that added ASA. Feel free to share a screenshot of your uploaded licenses to my via jomuniz at cisco dot com. Also check out my blog post on licensing.
how can i update the firepower system? All cisco docs tell me to update from ASDM
. i have the VM firepower system running and with that there is NO FP tab in asdm. as well, there is no way to update the firepower from the VM firepower system
my asa , asdm and firepower are working. but i have no means to move from v5.4 to v 6.01
please let me know how
Hi. What model of ASA do you have running Firepower? If your ASDM doesn’t show the firepower tab like in my blog post here (https://www.thesecurityblogger.com/cisco-asa-5506-unboxing-and-first-look-at-new-asdm-management/) …. then its very likely that you haven’t enabled the Firepower services yet. My suggestion would be to access the command line and try to session into the firepower command line. I suspect you will find you are not able to do this. If you can, then I suggest you run the setup again and make sure everything is functional. Another method to test is using a external firepower manager however my guess is you are only using ASDM for your management. Have you downloaded the firepower 6.0.0 yet? You would have to download then using the GUI to get you to 6.0.1. Hope these tips help
these is what my cisco SE security told me to do.
http://www.cisco.com/c/en/us/td/docs/security/firepower/quick_start/5500X/ftd-55xx-X-qsg.html#pgfId-181902
note that ASDM is not an option to manage the Firepower Threat Defense image. You need to use FMC in order to manage, so make sure you update it to the latest version as well.
Excellent man
Greetings from Nepal , Cheers 🙂