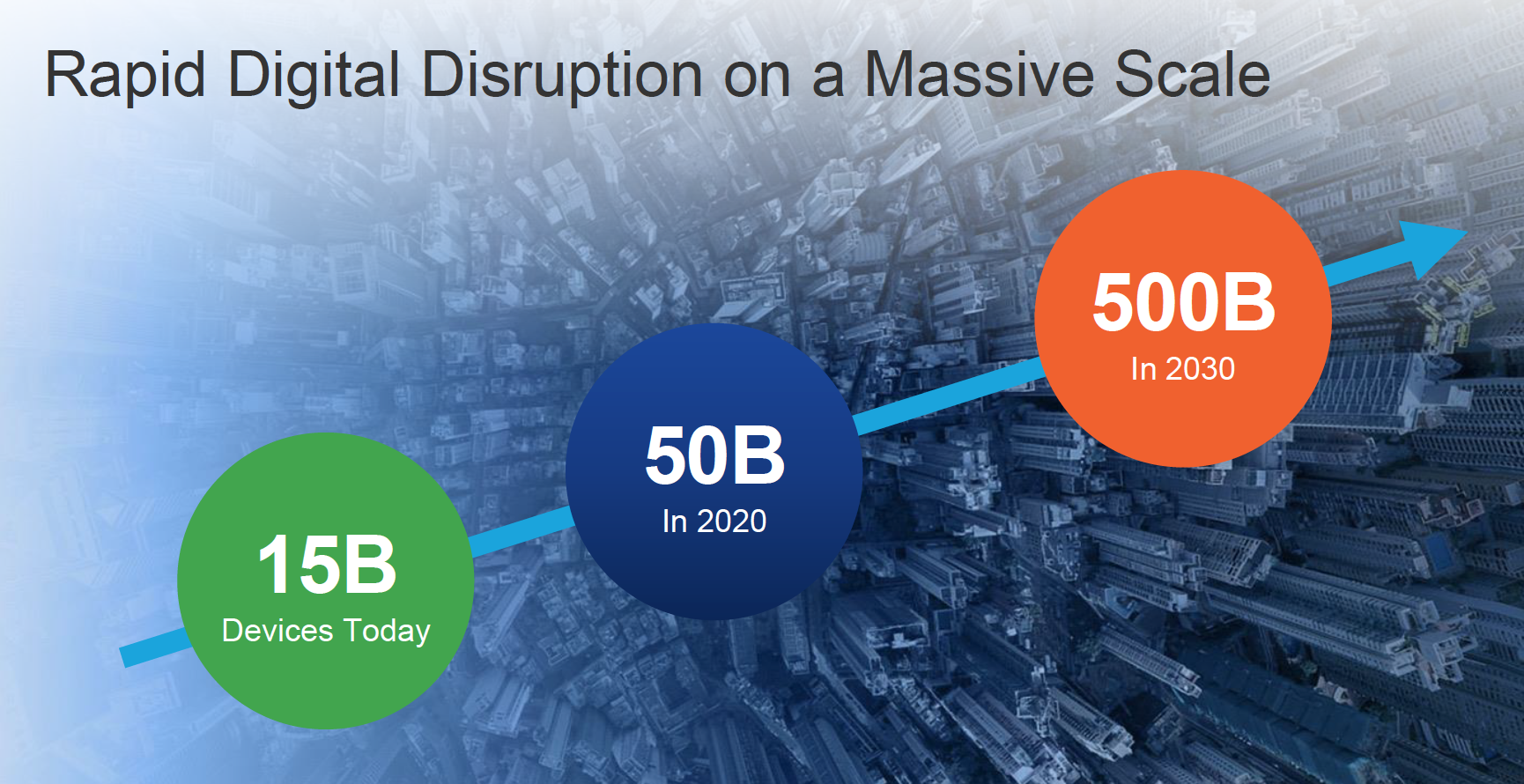
NetworkWorld just posted about the largest DDoS ever seen using IoT devices (Original posted here). For those that have seen one of my recent Keynotes or Ciscolive talk, you would have saw this slide showcasing the prediction of how many devices will be online by by 2030. That means if we have around 15 billion devices today and growth is targeting 500 billion … that is a lot of devices that must be IP enabled meaning a lot of IoT.
 This attack is just one example of what could happen if we continue to not hold any device with IP capabilities accountable for security concerns. Check out this article and think about what could happen if instead of 1 million … it was 1 billion devices behind this attack! Nobody would be safe from that size of volume based DoS weapon.
This attack is just one example of what could happen if we continue to not hold any device with IP capabilities accountable for security concerns. Check out this article and think about what could happen if instead of 1 million … it was 1 billion devices behind this attack! Nobody would be safe from that size of volume based DoS weapon.
Securing the internet of things should become a major priority now that an army of compromised devices – perhaps 1 million strong – has swamped one of the industry’s top distributed denial-of-service protection services.
It wasn’t that Akamai couldn’t mitigate the attack – it did so for three days – but doing so became too costly, so the company made a business decision to cut the affected customer loose, says Andy Ellis the company’s chief security officer.
he delivery network has dropped protection for the Krebs on Security blog written by Brian Krebs after an attack delivering 665Gbps of traffic overwhelmed his site Tuesday. The size of the attack was nearly double that of any Akamai had seen before.
An IoT botnet generating this much traffic is a bellwether event that Ellis says will take some time to analyze to come up with more efficient mitigation tools.
Its impact is similar to the 2010 attacks by Anonymous using the open source, low-orbit ion cannon tool, or the 2014 DDoS attacks launched from compromised Joomla and WordPress servers, he says.
The lesson for enterprises is that the DDoS protections they have in place need to be tweaked to handle higher attack volumes, he says.
IoT exploited
The massive Krebs on Security assault is the work of a botnet made up primarily of internet of things devices, according to Akamai. So many devices were used, in fact, that the attacker didn’t have to employ common tactics that amplify the impact of individual devices, Ellis says.
The number of machines in the latest botnet is still unknown, and could be as large as a million. “We’re still trying to size it,” he says. “We think that might be an overestimate but it’s also possible that will be a real estimate once we get into the numbers.”
With estimates of 21 billion IoT devices by 2020, the scale of botnets that might be created by these relatively unprotected machines could be enormous, says Dave Lewis, a global security advocate for Akamai who spoke Thursday at the Security of Things Forum in Cambridge, Mass.
“What if an attacker injects code into devices to create a Fitbit botnet?” he says. Researchers have already shown it’s possible to wirelessly load malware onto a Fitbit in less than 10 seconds, he says, so the possibility isn’t fantastic.
Some of the attacking machines are running clients known to run on cameras, he says. “It’s possible they are faking it or it’s possible it’s a camera that was doing these attacks,” he says. “There are indicators that there are IoT devices here, at scale”
The attack didn’t use reflection or amplification, so all the traffic consisted of legitimate http requests to overwhelm Krebs’s site, Ellis says. “It’s not junk traffic.”
A lot of things about the attack are still unknown such as who’s behind it and what method the botmasters used to infect the individual bots.
Ellis says some other providers Akamai had contacted report similar but smaller attacks likely from the same botnet. Many of them were aimed toward gaming sites, and Krebs has written about such attacks, so there may be a connection there, he says.
 Akamai will analyze the attack and devise tools to fight similar attacks, Ellis says.
Akamai will analyze the attack and devise tools to fight similar attacks, Ellis says.
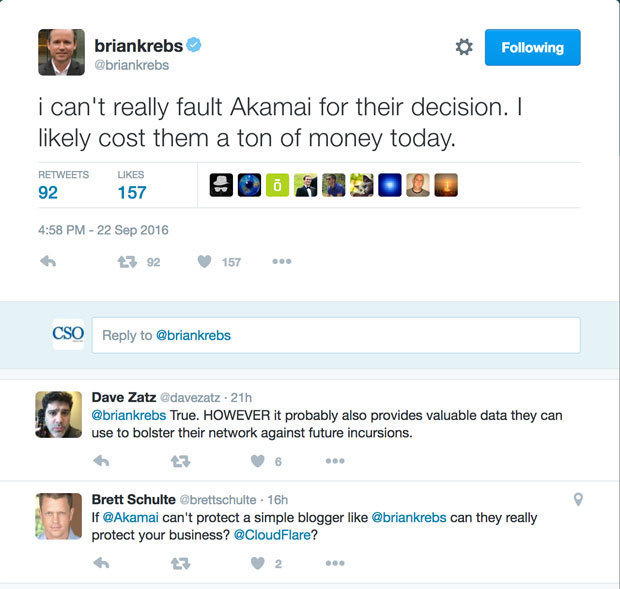
Krebs has tweeted about the attack after Akamai stopped protecting his site. “I can’t really fault Akamai for their decision. I likely cost them a ton of money today,” he wrote. “So long everyone. It’s been real.”