I posted about the Ashley Madison breach HERE. For those that are not following this, Ashley Madison, the popular affair website was breached by a group calling themselves The Impact Team. They threaten to leak customer records if Ashley Madison didn’t shutdown their website. Ashley Madison is still up and the deadline has passed so The Impact Team posted access to all 30 million customer records. My buddy Aamir aka Dr Chaos summed up the current state of this situation. His post can be found HERE.
Hackers attacked Ashley Madison (known as AM by its users), the dating site for married couples that promotes infidelity. They walked away with 30 million records containing site user information. While the initial ramifications seem obvious, the story continues to unfold with recent news that email addresses were discovered that originated from government agencies, high level politicians, and certain celebrities. The data represents a treasure trove of sensitive and extremely private data that has a high potential for causing damage to individuals.
Back to the main story – the hackers tried to blackmail the site’s parent company, claiming they’d release customer names to the public if the company didn’t shut down Ashley Madison and another site it owns called Established Men.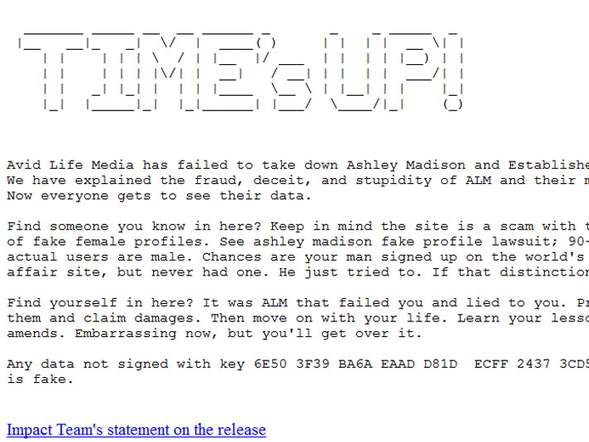
The attack represents a type of hactivism, and currently appears to be based on a strong ethical ideology. The only demand by the hacker group (called The Impact Team) was a closure of the two sites. They threatened to release the personal data if this was not done. The group’s enforcement of their morals appears to be the primary reason for their release of data instead of financial gain or other motivators.
The hackers have now released the information in a database that is posted on the Web. The actual data is located in a 10Gb compressed file. For those of you unfamiliar, this is a massive repository.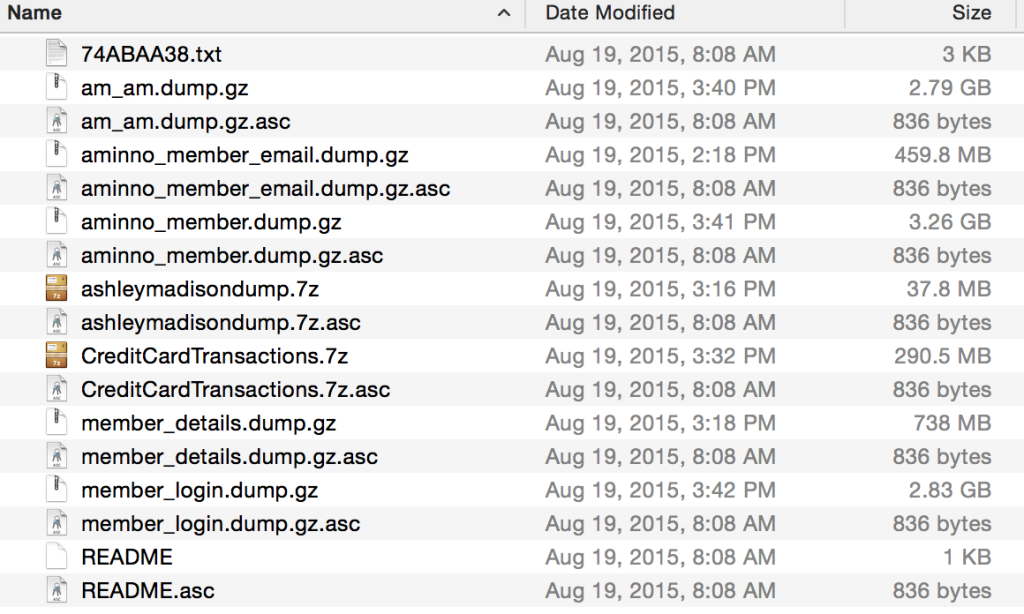 The database contains usernames, passwords, credit card data (only the last four digits), street address, full names, and profile information. Additionally, there seems to be some limited PayPal account data included in the repository as well.
The database contains usernames, passwords, credit card data (only the last four digits), street address, full names, and profile information. Additionally, there seems to be some limited PayPal account data included in the repository as well. It is difficult to say how long it will take individuals and organizations to sort through the data, and how that data will ultimately be used. There is the real threat of information being leveraged in divorce cases or other civil proceedings. I think the situation was best summed up by Andrew H. Scott in his Tweet which stated, “Lol. We’re going to need bigger courthouse.” Andrew is the mayor of Coal Run, Kentucky.
It is difficult to say how long it will take individuals and organizations to sort through the data, and how that data will ultimately be used. There is the real threat of information being leveraged in divorce cases or other civil proceedings. I think the situation was best summed up by Andrew H. Scott in his Tweet which stated, “Lol. We’re going to need bigger courthouse.” Andrew is the mayor of Coal Run, Kentucky.
I am sure there is a percentage of individuals in the hacker community who feel this was a positive thing, and that the hackers were simply fighting to somehow improve the overall morality of society. There is also the consideration of this act forcing individual or group values on the broader population. While on some level this violates individual rights to privacy, the argument of accountability, open information, and other peripheral factors of information availability will be debated long after I am gone.
The sad fact is this is effecting people in very real ways. As much as we might want to joke about the attack, people who don’t understand technology may be overreacting. I am not going to preach, but being understanding goes a long way for everyone.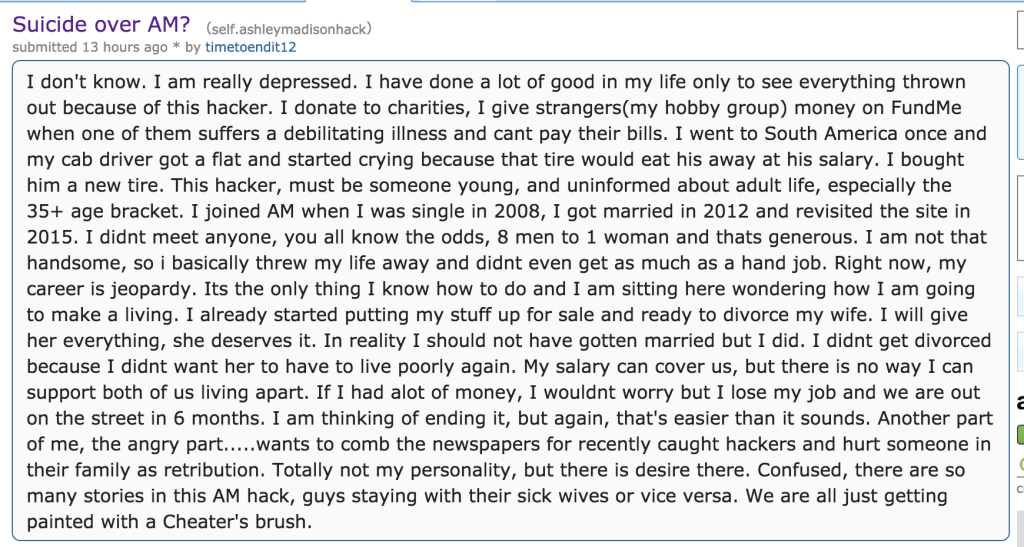
A major consideration of this situation is one of accuracy when tying people to the posted information. Attribution may actually be extremely difficult due to the inability to verify that the information is linkable to individuals or even accurate at all. Ashley Madison did not verify email addresses or physical addresses, so the reality is that many of them could simply be fake. One Ashley Madison user registered to the site using Tony Blair’s information, who is the former Prime Minister of the United Kingdom. It could have been anyone using his credentials when the user profile was created.
So the real question is this…how reliable is the data? Ashley Madison never confirmed anything as accurate. However, there are some ways of increasing the likelihood of accuracy when trying to determine if an individual was actually in the Ashley Madison site as a user. For instance, credit cards have a certain probability of linking directly to individuals, as do addresses, phone numbers and other information. A credit card number provides a higher degree of certainty, while public information, such as addresses or phone numbers, simply do not provide a similar level of proof of involvement.
In the security community we would say attribution is extremely difficult in this situation. But even within that community there is difference of opinion. According to an article on CNET.com, “The Company has verified it’s been hacked, and security researcher Brian Krebs has confirmed that some of the user information is accurate. But Stu Sjouwerman, chief executive of security company KnowBe4, said there are probably a few million fake accounts in there.” (see http://www.cnet.com/news/you-can-look-but-ashley-madison-information-is-hard-to-verify/)
I have spoken to more than dozen reliable sources that have claimed to use Ashley Madison, and I have found their information in the data repository. It is real, but probably has lots of fake information.
It was actually difficult to find them, even when provided specific items to search out. The data repository has multiple files that are sorted by PayPal accounts, member logins, and member data. In some cases I only found email addresses. Sometimes I found full member details including information they had on their profile. I even found some communication strings between certain members.
As I said, this information was not easy to find. In some instances I only knew what to look for because my sources had given me their profile numbers or email addresses. If you used a burner email address and did not use PayPal or a credit card, there is a possibility you might have little concern over this entire situation. For those of you that do not know, a burner email account is one you intend to delete at some point in time or after a specific use.
There is also the consideration that many people were drawn to Ashley Madison to find out what the buzz was about, and consequently signed up without ever using the service. Having user data in Ashley Madison data does not prove intent or even desire to be associated with the site. Some users could have been curious, signed up, looked, and simply walked away from it.
One side bit of humor appears to be coming out of this mess. It seems like Ashley Madison may have not been living up to the boy-meets-girl expectations of their customer base. On a very simple and quick glance, it appears the vast majority of the users are male. Okay…not that surprising when you think about how the world of the Web works.