This blog post will cover how to upgrade a virtualized FirePOWER manager from 6.0.0.0 to 6.0.1, ASA5512X running 6.0.0.0 centrally managed to 6.0.1 and 5506X not centrally managed from 6.0.0.0 to 6.0.1. I will also show how to install both the unified and non unified versions of 6.01. Let me explain what that means.
The new 6.0.1 software brings a lot of great features listed HERE in the release notes. There are two flavors of the new 6.0.1 code. One version keeps the ASA and FirePOWER code separate like it has been in the past. The other version unifies these codes meaning one management and no ASDM. The reason there are two versions of 6.0.1 is Cisco is slowly migrating the features from the ASA image to the FirePOWER unified image. Here is a list of the features that made it into the 6.0.1 unified image from the ASA image.
- IPv4 and IPv6 Connection state tracking and TCP normalization
- Access Control
- NAT (Full support)
- Unicast Routing (except EIGRP)
- ALGs (only default configuration)
- Intra chassis Clustering on Firepower 9300
- Stateful Failover (HA)
This means features such as EIGRP, Multicast, Site-to-site VPN, and device clustering are not available in the 6.0.1 unified image however coming with a future unified image. See the release notes for a full list of what is available and not available before determining which version of 6.0.1 is best for your organization. If you need features not available in the unified image, it is best to use the separate image until a future unified image release. Note that new features are available in both version of the 6.0.1 release. Again, see the release notes for details. Lets get to the configuration.
Note: I found out that the unified image is only supported using Smart licensing. If you are using classic licensing in your FirePOWER manager, you must switch over to Smart licensing before you can support the Unified image. This does not apply to the 6.0.1 separate image.
Upgrading FirePOWER Manager from 6.0.0 to 6.0.1
The first step is upgrading the FirePOWER manager to 6.0.0.1. I found my manager was at 6.0.0.0 when logging in and clicking updates. To download 6.0.0.1, simply click DOWNLOAD under the updates section to download the latest patches. After a few minutes, the 6.0.0.1 patch appeared saying it will require a reboot. Click the package icon to start the upgrade. You should see something like this during the upgrade process.
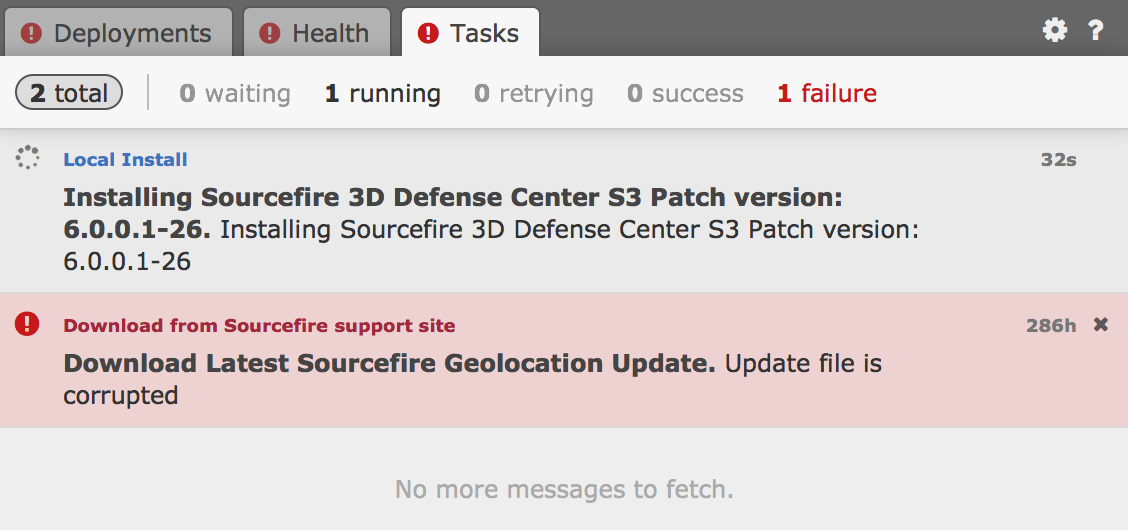 It took me about 30 minutes to complete the upgrade. After it is at 9%, I was logged out of the manager and couldn’t log back in until the system upgrade was complete. Its weird because it looks like its running yet you can’t log in so just be patient.
It took me about 30 minutes to complete the upgrade. After it is at 9%, I was logged out of the manager and couldn’t log back in until the system upgrade was complete. Its weird because it looks like its running yet you can’t log in so just be patient.
Once you can log in, you will see a task notification letting you know that you are now at 6.0.0.1.  Now you are ready to upgrade to 6.0.1 IE the latest FirePOWER software as of March 2016. You can download that from cisco.com, which will be a file called Sourcefire_3D_Defense_Center_S3_Upgrade-6.0.1-1213.sh. Once you have that, go back to your FirePOWER manager, click updates and select UPLOAD. Upload the .sh file, which will take a few minutes. You should see a success page and be able to apply that once its uploads.
Now you are ready to upgrade to 6.0.1 IE the latest FirePOWER software as of March 2016. You can download that from cisco.com, which will be a file called Sourcefire_3D_Defense_Center_S3_Upgrade-6.0.1-1213.sh. Once you have that, go back to your FirePOWER manager, click updates and select UPLOAD. Upload the .sh file, which will take a few minutes. You should see a success page and be able to apply that once its uploads.
NOTE: Minor releases such as 6.0.0.0 to 6.0.0.1 will be available by using the DOWNLOAD button in the Updates section of FirePOWER manager. Major updates such as 6.0.0.1 to 6.0.1 will not appear using the DOWNLOAD button. You must go to Cisco.com to download those and use the UPLOAD button in FirePOWER manager as explained.
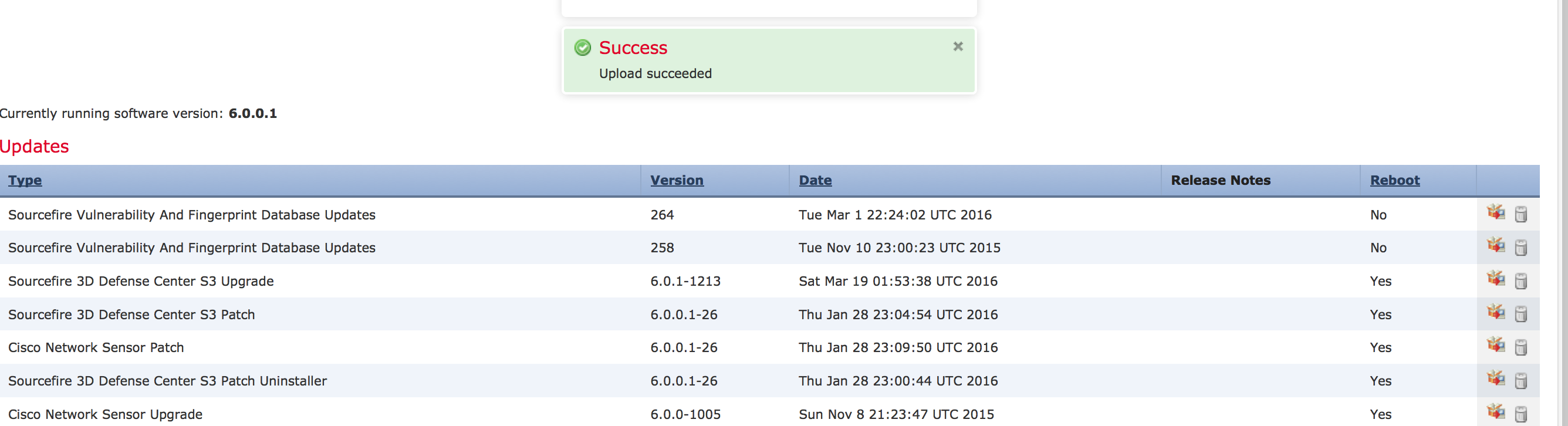 Click the package to start the upgrade. You need to select your manager and continue as shown.
Click the package to start the upgrade. You need to select your manager and continue as shown.  The installation will take around an 1.5 hours to complete the upgrade. You will see the installation started under the task window.
The installation will take around an 1.5 hours to complete the upgrade. You will see the installation started under the task window.
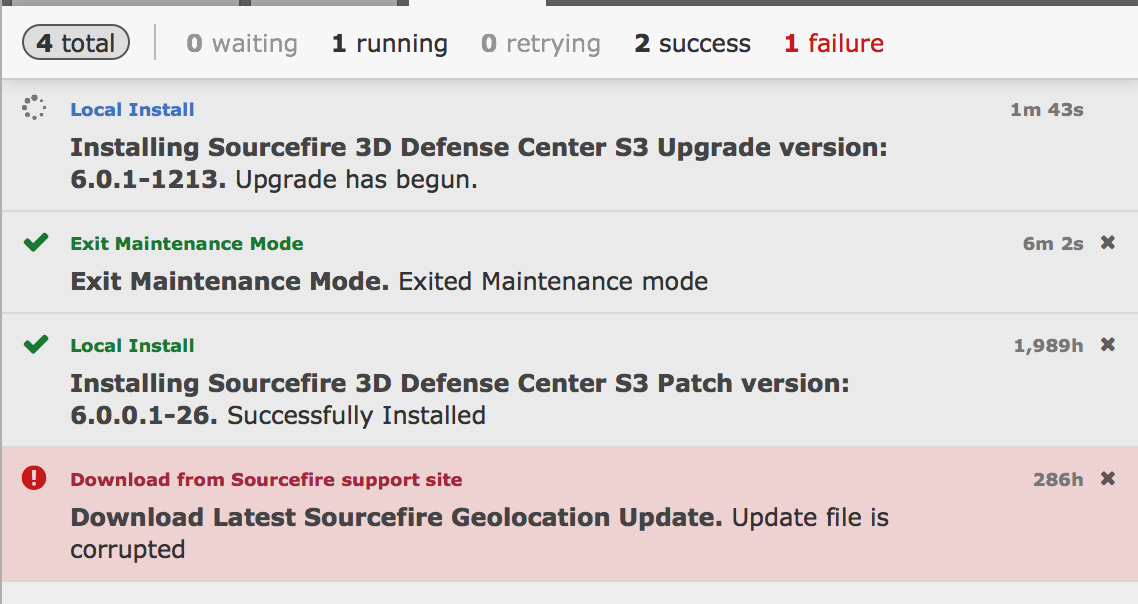 After 15 minutes during the upgrade process, it logged me out of the manager. I logged back in and found it had the following timer showing me the progress.
After 15 minutes during the upgrade process, it logged me out of the manager. I logged back in and found it had the following timer showing me the progress. 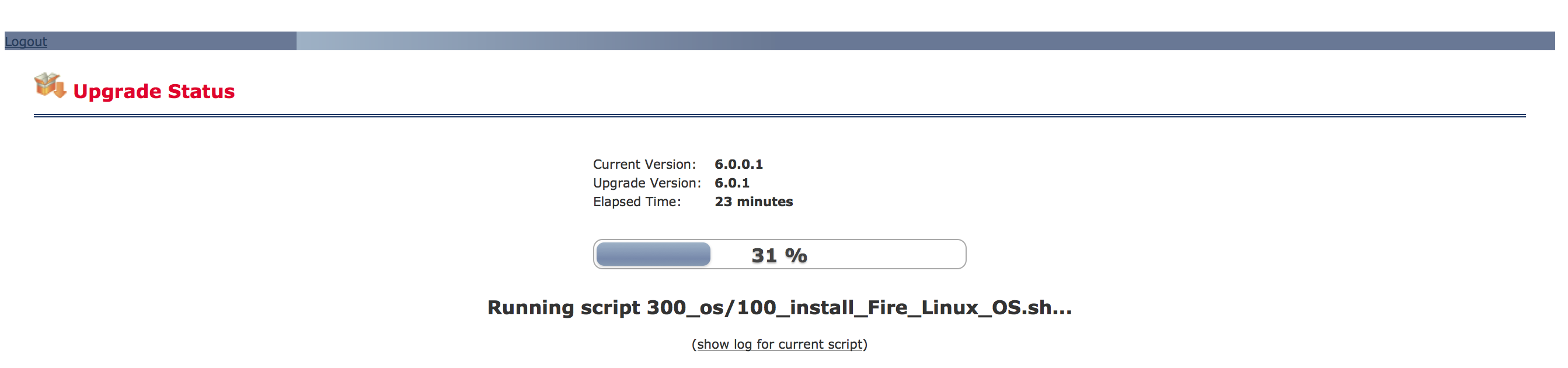 Once completed, you will be able to log into your FirePOWER manager and be alerted things are complete.
Once completed, you will be able to log into your FirePOWER manager and be alerted things are complete. 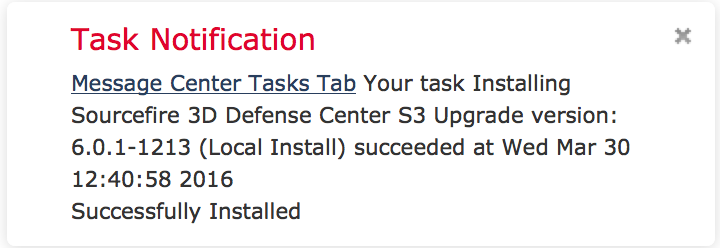 Now lets move to the ASA5512X.
Now lets move to the ASA5512X.
Upgrading a ASA5512X running FirePOWER 6.0.0 to 6.0.1
The first step is to make sure your ASA is managed by the FirePOWER manager. In my case, the ASA is running 6.0.0.0 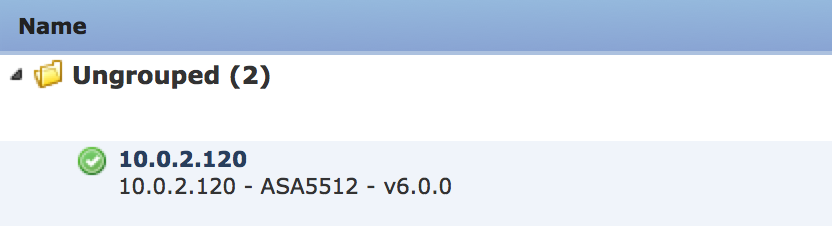 Just like with the FirePOWER manager, you need to upgrade to 6.0.0.1 before going to 6.0.1. You can download and apply the the 6.0.0.1 update the exact way as with the manager via going to system -> update, clicking Download and applying the 6.0.0.1 to the sensor. This is a minor update so no need to leave the GUI for this process.
Just like with the FirePOWER manager, you need to upgrade to 6.0.0.1 before going to 6.0.1. You can download and apply the the 6.0.0.1 update the exact way as with the manager via going to system -> update, clicking Download and applying the 6.0.0.1 to the sensor. This is a minor update so no need to leave the GUI for this process. 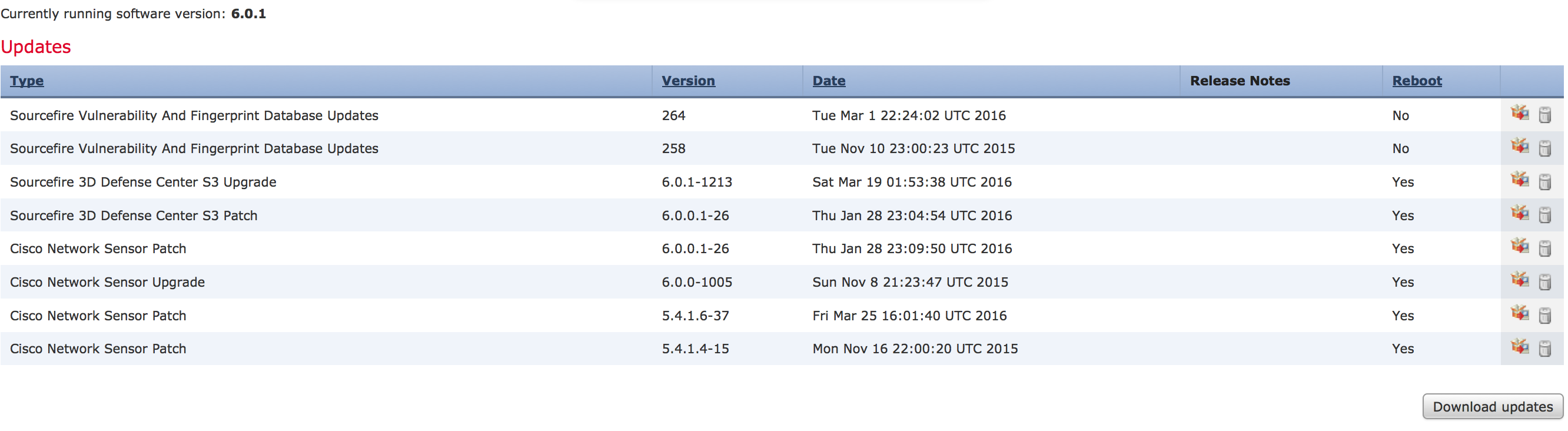 The upgrade takes around 40 minutes to complete. You can monitor this under the task menu.
The upgrade takes around 40 minutes to complete. You can monitor this under the task menu. 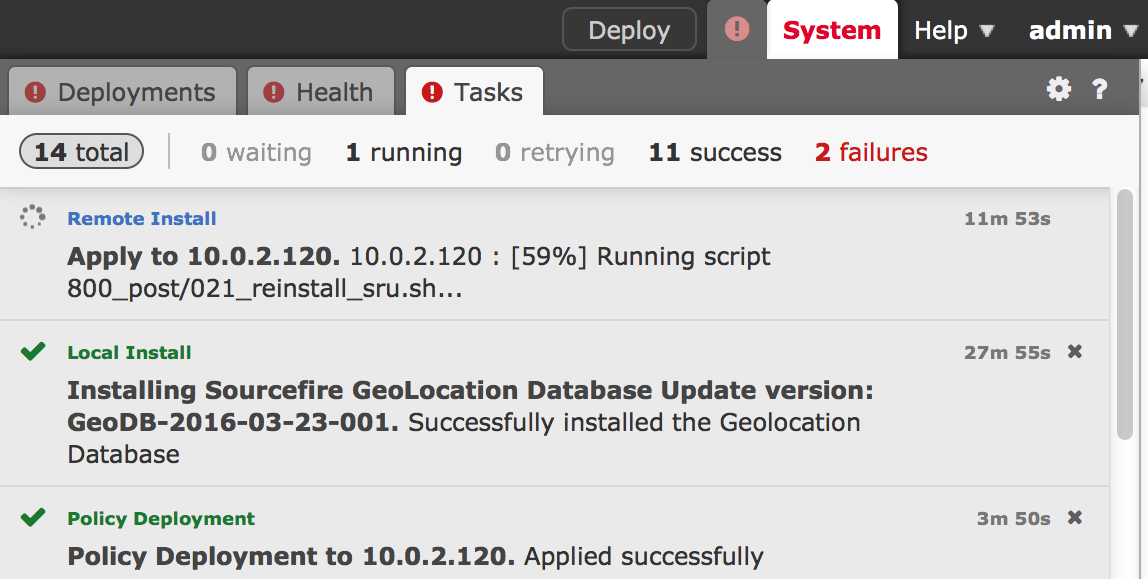 Now you need to choose which FirePOWER image you want to move forward with (see the opening of this post for details). In this case, I’m going with the separate FirePOWER and ASA image for my 5512X. I’ll go with the other unified image for my 5506x later in this post. The 5512X upgrade file is Cisco_Network_Sensor_Patch-6.0.1-29.sh. Once downloaded, go under system -> update and upload that file to the FirePOWER manager.
Now you need to choose which FirePOWER image you want to move forward with (see the opening of this post for details). In this case, I’m going with the separate FirePOWER and ASA image for my 5512X. I’ll go with the other unified image for my 5506x later in this post. The 5512X upgrade file is Cisco_Network_Sensor_Patch-6.0.1-29.sh. Once downloaded, go under system -> update and upload that file to the FirePOWER manager.
NOTE: The separate image upgrade process is simpler than the unified version.
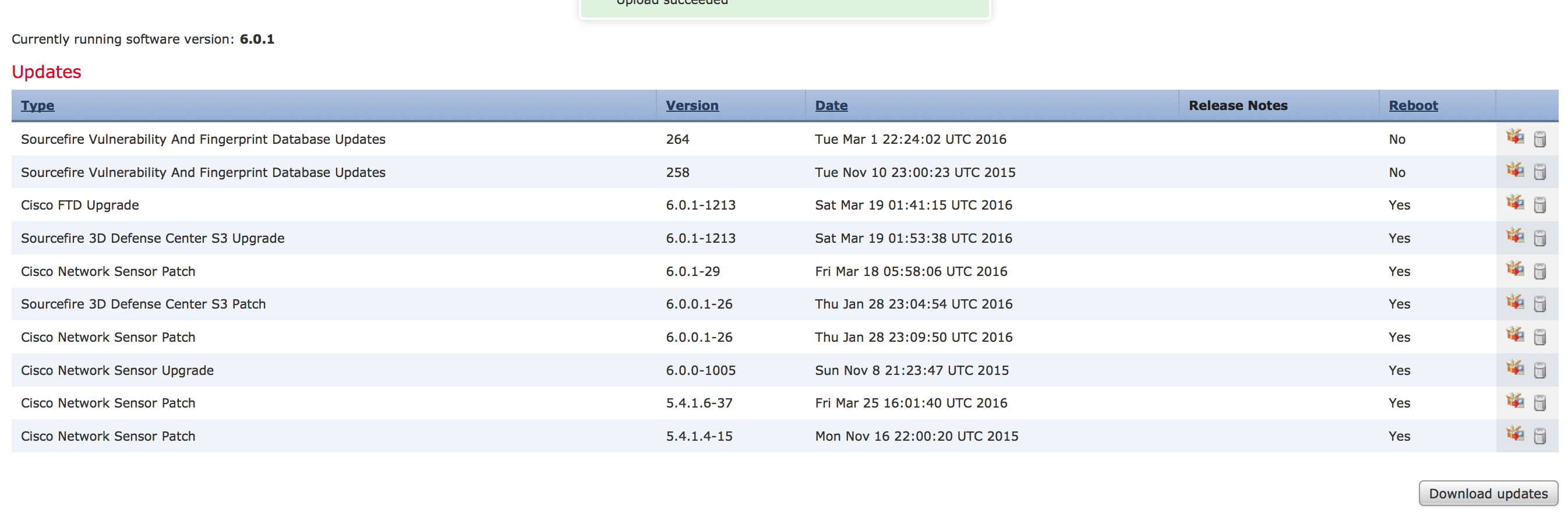
Below shows both the unified and separate ASA and Firepower 6.0.1 images uploaded. I found out I didn’t need to upload the unified image since you have to do a lot more to get it installed shown later in this post.
 Next apply the new 6.0.1 update to your ASA running firepower.
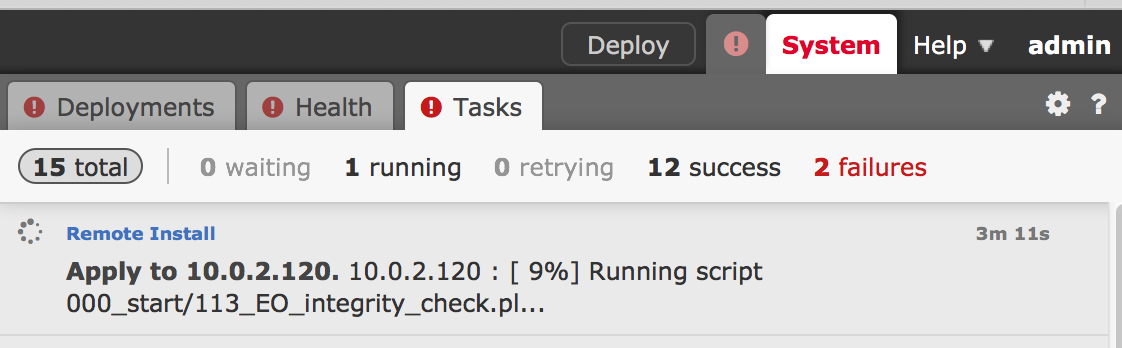
Next apply the new 6.0.1 update to your ASA running firepower. 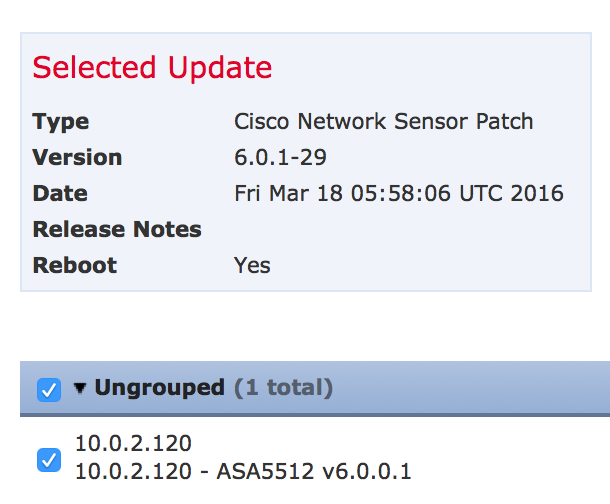 The upgrade took around 40 minutes. You can track the upgrade under the task management.
The upgrade took around 40 minutes. You can track the upgrade under the task management.
 Once upgraded, check to see the device is seen as being managed as 6.0.1 under devices -> device management. In my case, things look good. It took a few minutes after the 5512X reboot for it to show in the manager. Pretty easy to do this upgrade.
Once upgraded, check to see the device is seen as being managed as 6.0.1 under devices -> device management. In my case, things look good. It took a few minutes after the 5512X reboot for it to show in the manager. Pretty easy to do this upgrade. 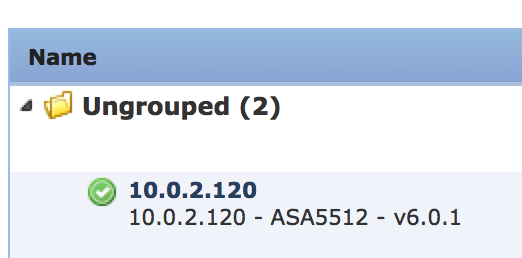 Now I’m going to move to the 5506X first with the separate image and next with the Unified Image. .
Now I’m going to move to the 5506X first with the separate image and next with the Unified Image. .
Upgrading a 5506X to the separate ASDM / FirePOWER 6.0.1 image
Next up is upgrading my 5506X to the separate ASA Firepower 6.0.1 image. Its current state pre upgrade is using ASDM without any centralized management. My goal is to add it to the FirePOWER centralized manager and upgrade it to 6.0.1.
The first step for my situation is to get my 5506X that is not centrally managed added to my FirePOWER management system. As shown in my screenshot of ASDM, my 5506 is running 6.0.0.1-26. 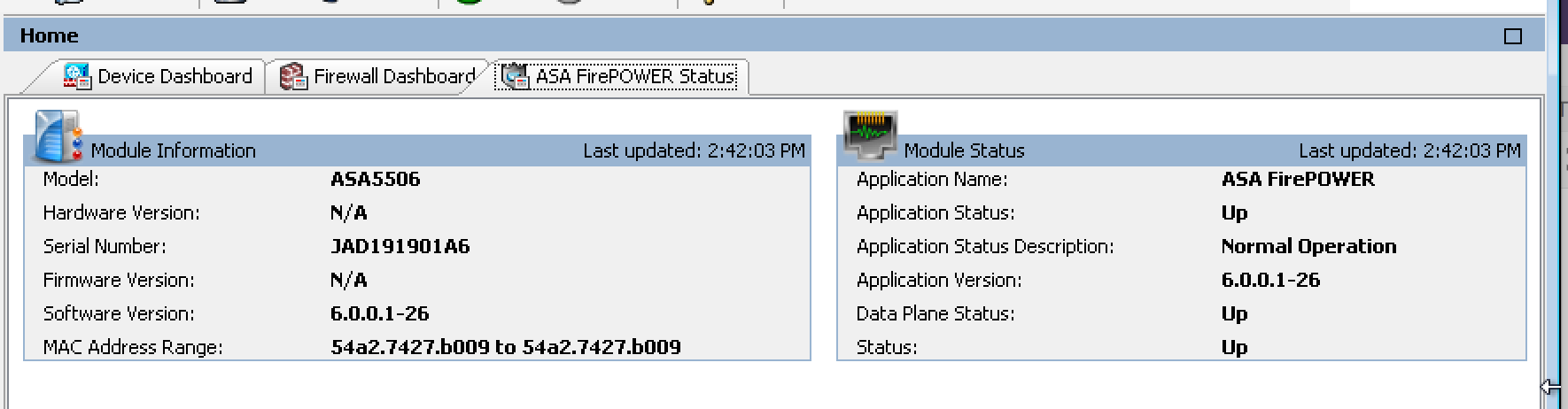 To add my 5506 to the centralized manager, I logged into the console port, typed session sfr console and logged into the sourcefire code. Next I added my manager using configure manager add (IP ADDRESS of Manager) (special word). The next screenshot shows my lab using the 10.0.2.105 and special word is cisco.
To add my 5506 to the centralized manager, I logged into the console port, typed session sfr console and logged into the sourcefire code. Next I added my manager using configure manager add (IP ADDRESS of Manager) (special word). The next screenshot shows my lab using the 10.0.2.105 and special word is cisco. 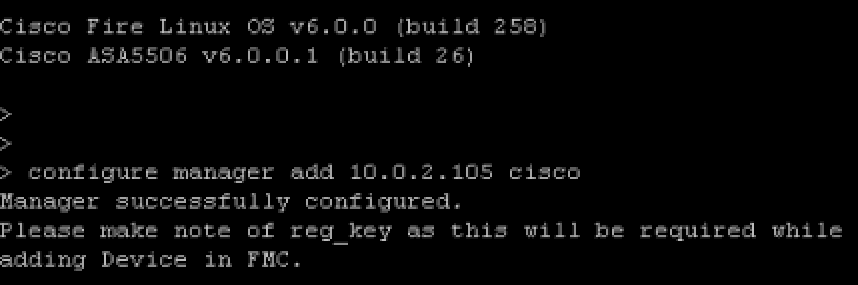 Next I logged into the FirePOWER manager, clicked device -> device management then clicked add device. I filled out the form and added my 5506 as shown.
Next I logged into the FirePOWER manager, clicked device -> device management then clicked add device. I filled out the form and added my 5506 as shown. 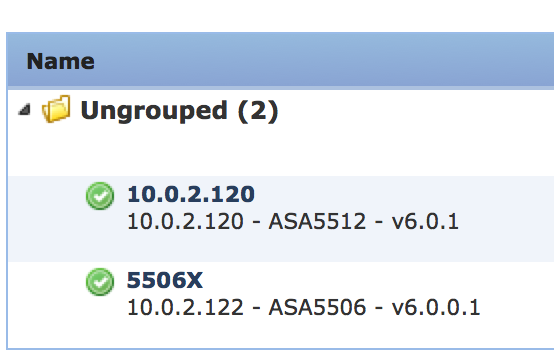 In this first example, im going with the separate ASDM and FirePOWER image, which is Cisco_Network_Sensor_Patch-6.0.1-29.sh. Follow the exact same steps as for the 5512X got my system to 6.0.1 as shown.
In this first example, im going with the separate ASDM and FirePOWER image, which is Cisco_Network_Sensor_Patch-6.0.1-29.sh. Follow the exact same steps as for the 5512X got my system to 6.0.1 as shown.
 Upgrading a 5506X to the Unifed FirePOWER 6.0.1 image.
Upgrading a 5506X to the Unifed FirePOWER 6.0.1 image.
That was fun however I want to test the unified version of 6.0.1. This requires a lot more work. The first step is verifying what version of ROMMON i’m running. The notes found HERE state I need at least ROMMON version 1.1.8. I consoled into my ASA5506 and found I was running 1.1.1 meaning I need to upgrade my ROMMON. Boooo 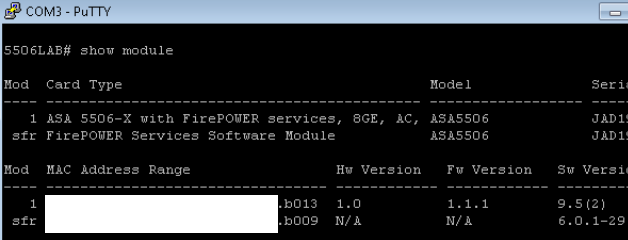 I found the 1.1.8 ROMMON image here under the software download section of the 5506X webpage giving me the file asa5500-firmware-1108.SPA. The documentation says to use a TFTP server however I like easy so I went into ASDM, clicked the File Manager under Tools and used the GUI to move the .SPA file to my ASA5506X disk0:/ as shown.
I found the 1.1.8 ROMMON image here under the software download section of the 5506X webpage giving me the file asa5500-firmware-1108.SPA. The documentation says to use a TFTP server however I like easy so I went into ASDM, clicked the File Manager under Tools and used the GUI to move the .SPA file to my ASA5506X disk0:/ as shown.  Next in the ASA5506X CLI, I typed the following command to start the rommon upgrade process.
Next in the ASA5506X CLI, I typed the following command to start the rommon upgrade process. ![]() The process verifies a hash and asks to proceed with a reboot. After the reboot, the ROMMON is upgraded and the system goes through its cycle process. The entire process takes 5-10 minutes. Now I ran a show module command to confirm I have ROMMON 1.1.8 running.
The process verifies a hash and asks to proceed with a reboot. After the reboot, the ROMMON is upgraded and the system goes through its cycle process. The entire process takes 5-10 minutes. Now I ran a show module command to confirm I have ROMMON 1.1.8 running. 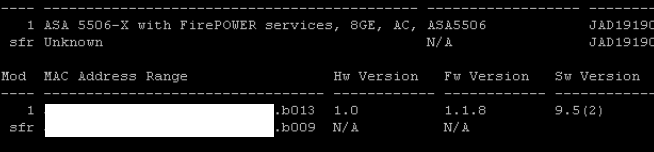 The next step involves actually using a TFTP server since its the image the system will boot directly from. Download that image from cisco.com as well as the .pkg file that will be installed after you boot the boot image. The boot image file is ftd-boot-9.6.1.0.lfbff and .pkg file is ftd-6.0.1-1213.pkg.
The next step involves actually using a TFTP server since its the image the system will boot directly from. Download that image from cisco.com as well as the .pkg file that will be installed after you boot the boot image. The boot image file is ftd-boot-9.6.1.0.lfbff and .pkg file is ftd-6.0.1-1213.pkg.
I used Solarwind’s free TFTP server as my TFTP server. First reboot the ASA5506 and during the boot up process press the ESC key to stop the boot up and put it in ROMMON mode. Next set the ADDRESS, NETMASK, GATEWAY, SERVER and IMAGE using the term followed by a equal. For example, the remote TFTP server would be set by using SERVER=10.0.2.62 in my example. Once you set everything, type tftpdnld to download the image. 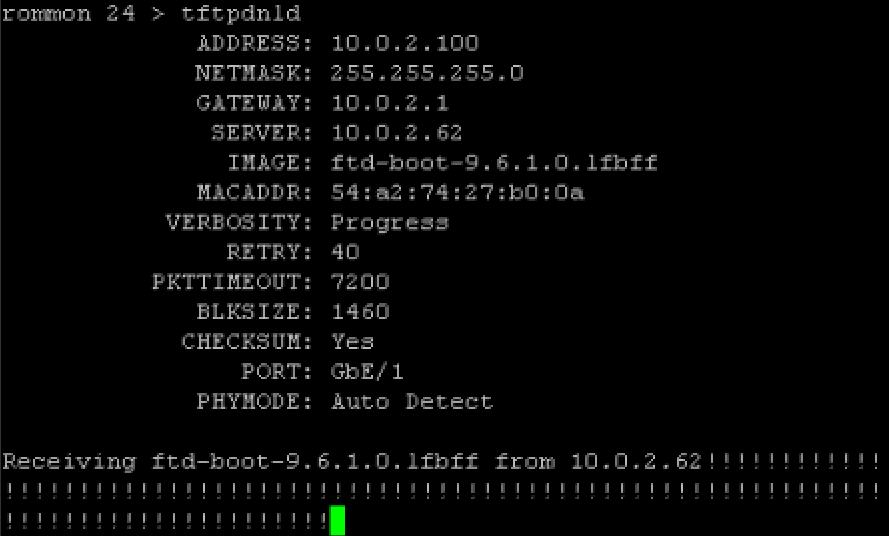 The ASA will automatically boot to that image. This will put you in the firepower boot image, very similar to how it looks when you session sfr console when the images are separated. This process tool around 5-10 minutes.
The ASA will automatically boot to that image. This will put you in the firepower boot image, very similar to how it looks when you session sfr console when the images are separated. This process tool around 5-10 minutes.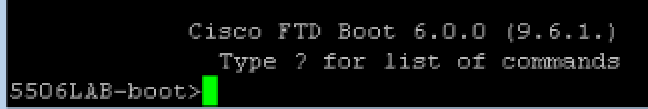 Next use the setup command to setup basic networking. Now you need to post the .pkg file to a http or https location so it can be installed. I used dropbox for this, posting it under a public folder. So for me, the command to install the .pkg file was system install https://DROPBOXPUBLICLOCATION.pkg. It will download and extract the image. Then you will be asked to continue and later asked to press ENTER to reboot once the image installs. You are also warned that the disk0 will be erased during the process. The entire install took me around 20-30 minutes.
Next use the setup command to setup basic networking. Now you need to post the .pkg file to a http or https location so it can be installed. I used dropbox for this, posting it under a public folder. So for me, the command to install the .pkg file was system install https://DROPBOXPUBLICLOCATION.pkg. It will download and extract the image. Then you will be asked to continue and later asked to press ENTER to reboot once the image installs. You are also warned that the disk0 will be erased during the process. The entire install took me around 20-30 minutes. 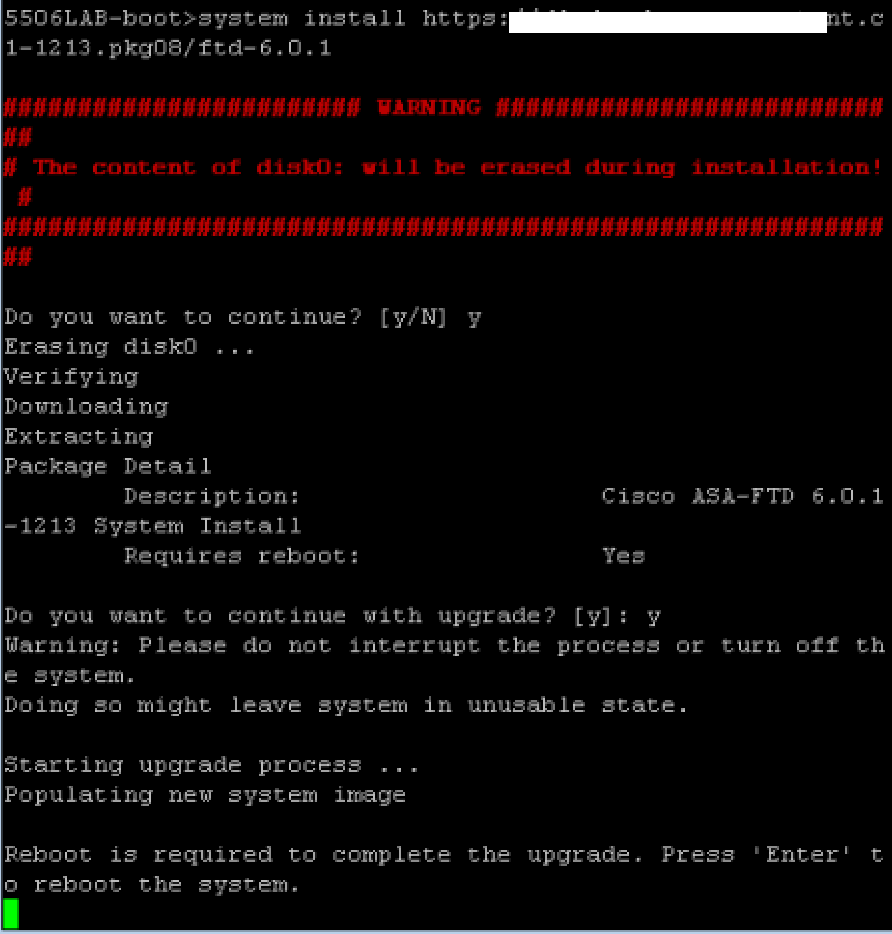 Once the entire process completes, you will see the firepower login. The default login is admin and password Admin123. You will have to go through the EULA upon logging in and provide a new password. Next you provide basic networking information to get it online.
Once the entire process completes, you will see the firepower login. The default login is admin and password Admin123. You will have to go through the EULA upon logging in and provide a new password. Next you provide basic networking information to get it online.
Once again, you need to add the manager using the configure manager add FIREPOWER_MANAGER_IP (special word) to be able to add it back to the centralized manager. Once that is done, go back to the FirePOWER manager and add it. That is done under the Devices -> Device Management and clicking ADD.
I had been using the classic license mode, which isn’t supported for the Unified management image. I found out when I tried to add my 5506X in the FirePOWER manager and was told I had to switch to smart licensing. Switching the smart licensing offers a 90 trail period, so I went with that and then added my 5506X. 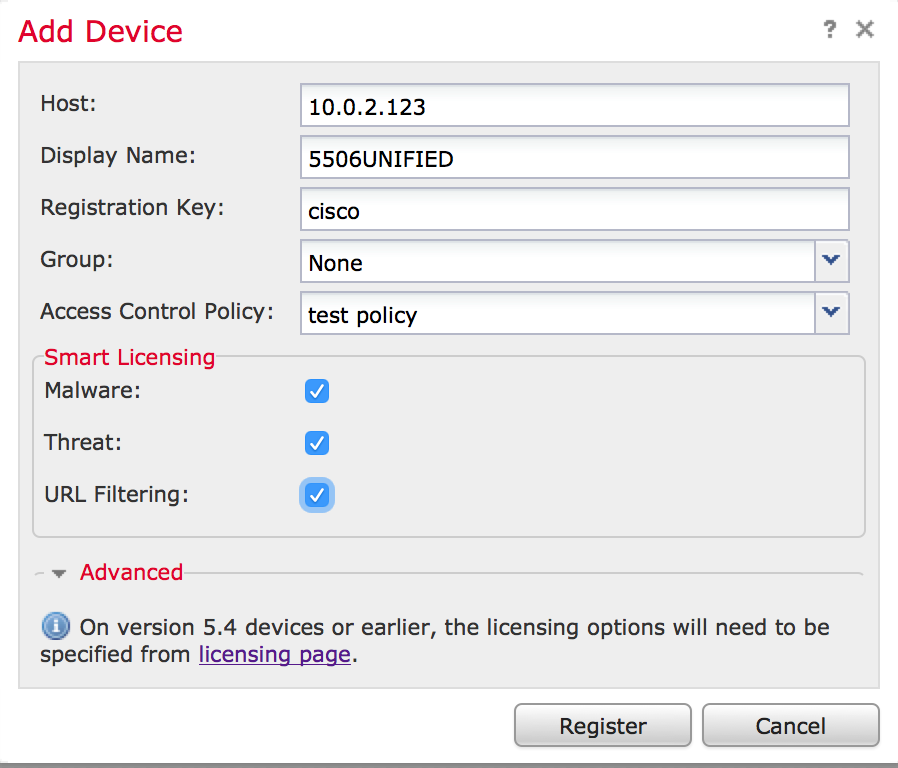 It took a few minutes for the 5506 to be discovered. Now I have a 5506X running the unified 6.0.1.
It took a few minutes for the 5506 to be discovered. Now I have a 5506X running the unified 6.0.1.  Here is an example of routing in the unified image.
Here is an example of routing in the unified image.  and here is the Interfaces section. Cool, no more ASDM.
and here is the Interfaces section. Cool, no more ASDM.  You can find a list of the new features HERE. Hopefully this guide helps with your upgrade.
You can find a list of the new features HERE. Hopefully this guide helps with your upgrade.





NOTE: A friend spent days pulling his hair out over a issue you may run into. If you do a password reset to access your ASA, you must set the boot back to confreg 0x41 prior to doing the install or you may experience weird networking.
Hi so in the future will this mean if I have a standalone 5506x asa using the ASDM I need to purchase this Firepower centralised management? Is this Firepower centralised management box called Firesight?
Cheers
Ross
I can’t talk about the future on here however today if you don’t want to use the centralized manager, use the separate image. There are ASDM enhancements that are included with 6.0.1 to help with administrators not using the centralized manager IE doing everything from ASDM. An example is the SSL Decryption for Cisco ASA with FirePOWER Services Managed Via ASDM. Hope this helps
This centralised management box is called Firesight management center for version 5 and Firepower management center for version 6. This is 6. Fun huh?
I was hoping we could go directly from 6.0.0 to 6.0.1. One of my client has 40+ ASA’s w/ FirePower devices. They aren’t going to be happy to hear they have to do two upgrades.
Hi Deyster. I am not following your comment. You can upgrade directly from 6.0.0 to 6.0.1 however it may be a little different depending on if you are going with the unified image or separate 6.0.1 image. Hopefully this clears up some of your concern.
Thanks for the quick response. When I read (and re-read) the article, you upgraded to 6.0.0.1 before going to 6.0.1. This was my concern as my client isn’t running 6.0.0.1 patch.
I ran into a couple of issues upgrading to 6.0.1 on my 5515X. First off the process took forever since I had to download 5.4.6, the upgrade readiness patch, 6.0.0-1005, and 6.0.1 for both the server and ASA and then upload them to the server. Took forever as they are all large files. First caveat, I had to increase the ram on the server to 8 GB so I had to power it off and change the ram and boot it back up. Second caveat, I couldn’t upgrade the ASA to V6, it kept failing at about 6% with just a failure message. Thanks Cisco for the detailed error really helped me troubleshoot the issue ;). I finally found the issue was cause by not reapplying my policies to the ASA. However, 3rd caveat, the policies I had wouldn’t work as it had several categories and settings that weren’t supported on version 6. So I had to fix the policies, reapply the policies, and then perform the update. Then I had to upgrade both the server and ASA to 6.0.1. Took me two days for what I thought was a simple upgrade. Now I’m having issues with the server being slow or not displaying when trying to make changes to policies.
Thats strange. Have you opened a TAC case to have them see why things are running slow? It took me a few hours to figure it out and things seem to run fine.
Hi Admin,
I got the message from SFR with Unresponsive when I deploy update from FMC to SFR. In FMC i saw maintenance mode of my target device.
Do you have any solution ?
Best Regards,
Chhayheng
The first response I would have is have you called TAC support? The second is have you tried consulting into the target device to see what messages are you seeing by that device? Third, when you updated, what version of code is your manager and target devices running. Note that the manager can only manage two version behind whatever its running. Next did you validate the update worked? Can you roll back if it didn’t or at least to gain back connectivity? Hope this helps!
Hi Admin,
Thank for you respond. I already fixed by rollback and update via command line.
Best Regards,
Chhayheng
Hi,
I found above a very detailed approach, thanks but in case during any .sh update it stuck and failed. How we can roll back to the original working state.
1. upgrade of FMC from 5.4.1.5 to 6.1. since its very time consuming, and if it fails at some point, Nowhere slated the steps to fix it
e:g 800_post/150_install_infodb.sh, 800_post/750_install_vdb_csds.pl
at any 500_rpms, 600_schema or 800_post level
a. what is the safe roll back procedure.
b. Is VDB and geo location update mendatory here while upgrade from 5.4.1.5 to 6.1 (current VDB is 264)
2. Upgrade of sfr (firePower modules) at managed via FMC from 5.4.0.7 to 6.1.
if sfr is in fail-open mode, still blocks the taffic?
during up upgrade path via FMC, does this reboot the ASA or just module only?
what is correct and bare-minimal down event we can expect while upgrading the sfr modules via FMC?
if I need to update active/passive pair via FMC, do i run the update first on standby then active? – and what conditions only modules fails over?
what is procedure of rollback ?
it would be appreciated if my questions get answered here..
Hi Jai,
First off, best practice is to back things up before you upgrade. Also you need to upgrade according to the recommended path. For example, you are suppose to be on 6.0.1 before going to 6.1. That means you are actually upgrading from 5.4 to 6.0 and THEN upgrading to 6.1.
See the release notes for more info http://www.cisco.com/c/en/us/td/docs/security/firepower/610/relnotes/Firepower_System_Release_Notes_Pre_Installation_Package_Version_610.html#22786
Regarding geolocation and vulnerability updates, that can be done after things are running properly from the GUI. Its not mandatory but highly recommended since the whole point of security is blocking the latest threats. Best practice is setting these to auto update on a specific time each week such as 1am so you are always close to the latest.
Regarding your managers … once again I believe you are suppose to go from 5.4 to 6.0 then to 6.1. If they are fail open, that means if the system goes down but here is power, the traffic will continue. So depending on if you are actually in fail open, that would mean it would not block traffic upon failure. If you are upgrading the module, that would only reboot the module hence fail open would permit traffic until the ACL is applied by the ASA again forcing traffic through the firepower module (assuming we are talking about the separate firepower and ASA images). Regarding updating a fail over cluster, yes start with the fail over appliance then do the master. This way if the fail over fails during the update or can’t take on managing the systems, your master is still there as a plan B.
Hope this helps
Joey
Thanks much Joey, can you also please advise the roll back steps
1. FMC
2, SFR modules upgraded via FMC
3. book/guide where steps to fix it
e:g 800_post/150_install_infodb.sh, 800_post/750_install_vdb_csds.pl
at any 500_rpms, 600_schema or 800_post level error during upgrade.