I finally received a brand new ASA5506 and thought I would share my experience along with the new FirePOWER ASDM GUI. For those that are not aware of this release or the ASA series, the history goes like this. Cisco released the VPN concentrator and PIX firewall a long time ago. Eventually those technologies were consolidated into the Adaptive Security Appliance (ASA) series of appliances. The smallest 1st generation ASA is the 5505 that has been around for a long time and designed for small offices or home networks (shown in the above picture on the right). Cisco released a new line of ASA appliances known as the X series however didn’t release a replacement for the 5505 until this past March. That replacement is the ASA5506 (the black appliance on the left).
The value of the 5506 compared to the 5505 is it can run the new FirePOWER technology just like all other versions of ASAx series appliances (more on that HERE). FirePOWER gives you Application Visibility and Control, Enterprise level IPS, URL filtering and end to end breach detection from network to endpoint. You also don’t have to buy any physical models like the first generation of ASA hardware since the X series has a virtual space that hosts these new features. This is similar to hosting virtual systems within hardware. Details on the ASA5506 and the rest of the ASAx series can be found HERE.
NOTE: The major new feature with this platform release is ASDM can manage certain FirePOWER features so you don’t have to own FireSIGHT management center. I’ll show the new ASDM interface in this post.
So the first thing I did after unboxing the 5506 was compare it to the 5505. As you can see from the pictures, the 5506 is slightly longer and “batman” black as I like to call its color. It does not have a fan so it’s silent when powered up. The power adapter is different from the 5505 however it takes a standard power cable so at least you don’t need that funky three prong power cable anymore. The next images show comparing a 5505 and 5506 power adapter. The 5506 is the white end one. The power cable is standard stuff.


Next I powered it up. Its crazy how quite it is. After a minute or two I plugged in a console cable and configured the 5506 for my network. Here is a youtube video covering the basic steps to configured a ASA using command line so you can access the GUI management known as ASDM found HERE. For my deployment, I’m going transparent mode so my ASA with FirerPOWER can act as a security assessment tool reading data off of a SPAN port. This means my management interface will have a IP address however the interface monitoring traffic from a SPAN port will use the following commands.
- interface gigbit1/1
- no nameif
- traffic-forward sfr monitor-only
- no shut
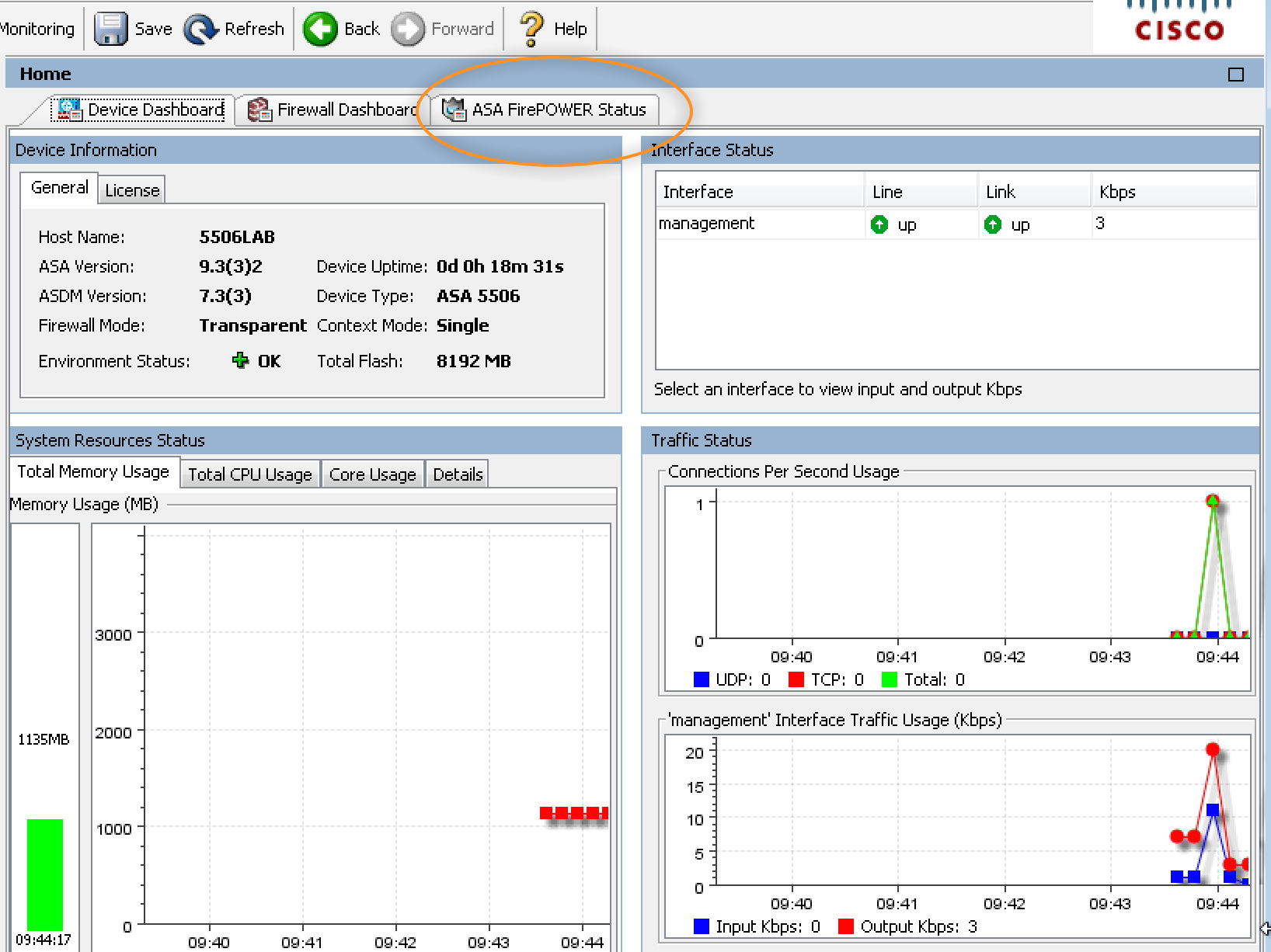
Once inside ASDM, I noticed the interface is similar to the previous versions however the FirePOWER service tab is already there and ready to be accessed.
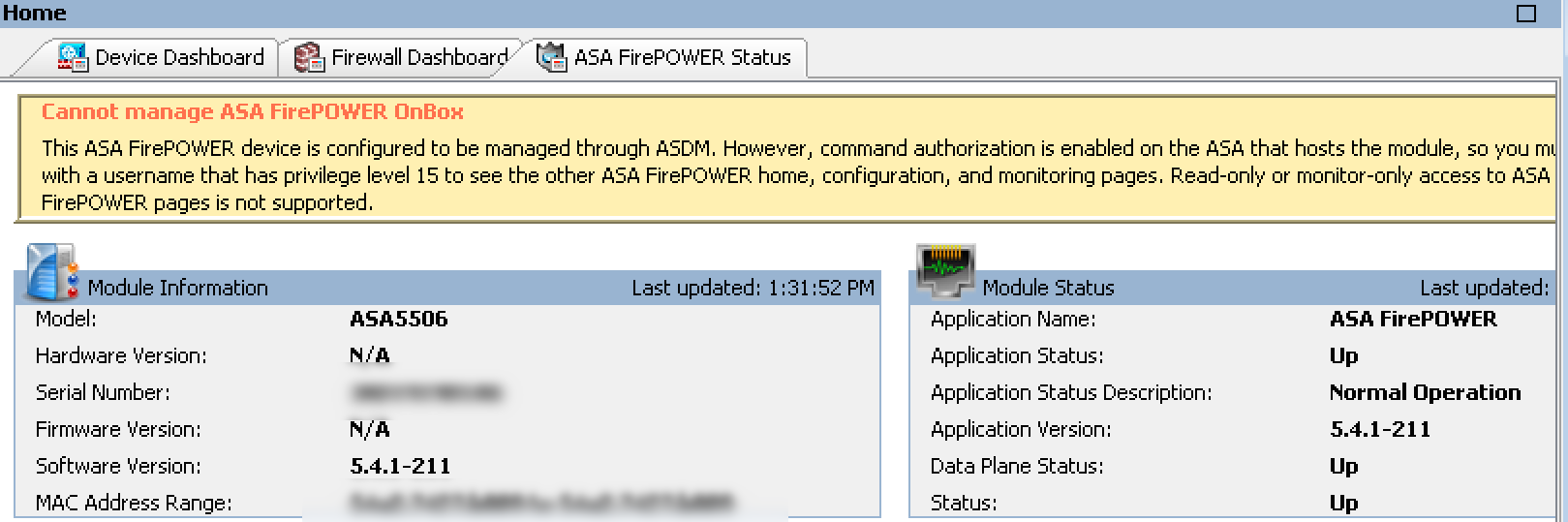
When I click the tab, I see the following warning message stating I need to either configure the FirePOWER system locally or use a external manager.
Before messing with FirePOWER, I went ahead and used the ASDM upgrade wizard to upgrade to the latest 9.3.3 ASA version and ASDM 7.4. This took about 5 minutes to complete including the reboot.
Next I want to enable FirePOWER. From the command line I can type session sfr to bring up the FirePOWER module that runs inside the ASA. It has its own command line, CPU, etc. and is already installed but needs to be configured. The login for the ASA5506 FP is username admin and password Sourcefire. Once inside, a wizard walks me through the basic network setup of the sourcefire model. Once complete, when I look back at ASDM, the FirePOWER tabs appear but I’m not seeing data yet.
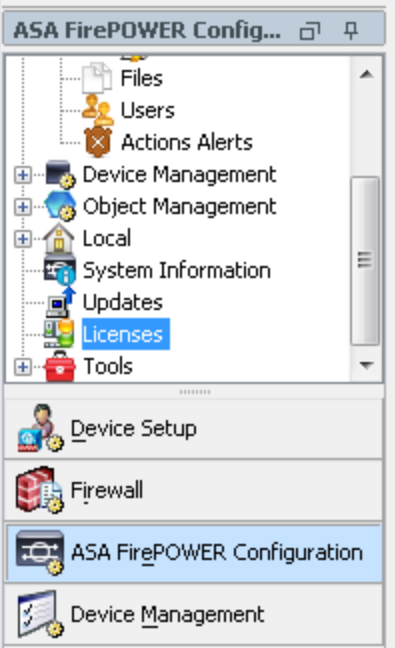
Next I need to license the FirePOWER features. I find this by going under configuration and selecting Licenses. I can apply licenses just like when licensing a FirePOWER appliance using the FireSIGHT manager but from ASDM. I applied a URL and AMP license. All configuration options for the FirePOWER features are found on the left tab titled ASA FirePOWER configuration.
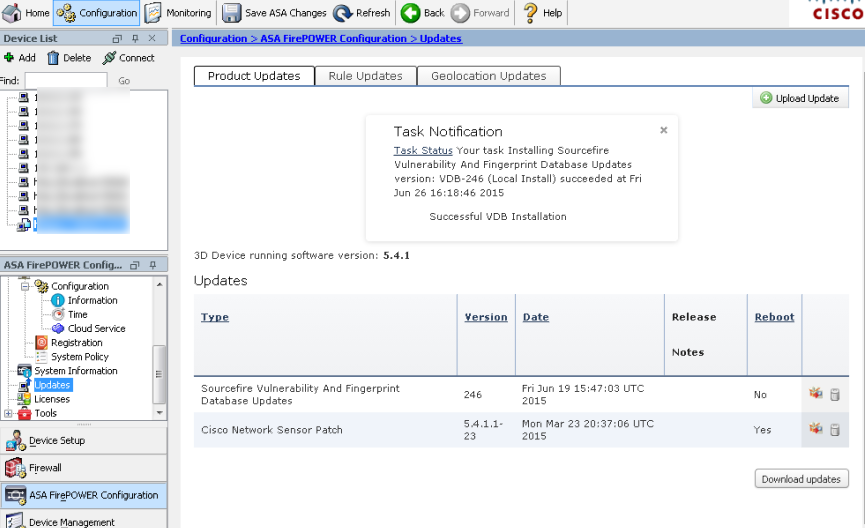
Next I can click updates and apply all updates to the system. For those that are familiar with configuring FirePOWER using FireSIGHT manager, this should very familiar. I can see the tasks as it updates the signatures, geo location and system update from 5.4.0 to 5.4.1 by clicking the Task Status link. The 5.4.1 update took about 40 mins to complete.
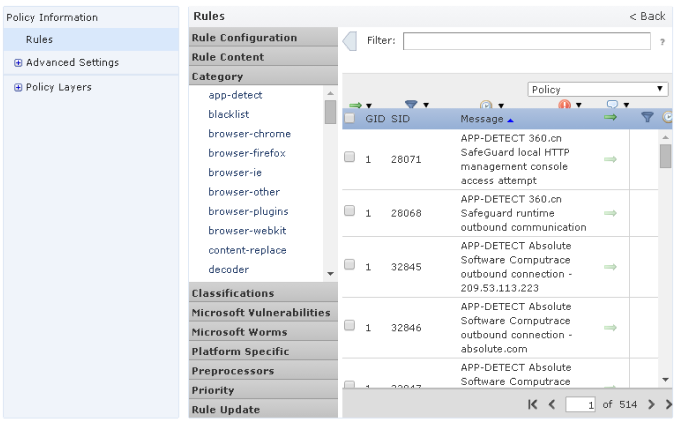
From here I can setup a URL policy to block or monitor websites, a IPS policy to look for threats and File policy to look for day zero breaches on my network. The next screenshot shows the IPS configuration listing thousands of IPS rules. I tuned mine for things like Malware, botnets, etc. Again those familiar with configuring FireSIGHT will see this is very similar looking. This is a enterprise level IPS with many tuning options.
The file policies are for what goes to the cloud and what is looked at locally for day zero detection. This means every file seen by my ASA will be giving a hash and evaluated through the cloud and locally for malicious behavior.
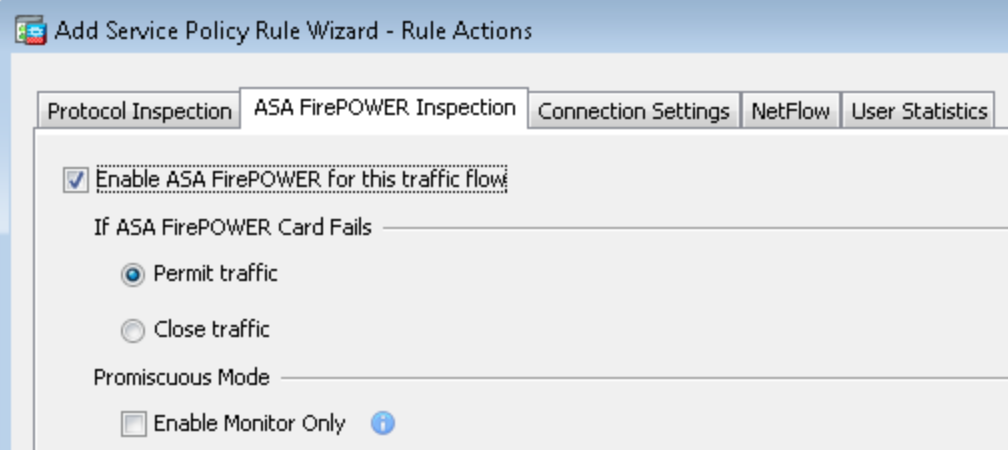
I went ahead and set it up to monitor for any adult, gambling, hate and a few other website categories. I also tuned it to know what is my internal network verses outside networks. Once my policies were setup, the last step was setting up the ASA to use a policy map to send traffic from the ASA through the FirePOWER solution. This is done by creating a global policy map, selecting all traffic, click the ASA FirePOWER Inspection tab and enabling the traffic flow through the FirePOWER function. Notice you can set it to fail open or closed.
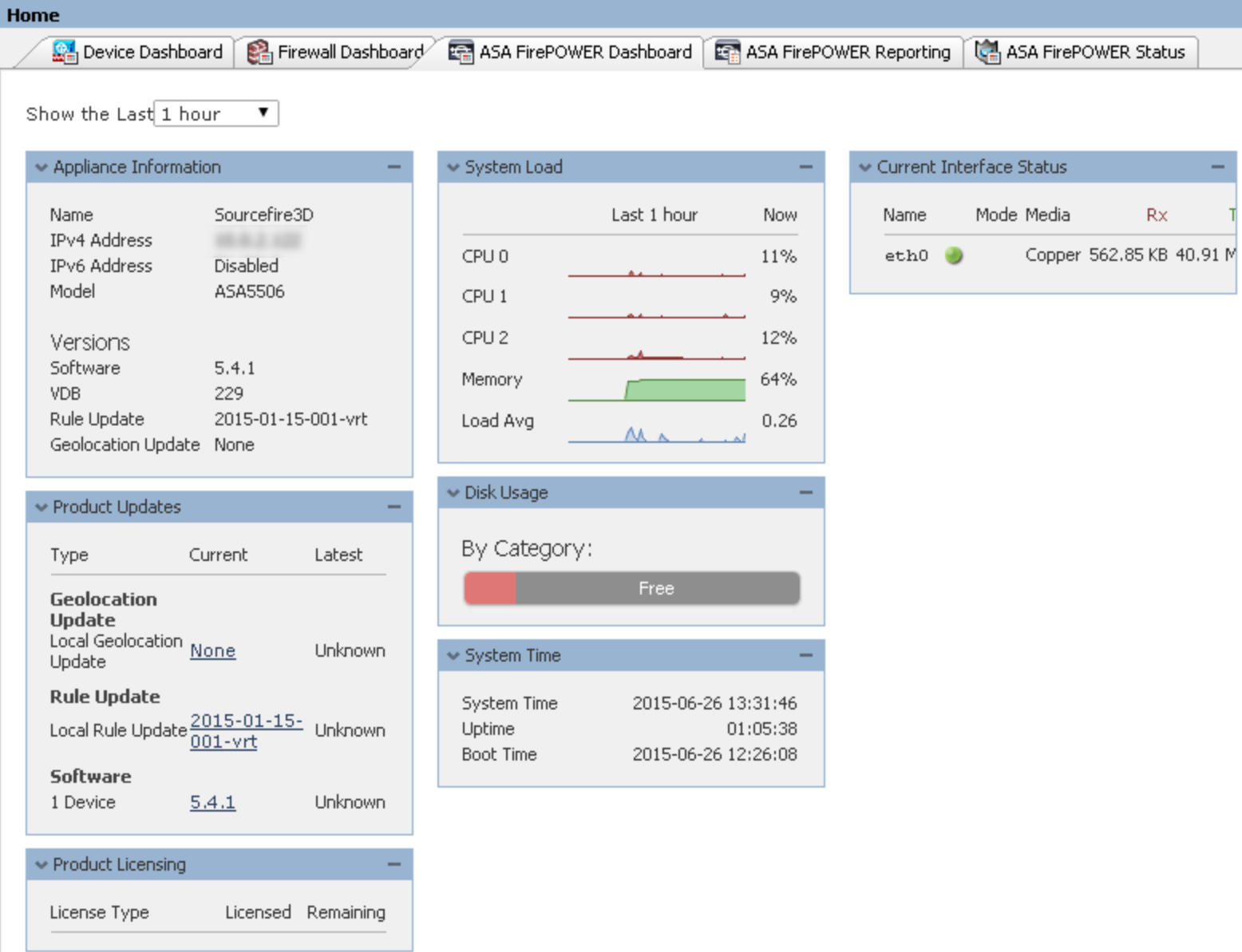
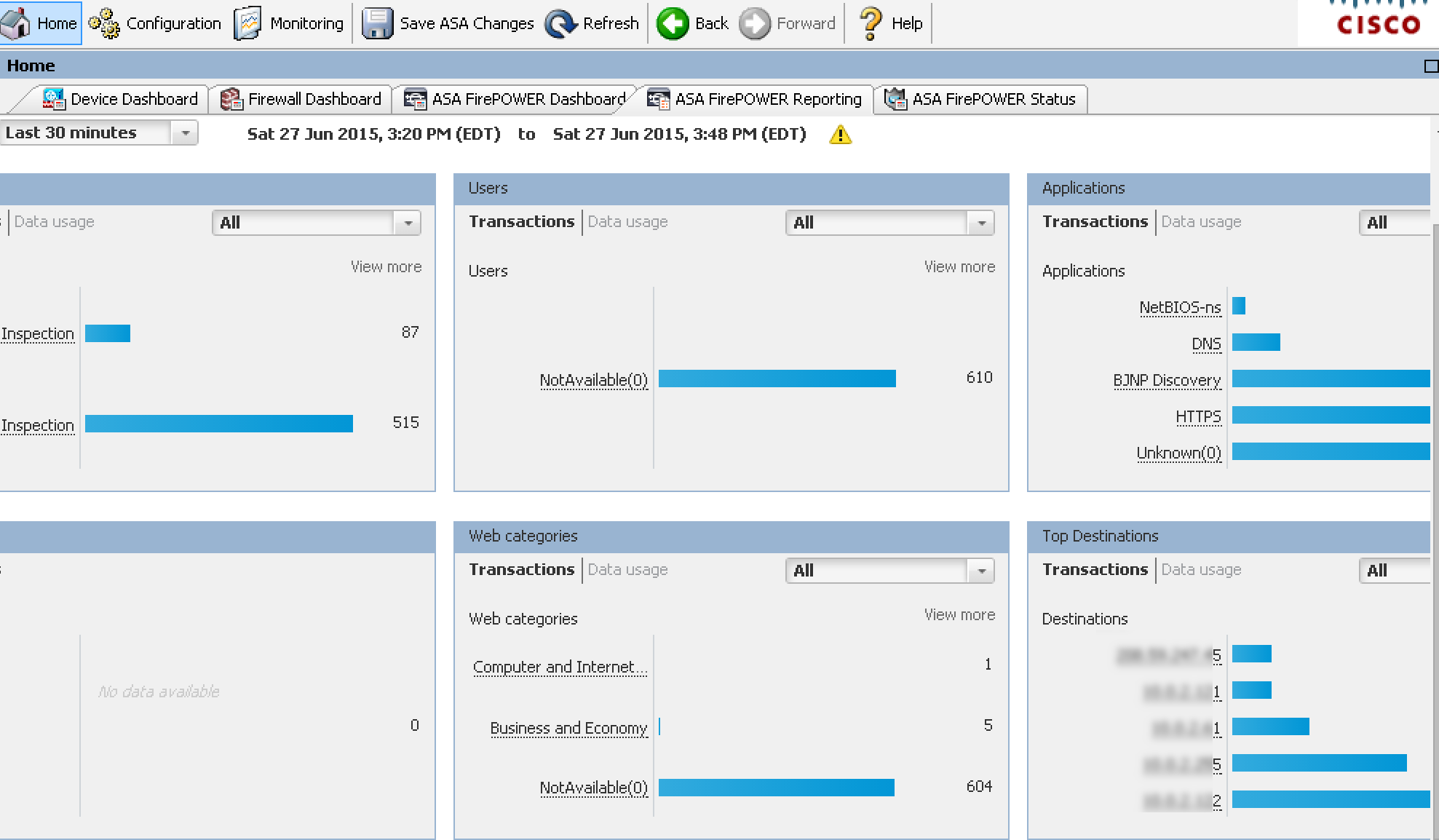
Once traffic is flowing, I can go back to the main ASDM dashboard and check out the traffic being seen by my ASA 5506 running FirePOWER as a transparent network tap. Pretty cool stuff. The next screenshot is using the ASDM FirePOWER dashboard to get an idea of what type of traffic is being seen on my network after running for a few minutes.






thanks for the writeup. overall it’s an excellent piece of kit, save for one glaring detail: those 8 gig ports are all layer-3. unlike the venerable 5505, the 5506-X has no layer-2 switching.
This is true. The 5506 also doesn’t have PoE. So there are pros and cons for upgrading however the FirePOWER stuff is a pretty good reason to consider these new appliances.
Hi,
Is there any way to generate report from Asdm, about firepower?
Tks
Hi,
Today there is limited reporting with the first version of FirePOWER on ASDM via local management. The centralized FireSIGHT manager offers much more detailed reporting that can be automated to export in various formats. ASDM does have a lot of the FirePOWER data in real time but exporting reports is limited with the first ASDM FirePOWER release.
I have a question: Does the Firepower software working on the 5506 have the same features, configuration menus, functionality etc as the Firepower software on bigger ASA models (e.g 5525X etc)? so if I buy a 5506 and learn the Firepower configuration, it will be exactly the same as Firepower on bigger ASA models?
Thanks for your time
In regards to the FirePOWER features (Content Filter, Application Layer Firewall, IPS/IDS and Network Dayzero), yes the 5506 up to the 5585 are the same. The 5506 as a ASA firewall without FirePOWER aka the plane ASA features have a few limitations compared to the larger models. First off, it has the lowest throughput. Second, it doesn’t have PoE. The last item to note is it doesn’t support switch ports at this time. Some of these and other things may change with a future code update. Hope this helps
Thanks a lot for your reply. That clarifies my questions.
Great port. I bought a 5506 and signed up with Cisco. I went ahead and completed the Get Demo and Evaluation Licenses wizard and received the Key but when I try to activate it, it states “License is Invalid: Not a valid feature license file”. The License ID is L-5506-TAMC-E45D=. Any clues?
I contacted Cisco and they were able to provide the demo license. Thanks for a great port
Hi,
I try to figure it our, that how many recommended devices connecting through these 5506x 5508x when all features are On?
Can it do Bandwidth Management, or multiple WAN?
Hi,
Nice presentation 🙂 I have the exact same setup as you have @ home. 5506-x + firepower.I works fine but i’m a bit disappointed in terms of speed.I have fiber link @ home : 1000Mbps via PPPoE. It goes to a maximum of 15 MB/s
which is ~ 120-130 Mbps.I expected as in the product description to get…not 750…but ~500Mbps. Could be anything wrong configured? or is just the way it goes.(CPU, MEM are in low usage)
Thank you
Hi, Thanks for the great blog.
Can we manage the Cisco 5506-X from another manager application, like IPS Manager express or Firesight management center, instead of the ASDM? I think the ASDM doesn’t manage the Firepower module well. It can’t manage the FirePower’s SSD and log files, can’t export summary reports, and can’t wipe old Firepower logs (I have some test run data and now I’m unable to delete them).
Thanks
Absolutely. Cisco recommends using the FirePOWER manager to manage all firepower solutions (ASA with FP, ISR with FP and FP appliances). This way you have one GUI containing all the data as well as the detail features you are looking for. ASDM only permits you to manage one ASA at a time. Also expect a unified image (ASA and Firepower) in the very near future.
Thanks for the response. Can we use the Firepower manager on VMware for free? I only want to manage 1 device, Asa5506x.
There is a cost however its dirt cheap for managing a few ASAs. Do you have all of the Firepower stuff licensed (URL, IPS and AMP?) on the 5506? As your Cisco solution provider for a quote with discounts for the management. You can also ask to download the VM and have them cut a 90 day key so you can try it out. I posted how to set that up on this blog.
Hi,
I try config a firewall asa 5525 and firesight management 5.4.1. But i cannot get any traffic from the firepower. i config ASA FirePOWER Passive Monitor-Only Traffic Forwarding Mode. Every one can help me plz!
I think you should check the Service Policy Rules in Firewall config as well. Read this: https://supportforums.cisco.com/blog/12294976/asa-5500-x-sourcefire-firepower-configuration