Many people prefer open source to buying enterprise products. The pro’s of enterprise include not having to build everything, threat feeds provided by vendor, vendor support tested deployments. The pro’s of open source are the cost savings (outside of time to build), customization options and for Snort, huge community support.
Comparitech provided a SNORT cheat sheet for those looking to go open source with their IPS/IDS needs. SNORT owned by Cisco is one of the leading open source IDS/IPS options out there. Many vendors use SNORT in the back end. Learn more about SNORT at https://www.snort.org/. The original post for the SNORT cheat sheet can be found at https://www.comparitech.com/net-admin/snort-cheat-sheet/. Here is the post from Comparitech.
All the tables provided in the cheat sheets are also presented in tables below which are easy to copy and paste.
The Snort Cheat Sheet covers:
- Sniffer mode, Packet logger mode, and NIDS mode operation
- Snort rules format
- Logger mode command line options
- NIDS mode options
- Alert and rule examples
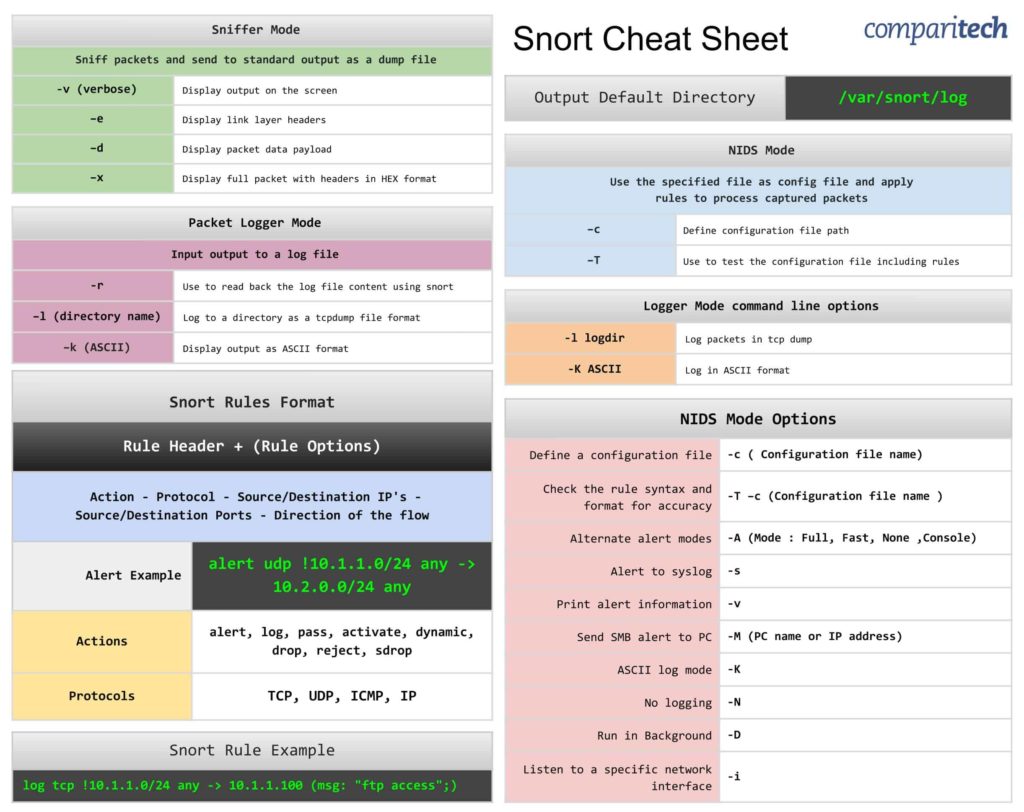
View or Download the Cheat Sheet JPG image
Right-click on the image below to save the JPG file ( 2443 width x 1937 height in pixels), or click here to open it in a new browser tab. Once the image opens in a new window, you may need to click on the image to zoom in and view the full-sized jpeg.
View or Download the cheat sheet PDF file
Download the cheat sheet PDF file here. When it opens in a new browser tab, simply right click on the PDF and navigate to the download menu.
What’s included in this cheat sheet
The following categories and items have been included in the cheat sheet:
Sniffer Mode
| Sniffer Mode | |
|---|---|
| Sniff packets and send to standard output as a dump file | |
| -v (verbose) | Display output on the screen |
| –e | Display link layer headers |
| –d | Display packet data payload |
| –x | Display full packet with headers in HEX format |
Packet Logger Mode
| Packet Logger Mode | |
|---|---|
| Input output to a log file | |
| -r | Use to read back the log file content using snort |
| –l (directory name) | Log to a directory as a tcpdump file format |
| –k (ASCII) | Display output as ASCII format |
NIDS Mode
NIDS Mode | |
|---|---|
Use the specified file as config file and apply rules to process captured packets | |
–c | Define configuration file path |
–T | Use to test the configuration file including rules |
Snort rules format
| Snort Rules Format | |
|---|---|
| Rule Header + (Rule Options) | |
| Action – Protocol – Source/Destination IP’s – Source/Destination Ports – Direction of the flow | |
| Alert Example | alert udp !10.1.1.0/24 any -> 10.2.0.0/24 any |
| Actions | alert, log, pass, activate, dynamic, drop, reject, sdrop |
| Protocols | TCP, UDP, ICMP, IP |
Logger mode command line options
| Logger Mode command line options | |
|---|---|
| -l logdir | Log packets in tcp dump |
| -K ASCII | Log in ASCII format |
NIDS mode options
| NIDS Mode Options | |
|---|---|
| Define a configuration file | -c ( Configuration file name) |
| Check the rule syntax and format for accuracy | -T –c (Configuration file name ) |
| Alternate alert modes | -A (Mode : Full, Fast, None ,Console) |
| Alert to syslog | -s |
| Print alert information | -v |
| Send SMB alert to PC | -M (PC name or IP address) |
| ASCII log mode | -K |
| No logging | -N |
| Run in Background | -D |
| Listen to a specific network interface | -i |
Snort rule example
| Snort Rule Example | log tcp !10.1.1.0/24 any -> 10.1.1.100 (msg: “ftp access”;) |
Output Default Directory
| Output Default Directory | /var/snort/log |