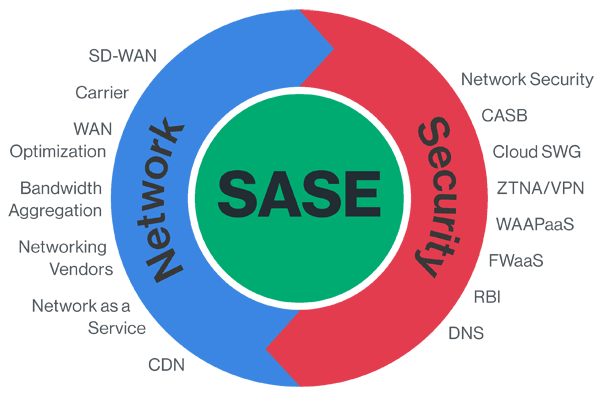
Secure Access Service Edge (SASE) is becoming one of those buzz word conversations that is taking the cybersecurity industry by storm. It all started when Gartner pointed out that in 2018, only 1% of organizations had a SASE investment however, by 2024, they expect 40% of all organizations will have a SASE adoption strategy. That statement kicked off a chain of interest and marketing from pretty much every security vendor based on the fear of missing the boat on this new security trend. Acquisitions are taking place (Examples are Fortinet acquiring OPAQ and Palo Alto acquiring CloudGenix), SASE marketing campaigns are blowing up on the internet, and vendors are creating their own definition for SASE as it fits the goal to sell their technology.
Every meeting I’m in that includes C levels has a conversation about SASE. It is the next big thing following the recent focus on “Zero Trust” marketing however, SASE is likely to stick around for a while. The reason for this is the benefits of both an economic and capabilities viewpoint is hard to ignore. SASE reminds me of when Telephony had a huge breakthrough offering the ability to combine traditional voice and network costs into a single platform leading to a massive swing to voice over IP network adoption. Yes, SASE can be that huge of a game-changer. It is time to pay attention.
This post will break down the components of Cloud and explain why SASE is targeted to be a huge game-changer for the technology industry. First, I need to start with the fundamentals of the cloud. This is the foundation for understanding SASE. Here are some basic definitions around key cloud concepts you need to understand before learning about SASE.
- SD-WAN: Software Defined Wide Area Networks is a virtual WAN architecture allowing enterprises to leverage any combination of transport service to securely connect users and applications. In particular, it allows to migrate off of MPLS or use a hybrid of services including MPLS.
- MPLS: One type of data service that can be used by a SD-WAN and the core technology for many traditional WANs.
- Secure Web Gateway (SWG): These are security tools designed to control web traffic with the goal of managing bandwidth consumption, protect you from malicious parties and enforce Internet usage policies such as not going to gambling websites during work hours. Think proxy or application layer firewall. The biggest challenge for SWG is forcing traffic through this technology when users are spread across various parts of the world. Forcing traffic through a VPN is becoming less possible as remote work and general data usage increases.
- Secure Internet Gateway (SIG): SIG aims to address the challenges of SWG by protecting data, applications and users regardless of where they are in the world. Problems addressed include protecting all ports and protocol (many proxy-based SWG solutions only protected port 443 and 80 traffic), providing security on and off a VPN, keeping up with the latest updates (automatically updated vs requiring steps to upgrade) and even adding the ability to link into SaaS offerings, which SWG can’t do. This does not address concerns with SaaS.
- SaaS: Software as a service means a cloud service that the cloud provider is responsible for everything and you just use the service. Think about Gmail or Salesforce as examples. You don’t have to deploy or managing anything outside of your data within their services. Challenges for SaaS include shadow IT meaning you don’t know when your employees are using a SaaS service unless you have specialized tools such as a CASB and knowing which SaaS tools are being used by employees. You may say only use Box but how do you know employees are not using DropBox or other unapproved services (in this example … I am a fan of DropBox and not saying anything bad about DropBox)?
- Cloud Access Security Broker (CASB): Tool that sites between cloud service users and cloud applications to allow visibility and control of cloud applications. Imagen trying to secure a SaaS. You can’t deploy firewalls, IPS or other security tools since you don’t have that control. You can, however, leverage a CASB.
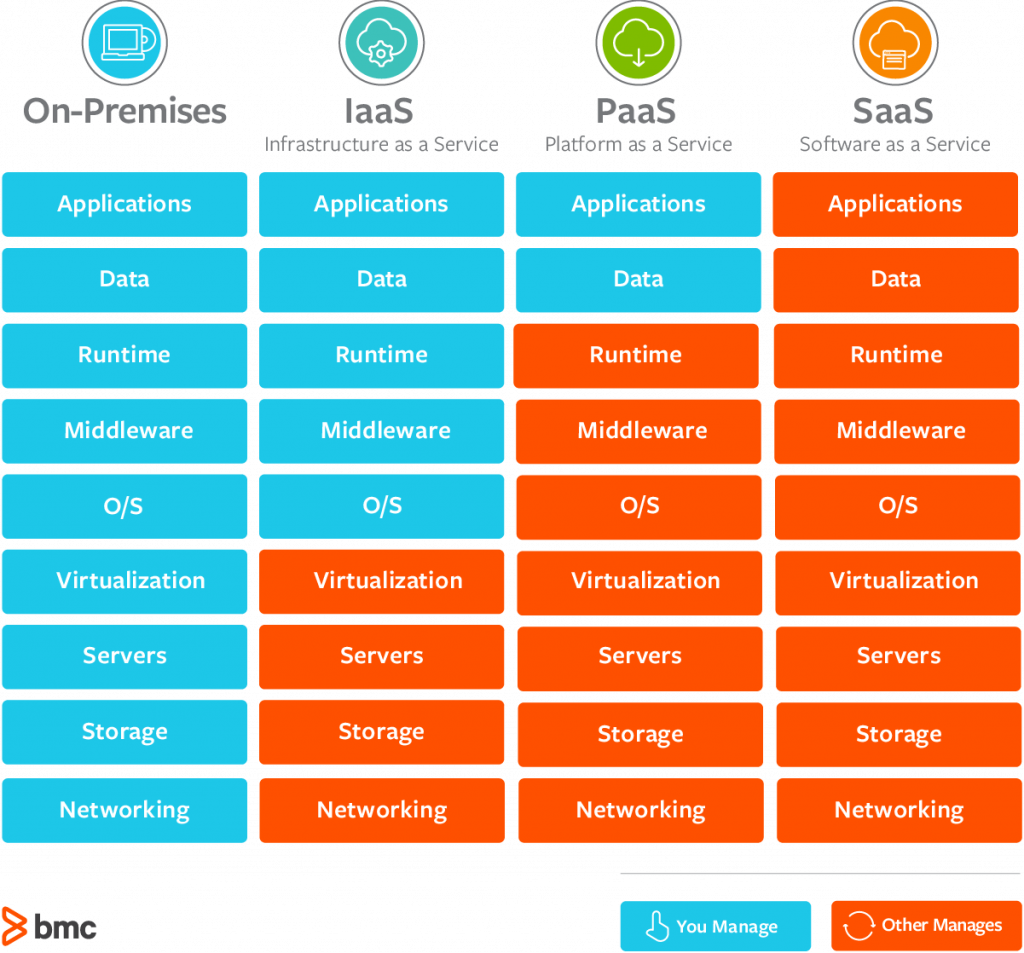
- IaaS / PaaS: Infrastructure and Platform as a Service are other cloud options that give you more control over what is running in the cloud. PaaS means the cloud service provider (CSP) manages the infrastructure however, you can control the application. Think controlling your own application however, you don’t worry about anything else. IaaS means you get even more control/responsibility by being able to deploy everything from the virtual servers that run your application to how the application runs. I included a chart developed by BNC below that breaks down comparing running your own data center, IaaS, PaaS, and SaaS. There isn’t an always best approach hence why adoption for any of these architectures depends on the business need.
So now that you have a basic understanding of cloud concepts, how does this all lead to SASE? Let’s break down the answer into a few parts. The first answer to WHY SASE is the potential savings from SD-WAN. It should be no surprise that cost savings are a major driver for this movement. Traditional WANs were never designed for the cloud. There are well-publicized articles showing the cost savings of migrating from MPLS circuits to SD-WAN. In summary, MPLS bandwidth costs are high and the programming necessary at a hardware level can also be expensive to manage. SD-WAN is made up of software rather than hardware allowing for simplicity in deployment and management. SD-WAN removes the need for proprietary hardware and lets sites connect to the cloud for connectivity. Applications can sit in the cloud also leading to huge improvements in performance vs deploying from a WAN. In short, many organizations are migrating to SD-WAN. It’s happening now.
Another driver to SD-WAN and any of these topics including SASE is mobility. Getting work done used to mean going into an office where IT services are provided however, those days are fading away fast. COVID19 has escalated the growth of supporting working from home increasing cloud-based technology adoption in many businesses … even those that believed it wouldn’t be possible. I have heard from dozen customer C levels over the last few months stating they thought COVID19 would dramatically reduce their employee productivity rate however, they found cloud and remote work technologies are actually proving this to not be true. Some organizations such as Facebook, Google and Microsoft are making bold statements about keeping a work from home approach for their business as the norm for the foreseeable future. More mobile workers will mean more cloud-based technology. It just makes more sense to use a SaaS verse deploying hundreds of devices to employee homes.
Up until now, I’ve been talking about two growth areas. The first is converting WANs to SD-WAN and other is migrating from hardware-based technology to software as a service (SaaS). In both cases, the number one question that comes up is SECURITY. This leads us to a need to secure all cloud usage including SD-WAN and SaaS, PaaS, IaaS. Today, security vendors are patching together security tools that once focused on WANs and Datacenters and calling the combination their “Secure Access Service Edge (SASE)” offering.
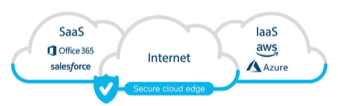
In most cases, this is actually not SASE according to how Gartner spelled it out. CASB and identity and access management (IAM) tools are being used to secure SaaS applications. Agents and virtual security appliances are being deployed in IaaS environments with the mentality of a traditional datacenter hosted from the cloud. Endpoints are having their traffic forced through cloud proxies and/or using VPNs to secure the host. Data loss technology is being deployed everywhere since organizations are losing their ability to track how their data is being used. Each of these approaches is important however, they are separate technologies all attempting to address different points of the cloud security problem. This image shows different views of the cloud and how related security concepts tend to be provided through different tools.
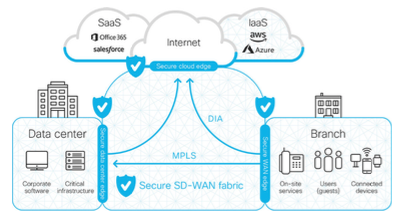
Gartner’s view of SASE is the combination of two things. First, it is taking all the value from SD-WAN meaning offering organizations the ability to get off of their costly MPLS WANs, which is happening now. The second part of SASE is securing the SD-WAN offering regardless if the data sits within a SaaS, PaaS, IaaS, private cloud (aka your internal datacenter), or on an endpoint. SASE needs to consider the value provided by CASB, SIG / SWG, security agents, data loss technology, VPN, and security tools such as virtualized next-generation firewalls / IPSs. SASE means to offer all of this along with an SD-WAN service.
You should see why SASE is a huge umbrella of features and services, which fundamentally would be impossible to ignore if delivered properly. It’s a bold claim for a vendor to offer this type of service, which nobody really can do without piecing existing technology together today. This is why vendors are bending the language to highlight what they can do while ignoring what should be included but is not without another tool or technology. That doesn’t mean a true SASE offering won’t be available soon. The next image is conceptually what SASE means. It’s securing all aspects of the SD-WAN.
Where do you go from here? I recommend you start looking into SD-WAN and SaaS security concepts. For example, think about traditional security tools such as Firewall and imagine that tool offered as a cloud service hence leading to Firewall as a serivce (FWaaS). This is the future for many organizations and it may come as a bundled offering under the SASE umbrella. This Gartner imagined 2024 isn’t too far away and the industry is taking this vision pretty seriously.