One situation that comes up every once in a while is the request to use an application layer firewall to decrypt SSL traffic. Usually this is for monitoring and reporting purposes however sometimes it is concerns of attacks happening over encrypted channels that bypass IPS detection and firewall capabilities meaning a user accessing a malicious source over HTTPS. The reality of it is attackers would have to use certificates, which would give away information that they typically don’t want to do. This attack vector is uncommon but a possible risk to consider.
The challenge to decrypt SSL on an application layer firewall is it substantially increases the traffic load impacting performance of the security solution. Think of a 1 Gig pipe transforming into a 5 Gig pipe while the hardware passing the traffic is sized for 1 Gig to get an idea of what is going on. One common work around is using selective decryption but even that sometimes only slightly lightens the impact.
Application layer firewall vendors that claim they don’t experience an impact when enabling SSL decryption are either not really decrypting everything or there is another element being removed to make it seem true. The reality is this is an industry challenge for application layer firewall solutions. NSS labs wrote about this a while back HERE.
The best approach to accommodate SSL decryption is to either properly size the application layer firewall when SSL is enabled (assuming the capability is available) or use a dedicated solution for SSL. Many vendors will quickly increase in size and price as the SSL throughput requirements increases sometimes making the final option financially unobtainable. Sometimes considering combining a dedicated SSL solution with the application firewall comes out to less than half of the cost to size up. Obviously pricing and sizing are all very flexible topics however in the end there are times a dedicated SSL appliance is the best option.
There are a handful of vendors in the SSL decryption space. I got to spend some time with one of them, A10 at Cisco live two weeks ago. A10 provided a white paper on their SSL Thunder SSI with Cisco FirePOWER found HERE and demo. Here is a brief overview of the A10 Thunder SSLi offering that compliments an Cisco FirePOWER with SSL decryption requirement.
The first thing to understand is the FirePOWER inline deployment pre SSL enabled. It could look something like this diagram showing traffic passing through the FirePOWER solution.
 The concern is when a client connects to an infected site and establishes a trusted encrypted channel between the host and malicious source as shown. The thought is attacks would happen over a encrypted channel rendering the security solution useless.
The concern is when a client connects to an infected site and establishes a trusted encrypted channel between the host and malicious source as shown. The thought is attacks would happen over a encrypted channel rendering the security solution useless.
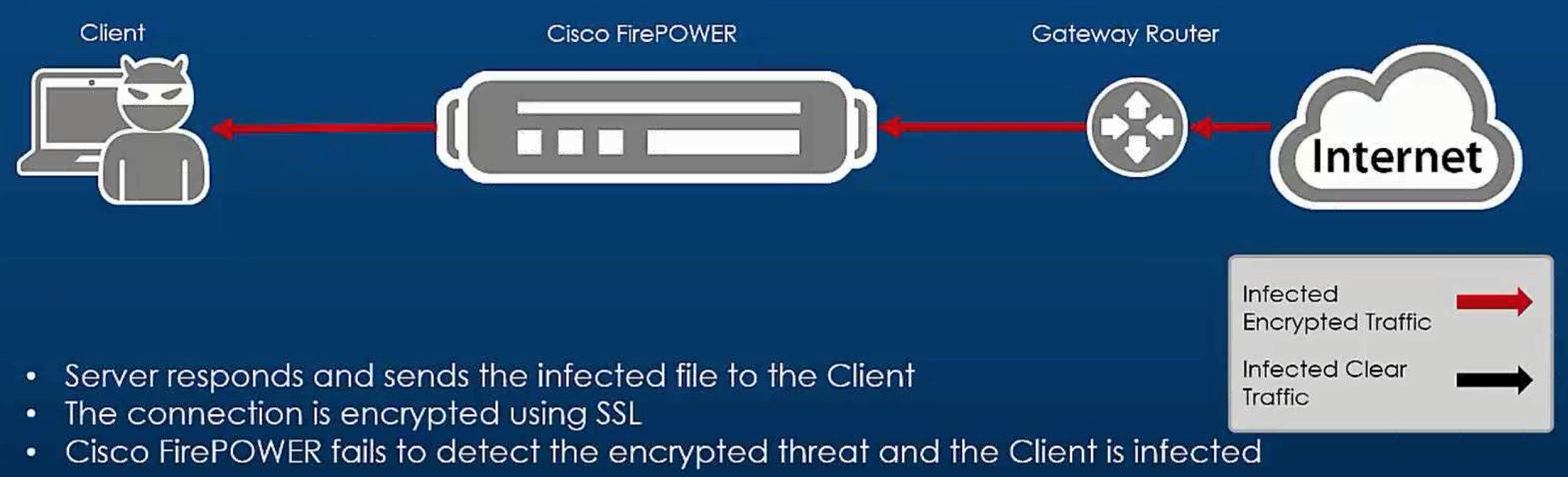 Now the reality of this attack for Cisco is the following. Cisco solutions such as FirePOWER first check the risk or “credit score” of a web source prior to establishing a SSL session if the URL license is enabled with proper configuration. Also having Cisco FireAMP enabled would check to see what came through regardless if the communication channel is encrypted. The concern would be the IPS detection not being able to see into the encrypted channel hence unable to block exploitation of a vulnerability on the host.
Now the reality of this attack for Cisco is the following. Cisco solutions such as FirePOWER first check the risk or “credit score” of a web source prior to establishing a SSL session if the URL license is enabled with proper configuration. Also having Cisco FireAMP enabled would check to see what came through regardless if the communication channel is encrypted. The concern would be the IPS detection not being able to see into the encrypted channel hence unable to block exploitation of a vulnerability on the host.
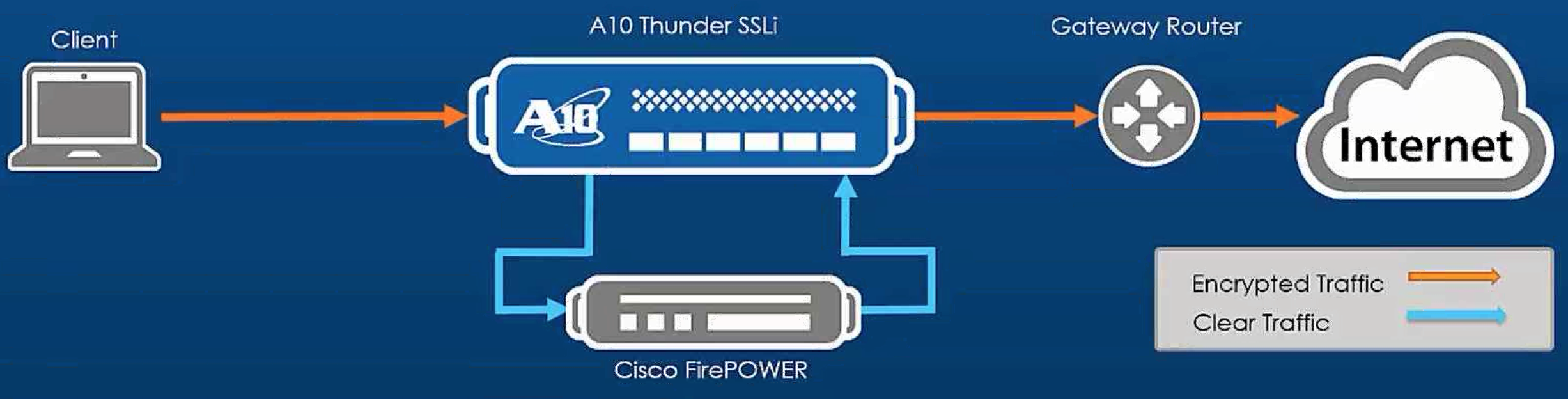
Cisco FirePOWER can decrypt SSL but at a performance cost. If that cost seems to be out of budget, another option would be using an A10 Thunder SSLi as the SSL decryption solution passing the unencrypted traffic through the Cisco FirePOWER solution for full security evaluation. Other technologies can also send unencrypted traffic as needed making the A10 option a very flexible alternative as shown.
 To get a quick overview of the A10Thunder SSLi appliance, lets start by accessing the web GUI.
To get a quick overview of the A10Thunder SSLi appliance, lets start by accessing the web GUI.
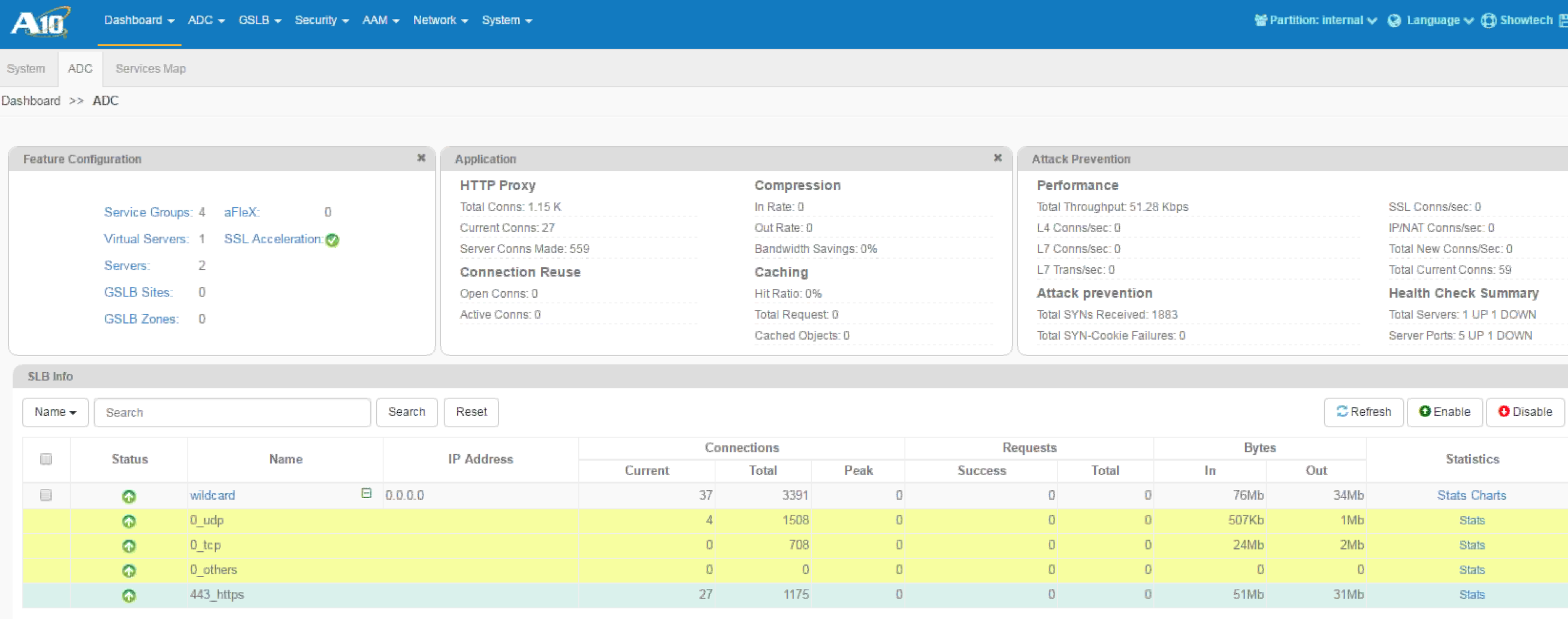
 Once you log in, you will see the dashboard showcasing standard information such as performance, what is being utilized, etc.
Once you log in, you will see the dashboard showcasing standard information such as performance, what is being utilized, etc.
 The setup is pretty straightforward. The FirePOWER solution is configured in bridge mode providing two GE interfaces configured in a security zone. One interface is configured as the outside in the outside security zone while the other is the inside interface configured for the inside security zone. Then an access control policy is set to send all users, zones and destination ports allowed through the A10 solution.
The setup is pretty straightforward. The FirePOWER solution is configured in bridge mode providing two GE interfaces configured in a security zone. One interface is configured as the outside in the outside security zone while the other is the inside interface configured for the inside security zone. Then an access control policy is set to send all users, zones and destination ports allowed through the A10 solution.
 The A10 Thunder SSLi offering will require a certificate to avoid being seen as a man-in-the-middle attack, which would be required for any SSL decryption option including Cisco FirePOWER. Once setup properly, traffic will flow through the A10 offering to be unencrypted and scanned by the Cisco FirePOWER solution before going back out the A10 solution in an encrypted format. This permits FirePOWER to leverage its full capabilities IE the IPS scanning of the unencrypted traffic for threats.
The A10 Thunder SSLi offering will require a certificate to avoid being seen as a man-in-the-middle attack, which would be required for any SSL decryption option including Cisco FirePOWER. Once setup properly, traffic will flow through the A10 offering to be unencrypted and scanned by the Cisco FirePOWER solution before going back out the A10 solution in an encrypted format. This permits FirePOWER to leverage its full capabilities IE the IPS scanning of the unencrypted traffic for threats.
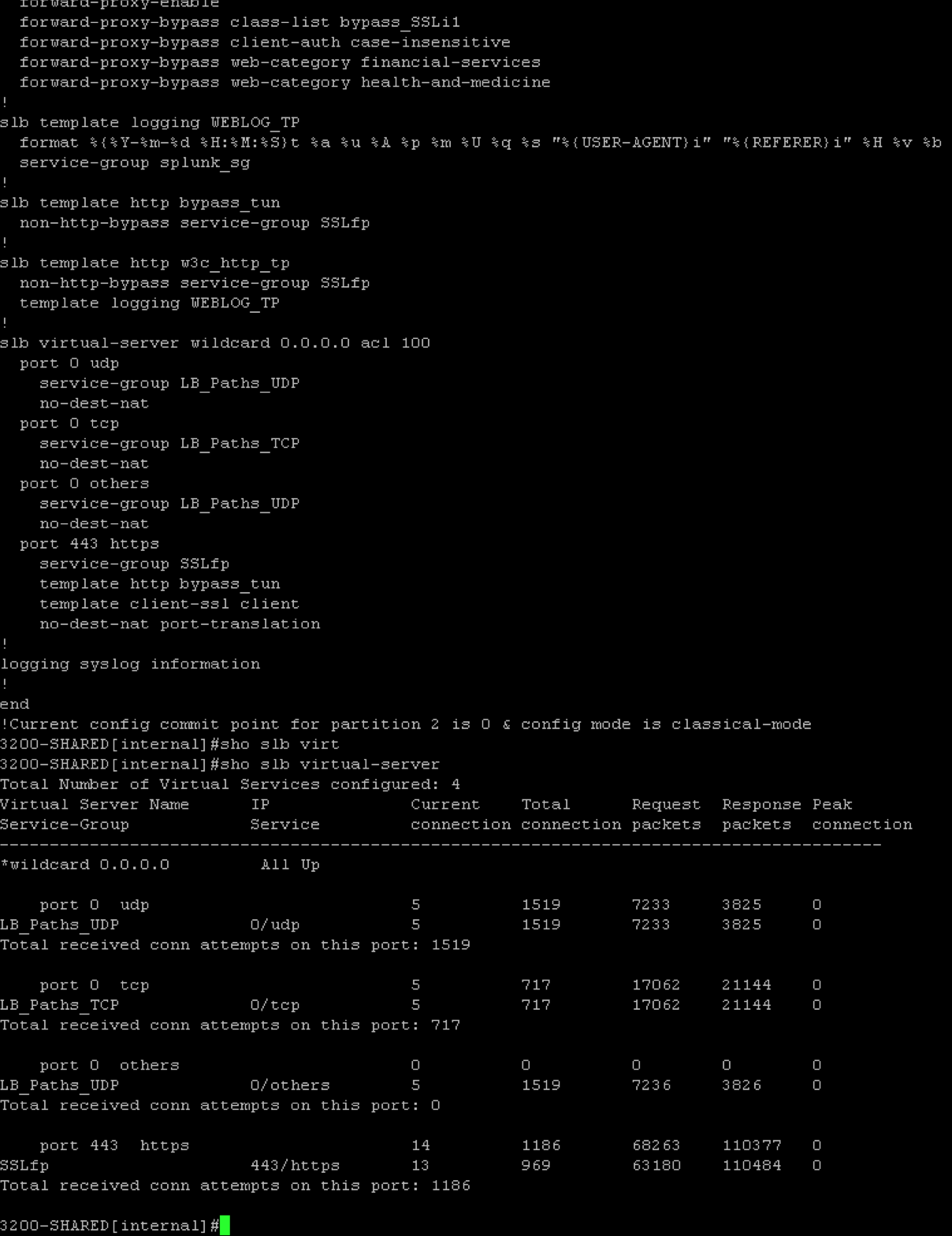
The entire thing can also be configured using the A10 command line which is surprisingly similar to Cisco IOS.
 This is a quick summary of how A10’s Thunder SSLi’s solution can be a possible option for addressing large SSL decryption requirements. Yes, Cisco FirePOWER can perform SSL decryption however at a performance cost. A10 provides another option if sizing up is not an option.
This is a quick summary of how A10’s Thunder SSLi’s solution can be a possible option for addressing large SSL decryption requirements. Yes, Cisco FirePOWER can perform SSL decryption however at a performance cost. A10 provides another option if sizing up is not an option.




