I find many organizations lack visibility within the data center even though that is where most of the action is happening. Datacenter administrators use the old approach of building walls around the data center with “next-generation” aka application layer firewalls, which include IPS and some malware detection capabilities. This approach isn’t awful however, any threats or vulnerabilities within the datacenter are not seen meaning you only see traffic coming and going from the data center aka “north-south” traffic. A better approach is to deploy technology within the datacenter to view traffic down to the process level.
Older approaches to viewing internal datacenter traffic include virtual devices that can see traffic within the virtual network aka “east-west” traffic as well as agents installed on virtual systems. These approaches are good however, challenges to this approach include tapping into each virtual network segment and creating policies for what is considered good and bad. This brings up the concept of Whitelist vs Blacklist security. Any security professional will tell you a whitelist approach is more secure meaning only allowing good however, many organizations use a blacklist approach due to the complications to deploy whitelist-based security. This challenge includes tools used within many data centers meaning they only look for known bad behavior or pattern match files for threats using signature-based tools leaving anything else consider as “good”. Examples of such tools include antivirus install on applications with some breach detection capabilities based on behavior matching or an IDS tapped into the virtual network reading traffic off of a span port. This approach does not give any forensics visibility of why something is malicious, what vulnerabilities were targeted and this approach has many gaps that can be exploited by malicious parties since you only flag threats that cross a detection point.
The best approach for datacenter security is to deploy whitelist-based security, which requires a few key ingredients. The first capability is the ability to map out applications and automatically develop a “known good” so whitelists can be created and dynamically adjusted. Dynamic tuning allows for real-time adjustments to what is and not allowed, which is fundamentally the only way to operationalize white-list security without impacting business. Second, threat intelligence needs to be leverage including known vulnerability data as well as current threat data so there is a baseline to compare against the current threat landscape. Lastly, there needs to be a method to deploy and manage the solution. Cisco Tetration is capable of doing all of this including monitoring any system or application for vulnerabilities, identify risk associated with unused/open ports and applications, identify unusual and potentially risky or malicious traffic, and audit for other situations including the old question … why is this application running slow … Network? Application? Client?
Let’s take a look at how this works. I’m going to access a Tetration deployment I recently was involved with.
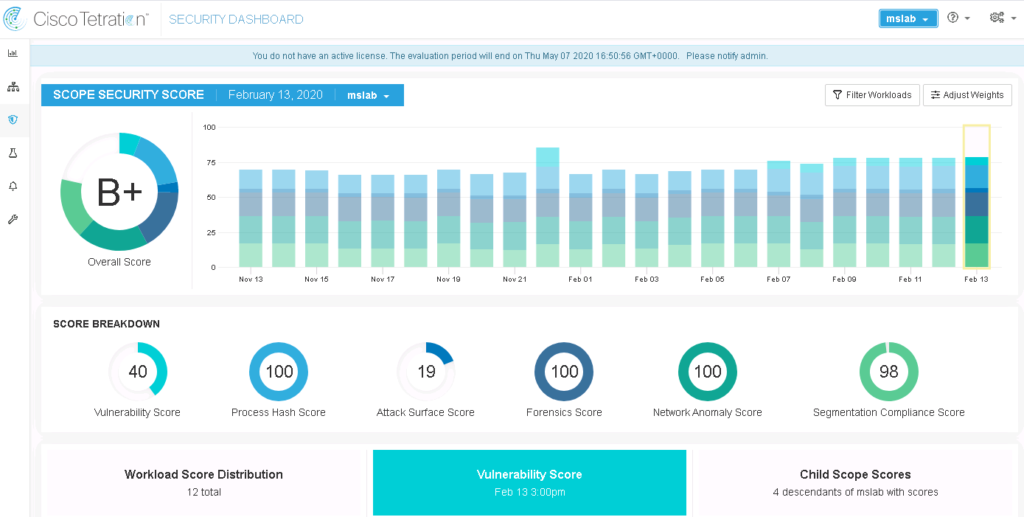
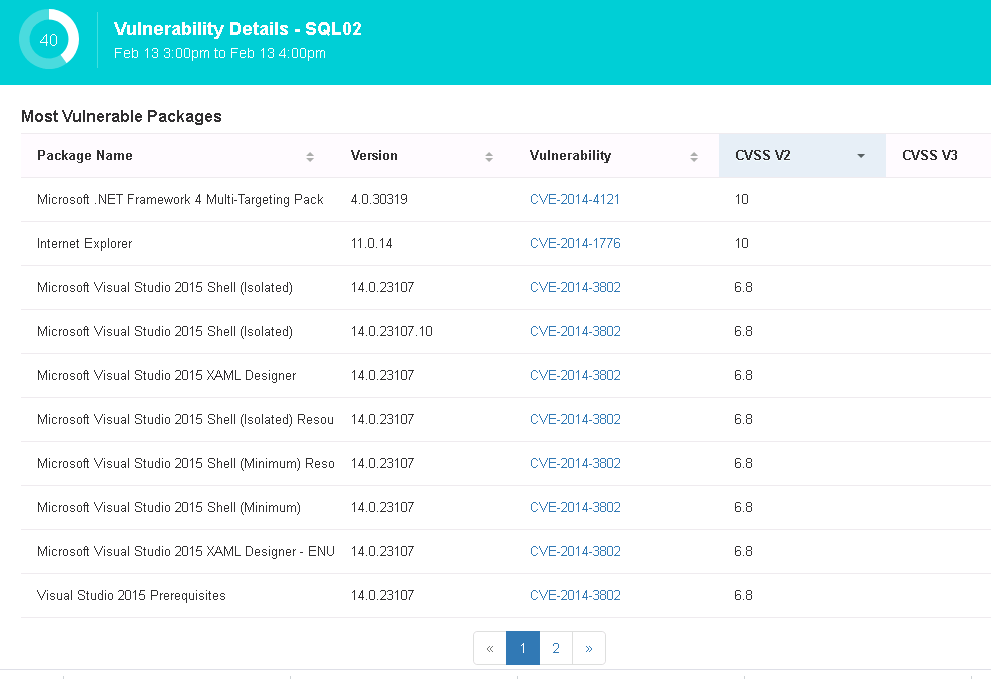
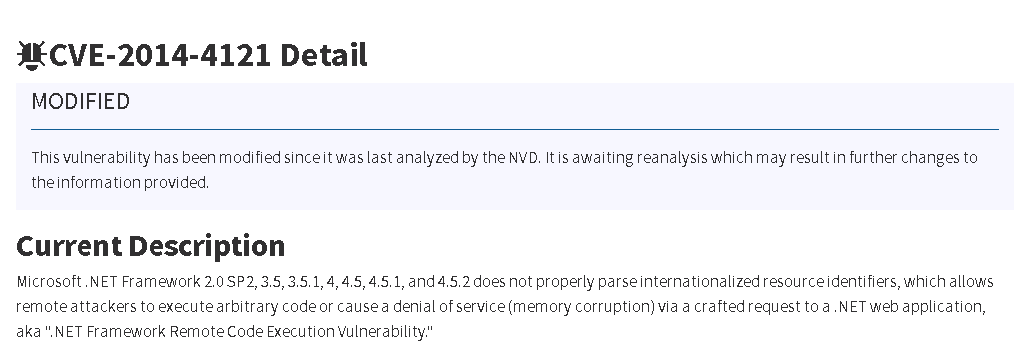
The first thing to check out is the Tetration Security Dashboard. The overall score being shown means a high-level assessment of the threat level for the environment. Vulnerabilities shown in the score breakdown include anything that could be potentially exploited. For example, I clicked one workload that was found as having a lot of vulnerabilities and saw what is shown in the next image. Clicking a CVE brought up the NIST explanation of the vulnerability found within the workload.
There is an attack surface mapping in the Tetration dashboard which looks at all systems and applications and decides which ports and protocols could be used for exploitation purposes. This of this as an assessment for potential targets within the datacenter.
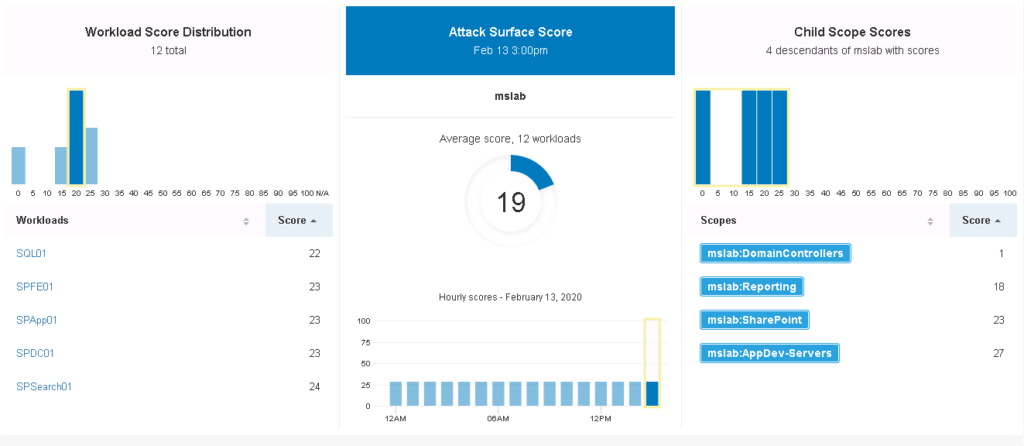
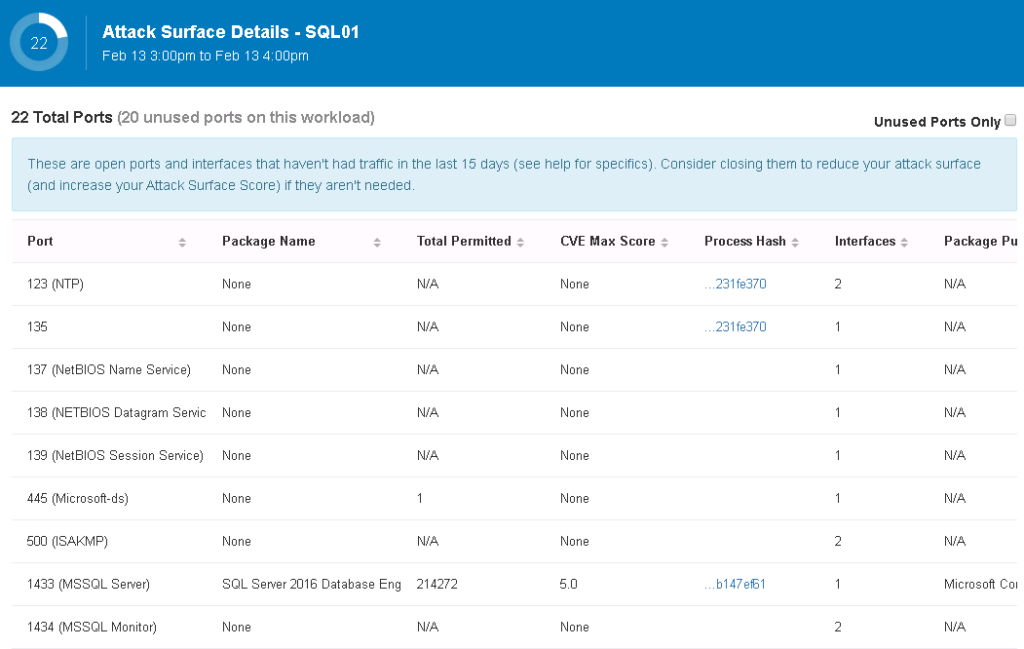
Here is an example of a SQL mapping showing various open ports
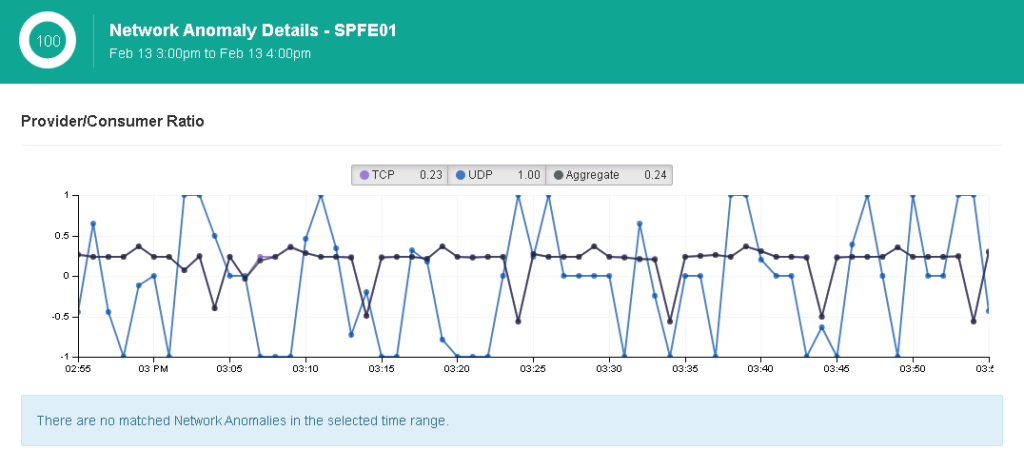
Anomaly detection is also very powerful and should be included in any breach detection strategy. The concept works by baselining what is considered normal traffic and behavior within systems and flagging anything unusual. If a malicious application attempts to conceal itself using various packing, encoding and stealth tactics, it will stand out as something different compared to other applications and processes. If the malware doesn’t use stealth, its behavior will be identified as malicious by behavior detection capacities hence the strength of combining breach detection and anomaly detection capabilities. The next image shows an example of a baseline and the top anomalies mapped against it.
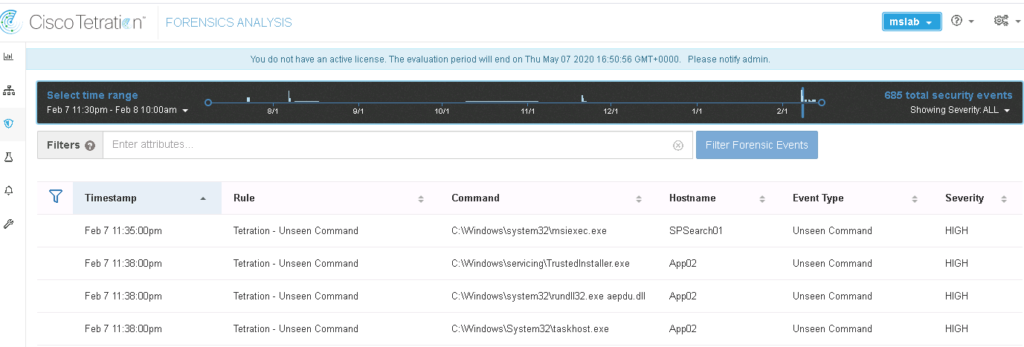
Another important datacenter security concept is forensics. Proper forensics includes traffic for each endpoint as well as the traffic between endpoints, which both are collected by Tetration. Tetration can be extremely effective at identifying insider threats since it will monitor for things it has never seen before, privilege escalation, side-channel attacks, meltdowns and many other threats that many datacenter administrators are blind to since these threats occur within the datacenter and typically executed with stealth in mind. Tetration exams data using a combination of signature, behavior and anomaly detection reducing the number of false positives.
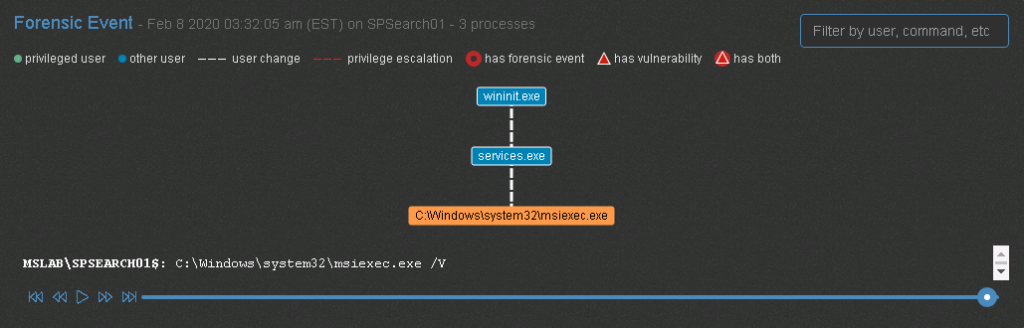
Clicking into any event allows the administrator to see the identify process’s relation to the program that was executed and what was specifically done.
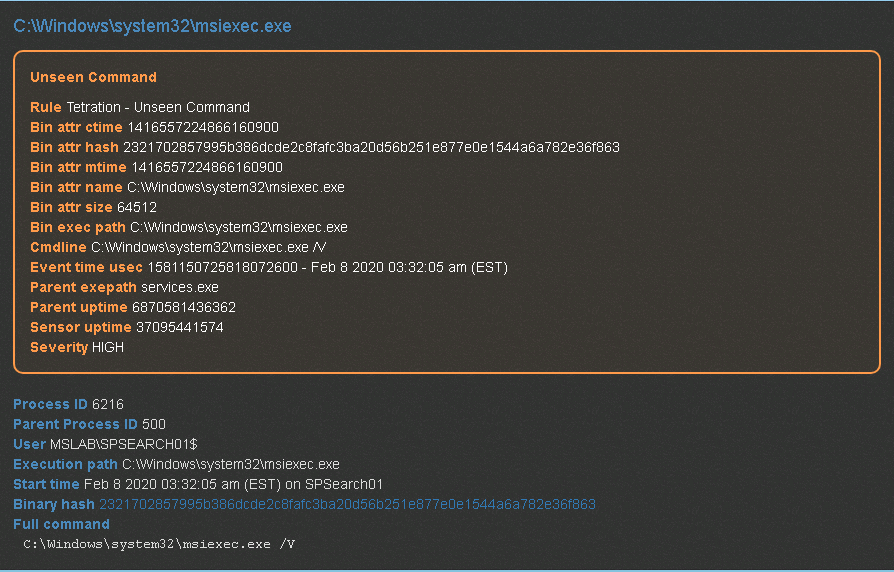
The last cool thing to touch on is the old “hey security/networking is blocking or making an application run slow right?”. Tetration can quickly zero in on traffic flow and identify latency as shown.
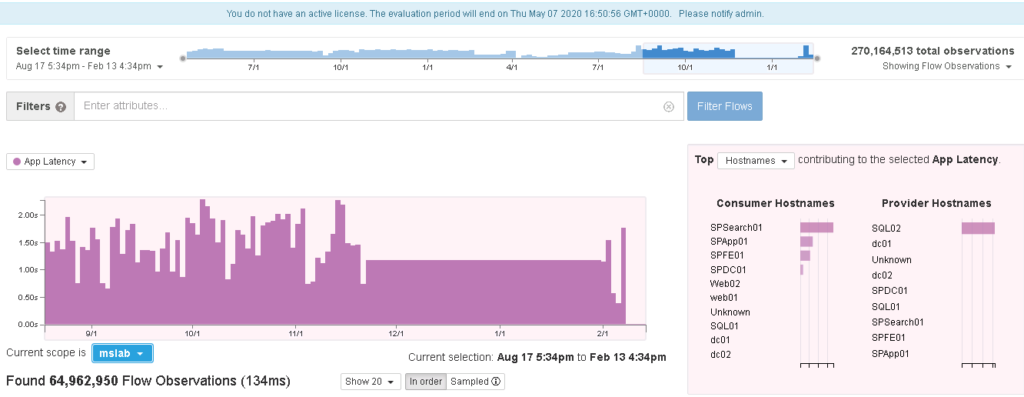
But the million-dollar question is, why is it slow? You can eliminate things like the network by filtering in on network delays. In this next image … Tetration proves all of the delays are not a network issue.
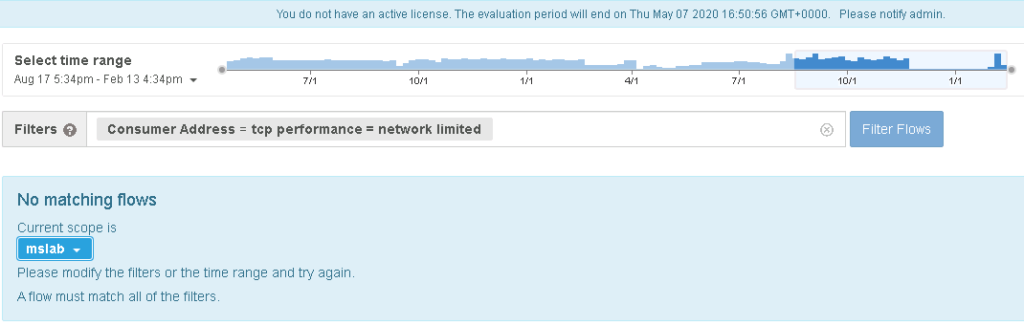
That is just a quick overview of how Cisco Tetration can provide a modern approach to securing the data center. Check out Cisco Tetration at your next security conference or at https://www.cisco.com/c/en/us/products/security/tetration/index.html. It’s a better approach for end-to-end data center visibility and security.



