I get this question often. Network security professionals or general security advocates within an organization can rattle on about security best practices for securing a network or endpoint but sometimes have difficulty speaking to securing cloud environments. It isn’t any more complex, but it is slightly different. The good news is all of the general security concepts such as defense in depth, least privilege access, continuous monitoring of all assets, baselining and so on all still apply. You just need to convert your understanding of traditional security tools into a cloud environment.
Note: I’ll use Microsoft’s tools as the template, however, focus on the capabilities being used and how they tie together to understand the overall concept of securing a cloud.
I’ll break securing a cloud (infrastructure as a service (IaaS) AND private cloud) into three parts, which are Configuration, Enforcement and Monitoring. I’ll start with configuration, which needs to be a centralized management platform. This isn’t a SIEM/SOAR/XDR solution as that is focused on Monitoring and responding to threats (examples are Splunk, Logrhythm or Microsoft Sentinel). You don’t use an XDR solution to configure a server, right? You do want an XDR solution, but save that thought for Monitoring.
Let’s focus on managing security Configuration within a cloud environment. I’ll use Microsoft Defender for Cloud acting as that central place to configure security for my example, but the general idea is having a place to do the following:
- Monitor configuration across all workloads. You need to monitor across on-premises and cloud rather than having two separate solutions. Most organizations also need to consider hybrid cloud meaning support between Azure, Amazon and Google.
- Monitoring of security capabilities such as firewall, workload defense, application behavior monitoring / baselining and data loss prevention both at rest and in motion. These settings are what is part of a security template that is deployed.
- Automate applying security settings such as hardening against best practices. Bonus capability: offering best practices as templates to simplify creating a security baseline for what is considered a secure build along with the ability to adapt that template to your environment.
- Offer easy to use forensic tools to detect and analyze potential attack behavior when events occur (or data that an XDR can use to accomplish these goals.
- Visibility into how licensing and cloud consumption is being used
- Asset monitoring and enforcement for the types of servers, databases and applications used.
There are different ways to accomplish goals for cloud security capabilities. One approach is loading a ton of tools such as a EDR for host threats, agent for vulnerability management, agent for network access control, agent for identity, agent for configuration enforcement, and so on and so on … then deploy a bunch of virtualized security tools and route traffic through them … then push all of that do an XDR solution with hopes that within the noise you will be able to identify and respond to threats. I’ve seen some organizations led by old school security advisors develop this approach in the cloud, which is extremely inefficient and costly. They ask a network vendor to virtualize their network tools or deploy agents on every server to gain visibility into cloud environments. It gets really messy quickly.
A better approach would be to leverage cloud and server native capabilities, fill gaps with 3rd party security tools and validate support of 3rd party tools within the centralized security platform. Every organization I speak with is trying to be more effective with what they already own and the major cloud providers (AWS, Azure and Google) all offer a ton of native security capabilities you should be considering before adding more security tools to your SOC. The same concept applies to server, host and database providers such as Apple and Microsoft.
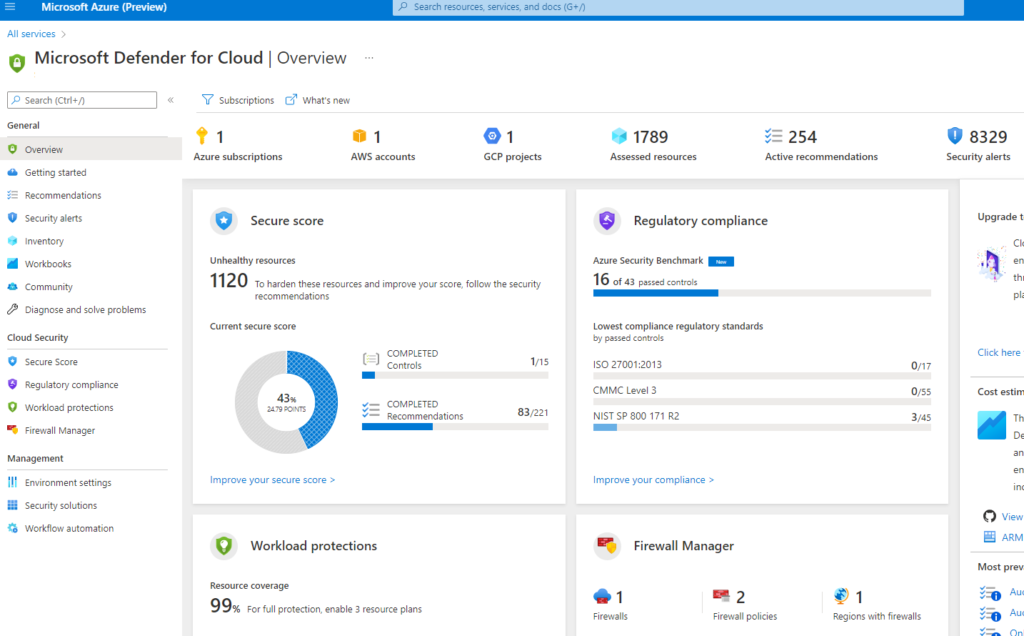
Using Microsoft as an example, the following image is the Microsoft Defender for Cloud dashboard highlighting how secure the environment is compared against security best practices, compliance monitoring, workload defense monitoring, firewall monitoring and not shown are panels for Inventory monitoring and Information protection (data loss). Many of the capabilities being used are native to Azure and Windows reducing the need for agents and additional virtualized security tools.
Configuring strong security is important but another critical practice part of Configuration that needs to be enforced is ensuing security in maintained. The days of periodic assessments are obsolete based on how quickly a vulnerability can be exploited. This means step two to secure a cloud is Enforcement of best practices. The biggest challenge is you can’t just pick a few static security templates and assume they are “best practices” for your environment now and in the future. We all love guidelines from NIST and ISO however, those need to be adjusted based on the current state of your environment. Stating you want all systems to always meet a static guideline just won’t work in a dynamic cloud environment. The required exceptions will continuously increase risk of compromise.
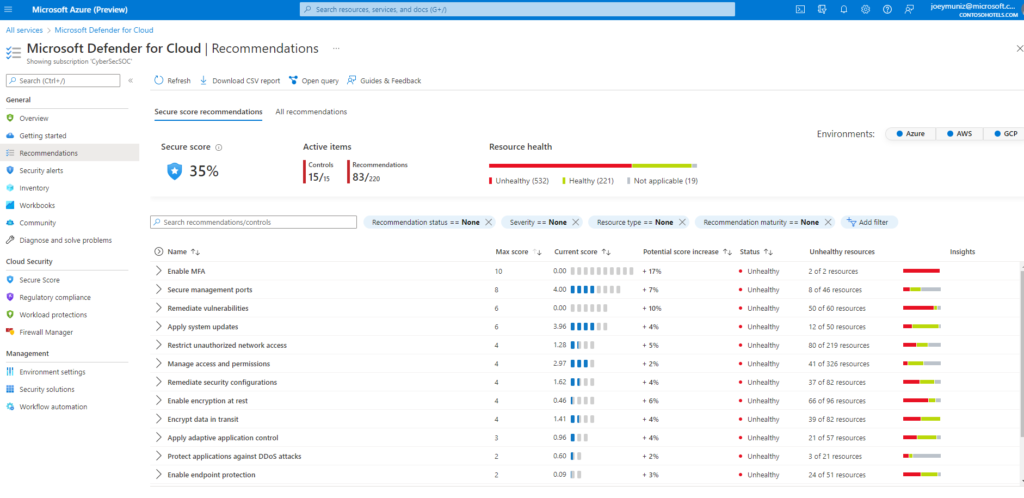
Looking back at the Microsoft Defender for cloud example, you can apply configuration hardening recommendations from Microsoft that takes your existing configuration, network and systems into account as best practices are being pulled from popular resources (NIST, ISO, etc.) and adjusted based on the current state of your environment. You can configure how best practices are enforced such as auto fixing configuration outside of required settings, lock down what can be delivered and create a store for servers that are already configured using the recommended security settings. The next image shows Microsoft Defender showing various recommendations for securing assets within Azure, AWS and Google.
Another aspect of enforcement is role-based access controls (RBAC). Security guidelines will state cloud services should by default be set to deny all access, which is how cloud providers provision their services. You have to configure what can access or leave a network segment and what can communicate with the outside world. You also have VPN options for protecting how administrators and users can connect to cloud services in a secure manner. Essentially, you need to create your access control, firewall and segmentation policies. All of the major cloud providers offer these capabilities natively. For Microsoft, services to accomplish RBAC include Azure Active Directory, Multi-factor Authentication, Azure Password Protection, Azure AD risky Sign-ins, Azure Risky users, Application security groups and Azure AD identity Security Score to name a few available settings.
Note: Some compliance requirements may include isolated servers or ensuring data remains within a country commonly referred to as data sovereignty requirements. The major cloud providers offer dedicated systems (example Azure Dedicated Host) at a higher cost to meet this requirement.
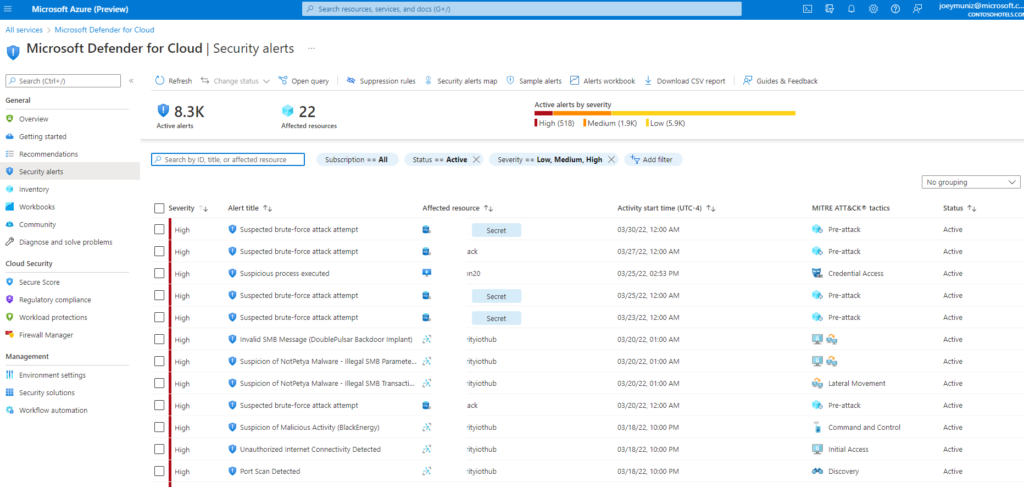
Once your cloud is configured in a secure manner and enforcement is in place, the 3rd and final step to secure a cloud is reviewing how the security operation center will protect it. This is where the XDR conversation comes into play. I posted about Microsoft Sentinel HERE to learn more about XDR concepts IE what a SIEM, SOAR, threat hunting, EDR/XDR and other SOC terms mean. The key is ensuring your XDR solution can work with all of your cloud security capabilities to avoid blind spots in monitoring. Most major XDR solution providers support the three major cloud provider security configuration dashboards such as support for Microsoft Defender for cloud. The following is the threat data from Microsoft Defender for Cloud that would be useful to export to your XDR solution.
That is a very high-level breakdown of steps to secure a cloud environment. I defined cloud in this post as on premise (private cloud) and infrastructure as a service (IaaS) but did not include software as a service (SaaS) since the responsibility for most security configuration is outsourced to the service provider.
(Note: I say MOST because you will have some responsibilities for securing SaaS and tools like a cloud access security broker (CASB) or multifactor authentication are available to increase security.)
Hopefully this writeup helps demystify securing the cloud.